The US government cannot control the skyrocketing use of encrypted communications that allow adversaries, terrorists, criminals — and ordinary folks who care deeply about privacy, including journalists — to block eavesdropping by national security agencies, says a new study funded by DARPA and the Center for Advanced Studies on Terrorism (CAST).
“The ‘golden age of SIGINT’ may be over, particularly within the next five or ten years,” the study, “Going Dark: Implications of an Encrypted World,” finds. The traditional methods of collecting signals intelligence and eavesdropping on communications used by the Intelligence Community (IC) will no longer be effective. “End-to-end encryption of all communications and data, differential privacy, and secure communications for all users are likely to be the new reality,” the study says. more
Tuesday, July 23, 2019
Android Smartphone Alert: Spearphone Eavesdropping
A Spearphone attacker can use the accelerometer in LG and Samsung phones to remotely eavesdrop on any audio that’s played on speakerphone, including calls, music and voice assistant responses.
A new way to eavesdrop on people’s mobile phone calls has come to light in the form of Spearphone – an attack that makes use of Android devices’ on-board accelerometers (motion sensors) to infer speech from the devices’ speakers.
An acronym for “Speech privacy exploit via accelerometer-sensed reverberations from smartphone loudspeakers,” Spearphone was pioneered by an academic team from the University of Alabama at Birmingham and Rutgers University.
They discovered that essentially, any audio content that comes through the speakers when used in speakerphone mode can be picked up by certain accelerometers in the form of sound-wave reverberations. And because accelerometers are always on and don’t require permissions to provide their data to apps, a rogue app or malicious website can simply listen to the reverberations in real time, recording them or livestreaming them back to an adversary, who can analyze and infer private data from them. more
A new way to eavesdrop on people’s mobile phone calls has come to light in the form of Spearphone – an attack that makes use of Android devices’ on-board accelerometers (motion sensors) to infer speech from the devices’ speakers.
An acronym for “Speech privacy exploit via accelerometer-sensed reverberations from smartphone loudspeakers,” Spearphone was pioneered by an academic team from the University of Alabama at Birmingham and Rutgers University.
They discovered that essentially, any audio content that comes through the speakers when used in speakerphone mode can be picked up by certain accelerometers in the form of sound-wave reverberations. And because accelerometers are always on and don’t require permissions to provide their data to apps, a rogue app or malicious website can simply listen to the reverberations in real time, recording them or livestreaming them back to an adversary, who can analyze and infer private data from them. more
Apple Watch Walkie-Talkie is Fixed
The latest release fixes a security flaw in the Walkie-Talkie app that could potentially allow users to listen in on others’ conversations. Apple disabled the app until it could fix the problem, which watchOS 5.3 apparently does. more
Spycam Report from China
Sales of spy cameras are rampant at Shenzhen’s gadget paradise, Huaqiangbei, according to a report by state broadcaster CCTV. The report, secretly filmed (ironically) by CCTV reporters, found vendors selling secret cameras disguised as pens, lighters and alarm clocks, among a number of other things. This is in spite of the fact that it's illegal in China to sell “espionage equipment” that can be used for secretly monitoring and photographing people.
In one case, the CCTV reporter bought a fake power socket with a camera hidden in one of the holes and double-sided tape on the back to allow for mounting on a wall. It included an SD card socket and a charging port at the bottom...
In another example from the report, one shop demonstrated a different power socket that hides the camera in a small hole in the bottom-right corner. The video can also be watched in real time from a smartphone app.
In recent months, a series of events that show just how easy it is to secretly film people in hotels has unnerved people in China. The apparent prevalence of the practice has raised concerns about people’s privacy and safety...
In another case, a couple found a hidden camera in the TV in their hotel room in the city of Zhengzhou. Police later determined one person had installed hidden cameras in at least five rooms. Then they detained a manager at the hotel when he claimed more than 80% of the hotels in the city have hidden cameras. more
In one case, the CCTV reporter bought a fake power socket with a camera hidden in one of the holes and double-sided tape on the back to allow for mounting on a wall. It included an SD card socket and a charging port at the bottom...
In another example from the report, one shop demonstrated a different power socket that hides the camera in a small hole in the bottom-right corner. The video can also be watched in real time from a smartphone app.
In recent months, a series of events that show just how easy it is to secretly film people in hotels has unnerved people in China. The apparent prevalence of the practice has raised concerns about people’s privacy and safety...
In another case, a couple found a hidden camera in the TV in their hotel room in the city of Zhengzhou. Police later determined one person had installed hidden cameras in at least five rooms. Then they detained a manager at the hotel when he claimed more than 80% of the hotels in the city have hidden cameras. more
Google: Wi-Spy Case Cashed Out
Google
is poised to pay a modest $13 million to end a 2010 privacy lawsuit
that was once called the biggest U.S. wiretap case ever and threatened
the internet giant with billions of dollars in damages.
The
settlement would close the books on a scandal that was touched off by
vehicles used by Google for its Street View mapping project. Cars and
trucks scooped up emails, passwords and other personal information from
unencrypted household Wi-Fi networks belonging to tens of millions of
people all over the world. more
Monday, July 22, 2019
From the What Goes Around Files: Russia's FSB Hacked
 Russia's Secret Intelligence Agency Hacked: 'Largest Data Breach In Its History'
Russia's Secret Intelligence Agency Hacked: 'Largest Data Breach In Its History'Red faces in Moscow this weekend, with the news that hackers have successfully targeted FSB—Russia's Federal Security Service. The hackers managed to steal 7.5 terabytes of data from a major contractor, exposing secret FSB projects to de-anonymize Tor browsing, scrape social media, and help the state split its internet off from the rest of the world.
The data was passed to mainstream media outlets for publishing. FSB is Russia's primary security agency with parallels with the FBI and MI5, but its remit stretches beyond domestic intelligence to include electronic surveillance overseas and significant intelligence-gathering oversight. It is the primary successor agency to the infamous KGB, reporting directly to Russia's president. more
Tuesday, July 16, 2019
Information Security: Privacy Tips for Business Travelers
The Basics...
- Beware of shoulder surfers. Get one of these.
- Know when to shut your mouth. Don't give strangers any confidential information.
- Use a Virtual Private Network (VPN).
- Change any passwords you used while on your tip.
- Keep your device with you to reduce info-suck opportunities.
- Avoid using public charging stations (unless you have one of these).
- Read Murray Associates' Guide to Off-Site Meeting Information Security.

Security Director Tips: You Don't Have to be an IT Dude to Protect Your Company Online
The Top 6 things you can do to better than the IT department. (Go ahead. Take back some turf.)
- Establish a cyber incident response plan.
- Regularly rehearse the response plan using a range of different scenarios.
- Monitor and manage the risk posed from the supply chain.
- Ensure the company understands the terms of their insurance and what is covered.
- Understand what 'normal' looks like for the business, in terms of application usage, so the company can identify any unfamiliar patterns.
- Investing in regular training and raising their people's awareness of cyber security. more

Monday, July 15, 2019
Spanish App Works Like Spanish Fly... undercover
Spain’s data protection agency has fined the country’s soccer league, LaLiga, €250,000 (about $280,000) for allegedly violating EU data privacy and transparency laws. The app, which is used for keeping track of games and stats, was using the phone’s microphone and GPS to track bars illegally streaming soccer games...
Using a Shazam-like technology, the app would record audio to identify soccer games, and use the geolocation of the phone to locate which bars were streaming without licenses. more
Using a Shazam-like technology, the app would record audio to identify soccer games, and use the geolocation of the phone to locate which bars were streaming without licenses. more
Spot on ID, or... "The Tell-Tale Heart"
via MIT Technology Review
A new device, developed for the Pentagon after US Special Forces requested it, can identify people without seeing their face: instead it detects their unique cardiac signature with an infrared laser. While it works at 200 meters (219 yards), longer distances could be possible with a better laser. “I don’t want to say you could do it from space,” says Steward Remaly, of the Pentagon’s Combating Terrorism Technical Support Office, “but longer ranges should be possible.”... In the longer run, this technology could find many more uses, its developers believe... more
Like eavesdropping?
(Spoiler Alert: Israeli scientists did this in 2009, and then improved it in 2014.) ~Kevin
A new device, developed for the Pentagon after US Special Forces requested it, can identify people without seeing their face: instead it detects their unique cardiac signature with an infrared laser. While it works at 200 meters (219 yards), longer distances could be possible with a better laser. “I don’t want to say you could do it from space,” says Steward Remaly, of the Pentagon’s Combating Terrorism Technical Support Office, “but longer ranges should be possible.”... In the longer run, this technology could find many more uses, its developers believe... more
Like eavesdropping?
(Spoiler Alert: Israeli scientists did this in 2009, and then improved it in 2014.) ~Kevin
Friday, July 12, 2019
FREE: "Top Secret: From Ciphers to Cyber Security" GCHQ Exhibit in London
 Historic gadgets used by British spies will be revealed for the first time later this week, as one of the country's intelligence agencies steps out the shadows to mark its centenary -- and to educate people about the risks of cyber-attacks.
Historic gadgets used by British spies will be revealed for the first time later this week, as one of the country's intelligence agencies steps out the shadows to mark its centenary -- and to educate people about the risks of cyber-attacks.The Government Communications Headquarters (GCHQ) will hold an unprecedented exhibition at London's Science Museum, taking visitors through 100 years of secret conversations and eavesdropping...
A prototype of the Enigma cipher machine used by the Germans will be on display. But the standout exhibit at this new exhibition is the 5-UCO machine developed in 1943 to send decrypted German messages to officers in the field...
"Top Secret: From Ciphers to Cyber Security" opens to the public on Wednesday and runs until February 2020. more
FREE but must book ahead: Science Museum, Exhibition Road, South Kensington, London SW7 2DD ~Kevin
Historical - A Covert Transmitter & A Mistake = Early Fake News
February 13, 1935 was probably the first case of a major news organization incorrectly reporting a courtroom verdict because of a radio communications fail - the birth of Fake News!
Flemongton, NJ - The Associated Press (AP) thought it was being uniquely creative - and sneaky - during "The Trial of the Century" involving the kidnapping and murder of Charles Lindberg's young son. A reporter secreted in a miniature shortwave transmitter, concealed within a leather brief case. A receiver station above the courtroom stood ready to copy the agreed upon code, based on the verdict, and send the results to its newspaper feeds.
Little did they know that a competing news agency had the same idea, but used a different code. The AP operator received the New York Daily News code assuming it was from the AP mole. It immediately sent the story to hundreds of editors across the world.
One of the short-wave transmitters carried by a reporter into the courtroom at Flemington was concealed in a small leather brief-case...
Short Wave Craft described how to build a short-wave set in a brief-case in the June 1932 issue - three years earlier! With a slight change in the connections, this receiver is easily converted into a transmitter for code signals, such as those used at the Hauptmann trial.
Short waves played a most important role in the famous million-dollar Hauptmann trial. Two tiny short-wave transmitters were secretly carried by reporters into the courtroom and were used to signal the jury's verdict to other reporters outside the locked courtroom. more
Flemongton, NJ - The Associated Press (AP) thought it was being uniquely creative - and sneaky - during "The Trial of the Century" involving the kidnapping and murder of Charles Lindberg's young son. A reporter secreted in a miniature shortwave transmitter, concealed within a leather brief case. A receiver station above the courtroom stood ready to copy the agreed upon code, based on the verdict, and send the results to its newspaper feeds.
Little did they know that a competing news agency had the same idea, but used a different code. The AP operator received the New York Daily News code assuming it was from the AP mole. It immediately sent the story to hundreds of editors across the world.
One of the short-wave transmitters carried by a reporter into the courtroom at Flemington was concealed in a small leather brief-case...
Short Wave Craft described how to build a short-wave set in a brief-case in the June 1932 issue - three years earlier! With a slight change in the connections, this receiver is easily converted into a transmitter for code signals, such as those used at the Hauptmann trial.
Short waves played a most important role in the famous million-dollar Hauptmann trial. Two tiny short-wave transmitters were secretly carried by reporters into the courtroom and were used to signal the jury's verdict to other reporters outside the locked courtroom. more
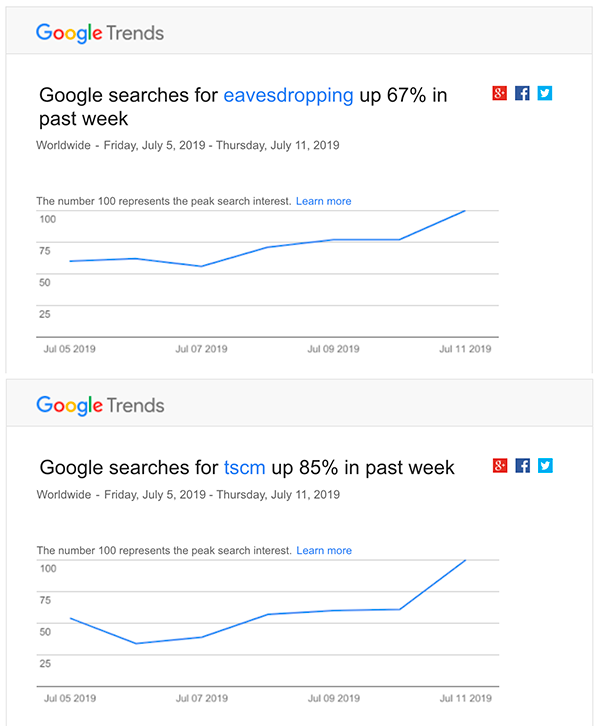
Eavesdropping and TSCM Trends Track Each Other
Conclusion: As organizations and individuals realize that electronic eavesdropping is escalating, they search for Technical Surveillance Countermeasures (TSCM) services, aka bug sweeps.
Thursday, July 11, 2019
Apple Temporarily Disables Walkie Talkie on Apple Watch Over Eavesdropping Concerns
Less than 24 hours after Apple issued a background update to remove a vulnerability in Zoom’s Mac app that installed a surreptitious web server that could activate the video camera without the user’s permission, Apple has disabled another app for a possible security breach. And this time it’s one of its own: Walkie Talkie.
Walkie Talkie was introduced with watchOS 5 as a quicker way to communicate between Apple Watches. Apple promotes it as “a new, easy way to have a one-on-one conversation with anyone who has a compatible Apple Watch.” However, it might not be as private as you think. Apple announced late Wednesday that it was temporarily disabling the Walkie Talkie on the Apple Watch due to eavesdropping concerns. more
This Week in Spycam News
S. Korea - A South Korean TV star has resigned over claims he secretly filmed a woman’s lower body, in the country’s latest celebrity spycam scandal. Presenter Kim Sung-joon pleaded for ‘forgiveness’ after police allegedly caught him red-handed at a metro station in Seoul. more
ID - A Monteview man is facing a felony charge after he admitted to hiding a camera in a bathroom and videotaping people naked, according to court documents. He contacted deputies with the Jefferson County Sheriff’s Office on Thursday, saying he wanted to turn himself in. During the phone call with a deputy, Roundy said he videotaped people taking showers at his home. He told the deputy he knew it was wrong and wanted to know if he could turn himself in on Friday. more
N. Ireland - An ex-children’s nurse accused of inventing a VIP paedophile gang told jurors he set up a hidden camera to film a boy using a toilet out of “curiosity” to see if he found sexual gratification in it. more
India - Days after a 27-year-old model had filed a case against a skin specialist popular among celebrities, accusing her of clandestinely installing a spy camera in her clinic at Lokhan Complex, Andheri West, and taking her pictures, the Oshiwara police arrested the doctor on Monday. more
FL - A Firestone Complete Auto Care employee was arrested Tuesday after recording at least two female customers using the restroom, the Port Orange Police Department... Police were notified of the recording after one of the victims found a recorder inside the women’s restroom. more
LA - The Jefferson Parish District Attorney has brought formal charges in the case of a camera in a restroom at Smoothie King headquarters in Metairie... He allegedly put the camera under a bathroom cabinet at the company's offices when he worked for Smoothie King. more
Canada - A 22-year-old man has been arrested after allegedly filming multiple women changing in a unisex change room at the Eaton Centre... The man then entered the change rooms and placed a homemade recording device on the floor between change room stalls and recorded numerous females changing. A woman occupying one of the change rooms noticed the device on the floor and immediately notified security and police. more
IN - A 20-year-old employee of an Indiana auto parts store has been charged with possession of child pornography and voyeurism after two 10-year-old girls uncovered a cell phone used to film in the company's staff bathroom... The filming device was discovered by the girls hidden behind a plunger and bottles of cleaning products. It had been placed slightly to the left of the toilet. One of the girls had just used the toilet and the other was partially undressed when they discovered the camera. more
Canada - A man pleaded guilty in a London courtroom Tuesday for secretly video taping his family and friends while they were using the bathroom. The court heard that the man set up a hidden camera in the bathroom of his home and recorded about 20 people between 2010 and 2017. He was charged by police after his daughter discovered the camera and told her mother. more
...and a major story from mid-June that slipped through the cracks...
Spycam Facts:
Time to read the next post and let it all sink in.
ID - A Monteview man is facing a felony charge after he admitted to hiding a camera in a bathroom and videotaping people naked, according to court documents. He contacted deputies with the Jefferson County Sheriff’s Office on Thursday, saying he wanted to turn himself in. During the phone call with a deputy, Roundy said he videotaped people taking showers at his home. He told the deputy he knew it was wrong and wanted to know if he could turn himself in on Friday. more
N. Ireland - An ex-children’s nurse accused of inventing a VIP paedophile gang told jurors he set up a hidden camera to film a boy using a toilet out of “curiosity” to see if he found sexual gratification in it. more
India - Days after a 27-year-old model had filed a case against a skin specialist popular among celebrities, accusing her of clandestinely installing a spy camera in her clinic at Lokhan Complex, Andheri West, and taking her pictures, the Oshiwara police arrested the doctor on Monday. more
FL - A Firestone Complete Auto Care employee was arrested Tuesday after recording at least two female customers using the restroom, the Port Orange Police Department... Police were notified of the recording after one of the victims found a recorder inside the women’s restroom. more
LA - The Jefferson Parish District Attorney has brought formal charges in the case of a camera in a restroom at Smoothie King headquarters in Metairie... He allegedly put the camera under a bathroom cabinet at the company's offices when he worked for Smoothie King. more
Canada - A 22-year-old man has been arrested after allegedly filming multiple women changing in a unisex change room at the Eaton Centre... The man then entered the change rooms and placed a homemade recording device on the floor between change room stalls and recorded numerous females changing. A woman occupying one of the change rooms noticed the device on the floor and immediately notified security and police. more
IN - A 20-year-old employee of an Indiana auto parts store has been charged with possession of child pornography and voyeurism after two 10-year-old girls uncovered a cell phone used to film in the company's staff bathroom... The filming device was discovered by the girls hidden behind a plunger and bottles of cleaning products. It had been placed slightly to the left of the toilet. One of the girls had just used the toilet and the other was partially undressed when they discovered the camera. more
Canada - A man pleaded guilty in a London courtroom Tuesday for secretly video taping his family and friends while they were using the bathroom. The court heard that the man set up a hidden camera in the bathroom of his home and recorded about 20 people between 2010 and 2017. He was charged by police after his daughter discovered the camera and told her mother. more
...and a major story from mid-June that slipped through the cracks...
New Zealand - Ninety women, 81 images, 30 hours of hidden camera video - the victims' stories... more
Spycam Facts:
- Most spycam attacks go undetected.
- A few are discovered... almost all by accident.
- Only a few of these are reported to the police.
- Only a few of these cases are solved.
- Only a few of these cases make the news.
- Only few of these make it to my desk.
- I only share a few of them with you.
Time to read the next post and let it all sink in.
New Report Projects the Size of the World Spycam Market 2019-2025
An extensive analysis of the Global Spy Cameras market strategy of the leading companies in the precision of import/export consumption, supply and demand figures, cost, price, revenue and gross margins.
The report starts by an introduction about the company profiling and a comprehensive review about the strategy concept and the tools that can be used to assess and analyze strategy.
It also analyzes the company’s strategy in the light of Porter’s Value Chain, Porter’s Five Forces, SWOT analysis, and recommendation on Balanced Scorecard for supply chain analysis...
The Spy Cameras market was valued at xx Million US$ in 2018 and is projected to reach xx Million US$ by 2025, at a CAGR of xx% during the forecast period.
In this study, 2018 has been considered as the base year and 2019 to 2025 as the forecast period to estimate the market size for Spy Cameras.
This report presents the worldwide Spy Cameras market size (value, production and consumption), splits the breakdown (data status 2014-2019 and forecast to 2025), by manufacturers, region, type and application. more
If you want to fill in the X's, you'll have to purchase the report ($4,600.).
Takeaway... It must be a monster market if professional forecast reports are covering it. But, we already knew that. ~Kevin
The report starts by an introduction about the company profiling and a comprehensive review about the strategy concept and the tools that can be used to assess and analyze strategy.
It also analyzes the company’s strategy in the light of Porter’s Value Chain, Porter’s Five Forces, SWOT analysis, and recommendation on Balanced Scorecard for supply chain analysis...
The Spy Cameras market was valued at xx Million US$ in 2018 and is projected to reach xx Million US$ by 2025, at a CAGR of xx% during the forecast period.
In this study, 2018 has been considered as the base year and 2019 to 2025 as the forecast period to estimate the market size for Spy Cameras.
This report presents the worldwide Spy Cameras market size (value, production and consumption), splits the breakdown (data status 2014-2019 and forecast to 2025), by manufacturers, region, type and application. more
If you want to fill in the X's, you'll have to purchase the report ($4,600.).
Takeaway... It must be a monster market if professional forecast reports are covering it. But, we already knew that. ~Kevin
Wednesday, July 10, 2019
Security Quote of the Week
"To paraphrase Warren Buffett, “we are in uncharted
territory, and it’s going to get worse, not better.” By not having the
right technology skillsets in every boardroom, companies and their
boards have set themselves up for failure, so it’s almost guaranteed to
get worse before it gets better.
Hackers come from all over the world with different motivations, including corporate espionage, and financial and health data theft.
They are incredibly diligent in figuring out creative ways to attack corporate networks, and while these anonymous hackers advance their tactics, it is critical for companies to anticipate what’s coming next and stay a step ahead of them." ~Bob Zukis in Forbes Magazine
 Inevitable... As IT security improves expect an increase in classic attacks: electronic eavesdropping, VoIP phone taps, dumpster diving, covert intrusions, employee subversion, and blackmail to name a few. Protection will come when information security is addressed in a holistic manner. ~ Kevin
Inevitable... As IT security improves expect an increase in classic attacks: electronic eavesdropping, VoIP phone taps, dumpster diving, covert intrusions, employee subversion, and blackmail to name a few. Protection will come when information security is addressed in a holistic manner. ~ Kevin
Hackers come from all over the world with different motivations, including corporate espionage, and financial and health data theft.
They are incredibly diligent in figuring out creative ways to attack corporate networks, and while these anonymous hackers advance their tactics, it is critical for companies to anticipate what’s coming next and stay a step ahead of them." ~Bob Zukis in Forbes Magazine
 Inevitable... As IT security improves expect an increase in classic attacks: electronic eavesdropping, VoIP phone taps, dumpster diving, covert intrusions, employee subversion, and blackmail to name a few. Protection will come when information security is addressed in a holistic manner. ~ Kevin
Inevitable... As IT security improves expect an increase in classic attacks: electronic eavesdropping, VoIP phone taps, dumpster diving, covert intrusions, employee subversion, and blackmail to name a few. Protection will come when information security is addressed in a holistic manner. ~ KevinFREE - Security Message Screen Savers
Security Message Screen Savers
- Reminders work.
- Put your idle computer screens to work.
- Three backgrounds to choose from, or commission custom screens.
Supreme Court Relaxes the Confidentiality Standard... but you have to do your part!
via Blank Rome LLP -
Robyn N. Burrows
 The Supreme Court in Food Marketing Institute v. Argus Leader Media, No. 18-481 (U.S. June 24, 2019) recently relaxed the standard for withholding confidential information under Exemption 4 of the Freedom of Information Act (“FOIA”)—a major win for contractors that regularly submit sensitive business information to the government...
The Supreme Court in Food Marketing Institute v. Argus Leader Media, No. 18-481 (U.S. June 24, 2019) recently relaxed the standard for withholding confidential information under Exemption 4 of the Freedom of Information Act (“FOIA”)—a major win for contractors that regularly submit sensitive business information to the government...
To take full advantage of the Court’s holding, companies doing business with the government should keep in mind the following practical tips:
 The Supreme Court in Food Marketing Institute v. Argus Leader Media, No. 18-481 (U.S. June 24, 2019) recently relaxed the standard for withholding confidential information under Exemption 4 of the Freedom of Information Act (“FOIA”)—a major win for contractors that regularly submit sensitive business information to the government...
The Supreme Court in Food Marketing Institute v. Argus Leader Media, No. 18-481 (U.S. June 24, 2019) recently relaxed the standard for withholding confidential information under Exemption 4 of the Freedom of Information Act (“FOIA”)—a major win for contractors that regularly submit sensitive business information to the government...To take full advantage of the Court’s holding, companies doing business with the government should keep in mind the following practical tips:
- Carefully document all efforts to keep information private.* This includes updating internal policies on maintaining the confidentiality of company records, increasing security features limiting access to certain sensitive data, and providing additional training to employees on how to properly handle confidential business information.
- In submissions to the government, clearly indicate which information is to be kept confidential. This includes marking the data with a protective legend identifying it as subject to Exemption 4 protection. Be aware that certain statutes and regulations may require specific language to be used.
- To the extent possible, obtain written assurances from the agency that the information will be kept confidential and will not be released to third parties absent the contractor’s consent. Contractors may also be able to negotiate contractual provisions protecting the data to be submitted to the government. more
Killed for Spying: The Story of the First Factory
Piedmont, in north-west Italy, is celebrated for its fine wine. But when a young Englishman, John Lombe, traveled there in the early 18th Century, he was not going to savoir a glass of Barolo. His purpose was industrial espionage.
Lombe wished to figure out how the Piedmontese spun strong yarn from silkworm silk. Divulging such secrets was illegal, so Lombe snuck into a workshop after dark, sketching the spinning machines by candlelight. In 1717, he took those sketches to Derby in the heart of England.
Local legend has it that the Italians took a terrible revenge on Lombe, sending a woman to assassinate him.
Whatever the truth of that, he died suddenly at the age of 29, just a few years after his Piedmont adventure. more
Lombe wished to figure out how the Piedmontese spun strong yarn from silkworm silk. Divulging such secrets was illegal, so Lombe snuck into a workshop after dark, sketching the spinning machines by candlelight. In 1717, he took those sketches to Derby in the heart of England.
Local legend has it that the Italians took a terrible revenge on Lombe, sending a woman to assassinate him.
Whatever the truth of that, he died suddenly at the age of 29, just a few years after his Piedmont adventure. more
A Favorite M.I.B. — M.I.A. — R.I.P. Torn
Tuesday, July 9, 2019
Kieffer Ramirez Shares His Favorite Niche Investigations Resources (most are free)
 SpyDialer
SpyDialer
Cost: FreeSearch people via their phone number, name, address, and/or e-mail address by using SpyDialer which contains billions of phone numbers obtained using social media and user-contributed address books.

Concerned about your information showing up on SpyDialer?!?! Check and see. If you appear there, you have the option of deleting your information... anonymously.
The 17 other resources appear here.
Labels:
advice,
computer,
information security,
PI,
privacy,
spy school,
Tips
More Than 1,000 Android Apps Spy... even when you deny permission!
 Permissions on Android apps are intended to be gatekeepers for how much data your device gives up. If you don't want a flashlight app to be able to read through your call logs, you should be able to deny that access.
Permissions on Android apps are intended to be gatekeepers for how much data your device gives up. If you don't want a flashlight app to be able to read through your call logs, you should be able to deny that access.But... even when you say no, many apps find a way around: Researchers discovered more than 1,000 apps that skirted restrictions, allowing them to gather precise geolocation data and phone identifiers behind your back...
Google said it would be addressing the issues in Android Q, which is expected to release this year. more
Monday, July 8, 2019
Porcelain — An Industrial Espionage Story
1712 A.D. ...a French Jesuit priest named François Xavier d’Entrecolles
pioneered industrial espionage by recording the secrets of porcelain
making while on a trip to China and sending them back to Europe...
 Another remarkable use for porcelain is the lithophane,
a sheet of porcelain so thin as to be translucent, with artwork etched
into it. The lithophane is thin enough that the art can only be seen
when backlit, but just thick enough that the image can have depth.
Lithophanes began to appear in several parts of Europe in the 1820s, but
they’re believed to have originated in China a millennia earlier during
the Tang Dynasty. Later Ming Dynasty scholars wrote of Tang bowls “as
thin as paper” that included secret images.
Another remarkable use for porcelain is the lithophane,
a sheet of porcelain so thin as to be translucent, with artwork etched
into it. The lithophane is thin enough that the art can only be seen
when backlit, but just thick enough that the image can have depth.
Lithophanes began to appear in several parts of Europe in the 1820s, but
they’re believed to have originated in China a millennia earlier during
the Tang Dynasty. Later Ming Dynasty scholars wrote of Tang bowls “as
thin as paper” that included secret images.
 Another remarkable use for porcelain is the lithophane,
a sheet of porcelain so thin as to be translucent, with artwork etched
into it. The lithophane is thin enough that the art can only be seen
when backlit, but just thick enough that the image can have depth.
Lithophanes began to appear in several parts of Europe in the 1820s, but
they’re believed to have originated in China a millennia earlier during
the Tang Dynasty. Later Ming Dynasty scholars wrote of Tang bowls “as
thin as paper” that included secret images.
Another remarkable use for porcelain is the lithophane,
a sheet of porcelain so thin as to be translucent, with artwork etched
into it. The lithophane is thin enough that the art can only be seen
when backlit, but just thick enough that the image can have depth.
Lithophanes began to appear in several parts of Europe in the 1820s, but
they’re believed to have originated in China a millennia earlier during
the Tang Dynasty. Later Ming Dynasty scholars wrote of Tang bowls “as
thin as paper” that included secret images.
High Profile Executives — A Company’s Most Vulnerable Target
High-profile people—executives, the board of directors, and other leaders—are privy to sensitive information that cybercriminals lust after which makes them primary targets...
 FBI statistics show that defrauding CEOs is a “$12 billion scam.” When private information about these high-net-worth individuals gets exposed, it carries a high degree of risk for that individual and their business alike. It might even include threats against the executive’s own physical security or that of their family...
FBI statistics show that defrauding CEOs is a “$12 billion scam.” When private information about these high-net-worth individuals gets exposed, it carries a high degree of risk for that individual and their business alike. It might even include threats against the executive’s own physical security or that of their family...
When information is readily available about a wealthy person, bad actors have more leverage to compromise them. Consider that Facebook’s board of directors recently granted Mark Zuckerberg a $10 million yearly allowance to security. That money goes to personnel, equipment, and services needed to keep him and his family safe by maintaining vigilance across both physical and digital realms. more
 FBI statistics show that defrauding CEOs is a “$12 billion scam.” When private information about these high-net-worth individuals gets exposed, it carries a high degree of risk for that individual and their business alike. It might even include threats against the executive’s own physical security or that of their family...
FBI statistics show that defrauding CEOs is a “$12 billion scam.” When private information about these high-net-worth individuals gets exposed, it carries a high degree of risk for that individual and their business alike. It might even include threats against the executive’s own physical security or that of their family...When information is readily available about a wealthy person, bad actors have more leverage to compromise them. Consider that Facebook’s board of directors recently granted Mark Zuckerberg a $10 million yearly allowance to security. That money goes to personnel, equipment, and services needed to keep him and his family safe by maintaining vigilance across both physical and digital realms. more
Breach at 10 of the World’s Biggest Telecoms, or Follow the Leader
A multi-year attack carried out by Chinese hackers was exposed recently, and the scope of it is beyond anything previously seen in nation-state cyber espionage.
Hacking group APT10, a notorious team that is widely believed to have Chinese government support, is believed to have compromised at least 10 major global carriers and used their networks to track and spy on high-profile business leaders and members of foreign governments.
What makes this cyber espionage incident unique is that the Chinese hackers appear to have been following their targets as they move from country to country, hopping from one breached network to another as needed. While this ability is not new, this kind of mass scale has not been seen before. more
Hacking group APT10, a notorious team that is widely believed to have Chinese government support, is believed to have compromised at least 10 major global carriers and used their networks to track and spy on high-profile business leaders and members of foreign governments.
What makes this cyber espionage incident unique is that the Chinese hackers appear to have been following their targets as they move from country to country, hopping from one breached network to another as needed. While this ability is not new, this kind of mass scale has not been seen before. more
Ag Tech Being Targeted by International Espionage
In a special report, HAT (Hoosier Ag Today) focuses on how ag biotech has become a top
priority for foreign spies. It sounds like the plot of a James Bond
thriller: foreign governments trying to steal top secret military
technology to take over the world. But, in reality, it has become
agricultural technology that foreign governments want to steal from the
U.S. “If you have a competitive advantage in the field of agriculture,
there is a high chance that a foreign government would target that
technology,” says Craig Moringiello, special agent with the FBI...
However, companies and universities are not the only ones at risk. The FBI is urging farmers to be vigilant as well. “Farmers should be vigilant in protecting their operations and security measures,” said Moringiello. He warned farmers to be aware when having foreign visitors on their farms. more
However, companies and universities are not the only ones at risk. The FBI is urging farmers to be vigilant as well. “Farmers should be vigilant in protecting their operations and security measures,” said Moringiello. He warned farmers to be aware when having foreign visitors on their farms. more
How to Tell If Someone Is Bugging or Tracking You
via Popular Mechanics...
Are you being bugged?
To find out, the first step is to consider carefully whether you are sufficiently interesting to warrant surveillance. If you’re a crook, a cheater, or a keeper of political or corporate secrets, the answer may be yes...
Consider also whether that gift from a business acquaintance could be a Trojan paperweight or Dumbo-eared desk clock. Maybe pass those along to Goodwill and, if you have any lingering doubts, call in a pro to execute a “bug sweep.” more
Are you being bugged?
To find out, the first step is to consider carefully whether you are sufficiently interesting to warrant surveillance. If you’re a crook, a cheater, or a keeper of political or corporate secrets, the answer may be yes...
Consider also whether that gift from a business acquaintance could be a Trojan paperweight or Dumbo-eared desk clock. Maybe pass those along to Goodwill and, if you have any lingering doubts, call in a pro to execute a “bug sweep.” more
Subscribe to:
Posts (Atom)