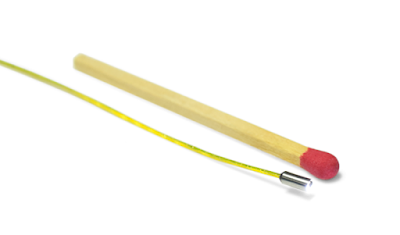
Specs: Color, 120 degree lens, 200 x 200 @ 30fps resolution
Wednesday, April 1, 2020
How Small Can a Video Camera Be?
Currently, one of the smallest we know is 1.66mm in size. It has a built-in high-intensity LED light. If you don't need the light it shrinks to .97mm in diameter.
Monday, March 30, 2020
Bosses Panic-Buy Spy Software...
... to keep tabs on remote workers.
“Companies have been scrambling,” said Brad Miller, CEO of surveillance-software maker InterGuard. “They’re trying to allow their employees to work from home but trying to maintain a level of security and productivity.”...
“It’s not because of lack of trust,” Miller said, who compared the software to banks using security cameras. “It’s because it’s imprudent not to do it.” more
“Companies have been scrambling,” said Brad Miller, CEO of surveillance-software maker InterGuard. “They’re trying to allow their employees to work from home but trying to maintain a level of security and productivity.”...
“It’s not because of lack of trust,” Miller said, who compared the software to banks using security cameras. “It’s because it’s imprudent not to do it.” more
Being Zoom'ed on Zoom has Organizations Worried, or they should be...
...experts warn that a rush to hold virtual meetings through
Zoom, which has close to 13m monthly active users, could pose security
risks.
The threat is so significant that British
Ministry of Defence staff were told this week that the use of Zoom was
being suspended with immediate effect while "security implications" were
investigated.
The biggest worry is that a sudden reliance on Zoom could allow
opportunistic hackers to quietly observe video calls as executives are
focused on responding to the spread of coronavirus.
...the idea of strangers barging into virtual meeting rooms should raise alarm. more
Online Zoom classes were disrupted by individuals spewing racist,
misogynistic or vulgar content. Experts say professors using Zoom should
familiarize themselves with the program's settings. more
Mysterious Hacker Group Eavesdropping on Corporate Email & FTP traffic
 Since at least early December 2019, a mysterious hacker group has been taking over DrayTek enterprise routers to eavesdrop on FTP and email traffic inside corporate networks...
Since at least early December 2019, a mysterious hacker group has been taking over DrayTek enterprise routers to eavesdrop on FTP and email traffic inside corporate networks...Instead of abusing the device to launch DDoS attacks or re-route traffic as part of a proxy network, the hackers turned into a spy-box...
...researchers didn't speculate why hackers were collecting FTP and email traffic. But speaking to ZDNet over the phone, a security researcher pointed out that this looked like a classic reconnaissance operation...
"It's obvious they're logging traffic to collect login credentials for FTP and email accounts," the researcher told ZDNet. "Those creds are flying unencrypted over the network. They're easy pickings." more
Tuesday, March 24, 2020
BBC Spycam Documentary
In a new BBC documentary Stacey Dooley Investigates: Spycam Sex Criminals.
The crime no doubt happens all over the world, but is actually one that has been sweeping South Korea lately, as many have been found guilty of planting recording equipment in public places and then charging people to view the footage online...
The upcoming documentary will see our fave reporter look into the subject head on to give us an insight into the voyeuristic practice and how now, with such advanced technology, it's easier than ever to hide cameras in public places.
Some of the cameras being used are as small as the head of a needle and are so difficult to spot, but Stacey will be taken on patrol with an experienced spy cam hunters to uncover hiding places.
Stacey Dooley Investigates: Spycam Sex Criminals will be available on iPlayer from 6am on 1st April - something to add to your quarantined watch list. more
The crime no doubt happens all over the world, but is actually one that has been sweeping South Korea lately, as many have been found guilty of planting recording equipment in public places and then charging people to view the footage online...
The upcoming documentary will see our fave reporter look into the subject head on to give us an insight into the voyeuristic practice and how now, with such advanced technology, it's easier than ever to hide cameras in public places.
Some of the cameras being used are as small as the head of a needle and are so difficult to spot, but Stacey will be taken on patrol with an experienced spy cam hunters to uncover hiding places.
Stacey Dooley Investigates: Spycam Sex Criminals will be available on iPlayer from 6am on 1st April - something to add to your quarantined watch list. more
Coronavirus Surveillance Escalates, Personal Privacy Plummets
Tracking entire populations to combat the pandemic now could open the doors to more invasive forms of government snooping later.
...government agencies are harnessing surveillance-camera footage, smartphone location data and credit card purchase records to help trace the recent movements of coronavirus patients and establish virus transmission chains...
...authorities are analyzing location data transmitted by citizens’ mobile phones to determine how many people are obeying a government lockdown order and the typical distances they move every day. About 40 percent are moving around “too much,” an official recently said.
...internal security agency is poised to start using a cache of mobile phone location data — originally intended for counterterrorism operations — to try to pinpoint citizens who may have been exposed to the virus...
...ratcheting up surveillance to combat the pandemic now could permanently open the doors to more invasive forms of snooping later. It is a lesson Americans learned after the terrorist attacks of Sept. 11, 2001, civil liberties experts say. more
...government agencies are harnessing surveillance-camera footage, smartphone location data and credit card purchase records to help trace the recent movements of coronavirus patients and establish virus transmission chains...
...authorities are analyzing location data transmitted by citizens’ mobile phones to determine how many people are obeying a government lockdown order and the typical distances they move every day. About 40 percent are moving around “too much,” an official recently said.
...internal security agency is poised to start using a cache of mobile phone location data — originally intended for counterterrorism operations — to try to pinpoint citizens who may have been exposed to the virus...
...ratcheting up surveillance to combat the pandemic now could permanently open the doors to more invasive forms of snooping later. It is a lesson Americans learned after the terrorist attacks of Sept. 11, 2001, civil liberties experts say. more
8 Steps to Control Cybersecurity Risk in a Work From Home Environment
During the COVID-19 pandemic and response, workers are heading home in record numbers. In this short 23-min. webinar, CI Security CTO Mike Simon covers the the critical work-from-home cybersecurity risks that employees need help with now.
The material is geared toward InfoSec and IT professionals, technical users, and team managers.
Top 8 Work From Home (WFH) Cybersecurity Priorities...
Step 1: Control the WFH Environment
Step 2: Control the WFH Computer
Step 3: Up Your Phishing Game
Step 4: Worry About Sensitive Documents and Regulated Data
Step 5: Watch for Cyber-Threats
Step 6: Expanding VPN
Step 7: Say No to Split-Tunnels
Step 8: Keep Great Records
The material is geared toward InfoSec and IT professionals, technical users, and team managers.
Top 8 Work From Home (WFH) Cybersecurity Priorities...
Step 1: Control the WFH Environment
Step 2: Control the WFH Computer
Step 3: Up Your Phishing Game
Step 4: Worry About Sensitive Documents and Regulated Data
Step 5: Watch for Cyber-Threats
Step 6: Expanding VPN
Step 7: Say No to Split-Tunnels
Step 8: Keep Great Records
Saturday, March 21, 2020
Remote Work, Security & Is Your Office Being Bugged While You're Home
It's a rule of thumb in cybersecurity that the more sensitive your system, the less you want it to touch the internet. But as the US hunkers down to limit the spread of Covid-19, cybersecurity measures present a difficult technical challenge to working remotely for employees... In some cases, working from home isn't an option at all...
Late last week, the US government's Cybersecurity and Infrastructure Security Agency issued an advisory to critical infrastructure companies to prepare for remote work scenarios as Covid-19 spreads...
But cybersecurity consultants who actually work with those high-stakes clients—including electric utilities, oil and gas firms, and manufacturing companies—say that it's not always so simple. For many of their most critical customers, and even more so for intelligence agencies, remote work and security don't mix. more
Special note to the business community...
Planting bugs is easy when your offices are empty. Business espionage types know this.
Quality TSCM sweep teams will be in demand and hard to book when Covid-19 subsides. Prepare now. Put your team on retainer.
If you don't have a quality provider contact us. We'll create a back-to-work inspection strategy, and a no-obligation estimate for you. ~Kevin
Late last week, the US government's Cybersecurity and Infrastructure Security Agency issued an advisory to critical infrastructure companies to prepare for remote work scenarios as Covid-19 spreads...
But cybersecurity consultants who actually work with those high-stakes clients—including electric utilities, oil and gas firms, and manufacturing companies—say that it's not always so simple. For many of their most critical customers, and even more so for intelligence agencies, remote work and security don't mix. more
Special note to the business community...
Planting bugs is easy when your offices are empty. Business espionage types know this.
Quality TSCM sweep teams will be in demand and hard to book when Covid-19 subsides. Prepare now. Put your team on retainer.
If you don't have a quality provider contact us. We'll create a back-to-work inspection strategy, and a no-obligation estimate for you. ~Kevin
Quote of the Week
"Organizations' ham-fisted operational changes due to the novel
Coronavirus will create a field day for practitioners of
espionage--industrial and otherwise."
(Sent to me by a knowledgeable source.)
(Sent to me by a knowledgeable source.)
Surveillance App Reworked for Coronavirus Alerts
Health officials in Britain are building an app that would alert the
people who have come in contact with someone known to have the
coronavirus. The project aims to adapt China’s tracking efforts for
countries wary of government surveillance.
The project is an urgent effort by the British authorities to translate a surveillance tool deployed to fight China’s outbreak into something more palatable in Western democracies. The app is being developed for use in Britain, but could be adapted for other countries, particularly those with similarly centralized health systems, officials said.
The catch... Unlike the smartphone-tracking system used by the Chinese government, the British project would rely entirely on voluntary participation and would bank on people sharing information out of a sense of civic duty. more
The project is an urgent effort by the British authorities to translate a surveillance tool deployed to fight China’s outbreak into something more palatable in Western democracies. The app is being developed for use in Britain, but could be adapted for other countries, particularly those with similarly centralized health systems, officials said.
The catch... Unlike the smartphone-tracking system used by the Chinese government, the British project would rely entirely on voluntary participation and would bank on people sharing information out of a sense of civic duty. more
Friday, March 20, 2020
Will Working from Home Increase Business Espionage Opportunities
I received a question today about inductive coupling; gleaning computer data leaked on to power lines (aka, mains) from keyboards, screens, etc. The person mentioned this was possible if the residences shared the same power transformer.
"So, does the increase in work-from-home offices these days increase the business espionage threat?"
Interesting question. Got me thinking.
I replied...
You're correct about sharing a transformer. Information can be induced onto the mains and intercepted on that side of the circuit. Several floors in an apartment building and usually 3-4 homes in a residential neighborhood can share one transformer.
But, let's think this through...
Back before we all became computerized the mains lines were relatively noise-free. Carrier-current bugs and wireless intercoms worked quite well for transmitting audio. These days, the noise level is a digital cacophony, created by everyone who shares the circuit.
The very low signal level a keyboard might contribute would be difficult to hear. Segregating the signal from other digital noise would also be a challenge. With diligence and the right instrumentation deciphering this digital data is doable. It would not be a nosy neighbor doing this. If you got that far, you're probably a government and the home worker has a bigger than average problem.
Realistically speaking...
A fairly static group of mains users also reduces risk. Your neighbors aren't deep cover spies who have waited years for the chance you might be forced to work from home. Moving into a neighborhood or apartment building with spying intentions is possible, but not easy to do on a moments notice. There are easier ways to obtain even more information, with a lot less work, and greater chance of success.
Worry about these things...
The weak links in a home office are: the computer, wireless keyboards, Wi-Fi, and internet modems. Current versions of wireless keyboards use Bluetooth (30 foot range) with some pretty good security features. As for date leaking onto the mains... Most smart people use a UPS battery backup with filtering for their computers, so no problem there. For anyone without a UPS getting one is a very worthwhile recommendation for multiple reasons.
Threats the average home office faces...
Imagine this...
Your company needs to have a technical security consultant on retainer—because there is more to know.
"So, does the increase in work-from-home offices these days increase the business espionage threat?"
Interesting question. Got me thinking.
I replied...
You're correct about sharing a transformer. Information can be induced onto the mains and intercepted on that side of the circuit. Several floors in an apartment building and usually 3-4 homes in a residential neighborhood can share one transformer.
But, let's think this through...
Back before we all became computerized the mains lines were relatively noise-free. Carrier-current bugs and wireless intercoms worked quite well for transmitting audio. These days, the noise level is a digital cacophony, created by everyone who shares the circuit.
The very low signal level a keyboard might contribute would be difficult to hear. Segregating the signal from other digital noise would also be a challenge. With diligence and the right instrumentation deciphering this digital data is doable. It would not be a nosy neighbor doing this. If you got that far, you're probably a government and the home worker has a bigger than average problem.
Realistically speaking...
A fairly static group of mains users also reduces risk. Your neighbors aren't deep cover spies who have waited years for the chance you might be forced to work from home. Moving into a neighborhood or apartment building with spying intentions is possible, but not easy to do on a moments notice. There are easier ways to obtain even more information, with a lot less work, and greater chance of success.
Worry about these things...
The weak links in a home office are: the computer, wireless keyboards, Wi-Fi, and internet modems. Current versions of wireless keyboards use Bluetooth (30 foot range) with some pretty good security features. As for date leaking onto the mains... Most smart people use a UPS battery backup with filtering for their computers, so no problem there. For anyone without a UPS getting one is a very worthwhile recommendation for multiple reasons.
Threats the average home office faces...
- shared cable internet,
- Wi-Fi signal hacking,
- spyware viruses (data, audio and video compromise),
- Wi-Fi connected printer intercepts,
- information phishing scams,
- and none of the usual enterprise type protections.
Imagine this...
- Step #1: The spy purchases a USB Rubber Ducky (to crack into the computer) and an o.mg cable (to crack into the smartphone). Total cost: <$200.00.
- Step #2: Spy plops these into an old Amazon box and mails it to "the mark."
- Step #3: Mark goes, "Wow, cool. I didn't order this. Amazon must have screwed up. Not worth sending back. I'll keep it."
- Step #4: Mark plugs this windfall into his computer and phone.
- Step #5: Gotcha!
Your company needs to have a technical security consultant on retainer—because there is more to know.
Thursday, March 19, 2020
Face Masks v. Facial Recognition - China has it Covered
Hanwang, the facial-recognition company that has placed 2 million of its cameras at entrance gates across the world, started preparing for the coronavirus in early January.
Huang Lei, the company’s chief technical officer, said that even before the new virus was widely known about, he had begun to get requests...to update its software to recognize nurses wearing masks...
The company now says its masked facial recognition program has reached 95 percent accuracy in lab tests, and even claims that it is more accurate in real life, where its cameras take multiple photos of a person if the first attempt to identify them fails. more
Huang Lei, the company’s chief technical officer, said that even before the new virus was widely known about, he had begun to get requests...to update its software to recognize nurses wearing masks...
The company now says its masked facial recognition program has reached 95 percent accuracy in lab tests, and even claims that it is more accurate in real life, where its cameras take multiple photos of a person if the first attempt to identify them fails. more
The Best Way to Sumggle a Filing Cabinet of Secrets
An American citizen will spend the next four or so years behind bars in the US for smuggling corporate secrets out of the states to his spymasters in China.
A federal district judge this week sentenced Xuehua Edward Peng, 56, of Hayward, California, after he admitted handing over the trade secrets to Beijing. Peng earlier confessed that SD cards loaded with information stolen from an unspecified US company were left for him to collect at hotels by a contact only known as Ed.
Peng would also hide tens of thousands of dollars in hotel rooms for Ed to collect as payment. Lawyers said Peng spent years trafficking confidential info. more
Flashback to 2009 when we made a point about this vulnerability...
A federal district judge this week sentenced Xuehua Edward Peng, 56, of Hayward, California, after he admitted handing over the trade secrets to Beijing. Peng earlier confessed that SD cards loaded with information stolen from an unspecified US company were left for him to collect at hotels by a contact only known as Ed.
Peng would also hide tens of thousands of dollars in hotel rooms for Ed to collect as payment. Lawyers said Peng spent years trafficking confidential info. more
Flashback to 2009 when we made a point about this vulnerability...
Tuesday, February 25, 2020
Schools Using Kids' Phones to Track and Surveil Them
Teachers often lament that phones can be a distraction in classrooms. Some governments have even banned phones outright in schools. But a few school administrations see phones in schools as a benefit because they can help keep track of students more efficiently.
At least 10 schools across the US have installed radio frequency scanners, which pick up on the Wi-Fi and Bluetooth signals from students' phones and track them with accuracy down to about one meter, or just over three feet, said Nadir Ali, CEO of indoor data tracking company Inpixon.
His company has been in talks with other school districts, and a few schools in the Middle East are also considering the product... more
At least 10 schools across the US have installed radio frequency scanners, which pick up on the Wi-Fi and Bluetooth signals from students' phones and track them with accuracy down to about one meter, or just over three feet, said Nadir Ali, CEO of indoor data tracking company Inpixon.
His company has been in talks with other school districts, and a few schools in the Middle East are also considering the product... more
Bathroom Spycam'er Gives GoPro A Whole New Meaning
A New Jersey teen's recent routine visit to a bookstore turned into a horrible nightmare when someone filmed her while she was inside a bathroom stall, according to prosecutors.
Juan Mejia, 44, of Paterson was arrested on Wednesday at the Barnes & Noble bookstore in Clifton after he secretly videotaped two separate women who were using the bathroom stalls, according to the Passaic County Prosecutor's Office.
The incident happened when her teen daughter said she had to use the bathroom. So, Delaney said, she went upstairs to help her own mother find a book.
Shortly after getting upstairs, Delaney said, her phone "started going off like crazy."
It was her daughter "texting me that someone in the stall next to her was filming her with a GoPro, that she was scared, and to please find someone and help her," Delaney wrote.
 Barnes & Noble issued a statement, saying the company was "disturbed" to learn of the incident... more
Barnes & Noble issued a statement, saying the company was "disturbed" to learn of the incident... more
"Disturbed" is not the right response. Every business offering toilet, shower and/or changing facilities needs this.
Juan Mejia, 44, of Paterson was arrested on Wednesday at the Barnes & Noble bookstore in Clifton after he secretly videotaped two separate women who were using the bathroom stalls, according to the Passaic County Prosecutor's Office.
The incident happened when her teen daughter said she had to use the bathroom. So, Delaney said, she went upstairs to help her own mother find a book.
Shortly after getting upstairs, Delaney said, her phone "started going off like crazy."
It was her daughter "texting me that someone in the stall next to her was filming her with a GoPro, that she was scared, and to please find someone and help her," Delaney wrote.
 Barnes & Noble issued a statement, saying the company was "disturbed" to learn of the incident... more
Barnes & Noble issued a statement, saying the company was "disturbed" to learn of the incident... more"Disturbed" is not the right response. Every business offering toilet, shower and/or changing facilities needs this.
Subscribe to:
Comments (Atom)