TX - Galveston police are on the lookout for the “dancing burglar” who was captured on video busting some moves during the break-in of a Duck Tours amphibious vehicle.
The 38-second video released by Galveston police Capt. Jeff Heyse on Wednesday shows a man apparently chatting with someone before he busts the dance moves.
The dancer (later identified as a juvenile) is one of three people sought in connection with the March 27 burglary of a Duck Tours amphibious automobile, which takes sightseers along Galveston streets and the bay. (more)
Sunday, May 20, 2012
"One can never be too far away, or too thin. Besides, what's in a name?"
NJ - An appeals court has ruled that police in New Jersey can wiretap a suspect in another state without obtaining a warrant from the judge of that state.
Thursday’s ruling also confirms the murder conviction of Edward Ates, a Florida man who was sentenced to life in prison after failing to persuade a jury of the argument that he was too fat to have committed the 2006 murder of his son-in-law.
Ates was convicted in 2009 of fatally shooting his former son-in-law. An investigation by Bergen County prosecutors included wiretapping calls Ates made from Florida to his mother and sister in Louisiana. (more)
Thursday’s ruling also confirms the murder conviction of Edward Ates, a Florida man who was sentenced to life in prison after failing to persuade a jury of the argument that he was too fat to have committed the 2006 murder of his son-in-law.
Ates was convicted in 2009 of fatally shooting his former son-in-law. An investigation by Bergen County prosecutors included wiretapping calls Ates made from Florida to his mother and sister in Louisiana. (more)
Saturday, May 19, 2012
Security Tops Boardroom Agendas
via the Financial Times...
Securing corporate intellectual property assets, customer data and other information in the face of an onslaught of attacks from cyber thieves, spies and “hactivists” is now a top priority for most chief information officers and – increasingly – for the corporate boardroom.
“It is definitely something I think about all the time,” says the chief information officer of a US-based consumer goods multinational that, like many other companies, particularly those in the financial services sector, now has an IT security team led by a chief information security officer (CISO.)...
“Our companies are targeted for insider information and our universities and national laboratories are targeted for their research and development,” Robert Mueller, Federal Bureau of Investigations director told a US congressional panel last year...
Meanwhile companies and other organizations have begun to spend more on identifying and protecting their key data using multiple layers of defense and, perhaps most importantly, monitoring and detection systems that can identify security breaches quickly and efficiently. (one example) (more)
Securing corporate intellectual property assets, customer data and other information in the face of an onslaught of attacks from cyber thieves, spies and “hactivists” is now a top priority for most chief information officers and – increasingly – for the corporate boardroom.
“It is definitely something I think about all the time,” says the chief information officer of a US-based consumer goods multinational that, like many other companies, particularly those in the financial services sector, now has an IT security team led by a chief information security officer (CISO.)...
“Our companies are targeted for insider information and our universities and national laboratories are targeted for their research and development,” Robert Mueller, Federal Bureau of Investigations director told a US congressional panel last year...
Meanwhile companies and other organizations have begun to spend more on identifying and protecting their key data using multiple layers of defense and, perhaps most importantly, monitoring and detection systems that can identify security breaches quickly and efficiently. (one example) (more)
This Time the Janitor is Spied Upon
AK - Educators at Gilson Junior High were shocked and outraged to learn
janitorial supervisors had planted a hidden camera in the ceiling tiles
of the teacher lounge above a computer workplace, ostensibly in hopes of
catching janitors goofing off on the computer rather than working.
Outrage spread when a second camera hidden in a clock was discovered in a
custodial closet at Valdez High School. It was later learned the same
camera had been located in the teacher lounge at the junior high days
before it was found at the high school. (more)
Possible Surveillance Drone Strike? In Colorado?!?!
CO - A mystery object, thought to be a military or law enforcement drone, flying in controlled airspace over Denver almost caused a catastrophic mid air crash with a commercial jet Monday.
The pilot of the Cessna jet radioed air traffic controllers to warn them that “A remote controlled aircraft” had flown past his plane far too close for comfort.
“Something just went by the other way … About 20 to 30 seconds ago. It was like a large remote-controlled aircraft.” the pilot said in the transmission that was captured on the live air traffic audio website liveatc.net (Look for 2012-05-16 15:00:51 in the archive section. Free registration required.) (more)
The pilot of the Cessna jet radioed air traffic controllers to warn them that “A remote controlled aircraft” had flown past his plane far too close for comfort.
“Something just went by the other way … About 20 to 30 seconds ago. It was like a large remote-controlled aircraft.” the pilot said in the transmission that was captured on the live air traffic audio website liveatc.net (Look for 2012-05-16 15:00:51 in the archive section. Free registration required.) (more)
"Spy, the Secret World of Espionage" Now open in NYC
The mysterious cloak and dagger world of international espionage and its real-life heros and villains are exposed in a new exhibition, the first to be sanctioned by U.S. intelligence agencies.
"Spy, the Secret World of Espionage," which opens at the Discovery Times Square on Friday, includes hundreds of artifacts, some from the vaults of the CIA and FBI and the National Reconnaissance Office (NRO).
They range from a World War Two-era collapsible motorbike that could be dropped by parachute and deployed in 10 seconds and a German ENIGMA machine to create secret messages to a camel saddle used by one of the first CIA agents in Afghanistan after the 9/11 attacks to bugging devices, microdots and surveillance equipment.
"This is the first and only time these items will ever travel. It is kind of an unparalleled cooperation and collaboration with the CIA and FBI," said H. Keith Melton, author, intelligence historian and expert on spy technology who contributed items from his own collection. (more)
"Spy, the Secret World of Espionage," which opens at the Discovery Times Square on Friday, includes hundreds of artifacts, some from the vaults of the CIA and FBI and the National Reconnaissance Office (NRO).
They range from a World War Two-era collapsible motorbike that could be dropped by parachute and deployed in 10 seconds and a German ENIGMA machine to create secret messages to a camel saddle used by one of the first CIA agents in Afghanistan after the 9/11 attacks to bugging devices, microdots and surveillance equipment.
"This is the first and only time these items will ever travel. It is kind of an unparalleled cooperation and collaboration with the CIA and FBI," said H. Keith Melton, author, intelligence historian and expert on spy technology who contributed items from his own collection. (more)
Friday, May 18, 2012
Facebook's Trading Day Begins with... a Wiretap Lawsuit
Facebook is being sued for $15 billion for tracking users, even after they have logged out of the social network, and violating federal wiretap laws.
Today’s lawsuit, filed in Federal Court in San Jose, California, combines 21 separate cases across the U.S. in 2011 and early 2012... If the claimants are successful in their case against Facebook, they could prevent Menlo Park from collecting the huge amount of data it collects about its users to serve ads back to them.
Like the previous lawsuits, Facebook is once again being accused of violating the Federal Wiretap Act, which provides statutory damages per user of $100 per day per violation, up to a maximum per user of $10,000. The complaint also asserts claims under the Computer Fraud and Abuse Act, the Stored Communications Act, various California Statutes, and California common law. It’s worth noting that similar cases against Facebook and others filed under the wiretap law have been thrown out because browser cookies are simply not considered wiretaps and plaintiffs have difficulty proving any harm. (more)
Today’s lawsuit, filed in Federal Court in San Jose, California, combines 21 separate cases across the U.S. in 2011 and early 2012... If the claimants are successful in their case against Facebook, they could prevent Menlo Park from collecting the huge amount of data it collects about its users to serve ads back to them.
Like the previous lawsuits, Facebook is once again being accused of violating the Federal Wiretap Act, which provides statutory damages per user of $100 per day per violation, up to a maximum per user of $10,000. The complaint also asserts claims under the Computer Fraud and Abuse Act, the Stored Communications Act, various California Statutes, and California common law. It’s worth noting that similar cases against Facebook and others filed under the wiretap law have been thrown out because browser cookies are simply not considered wiretaps and plaintiffs have difficulty proving any harm. (more)
Android Cell Phone Users Security Alert
Malware targeting Android users has nearly quadrupled since 2011. As you can see in the graph, 10 Android malware families were detected in Q1 2011. This number increased for two quarters in a row, then dipped for one, and then finally settled at 37 in Q1 2012. That means a year-over-year growth of 270 percent.
The data comes from security firm F-Secure. The trend was revealed today in the company’s 47-page Mobile Threat Report Q1 2012 (PDF).
 It makes sense that both the number of malware families and malicious Android APKs is increasing, but it’s still staggering to see that the latter number is now over 3,000, whereas last year it was just above 100.
It makes sense that both the number of malware families and malicious Android APKs is increasing, but it’s still staggering to see that the latter number is now over 3,000, whereas last year it was just above 100.
The increase in malware numbers is indicative of a wider increase in mobile threats, according to F-Secure. Even more worrying, however, is that the Finnish security firm warned many of the apps are targeting Android users’ financial data, noting that 34 of the current malware families are designed to steal money from infected smartphones. (more)
Tip: Do not download, open or install anything unless you absolutely need it and are 100% confident it is coming to you from a trusted source. ~Kevin
The data comes from security firm F-Secure. The trend was revealed today in the company’s 47-page Mobile Threat Report Q1 2012 (PDF).
 It makes sense that both the number of malware families and malicious Android APKs is increasing, but it’s still staggering to see that the latter number is now over 3,000, whereas last year it was just above 100.
It makes sense that both the number of malware families and malicious Android APKs is increasing, but it’s still staggering to see that the latter number is now over 3,000, whereas last year it was just above 100. The increase in malware numbers is indicative of a wider increase in mobile threats, according to F-Secure. Even more worrying, however, is that the Finnish security firm warned many of the apps are targeting Android users’ financial data, noting that 34 of the current malware families are designed to steal money from infected smartphones. (more)
Tip: Do not download, open or install anything unless you absolutely need it and are 100% confident it is coming to you from a trusted source. ~Kevin
Password Evaluation Program Will Surprise You
Passfault evaluates the strength of passwords accurately enough to predict the time to crack. It makes creating passwords and password policies significantly more intuitive and simple.
When setting a password, Passfault examines the password, looking for common patterns. Passfault than measures the strength of the patterns and combinations of patterns. The end result is a more academic and accurate measurement of password strength. (more) (test your password)
You might think a password like 123!@#qweQWE would provide excellent protection. Wrongo. It can be cracked in a day according to Passfault. Why? Because it contains a readily identifiable pattern of keystrokes. Now try something easy to remember like ToBeOrNotToBe. Surprised? Thought so. ~Kevin
Friday, May 11, 2012
America Begins to Strike Back Publicly Against Trade Secret Thefts (Plus, an idea for a change in the law.)
The Federal Bureau of Investigation's spy hunters usually shy away from drawing attention. But they're hoping the public takes notice of a new campaign trying to stop foreign spies from stealing trade secrets from U.S. companies.
The FBI, which is responsible for investigating breaches by foreign intelligence agencies, Friday will unveil billboards in nine cities around the country with the message: Protect America's Trade Secrets. The billboards direct the public to a section of the FBI website where the bureau provides warning signs to look for in the cubicle next to you.
Behind the campaign is the government's view that state-sponsored espionage targeting companies is growing so fast it is a national security concern. Lost trade secrets lead to lost jobs and in a time of economic struggle poses a national threat, says Frank Figliuzzi, the FBI's assistant director for counterintelligence. (more)
Note to FBI... Awareness is good, but it is not enough. Some private-sector intellectual property is so vital it should be classified as a National Security Resource.
The centuries-old, lopsided, 'punish the spy' model of protecting intellectual property has never worked. (more) (more) Caretakers of national security level proprietary information need to be held legally accountable for its protection. Doing this will give the law the balance and weight it needs to be effective.
Recommendation: Amend the Espionage Act to include mandatory, pro-active, business counterespionage security requirements. ~Kevin
The centuries-old, lopsided, 'punish the spy' model of protecting intellectual property has never worked. (more) (more) Caretakers of national security level proprietary information need to be held legally accountable for its protection. Doing this will give the law the balance and weight it needs to be effective.
Recommendation: Amend the Espionage Act to include mandatory, pro-active, business counterespionage security requirements. ~Kevin
Labels:
advice,
business,
counterespionage,
FBI,
government,
historical,
law,
mores,
trade secret
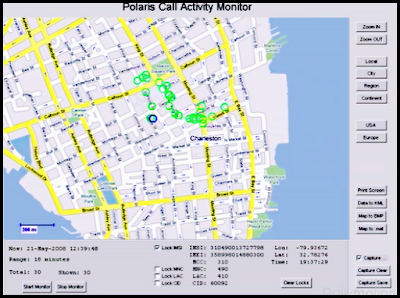
Cell Phone Tracking Insight - You're In Sight
This week at the CTIA show in New Orleans, Polaris Wireless unveiled Altus Mobile, an application that lets law-enforcement personnel track suspects via their cellphone numbers or mobile equipment identifier — a 56-bit identification number that is burned into the device and is extremely difficult to modify. The application leverages Polaris’s Wireless Location Signatures platform, which simultaneously can locate all subscriber devices on a wireless network, both in real time and historically.
That means law-enforcement officers will know where a suspect is, where he has been and where he is heading at any given moment, said Mahesh Patel, Polaris’s senior vice president of products and technology.
“Previously, this information was available to them on their desktops through our Altus surveillance solution, but now officers can take this information into the field with them,” Patel said. “Real-time access to this kind of intelligence will be a big plus for tactical operations.” (more)
“Previously, this information was available to them on their desktops through our Altus surveillance solution, but now officers can take this information into the field with them,” Patel said. “Real-time access to this kind of intelligence will be a big plus for tactical operations.” (more)
Verizon Mates With Cellcrypt - Bet You Can't Hear Me Now
UK mobile security firm Cellcrypt is partnering with carrier giant Verizon to sell its voice encryption technology for mobiles and smartphones to the US Government, the pair have announced.
Already in testing with unnamed US Government departments the service will be formally released later in 2012 as a co-branded product that marks a major foot in the door for Cellcrypt.
Working on Android, iPhone and BlackBerrys, the company’s software encrypts GSM mobile, WiFi and satellite phone calls to FIPS 140-2 level between handsets running the same software, defeating the potential for man-in-the-middle eavesdropping. (more)
Already in testing with unnamed US Government departments the service will be formally released later in 2012 as a co-branded product that marks a major foot in the door for Cellcrypt.
Working on Android, iPhone and BlackBerrys, the company’s software encrypts GSM mobile, WiFi and satellite phone calls to FIPS 140-2 level between handsets running the same software, defeating the potential for man-in-the-middle eavesdropping. (more)
Wednesday, May 9, 2012
FBI - Beware of Software Update Messages when Traveling
Recent analysis from the FBI and other government agencies demonstrates that malicious actors are targeting travelers abroad through pop-up windows while establishing an Internet connection in their hotel rooms.
Recently, there have been instances of travelers' laptops being infected with malicious software while using hotel Internet connections. In these instances, the traveler was attempting to setup the hotel room Internet connection and was presented with a pop-up window notifying the user to update a widely-used software product. If the user clicked to accept and install the update, malicious software was installed on the laptop. The pop-up window appeared to be offering a routine update to a legitimate software product for which updates are frequently available.
The FBI recommends that all government, private industry, and academic personnel who travel abroad take extra caution before updating software products on their hotel Internet connection. (more)
Recently, there have been instances of travelers' laptops being infected with malicious software while using hotel Internet connections. In these instances, the traveler was attempting to setup the hotel room Internet connection and was presented with a pop-up window notifying the user to update a widely-used software product. If the user clicked to accept and install the update, malicious software was installed on the laptop. The pop-up window appeared to be offering a routine update to a legitimate software product for which updates are frequently available.
The FBI recommends that all government, private industry, and academic personnel who travel abroad take extra caution before updating software products on their hotel Internet connection. (more)
Spook Summer School Saturday
Spy School — a Tampa Bay History Center program specially designed for teens — will instruct youngsters about surveillance, information gathering and disguise
 Agents and experts will teach children ages 12 to 18, offering tips on how to enter the espionage career field.
Agents and experts will teach children ages 12 to 18, offering tips on how to enter the espionage career field.
The program costs $60 per student but history center members get a $5 discount. Spy School begins Saturday and offers a guided tour with curator Rodney Kite-Powell.
The Tampa Bay area might not seem like an obvious spy hub. But many retired FBI, CIA and military members live in the area, and one of the nation's more high-profile spy court cases unfolded in 2001 in a U.S. District Court in Tampa. Also, United States Special Operations Command is based in Tampa.
For information on Spy School, call (813) 675-8960 or email Jennifer Tyson, the center's assistant curator of education, at jtyson @tampabayhistorycenter .org. (more)
 Agents and experts will teach children ages 12 to 18, offering tips on how to enter the espionage career field.
Agents and experts will teach children ages 12 to 18, offering tips on how to enter the espionage career field. The program costs $60 per student but history center members get a $5 discount. Spy School begins Saturday and offers a guided tour with curator Rodney Kite-Powell.
The Tampa Bay area might not seem like an obvious spy hub. But many retired FBI, CIA and military members live in the area, and one of the nation's more high-profile spy court cases unfolded in 2001 in a U.S. District Court in Tampa. Also, United States Special Operations Command is based in Tampa.
For information on Spy School, call (813) 675-8960 or email Jennifer Tyson, the center's assistant curator of education, at jtyson @tampabayhistorycenter .org. (more)
P.S. This is part of the International Spy Museum's traveling road show, "Spies,
Traitors, Saboteurs: Fear and Freedom in America." One of the show's features are historical artifacts on loan from Murray Associates / Spybusters, LLC; an APL Badge and ID Card (1917) carried by
operatives of the American Protective League (APL) who spied on their
fellow Americans on behalf of the U.S. Justice Department during World
War I. (see them here)
Tuesday, May 8, 2012
Spybusters Tip #834 - Singing the Butt-Dialing Blues
Spybusters Tip #834 - Stop butt-dialing by using your phone's password feature.
Here's what happens when you don't...
Druggie butt-dials police. Busted.
T-Mobile's Butt Dialing commercial.
"Butt" Dialing Becoming A Problem For 911 Dispatchers.
T-Mobile's Butt Dialing commercial.
"Butt" Dialing Becoming A Problem For 911 Dispatchers.
Subscribe to:
Comments (Atom)