"Peacetime espionage is best defined as not particularly illegal, and the lack of global governance is likely an intentional choice." ~Danielle Han, from the article: Aspymmetrical Powers: Economic and Cyber Espionage
Friday, December 30, 2022
Georgia Coaches Laugh Off Unfounded ‘Spy Camera’ Accusations
Georgia coaches laughed off Thursday’s hot rumor at the Chick-fil-A Peach Bowl. There was a loose accusation from an Ohio State sportswriter that the Bulldogs used a hidden camera to spy on the Buckeyes’ practices at Mercedes-Benz Stadium.
The truth is, there was a camera found in the stadium before the Buckeyes’ first practice at Mercedes-Benz Stadium this week during a routine security sweep, according to people familiar with the situation. The camera belonged to the stadium as a permanent fixture and was not being operated at the time. Ohio State was informed about it, the camera promptly was removed and everybody moved on. more
Time to read:
Spies on the Sidelines: The High-Stakes World of NFL Espionage
“I hope that’s true,” UGA offensive coordinator Todd Monken said, laughing aloud when asked about it during Media Day on Thursday. “I hope we’ve been in their hotel. I hope we’ve been in their practices. I hope we’re logged into their computers.”
Monken quickly added – “That’s a joke.” ...
The truth is, there was a camera found in the stadium before the Buckeyes’ first practice at Mercedes-Benz Stadium this week during a routine security sweep, according to people familiar with the situation. The camera belonged to the stadium as a permanent fixture and was not being operated at the time. Ohio State was informed about it, the camera promptly was removed and everybody moved on. more
Time to read:
Spies on the Sidelines: The High-Stakes World of NFL Espionage
EarSpy Attack Can Use Motion Sensors Data to Pry on Android Devices
As smartphone manufacturers are improving the ear speakers in their devices, it can become easier for malicious actors to leverage a particular side-channel for eavesdropping on a targeted user’s conversations, according to a team of researchers from several universities in the United States.
The attack method, named EarSpy, is described in a paper published just before Christmas by researchers from Texas A&M University, Temple University, New Jersey Institute of Technology, Rutgers University, and the University of Dayton.
EarSpy relies on the phone’s ear speaker — the speaker at the top of the device that is used when the phone is held to the ear — and the device’s built-in accelerometer for capturing the tiny vibrations generated by the speaker. more
The attack method, named EarSpy, is described in a paper published just before Christmas by researchers from Texas A&M University, Temple University, New Jersey Institute of Technology, Rutgers University, and the University of Dayton.
EarSpy relies on the phone’s ear speaker — the speaker at the top of the device that is used when the phone is held to the ear — and the device’s built-in accelerometer for capturing the tiny vibrations generated by the speaker. more
Turning Google Smart Speakers into Wiretaps
I (@downrightnifty4874) was recently rewarded a total of $107,500 by Google for responsibly disclosing security issues in the Google Home smart speaker that allowed an attacker within wireless proximity to install a “backdoor” account on the device, enabling them to send commands to it remotely over the Internet, access its microphone feed, and make arbitrary HTTP requests within the victim’s LAN (which could potentially expose the Wi-Fi password or provide the attacker direct access to the victim’s other devices). These issues have since been fixed. more video
The Lasers are Coming - Killer Eyeglasses & Drones
For years, movies have teased us with the possibilities of augmented reality (AR) and mixed reality (MR), from Minority Report to Iron Man. But unlike robotic insects and flying suits, AR and MR smart glasses are much closer to reality for everyday consumers. One of the major barriers has been consumers’ desire for lightweight smart glasses that resemble standard eyeglasses and can be worn all day, every day. Compact, chic designs require projection technology and batteries that are as small and power-efficient as possible, which has been difficult to achieve. The internet hype that AR glasses are just around the corner has given into the reality that there are a number of large problems to solve before mass deployment in the consumer space can begin. more
---
Aerial drones are essentially the new improvised explosive devices (IEDs)—they’re relatively cheap and easily weaponized. Weaponized swarms of drones working together on a mission are an asymmetric threat that can quickly turn into an ugly situation. In the future, drones are expected to become faster, more autonomous, more difficult to detect or jam, and deadlier, with more sophisticated swarm attacks.
An arms race of sorts is quietly underway to be able to counter any countermeasures against drones. So the U.S. military is adopting a multilayered counter-drone approach to deal primarily with small drones (classified as Groups 1 and 2)—including commercial ones you can easily buy online and ones with fixed wings that look like tiny airplanes. Pinpoint accuracy at the speed of light makes high-energy lasers, a form of directed energy, one of the most promising options. more
Monday, December 26, 2022
FutureWatch: More Progress on the Electronic Dog Nose - TSCM Potential
Recap #1: Device can detect distress signals from plants that are harmed, under attack It turns out the best way to hear a plant scream is to smell it. (10/17/2008) more
Recap #2: Specially trained dogs have been used to sniff out covert electronic items, like cell phones in prisons, for quite a while now. The secret to detection is the device's electronic circuit boards. They contain these compounds: triphenylphosphine oxide (TPPO) and hydroxycyclohexyl phenyl ketone (HPK). This second compound is also found on CDs, DVDs, Blu-Rays, the old tech floppy disks. (5/18/2021) more
FutureWatch: Technical Surveillance Countermeasures (TSCM) professionals have many types of technologies at their disposal for detecting illegal electronic surveillance devices. To name a few... Non-Linear Junction Detection, Infrared Thermography, and Radio-frequency Spectrum Analysis. We are now well on our way to adding EDN to our kit.
Recap #2: Specially trained dogs have been used to sniff out covert electronic items, like cell phones in prisons, for quite a while now. The secret to detection is the device's electronic circuit boards. They contain these compounds: triphenylphosphine oxide (TPPO) and hydroxycyclohexyl phenyl ketone (HPK). This second compound is also found on CDs, DVDs, Blu-Rays, the old tech floppy disks. (5/18/2021) more
The latest development:
Researchers use biomimicry to enhance particle detection 16-fold by sniffing like dogs. more
Researchers use biomimicry to enhance particle detection 16-fold by sniffing like dogs. more
FutureWatch: Technical Surveillance Countermeasures (TSCM) professionals have many types of technologies at their disposal for detecting illegal electronic surveillance devices. To name a few... Non-Linear Junction Detection, Infrared Thermography, and Radio-frequency Spectrum Analysis. We are now well on our way to adding EDN to our kit.
Friday, December 23, 2022
Eavesdropping & Anti-Eavesdropping Apps
Two new apps to be aware of…
The iEavesdrop app redirects internal microphone, external wired microphone or line input input audio to any Bluetooth audio device such as AirPods so that you can use your phone as a stealth listening device.Using the correct line input cables, audio from any device such as an external microphone, in-flight entertainment or portable gaming device can be routed to your AirPods or other Bluetooth device. iEavesdrop will work with all iOS devices.
THIS APP CAN ALSO BE USED FOR MANY OTHER PURPOSES SUCH AS A BABY MONITOR, HEARING AID OR ANY OTHER APPLICATION THAT REQUIRES YOU TO LISTEN IN OR ROUTE MICROPHONE AUDIO TO A BLUETOOTH DEVICE.
(iOS)
———

(ANDROID)
About this app...
Ever thought someone might eavesdrop through your smart phone? Skewy is a privacy protection method, which is more than just a software setting. With Skewy you can mask your conversation with a simple – yet effective method. Simply making the audio data picked up by your phone unusable. Additionally, Skewy can detect ultrasonic signals to indicate the presence of device tracking technologies.
Thursday, December 22, 2022
Last Minute Xmas Gift for Your TSCM Nerd
Most of these T-shirts are available on amazon.com
Sunday, December 18, 2022
Reno 911: Mayor Finds GPS Tracker on Her Car – Sues PI
Reno mayor Hillary Schieve is suing a private investigator and his company after finding a device attached to her vehicle that was capable of tracking its real-time location.
The lawsuit alleges that the investigator trespassed onto her property to install the device without her consent. It says Schieve was unaware until a mechanic noticed it while working on her vehicle.
The complaint says, further, that the investigator was working on behalf of an “unidentified third party” whose identity she has not been able to ascertain...
There was no immediate response to a request for comment emailed Friday by The Associated Press to David McNeely, the investigator alleged to have placed the tracking device, and 5 Alpha Industries, the company... She brought it to police in neighboring Sparks, and they were able to determine that it had been purchased by McNeely. more
Do-it-Yourself Vehicle GPS Tracker Detection
The lawsuit alleges that the investigator trespassed onto her property to install the device without her consent. It says Schieve was unaware until a mechanic noticed it while working on her vehicle.
The complaint says, further, that the investigator was working on behalf of an “unidentified third party” whose identity she has not been able to ascertain...
There was no immediate response to a request for comment emailed Friday by The Associated Press to David McNeely, the investigator alleged to have placed the tracking device, and 5 Alpha Industries, the company... She brought it to police in neighboring Sparks, and they were able to determine that it had been purchased by McNeely. more
Do-it-Yourself Vehicle GPS Tracker Detection
Students Analyze, Hack, Remove Under-Desk Surveillance Devices
Northeastern University - In October, the university quietly introduced heat sensors under desk without notifying students or seeking their consent. Students removed the devices, hacked them, and were able to force the university to stop its surveillance.
Early in October, Senior Vice Provost David Luzzi installed motion sensors under all the desks at the school's Interdisciplinary Science & Engineering Complex (ISEC), a facility used by graduate students and home to the "Cybersecurity and Privacy Institute" which studies surveillance. These sensors were installed at night—without student knowledge or consent—and when pressed for an explanation, students were told this was part of a study on “desk usage," according to a blog post by Max von Hippel, a Privacy Institute PhD candidate who wrote about the situation for the Tech Workers Coalition’s newsletter.
Early in October, Senior Vice Provost David Luzzi installed motion sensors under all the desks at the school's Interdisciplinary Science & Engineering Complex (ISEC), a facility used by graduate students and home to the "Cybersecurity and Privacy Institute" which studies surveillance. These sensors were installed at night—without student knowledge or consent—and when pressed for an explanation, students were told this was part of a study on “desk usage," according to a blog post by Max von Hippel, a Privacy Institute PhD candidate who wrote about the situation for the Tech Workers Coalition’s newsletter.
More sensors were removed afterwards and put into a "public art piece" in the building lobby spelling out NO! more
Timothy Webster, Pinkerton Spy for the Union Army
In Chicago’s Graceland Cemetery, there is a headstone bearing the name, “Timothy Webster,” but the grave is empty.
The headstone in the Chicago cemetery is actually a memorial, part of the Pinkerton National Detective Agency’s burial plot for its deceased agents.
Webster is actually buried beneath a simple white marble stone in the township cemetery at Onarga, an Iroquois County village some 90 miles south of Chicago.
The headstone in the Chicago cemetery is actually a memorial, part of the Pinkerton National Detective Agency’s burial plot for its deceased agents.
Timothy Webster died at the age of 40 in Richmond, Virginia, where he was hanged as a Union spy on April 29, 1862, by the Confederate government. He was the first spy executed by the Confederates during the Civil War. more
Twit Gets 3 1/2-Year Term on Spying for Saudis
A former Twitter Inc manager convicted of spying for Saudi Arabia by sharing user data several years ago and potentially exposing users to persecution was sentenced to 3-1/2 years in prison on Wednesday, U.S. prosecutors said. more
Can You Solve the GCHQ Christmas Card Challenge?
Today we've released the 2022 #GCHQChristmasChallenge. The puzzle, masterminded by a team of our in-house puzzlers, features on our Director's annual Christmas card.
The card is sent to partners in the UK and around the world who work with us to counter threats, including hostile state activity, terror groups and organised crime gangs.
Whilst the Challenge has been designed for schools and colleges, we're also encouraging the wider public to take on the challenge to pit their wits against our puzzlers. more video And, of course, count on the Security Scrapbook to provide the solution.
Whilst the Challenge has been designed for schools and colleges, we're also encouraging the wider public to take on the challenge to pit their wits against our puzzlers. more video And, of course, count on the Security Scrapbook to provide the solution.
Former Criminal Justice Professor Bugged Ex's Car
A former Iowa Wesleyan University criminal justice professor accused of stalking his ex-wife has been sentenced...charged with stalking and electronic or mechanical eavesdropping...
According to criminal complaints, Buffington is accused of placing a recording device on his ex-wife’s car, which recorded conversations within the vehicle.
Police said Buffington took his two daughters to his office at Iowa Wesleyan and played the recordings for them. Later, one of Buffington’s daughters obtained the recording device and a zip drive and gave them to law enforcement. That daughter told police she found it in Buffington’s bedroom nightstand...
Buffington also is accused of placing nails in the tires of his ex-wife’s car and admitting to her that he tracked her via OnStar. more
According to criminal complaints, Buffington is accused of placing a recording device on his ex-wife’s car, which recorded conversations within the vehicle.
Police said Buffington took his two daughters to his office at Iowa Wesleyan and played the recordings for them. Later, one of Buffington’s daughters obtained the recording device and a zip drive and gave them to law enforcement. That daughter told police she found it in Buffington’s bedroom nightstand...
Buffington also is accused of placing nails in the tires of his ex-wife’s car and admitting to her that he tracked her via OnStar. more
How to find GPS trackers and Bugs in your vehicle.
The National Cryptologic Museum is Open Again - Revamped - With New Spy Stuff
Vince Houghton (the new director of the National Security Agency's National Cryptologic Museum) and his team unveiled what they'd been working on during the COVID 19 pandemic: a complete overhaul of the aging, 1990s-era museum in Fort Meade, Md...
"These are artifacts that have never been on display before to the public at all," Houghton noted...
Until recently, historians believed many of the artifacts on display at the Cryptologic Museum were lost to history. For Houghton, unearthing old and unique pieces of cryptologic history has been an exceptionally satisfying part of his mission.
That's because the NSA maintains a large warehouse where employees have kept highly classified objects in the hopes that one day those stories could be told. Houghton compared the warehouse, where he and his colleagues spent hours before opening the museum, as "the end of Raiders of the Lost Ark," the 1981 Indiana Jones movie ending in a giant room full of treasure.
"It's floor to ceiling crates that are deteriorating, because they were sent back there in 1945," Houghton said. "To me it was like every day was Christmas, because I'm such a nerd about this stuff." more
"These are artifacts that have never been on display before to the public at all," Houghton noted...
Until recently, historians believed many of the artifacts on display at the Cryptologic Museum were lost to history. For Houghton, unearthing old and unique pieces of cryptologic history has been an exceptionally satisfying part of his mission.
That's because the NSA maintains a large warehouse where employees have kept highly classified objects in the hopes that one day those stories could be told. Houghton compared the warehouse, where he and his colleagues spent hours before opening the museum, as "the end of Raiders of the Lost Ark," the 1981 Indiana Jones movie ending in a giant room full of treasure.
"It's floor to ceiling crates that are deteriorating, because they were sent back there in 1945," Houghton said. "To me it was like every day was Christmas, because I'm such a nerd about this stuff." more
Wednesday, December 7, 2022
Weird Science: Hacker Hacks Home Cam Then Reports it to Authorities
A former Davenport West High School science teacher has been found guilty of secretly recording people in various stages of undress in his Bettendorf home.
Clinton R. Vanfossen, 61, will be sentenced Jan. 5 on five counts of invasion of privacy, one count each of preventing apprehension and obstructing justice and electronic or mechanical eavesdropping...
District Court Judge Meghan Corbin filed a written ruling Monday. According to Corbin’s written ruling:
Bettendorf police received a tip from the National Center for Missing and Exploited Children.
According to the tip, a computer hacker in France hacked into the cameras of a home in Bettendorf and reported what he believed were people being unknowingly filmed in intimate moments.
Officers went to the location of the reported cameras, which were in Vanfossen’s Bettendorf home.
Officers searched the home and found two purported smoke detectors that appeared to contain a camera. The first camera was found in the second-floor hallway and the second camera was found inside a family member’s bedroom. more
Clinton R. Vanfossen, 61, will be sentenced Jan. 5 on five counts of invasion of privacy, one count each of preventing apprehension and obstructing justice and electronic or mechanical eavesdropping...
District Court Judge Meghan Corbin filed a written ruling Monday. According to Corbin’s written ruling:
Bettendorf police received a tip from the National Center for Missing and Exploited Children.
According to the tip, a computer hacker in France hacked into the cameras of a home in Bettendorf and reported what he believed were people being unknowingly filmed in intimate moments.
Officers went to the location of the reported cameras, which were in Vanfossen’s Bettendorf home.
Officers searched the home and found two purported smoke detectors that appeared to contain a camera. The first camera was found in the second-floor hallway and the second camera was found inside a family member’s bedroom. more
Canada Awarded RCMP Contract to Firm with Ties to China
Canada - The federal government awarded a contract to provide and maintain RCMP communications equipment to a company with ties to the Chinese government, Radio-Canada has learned.
The contract has security experts raising concerns about potential Chinese access to RCMP communications and data.
On October 6, 2021, the federal government awarded Sinclair Technologies a contract worth $549,637 for a radio frequency (RF) filtering system. One of the system's purposes is to protect the RCMP's land-based radio communications from eavesdropping...
Conor Healy, a Canadian now based in Washington, said, "the risks include eavesdropping, collection of communications data and jamming or shutting down the radio communications system." more
The contract has security experts raising concerns about potential Chinese access to RCMP communications and data.
On October 6, 2021, the federal government awarded Sinclair Technologies a contract worth $549,637 for a radio frequency (RF) filtering system. One of the system's purposes is to protect the RCMP's land-based radio communications from eavesdropping...
Conor Healy, a Canadian now based in Washington, said, "the risks include eavesdropping, collection of communications data and jamming or shutting down the radio communications system." more
PI Surveillance of Hand Injury Plaintiff Becomes 30.1 Billion Lawsuit
Cheap surveillance devices get expensive...
$11M settlement sparks $13.1B suit against American Family Insurance
A new lawsuit seeking billions of dollars in punitive damages claims AmFam and other parties illegally surveilled the plaintiff and her family...
$11M settlement sparks $13.1B suit against American Family Insurance
A new lawsuit seeking billions of dollars in punitive damages claims AmFam and other parties illegally surveilled the plaintiff and her family...
It said that the lawyers hired the PI firm, at AmFam’s behest, to install surveillance devices around Mezqutal’s property and on family vehicles throughout the month of October 2019, or thereabouts.
“The AmFam defendants’ directions to the Martinelli Investigations Defendants included the mandate to have the investigators do whatever they needed to do to get surveillance of the plaintiff,” it said. “This direction was passed on to the Martinelli Investigations defendants by the Baker Donelson defendants.”
The PI defendants “unlawfully entered” Mezquitals’ property and “placed various electronic devices” on her property and two vehicles “to unlawfully record the activities of Plaintiff and her minor children. The electronic devices included at least one hidden video camera and multiple GPS tracking devices.”
The complaint said the PI team strapped a Spypoint Link-Dark “trail cam” digital camera, which is to a tree positioned to “capture plaintiff’s house, vehicles, and a portion of Plaintiff’s driveway. “The view provided by the Spypoint Link-Dark camera is not possible to obtain from a public road or from any other public property, it said. The “unlawful recordings were made without the consent of all persons observed and included photographs, videos, and electronic recordings of the activities of plaintiff and her minor children in a private place that was out of public view.”
The complaint includes claims for invasion of privacy, trespass to realty, trespass to personality, intentional infliction of emotional distress, negligence and punitive damages and seeks joint and several liability for all the defendants. more (Spypoint camera sales video)
“The AmFam defendants’ directions to the Martinelli Investigations Defendants included the mandate to have the investigators do whatever they needed to do to get surveillance of the plaintiff,” it said. “This direction was passed on to the Martinelli Investigations defendants by the Baker Donelson defendants.”
The PI defendants “unlawfully entered” Mezquitals’ property and “placed various electronic devices” on her property and two vehicles “to unlawfully record the activities of Plaintiff and her minor children. The electronic devices included at least one hidden video camera and multiple GPS tracking devices.”
The complaint said the PI team strapped a Spypoint Link-Dark “trail cam” digital camera, which is to a tree positioned to “capture plaintiff’s house, vehicles, and a portion of Plaintiff’s driveway. “The view provided by the Spypoint Link-Dark camera is not possible to obtain from a public road or from any other public property, it said. The “unlawful recordings were made without the consent of all persons observed and included photographs, videos, and electronic recordings of the activities of plaintiff and her minor children in a private place that was out of public view.”
The complaint includes claims for invasion of privacy, trespass to realty, trespass to personality, intentional infliction of emotional distress, negligence and punitive damages and seeks joint and several liability for all the defendants. more (Spypoint camera sales video)
Tuesday, December 6, 2022
Just Because You are Paranoid... Device Found in CEO's Car
Eskom CEO, André de Ruyter, has doubled down on the claim that he stumbled upon a highly sophisticated tracking device under the driver’s seat of his Volvo...
This comes after details were provided to press in October about a circuit board, described as an “NSA-level device”, that De Ruyter found while cleaning his car.
Articles cited a preliminary report prepared by former police commissioner George Fivaz who claimed the device isn’t commercially available, and is typically used by law enforcement and intelligence agencies...
Journalists were provided photos of the circuit board, which they duly published....
Security researcher Daniel Cuthbert was willing to comment on the record.
He explained that, based on the evidence, the device was likely nothing more than a remote of some kind.
Such a remote button could be a gate or garage opener, a panic button, or a way to arm and disarm a home alarm.
MyBroadband’s in-house researcher and electronic engineer Wikus Steyn agreed.
“There is no GPS chip or antenna, so no tracking that way. I see no mic onboard, although there is what seems to be a 2-pin input at the top, but that is most likely for a push button,” Steyn stated. He also said the quality of soldering suggests cheap mass production. more
Our take... I agree with Dan and Wikus. (but be sure to read the last paragraph) If the TI IC info in the photo is correct TI lists the chip's applications as:
- Low-Power, High-Performance, Wireless Systems With Data Rate Up to 1250 kbps
- ISM/SRD Bands: 169, 433, 868, 915, and 920 MHz
- Possible Support for Additional Frequency Bands: 137 to 158.3 MHz, 205 to 237.5 MHz, and 274 to 316.6 MHz
- Smart Metering (AMR/AMI)
- Home and Building Automation
- Wireless Alarm and Security Systems
- Industrial Monitoring and Control
- Wireless Healthcare Applications
- Wireless Sensor Networks and Active RFID
- IEEE 802.15.4g Applications
- Wireless M-Bus, All Modes
Eskom CEO, André de Ruyter, may have misidentified this item, but it definitely doesn't mean he is not being surveilled. Thoughts of tracking and bugging are not normal. Something has made him suspicious. Trust your instincts, André. Get some professional TSCM help, and don't make it a public issue.
Sophos 2023 Threat Report
The Sophos 2023 Threat Report uncovers the latest cyberthreat trends and provides the insights you need to defend against evolving attacks.
Based on the research and real-world experiences of Sophos X-Ops – a new cross-operational unit that links Sophos' threat, incident response and AI cybersecurity experts, the report covers:
Based on the research and real-world experiences of Sophos X-Ops – a new cross-operational unit that links Sophos' threat, incident response and AI cybersecurity experts, the report covers:
- The lasting cyber impact of the war in Ukraine
- The maturity of the “as-a-service” industry and how it has put advanced threat tactics into the hands of nearly any criminal
- How ransomware operators have evolved their activities and mechanisms, both to evade detection and to incorporate novel techniques
- A deep dive into the abuse of legitimate security tools by criminals to execute attacks
- An analysis of the threats facing Linux, Mac, and mobile systems
Spy Tech: Amazing Microphone Tricks
Forget about turning up the TV to block eavesdropping bugs.
The EveryWord™ Ultra Far-Field AFE Processor is here.
ArkX Labs' EveryWord ultra far-field voice capture and control DSP solutions offer an unmatched voice experience for H2H and H2M interfaces.
ArkX Labs' EveryWord ultra far-field voice capture and control DSP solutions offer an unmatched voice experience for H2H and H2M interfaces.
Utilizing 3-D reverberation technology, the AFE voice module and development kit capture voice commands from 3x the distance (up to 9+ meters) versus traditional beam-forming technology.
These solutions work reliably around corners, and in noisy and reverberate environments without having to lower the playback volume from other loud or competing single-point noise sources... Just watch the video.
Friday, December 2, 2022
Quote of the Week
“Realizing that espionage is not science fiction, but a tangible and real risk, is the first step to protect ourselves against it,”
- Nicolas Fierens Gevaert, a spokesperson for the Belgian foreign affairs ministry. more
Wednesday, November 30, 2022
Five News Outlets Urge U.S. to Drop Espionage Charges Against Assange
The New York Times and four other major media outlets that first helped WikiLeaks founder Julian Assange publish sensitive U.S. government documents sent a letter on Monday to federal prosecutors urging them to stop prosecuting him.
The open letter, titled "Publishing is Not a Crime," was signed by the editors and publishers of The Times, The Guardian, the French outlet Le Monde, the German outlet Der Spiegel and the Spanish paper El Pais...
He faces extradition to the United States to stand trial for the hacking-related offenses and violating the 1917 Espionage Act. If Assange is convicted, he could serve up to 175 years in prison. more
Espionage Group Using USB Devices to Hack Targets
USB devices are being used to hack targets in Southeast Asia, according to a new report by cybersecurity firm Mandiant.
The use of USB devices as an initial access vector is unusual as they require some form of physical access — even if it is provided by an unwitting employee — to the target device.
Earlier this year the FBI warned that cybercriminals were sending malicious USB devices to American companies via the U.S. Postal Service with the aim of getting victims to plug them in and unwittingly compromise their networks...
The use of USB devices as an initial access vector is unusual as they require some form of physical access — even if it is provided by an unwitting employee — to the target device.
Earlier this year the FBI warned that cybercriminals were sending malicious USB devices to American companies via the U.S. Postal Service with the aim of getting victims to plug them in and unwittingly compromise their networks...
The hackers behind it are concentrating on targets in the Philippines. The researchers assess the group has a China nexus, although it did not formally attribute the cyber espionage operation to a specific state-sponsored group. more
Tiny State Buys $60 Million Surveillance System
(Kogi is a small state in Nigeria.)
Kogi governor acquires $60 million Chinese surveillance to eavesdrop on people. “We are putting the whole state on the map, real-time, virtual, audio and visual, so as you enter Kogi state from anywhere, we will see you. I won’t go into too much detail.”
Abdulkareem Siyaka, Kogi State Investment Promotion and Public Private Partnership Agency CEO, disclosed that the project would create 685,000 jobs and attract over N591 billion in investment yearly while encouraging migration to Kogi’s rural areas. more
The EU's Spyware Conundrum
MEPs are concerned that eavesdropping with Pegasus-type software is escalating, but the bloc is unlikely to impose rules as the final word rests with member states who dislike such oversight, experts said.
Pegasus and other software, such as Predator, have gained significant notoriety in recent years after it came to light they were being used by governments and politicians against political rivals, journalists, and activists, amongst others...
Jeroen Lenaеrs, chair of the PEGA European Parliament’s Committee of Inquiry to investigate the use of Pegasus and equivalent surveillance spyware, said it was “pretty scary” how much information about personal life the Pegasus-type spyware can get...
Pegasus and other software, such as Predator, have gained significant notoriety in recent years after it came to light they were being used by governments and politicians against political rivals, journalists, and activists, amongst others...
Jeroen Lenaеrs, chair of the PEGA European Parliament’s Committee of Inquiry to investigate the use of Pegasus and equivalent surveillance spyware, said it was “pretty scary” how much information about personal life the Pegasus-type spyware can get...
“The Commission realises that something must be done,” said Lenaеrs... But he lamented the lack of political will from many capitals. more
Under Appreciated Espionage Attach Vector - Computer Repair Shops
If you’ve ever worried about the privacy of your sensitive data when seeking a computer or phone repair, a new study suggests you have good reason. It found that privacy violations occurred at least 50 percent of the time, not surprisingly with female customers bearing the brunt.
Researchers at University of Guelph in Ontario, Canada, recovered logs from laptops after receiving overnight repairs from 12 commercial shops. The logs showed that technicians from six of the locations had accessed personal data and that two of those shops also copied data onto a personal device. Devices belonging to females were more likely to be snooped on, and that snooping tended to seek more sensitive data, including both sexually revealing and non-sexual pictures, documents, and financial information. more
Researchers at University of Guelph in Ontario, Canada, recovered logs from laptops after receiving overnight repairs from 12 commercial shops. The logs showed that technicians from six of the locations had accessed personal data and that two of those shops also copied data onto a personal device. Devices belonging to females were more likely to be snooped on, and that snooping tended to seek more sensitive data, including both sexually revealing and non-sexual pictures, documents, and financial information. more
Saturday, November 26, 2022
Trade Secret Litigation 101
Trade secrets, and their associated value, are an understated facet of commercial activity. The intellectual property owned and protected by businesses carry with them enormous economic weight and are often the target of inappropriate corporate activities such as espionage and theft.
Too often, these pieces of property are insufficiently protected, misunderstood, and do not get the attention they deserve. As such, trade secret litigation has evolved into a niche, but growing area of law practice.
Below, we will explore some of the key elements of trade secret litigation, its scope and magnitude, distinctions between trade secrets and other types of intellectual property, as well as several other important considerations... more
Below, we will explore some of the key elements of trade secret litigation, its scope and magnitude, distinctions between trade secrets and other types of intellectual property, as well as several other important considerations... more
This Week in Spy News
Swedish brothers face trial on Russia spy charges
Two Swedish brothers accused of selling secrets to Russia's intelligence services have gone on trial in what has been called one of Sweden's worst ever alleged cases of espionage. more
Alleged Chinese spy detained in Quebec seeks bail, wants to clear name
A former employee of Quebec's electricity utility who is charged with economic espionage for the benefit of China denied on Thursday that he was a flight risk and said he wanted to stay in Canada to fight the charges. more
US Senators Reportedly Worried About Foreign Espionage As Chinese Drones Fly Over No-Go Zones In DC
Recreational drones made by Da-Jiang Innovations, or DJI, a Chinese technology company, have been reportedly detected in restricted airspace over Washington, D.C. more
UK bans Chinese surveillance cameras from 'sensitive' sites
Hikvision, a leading Chinese surveillance company, has denied suggestions that it poses a threat to Britain's national security after the UK government banned the use of its camera systems at "sensitive" sites. more
Travelling Australian espionage exhibition reveals double life of post-WWII spies
The touring exhibition is at the Albury Library Museum, on the New South Wales and Victorian border, where it explores espionage and counter-espionage in Australia, from federation through to the present day. more
Bond-inspired watches pay homage to franchise’s 60 years

Two Swedish brothers accused of selling secrets to Russia's intelligence services have gone on trial in what has been called one of Sweden's worst ever alleged cases of espionage. more
Alleged Chinese spy detained in Quebec seeks bail, wants to clear name
A former employee of Quebec's electricity utility who is charged with economic espionage for the benefit of China denied on Thursday that he was a flight risk and said he wanted to stay in Canada to fight the charges. more
US Senators Reportedly Worried About Foreign Espionage As Chinese Drones Fly Over No-Go Zones In DC
Recreational drones made by Da-Jiang Innovations, or DJI, a Chinese technology company, have been reportedly detected in restricted airspace over Washington, D.C. more
Pakistan appoints ex-spy master Gen. Munir as new army chief
Pakistani Prime Minister Shahbaz Sharif has named the country's former spy chief as head of the military, the information minister said Thursday, ending months of speculation about the new appointment. more
Fear of espionage: USA bans Huawei products from stores
The US government bans the sale and import of communication devices from Chinese smartphone manufacturers and network suppliers Huawei and ZTE. They posed an unacceptable risk to national security, the US telecommunications regulator FCC said on Friday. more
Pakistani Prime Minister Shahbaz Sharif has named the country's former spy chief as head of the military, the information minister said Thursday, ending months of speculation about the new appointment. more
Fear of espionage: USA bans Huawei products from stores
The US government bans the sale and import of communication devices from Chinese smartphone manufacturers and network suppliers Huawei and ZTE. They posed an unacceptable risk to national security, the US telecommunications regulator FCC said on Friday. more
UK bans Chinese surveillance cameras from 'sensitive' sites
Hikvision, a leading Chinese surveillance company, has denied suggestions that it poses a threat to Britain's national security after the UK government banned the use of its camera systems at "sensitive" sites. more
The touring exhibition is at the Albury Library Museum, on the New South Wales and Victorian border, where it explores espionage and counter-espionage in Australia, from federation through to the present day. more

Swiss watchmaker Omega has released two 007-inspired timepieces.
Photos courtesy Omega
In honour of six decades of high-tech gadgets, espionage, and ‘shaken, not stirred’ martinis, Swiss watchmaker Omega has crafted two new James Bond-inspired timepieces. more
Photos courtesy Omega
In honour of six decades of high-tech gadgets, espionage, and ‘shaken, not stirred’ martinis, Swiss watchmaker Omega has crafted two new James Bond-inspired timepieces. more
Autonomous Vehicle Espionage Concerns in Congress
A member of the American House of Representatives has raised concerns about the dangers of AVs, warning that these vehicles represent a treasure trove of data that could be exploited against American citizens—or national interests...
 |
According to an article by Wired, AVs effectively serve as moving cameras with access to emails, messages, phone calls.
...even though AVs can improve mobility for people with disabilities and make roads safer, they also enable larger, more sophisticated foreign espionage against industries, organizations and dissidents in the United States. For the original letter posted by Wired, click here.
...even though AVs can improve mobility for people with disabilities and make roads safer, they also enable larger, more sophisticated foreign espionage against industries, organizations and dissidents in the United States. For the original letter posted by Wired, click here.
Best Opening Line of a Scam Email Ever (off topic)
Dear Friend,
I am enchanted using this tremendous opportunity to converse with you in this medium of communication....
From, Mr. James Mensa, the accounting manager in the Bank of Africa Ltd., Ghana... offering me "US$4.6million us dollars." I declined the money, however the opening sentence is priceless. I'm stealing that for my own use. ~Kevin
Monday, October 31, 2022
Poor Spycraft: Suspected Spy Had a One-Way Ticket Out of Norway
A man suspected of spying for Russia in Norway had bought a one-way ticket out of the Scandinavian country for the day after he was detained, his lawyer said Thursday.
“He was originally leaving. He had a one-way ticket for Oct. 25,” his lawyer Thomas Hansen told the VG newspaper. He added that his client explained that he had canceled the plane ticket. He did not know where his client intended to travel. more
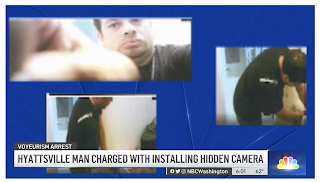
Repair Worker Accused of Hiding Camera in DC Apartment
D.C. police and prosecutors say 41-year-old Eddy Giron installed a small camera in the bathroom of an apartment in Southwest D.C. near the Waterfront Metro station while he did remodeling work...
Detectives are investigating the possibility that there could be other victims. more
Prosecutors said Giron moved the camera to different locations in the bathroom over the course of three days, including inside a vent and beneath the sink aimed at the toilet...
Detectives are investigating the possibility that there could be other victims. more
Retail Employee Says Company Installed Illegal Audio-Recording Cameras at Work
In the U.S., most surveillance laws are dictated at the state level. While the majority of workplaces allow companies to install video cameras that capture visuals of whatever is going on in the store, including interactions of customers and employees, recording audio of their conversations is strictly prohibited in many states.
One of those states is New York, which has implemented anti-eavesdropping statutes that protect employees' conversations from being recorded while at work.
TikToker Ethan Carlson, who posts under the handle @therealethancarlson, recently uploaded a video about his workplace's audio-enabled cameras, prompting many viewers to urge him to report his employer.
In a now viral clip, Ethan says to the camera, "This is not a f--king drill, my place of work has installed these cameras."
He then points his camera lens and zooms in to show security devices installed up high in his store. more
One of those states is New York, which has implemented anti-eavesdropping statutes that protect employees' conversations from being recorded while at work.
TikToker Ethan Carlson, who posts under the handle @therealethancarlson, recently uploaded a video about his workplace's audio-enabled cameras, prompting many viewers to urge him to report his employer.
In a now viral clip, Ethan says to the camera, "This is not a f--king drill, my place of work has installed these cameras."
He then points his camera lens and zooms in to show security devices installed up high in his store. more
Recently in Spycam News
WA - School Employee charged with over 137 counts of voyeurism after it was found that he put a video camera in the female bathroom of a high school that he was working in, reportedly doing so since 2013. more
Singapore - A 25-year-old man was sentenced to three years and 24 weeks in jail and five strokes of the cane for video voyeurism. He was previously sentenced to three years in jail and three strokes of the cane in November 2018. more
FL - Twice this week there were reports that women were secretly recorded in spaces they thought they had privacy while undressing... "I've watched this issue get worse, and the legislation has responded by getting tougher," Palm Beach County State Attorney Dave Aronberg said. more
FL - Condo Association President, Charged with 4 Counts of Video Voyeurism... a cord led to a charger, which had a USB from which a USB cord connected to something in the plant. It was a tiny surveillance video camera. It had been placed there to spy on the bedroom’s occupants. more
Singapore - A 25-year-old man was sentenced to three years and 24 weeks in jail and five strokes of the cane for video voyeurism. He was previously sentenced to three years in jail and three strokes of the cane in November 2018. more
FL - Twice this week there were reports that women were secretly recorded in spaces they thought they had privacy while undressing... "I've watched this issue get worse, and the legislation has responded by getting tougher," Palm Beach County State Attorney Dave Aronberg said. more
FL - Condo Association President, Charged with 4 Counts of Video Voyeurism... a cord led to a charger, which had a USB from which a USB cord connected to something in the plant. It was a tiny surveillance video camera. It had been placed there to spy on the bedroom’s occupants. more
- You don't have to be a victim. Learn how to spot spycams in places where you expect privacy.
Wednesday, October 19, 2022
Police Use New Tool to Track People Without a Warrant
Government agencies and private security companies in the U.S. have found a cost-effective way to engage in warrantless surveillance of individuals, groups and places: a pay-for-access web tool called Fog Reveal.
The tool enables law enforcement officers to see “patterns of life” – where and when people work and live, with whom they associate and what places they visit. The tool’s maker, Fog Data Science, claims to have billions of data points from over 250 million U.S. mobile devices. more
The tool enables law enforcement officers to see “patterns of life” – where and when people work and live, with whom they associate and what places they visit. The tool’s maker, Fog Data Science, claims to have billions of data points from over 250 million U.S. mobile devices. more
Espionage Claim in Airbus Court Fight
Airbus has faced claims that it is using a court battle with an airline to obtain “super sensitive” commercial secrets about Boeing, its main rival.
In the latest twist to the dispute between Qatar Airways and Airbus, the world’s second largest aircraft manufacturer, a judge heard allegations that amounted to corporate espionage.
The Gulf airline is bringing a £1.3 billion claim against Airbus over allegations that problems with cracking paint rendered the A350 passenger aircraft unsafe. more
In the latest twist to the dispute between Qatar Airways and Airbus, the world’s second largest aircraft manufacturer, a judge heard allegations that amounted to corporate espionage.
The Gulf airline is bringing a £1.3 billion claim against Airbus over allegations that problems with cracking paint rendered the A350 passenger aircraft unsafe. more
Zillow Sued For Alleged Wiretapping - It’s not what you think...
If your company maintains a website – whether offering financial products or just selling pet stairs – you now need to be familiar with state and federal wiretapping laws.
The term “wiretapping” probably brings to mind images of police detectives or FBI agents huddled in the back of a white panel van or in a dark room with headphones on, listening to and recording conversations among shady characters.
Yet a spate of recent class action lawsuits against a variety of business websites – including cases filed separately in September in Pennsylvania, Washington, and Missouri against Zillow Group Inc., as well as those filed against hardware retailer Lowe’s and travel website Expedia, among others – all cite state wiretapping laws as the basis of their complaints about invading consumer privacy...
Privacy experts say all of these wiretapping lawsuits have far reaching implications for any business that maintains a website and uses coding, software, or third-party vendors to analyze what clients or consumers do when they visit online. more
Privacy experts say all of these wiretapping lawsuits have far reaching implications for any business that maintains a website and uses coding, software, or third-party vendors to analyze what clients or consumers do when they visit online. more
Sensors Tap Into Mobile Vibrations to Eavesdrop Remotely
Using an off-the-shelf automotive radar sensor and a novel processing approach, Penn State researchers demonstrated they could detect the vibrations of a cell phone's earpiece and decipher what the person on the other side of the call was saying with up to 83% accuracy...
The radar operates in the millimeter-wave (mmWave) spectrum, specifically in the bands of 60 to 64 gigahertz and 77 to 81 gigahertz, which inspired the researchers to name their approach "mmSpy." This is a subset of the radio spectrum used for 5G, the fifth-generation standard for communication systems across the globe.
In the mmSpy demonstration, the researchers simulated people speaking through the earpiece of a smartphone. The brand is irrelevant, Basak said, but the researchers tested their approach on both a Google Pixel 4a and a Samsung Galaxy S20. The phone's earpiece vibrates from the speech, and that vibration permeates across the body of the phone.
"We use the radar to sense this vibration and reconstruct what was said by the person on the other side of the line," Basak said, noting that their approach works even when the audio is completely inaudible to both humans and microphones nearby. more
This paper presents a system mmSpy that shows the feasibility of eavesdropping phone calls remotely. Towards this end, mmSpy performs sensing of earpiece vibrations using an off-the-shelf radar device that operates in the mmWave spectrum (77GHz, and 60GHz). abstract
In the mmSpy demonstration, the researchers simulated people speaking through the earpiece of a smartphone. The brand is irrelevant, Basak said, but the researchers tested their approach on both a Google Pixel 4a and a Samsung Galaxy S20. The phone's earpiece vibrates from the speech, and that vibration permeates across the body of the phone.
"We use the radar to sense this vibration and reconstruct what was said by the person on the other side of the line," Basak said, noting that their approach works even when the audio is completely inaudible to both humans and microphones nearby. more
This paper presents a system mmSpy that shows the feasibility of eavesdropping phone calls remotely. Towards this end, mmSpy performs sensing of earpiece vibrations using an off-the-shelf radar device that operates in the mmWave spectrum (77GHz, and 60GHz). abstract
Saturday, October 15, 2022
SPECIAL EDITION: U.S. Bugging Operation Against Soviets
by Zach Dorfman
It's unknown why the Soviets declined to publicize all the bugs they found within their U.S.-based facilities. The Russians ripped them out from their hiding spots, ostensibly preventing them from feeding the U.S. disinformation through the listening devices and trackers they identified.
Recently, I obtained a set of declassified 1980s intelligence files from Poland’s cold war-era archives. The files detailed a Soviet operation to identify and remove a cornucopia of bugs placed in Russian diplomatic facilities across the United States.
The document — written in Russian and almost certainly produced by the KGB, unlike the other Polish-language files in the tranche of documents — provides a meticulous pictorial account of the ways in which the U.S. spy services sought to technically surveil the Russians on American soil. The file offers an unprecedented, stunning — if dated — look at these efforts to eavesdrop on Russian government activities within the U.S.
The document — written in Russian and almost certainly produced by the KGB, unlike the other Polish-language files in the tranche of documents — provides a meticulous pictorial account of the ways in which the U.S. spy services sought to technically surveil the Russians on American soil. The file offers an unprecedented, stunning — if dated — look at these efforts to eavesdrop on Russian government activities within the U.S.
The file details a number of bugs found at Soviet diplomatic facilities in Washington, D.C., New York, and San Francisco, as well as in a Russian government-owned vacation compound, apartments used by Russia personnel, and even Russian diplomats’ cars.
And the bugs were everywhere:
- encased in plaster in an apartment closet;
- behind electrical and television outlets;
- bored into concrete bricks and threaded into window frames;
- inside wooden beams and baseboards;
- stashed within a building’s foundation itself;
- surreptitiously attached to security cameras;
- wired into ceiling panels and walls;
- and secretly implanted into the backseat of cars and in their window panels, instrument panels, and dashboards.
It’s an impressive — and impressively thorough — effort by U.S. counterspies...
 |
| Click to enlarge. |
“The number of bugs is useful as an indication that this is a sustained operation over years,” a former U.K. intelligence official with experience conducting technical operations told me. (The official requested anonymity to discuss sensitive intelligence techniques.) The sheer variety in where U.S. counterspies placed the bugs shows a great deal of “creativity” on their part, the former U.K. official said. While the bugging of cars and power outlets is considered “fairly standard,” the former official added, U.S. spies cleverly inserted bugs in more unusual locations like window frames...
It's unknown why the Soviets declined to publicize all the bugs they found within their U.S.-based facilities. The Russians ripped them out from their hiding spots, ostensibly preventing them from feeding the U.S. disinformation through the listening devices and trackers they identified.
 |
| Click to enlarge. |
The likelier explanation is that the KGB knew that U.S. diplomatic facilities in the Soviet Union were bugged to hell — including, at certain points, with listening devices activated by blasting American facilities with microwaves. The use of this technique by the Soviets, which some U.S. officials believed sickened those exposed to it, became a serious diplomatic issue in the 1970s between the two superpowers. more
(Kevin) A friend of mine, now deceased, was one of the CIA technical specialists during this time period who developed and planted these devices. He was prohibited from discussing the actual devices and placement operations even after he retired. However, he did write a "fictitious" story which details a typical bugging operation. Corporate security directors especially should read... The Attack on Axnan Headquarters: An Espionage Operation
Thursday, October 6, 2022
Office Bugging Leak Inquiry—Given 7 Days to Submit Report
Pakistani Prime Minister Shehbaz Sharif had ordered the formation of a committee to investigate the leaking of several audio files and a review of cybersecurity at the prime minister’s office (PMO). Formally starting today, the committee will probe the public release of audio clips that took place in the PM office.
PM Office leak inquiry committee is chaired by Rana Sanaullah, Interior Minister, the main agenda behind it is to inquire how this bugging was done and how cyber security was compromised from such a sensitive office...
Subscribe to:
Posts (Atom)