Berning Robot SC Electronic 35mm camera
Serial number 0-01486. Schneider Xenagon 30mm lens, for covert uses. This 35mm camera manufactured in the 1980s takes images 16x16mm in size on its own small diameter cassettes which allow 40 monochrome or 35 colour images to be taken (colour film being thicker than black and white, hence the different capacities). The camera has an interchangeable back, eliminating the need for rewinding film in camera. The camera uses a TTL metering system. The lens has a fixed f5.6 aperture, which allows shutter speeds to be set between 4 and 1/500 of a second. Manual settings are possible. Images can be shot at the rate of one frame every 1.5 seconds. The slowness of the motorised wind on minimises the noise of the camera operationally. Various shutter release mechanisms are known, both mechanical and electronic, including radio control. Mossad allegedly developed an infra-red pulse controlled shutter release. Purported to have been designed to the specifications of the Israeli intelligence service, the camera was intended for covert surveillance. Both its size being around the size of a cigarette packet and its silent operation make it very suitable. It was also certainly used by the East German STASI and other intelligence agencies. The size of the camera lends itself to use in a variety of concealments. Examples evidenced include Sony ‘Walkman’ cassette players, books and handbags. A high quality button frontage for the lens exists. This model comes with an adapted bag concealment, where the lens shoots through a decorative metal emblem on the side of the bag and the shutter is fired by a concealed button. and many more videos from spycamerasaurus, @spycamerasaurus3745Sunday, January 15, 2023
Sunday, January 1, 2023
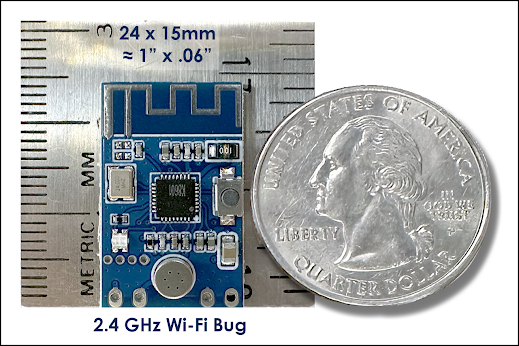
The 2.4 GHz Bug: $10
Friday, December 30, 2022
EarSpy Attack Can Use Motion Sensors Data to Pry on Android Devices
The attack method, named EarSpy, is described in a paper published just before Christmas by researchers from Texas A&M University, Temple University, New Jersey Institute of Technology, Rutgers University, and the University of Dayton.
EarSpy relies on the phone’s ear speaker — the speaker at the top of the device that is used when the phone is held to the ear — and the device’s built-in accelerometer for capturing the tiny vibrations generated by the speaker. more
Monday, December 26, 2022
FutureWatch: More Progress on the Electronic Dog Nose - TSCM Potential
Recap #2: Specially trained dogs have been used to sniff out covert electronic items, like cell phones in prisons, for quite a while now. The secret to detection is the device's electronic circuit boards. They contain these compounds: triphenylphosphine oxide (TPPO) and hydroxycyclohexyl phenyl ketone (HPK). This second compound is also found on CDs, DVDs, Blu-Rays, the old tech floppy disks. (5/18/2021) more
Researchers use biomimicry to enhance particle detection 16-fold by sniffing like dogs. more
FutureWatch: Technical Surveillance Countermeasures (TSCM) professionals have many types of technologies at their disposal for detecting illegal electronic surveillance devices. To name a few... Non-Linear Junction Detection, Infrared Thermography, and Radio-frequency Spectrum Analysis. We are now well on our way to adding EDN to our kit.
Tuesday, December 6, 2022
Spy Tech: Amazing Microphone Tricks
ArkX Labs' EveryWord ultra far-field voice capture and control DSP solutions offer an unmatched voice experience for H2H and H2M interfaces.
Wednesday, November 30, 2022
Under Appreciated Espionage Attach Vector - Computer Repair Shops
Researchers at University of Guelph in Ontario, Canada, recovered logs from laptops after receiving overnight repairs from 12 commercial shops. The logs showed that technicians from six of the locations had accessed personal data and that two of those shops also copied data onto a personal device. Devices belonging to females were more likely to be snooped on, and that snooping tended to seek more sensitive data, including both sexually revealing and non-sexual pictures, documents, and financial information. more
Thursday, September 8, 2022
Using SDRs for Signals Intelligence (SIGINT)
By detecting strange signals in a hostile electromagnetic environment, SIGINT systems can rapidly adapt to emerging threats, locate unknown and/or illegal devices, and counteract against adversarial interference. SIGINT requires a large variety of devices, techniques, and algorithms for RF signal detection, measurement, processing, exploitation, and manipulation.
The most fundamental component in a SIGINT system is the spectrum analyzer. more
Tech Aids Chess Cheating and Possibly More
Thursday, August 18, 2022
Spybuster Tip #823 - The Car Thief Cell Phone Trick
During a crime forum in the Cooper-Young neighborhood, Crump station officers said it was a new tool being used by the bad guys looking for items to steal.
They told the group it doesn’t matter how dark the tint is on your windows; when you put a cell phone in camera mode up to the windows, you can see right through them.
We (WREG-TV) put a cell up to a back window; sure enough, you could see everything in the backseat. more
Tuesday, August 16, 2022
Indoor Optical Fiber Eavesdropping Approach and its Avoidance
1994 - 1999
Number made - 323
Be Careful What You Fish For
Surveillance Documentary: Theo Anthony on All Light, Everywhere
Back home in Baltimore, Anthony also attends to the efforts of Ross McNutt, president of Persistent Surveillance Systems, to sell citizens on his “God’s-eye view” plane-mounted live-feed spy cams – somewhat belatedly, since the tech had previously been deployed in 2016 without disclosure even to the mayor. Now he presents a genial face in community liaison meetings, offering blandishments about providing an “unbiased witness” in “troubled cities”. As Anthony’s voiceover says over an Axon promotional video, “It feels like watching a corporation dream out loud”: the claim is objectivity, the dream is omniscience, the end game is power. One thinks of Jeremy Bentham’s all-seeing panopticon, but also of Naomi Klein’s insights in No Logo into corporate aspirations of weightless, unburdened power. more
Thursday, August 11, 2022
SOS (and more) With the Touch of a Finger
Sunday, July 31, 2022
Chinese Backup Chargers can Eavesdrop and Locate Individuals
Practical Spy Gear: High-Tech Personal Electronics
Personal electronics have come a long way in just the past few years. This sampling of gear that used to be available only to spies just may prove useful in your daily life.
Uzi Parabolic Listening Kit
This comes in handy when you need to better hear what the referee is saying during a football game or want to listen to the songbirds in your backyard. The parabolic microphone and wind deflector funnel sound to an amplifier so you can hear every word or note clearly.
Keep It Clean
Destruct Pro Data Wipe Key
If you sell your computer or send it in for service, make sure your business or personal information doesn’t go along with it. Using a three-phase data-wiping process, this easy-to-use device can be used as often as needed on any PC whose contents you need to delete.
See What’s Ahead
Lanmodo Vast Pro Night Vision Driving Camera
Driving on dark, snowy, rainy, or foggy roads known to be populated with deer or pedestrians can be stressful. This system provides a clear, crisp image of what’s ahead, up to 984 feet, providing you with time to react. An integrated dashcam records in 1080p high-resolution.
Monday, March 28, 2022
Three Declassified Spy Gadgets Of The CIA
Informally known as the “Agency” or the “Company”, the Central Intelligence Agency is a civilian foreign intelligence service of the United States government. Its main task is to gather, process, and analyze national security information from all over the world, mostly through the use of human intelligence and performing actions behind the curtain. It was former-President Harry S. Truman’s initiative to create the Central Intelligence Group out of the Office of Strategic Services on January 22, 1946, which was transformed itself into the Central Intelligence Agency by the implementation of the National Security Act of 1947.
Here are three of the declassified spy gadgets that were designed by the CIA and could be found in their museum:
Spy Quote of the Week
Monday, January 24, 2022
Yamaha Announces VSP-2 Speech Privacy System
Yamaha Unified Communications is broadening its support for productive and confidential conferences and meetings with the new VSP-2 Speech Privacy System. The new system is designed to be quickly retrofitted in almost any office. It also features Yamaha’s high-performance audio technology that prevents speech privacy problems. This is achieved by effectively reducing human voice intelligibility with customizable sound options.
In addition, the system components include the VSP-CU2 control unit with user-selectable sound types and volume levels, supporting two, four, or eight VSP-SP2 speakers. moreSunday, January 9, 2022
iPhone Malware Tactic Causes Fake Shutdowns: Enables Spying
The ‘NoReboot’ technique is the ultimate in persistence for iPhone malware, preventing reboots and enabling remote attackers to do anything on the device while remaining completely unseen.
In the world of mobile malware, simply shutting down a device can often wipe out any bad code, given that persistence after rebooting is a challenge for traditional malicious activity. But a new iPhone technique can hijack and prevent any shut-down process that a user initiates, simulating a real power-off while allowing malware to remain active in the background.The stealthy technique, dubbed “NoReboot” by researchers, is “the ultimate persistence bug,” according to a ZecOps analysis this week...
Is There a Patch for NoReboot?
ZecOps researchers noted that even though they call the issue a “persistence bug,” it can’t actually be patched because “it’s not exploiting any…bugs at all — only playing tricks with the human mind.” Via Twitter, the firm said that the technique works on every version of iPhone, and to prevent it, Apple would need to build in a hardware-based indicator for iPhone sleep/wake/off status.
To protect themselves, iPhone users should run standard checks for malware and trojanized apps, and take the usual vetting precautions when downloading and installing new apps. more
Tuesday, December 7, 2021
Spy Trick # 712 - The Memory Card Ring (Make Your Own!)
Honus, a former bicycle industry designer turned professional jeweler can teach you how to make your own spy ring.
This is how spies (and corrupt employees) can sneak file cabinets of documentation out of companies, no matter how good their security is. more
more spy rings
Secret Message Decoder Ring Great Christmas gift