Is this The World’s Smallest Voice Recorder?
Specifications
TileRec by ATTO Digital
Ultra-small: ≈1.53”x1.53”x.02” (≈39 x 39 x 5 mm)
Record modes: Voice activated or continuous.
Storage capacity: 145 hours.
Format: 128 kbps CD Quality MP3.
Playback: Download files to any computer.
Battery “on time”: Up to 24 hours.
Battery charge time: 2 hours.
Housing: Sturdy aluminum case.
Operates with one on/off switch.
Cost: $59.80 Amazon
Voice recorders keep getting smaller and smaller.
However, If smallest means thin to you, yes there is a thinner one, the Edic-mini Tiny16+ A75…
1 mm thinner, 12 mm less wide, but double the length. And, at $345, six times the price. They also make one card-key sized (2.7 mm thin).

If by smallest you mean really, really thin…
You might want to consider the NAGRA Dollar Bill recorder that’s being
marketed to law enforcement instead. Thirty-one times as expensive as
the TileRec.
There are many slightly larger voice recorders that are still considered to be mini in size. Our search on eBay returned 1,809 results and over 2,000 on Amazon.
The prices on eBay ranged from $1.45 (with free shipping from China!) to $2,000. for the Edic-mini Tiny+ B76-150HQ. The Edic-mini Tiny+ being closest in size to the TileRec.
A Voice Recorder Manufacturer Speaks
Jang Sung-Churl, chief executive of electronics firm Auto Jungbo Co. Ltd., told Reuters
that covert recording devices “have been selling like hotcakes” …sales
of voice recorders so far this year (2019) have doubled to 80 devices
per day, Jang said as he forecast sales to also double this calendar
year to 1.4 billion won ($1,172,289).
Think about it. That's almost 30,000 devices sold per year... before the expected doubling of sales. And, he is only one manufacturer. An educated guess is that there are thousands of manufacturers around the world.
Accessibility + Affordability = Big Concerns.
Who Cares About Voice Recorder Size?
Lots of folks, for many and varied reasons…
- Sneaky people who want to eavesdrop.
- Sneaky people who want to entrap others.
- Anyone worried about covert surveillance.
- Local law enforcement detectives and Private Investigators. They might not have the budget necessary for a covert NAGRA Dollar Bill Recorder, but have the smarts to slap a TileRec between two one-dollar bills.
- Technical Surveillance Countermeasures (TSCM) Technicians whose job it is to find illegal, electronic surveillance devices.
It all boils down to these two things:
People hiding voice recorders, and… thwarting the people doing it.
Discovering Voice Recorders
Since the offense has the advantage let’s concentrate on the defense.
The average
covert voice recorder will either be carried by a person to record face
to face conversations or it will be hidden within
conversations-of-interest areas.
In-Person Recording Detection Tips
- Since frisking is probably out of
the question, assume you are being recorded.
Even if you could frisk,
results would be iffy; these voice recorders are tiny.
- At the outset of a conversation ask
the other person if they are recording you. Watch their reaction. Do
they overly protest, or fake anger?
If they say no but record anyway,
the recording’s value can be challenged. They lied, so maybe they also
faked, edited or doctored the recording.
- Also… Be professional. If you would not say it in a courtroom, don’t say it.
Big Red Flag – When someone tries to recreate a previous conversation with you.
Covert Recording Detection Tips
- Pay attention to your surroundings.
Who has access and when? Voice recorders need to be retrieved: to review
recordings and to recharge batteries.
- Avoid using the same area for all your sensitive conversations. Use various and unpredictable locations if possible.
- Conducting your own search for
surveillance devices is futile. An experienced eavesdropper will plant
one easy-to-find device. They know the search will stop at that point.
The harder-to-find device and it’s back-up will still be on the job.
Without proper training and instrumentation your success is unlikely.
-
For office and home office
situations an independent Technical Surveillance Countermeasures (TSCM)
sweep team should be employed. Have them conduct periodic due diligence debugging inspections.
In addition to searching for room audio and video surveillance devices
have them check your vehicles. Vehicle inspections also include a search
for GPS tracking devices.
TileRec Voice Recorder Detection Test
 Testing Our Defenses
Testing Our Defenses
Murray Associates conducted tests to determine the effectiveness of their detection
techniques on mini voice recorders.
TileRec was
difficult–but not impossible–to detect compared to other recorders
tested.
During a professional TSCM inspection the technician’s physical search is aided by an instrument called a Non-Linear Junction Detector (NLJD). This instrument can detect electronic surveillance devices, including mini voice recorders, active or dormant.
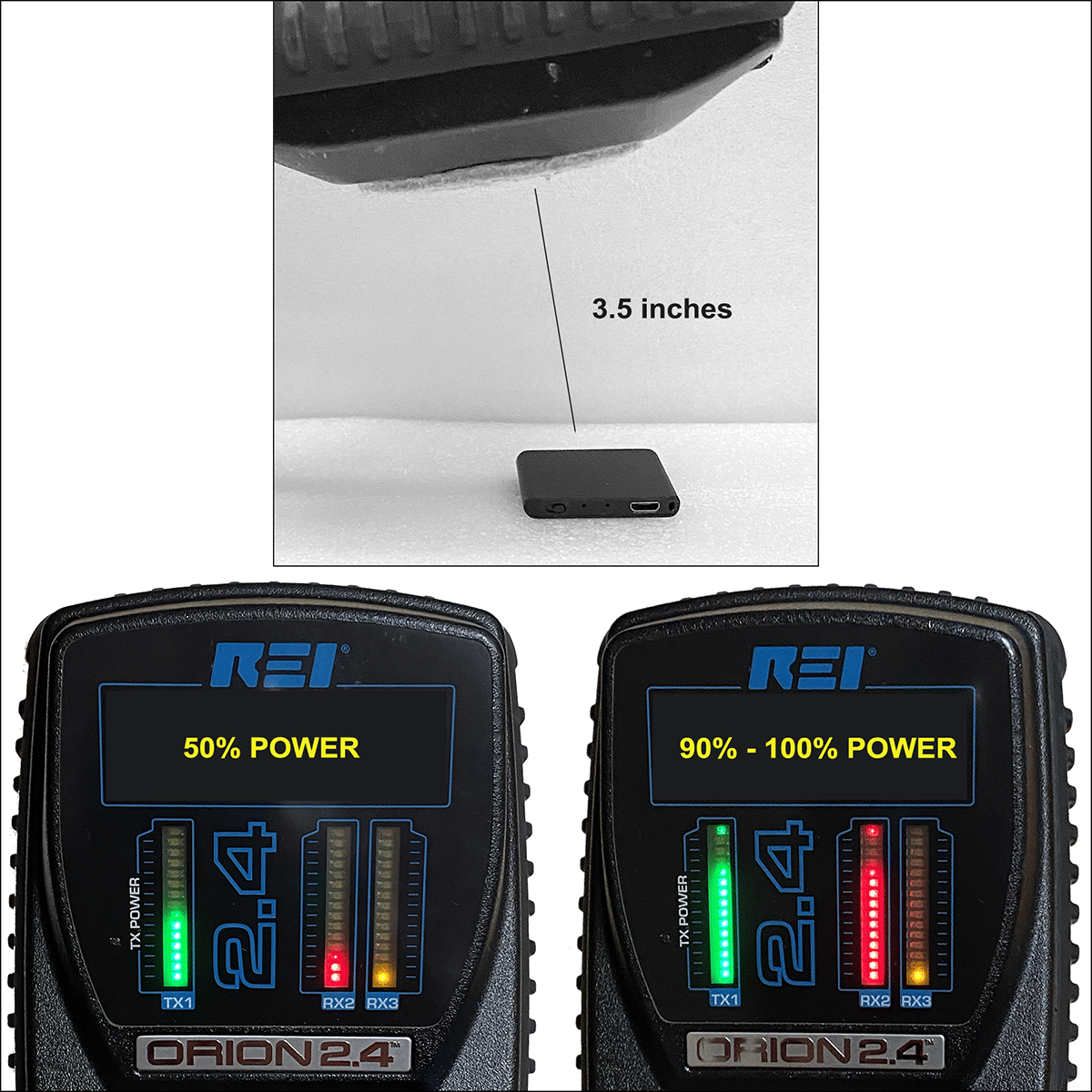
A distance
of 3 to 4 inches was chosen to test the NLJD detection technique. This
simulates the recorder being secreted within another object. Green shows the power output. Red shows the level of detection.
With the
NLJD set at 50% power output the TileRec was barely detectable. When the
power was increased to 90-100%, success. Even at this higher power
operator skill in using the NLJD was critical.
Conclusions
- The TileRec is (probably)
The World’s Smallest (affordable)
Voice Recorder (as of now).
- Size doesn’t matter. Any mini recorder can be easily secreted and threaten privacy.
- The market for mini recorders is huge. There are a lot of them out there. Some of the very good ones are very inexpensive.
- Detection is difficult, but not impossible.
- The best self-protection tactic is
watching what you say and situational awareness. Critical situations
require the assistance of a professional TSCM / counterespionage firm.
* * *
Kevin D.
Murray CPP, CISM, CFE is a business counterespionage consultant and TSCM
specialist with over four decades of experience.
Murray Associates
is an independent counterespionage consulting firm, providing eavesdropping
detection (TSCM) and counterespionage services to business, government and the
at-risk individual.
Headquartered in the New York metropolitan area, a Murray Associates
team can assist you quickly, anywhere in the United States, and
internationally.
If you have any questions, or would like to schedule TSCM / information security audits, please let us know.