Thursday, July 24, 2025
FutureWatch: As You Distort Wi-Fi Space You Become Identifiable
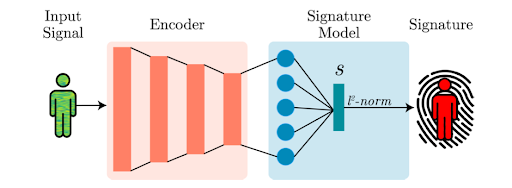
Researchers in Italy have shown that even ordinary Wi-Fi signals can be used to track people, without needing them to carry any device at all.
A team from La Sapienza University of Rome has developed a system called ‘WhoFi,’ which can generate a unique biometric identifier based on how a person’s body interacts with surrounding Wi-Fi signals. WhoFi can identify people within a Wi-Fi area with an accuracy of 95.5%.
The approach, described in a preprint paper, uses signal distortions caused by the human body to re-identify individuals as they move across spaces covered by different Wi-Fi networks.
More information: Danilo Avola et al, WhoFi: Deep Person Re-Identification via Wi-Fi Channel Signal Encoding, arXiv (2025). DOI: 10.48550/arxiv.2507.12869
Thursday, May 22, 2025
Going Away This Holiday Weekend? Hide Your Stuff
A bold thief made off with a $25,000 Jet Ski in broad daylight Wednesday, and the crime was caught on doorbell camera.
Friday, August 2, 2024
Voice Over Wi-Fi Vulnerability Let Attackers Eavesdrop Calls And SMS
This process consists of two main phases: negotiation of encryption parameters and performing a key exchange using the Internet Key Exchange protocol, followed by authentication....
These findings highlight the systemic flaws in the implementation of VoWiFi, which could make users vulnerable to man-in-the-middle attacks, and communication security is compromised on a global scale, consequently requiring better security measures in VoWiFi protocols and implementations. more
Sunday, February 11, 2024
AI Wi-Fi CCTV - Spooky
The signals from WiFi can be used to map a human body, according to a new paper.
Thursday, February 1, 2024
FutureWatch: New Wi-Fi Tech Has Potential Spy Applications
The company is sampling its Wi-Fi Alliance and FCC-certified MM6108 production silicon – the fastest, smallest, lowest power and longest-range Wi-Fi HaLow SoC available in the market. more
Friday, March 17, 2023
Getting Clocked Can Disable Your Wi-Fi Cameras
Watch Functions
- Deauther Attack: Disconnect 2.4G WiFi
- Deauther Beacon: Create fake networks
- Deauther Probe: Confuse Wi-Fi trackers
- Packet Monitor: Display Wi-Fi traffic
- Kicks devices off a WiFi network- Spam beacon frames
- Spam probe requests
Additional background information about deauthentication attacks via Atlas VPN...
A deauth or deauthentication attack (DoS) disrupts connections between users and Wi-Fi access points. The attackers force devices to lose access and then reconnect to a network they control. Then, perpetrators can track connections, capture login details, or trick users into installing rogue programs... this attack does not need unique skills or elaborate equipment. Deauth attacks could also knock devices offline, like home security software.
How it it Used?
• Forcing hidden cameras to go offline. Over the years, frequent disputes forced Airbnb to forbid the use of cameras in rented apartments or rooms. Yet, more cunning homeowners can conceal cameras from their guests.
• Hotels that push paid Wi-Fi. There have been incidents when hotels employed deauthentication attacks to promote their Wi-Fi services. In fact, the Federal Communications Commission (FCC) issued documents stating that blocking or interfering with Wi-Fi hotspots is illegal. One of the first offenders was the Marriott hotel, with financial motives for disrupting visitors’ access points. However, charging perpetrators with deauthentication attacks is a rare sight. Usually, victims might blame the interruptions on unstable Wi-Fi.
• Susceptible smart devices. Criminals could push connected devices offline for several reasons. One danger is that attackers might disable security systems. Thus, such interruption halts monitoring of the home, office, or another area. In worst-case scenarios, such deauth attacks could facilitate burglars entering buildings. Another example comes from a vulnerability in Ring Video Doorbell Pro (now fixed). The exploited flaw means using a Wi-FI deauthentication attack to force the device to re-enter the configuration mode. Then, eavesdroppers can capture Wi-Fi credentials orchestrated to travel in an unencrypted HTTP.
• Forcing users to join evil twins. Spoofed deauthentication frames force targeted devices to drop their connection. It could be a way to break the legitimate connection and trick users into joining fake hotspots. Deauth attacks could flood the access point so that devices cannot join for a period of time.
Our Tips: How to Make Sure They Don't Disable Your WiFi Cameras
Tip 1. Don't go wireless, use Cat6a shielded cable.
Tip 2. Use Power over Ethernet (PoE). Make sure it is properly grounded.
Tip 3. Make sure the power supply to the network is backed-up (UPS). Power failures do happen.
Tip 4. Hide the cables to deter sabotage.
Tip 5. If you absolutely, positively need a wireless video solution consider using a 4G cellular camera, or a dedicated video link.
WiFi Camera Attack Prevention
The prevention of deauthentication attacks does not offer many options. But there are effective strategies for mitigating their impact. Ensure that your network applies WPA2 encryption. If you use a pre-shared key, it must be complex and lengthy to withstand threats like brute-force attacks. Another improvement might be 802.11w, which validates deauthentication frames and discards spoofed ones. Older hardware and IoT might not support it, raising issues for some Wi-Fi clients.
Furthermore, remember you have minimal control over free public Wi-Fi and its security.
A VPN can assist if deauthentication attacks force clients to connect to evil twins. Atlas VPN creates a secure path between users and access points. Encrypted traffic will prevent attackers from capturing any meaningful communications or data. more
Thursday, August 18, 2022
Apple AirTag: All Things Technical
Privacy Concerns (brief summary below)
While it is possible to use other products similar to AirTag to track people, they cannot benefit from the unmatched global coverage of the FindMy network. This makes the AirTag a more appealing device to people with malicious intent and so privacy features are important.
Let’s look at how reality compares to the claims Apple makes about the AirTag privacy features when the known security issues are considered.
- Sound alerts are infrequent and unlikely
- Speaker can be disabled
- Location can be tracked for the whole day
- Location can be spoofed
- “AirTag Found Moving With You” alert can be avoided
- Location history could be decrypted
Thursday, May 26, 2022
New Countermeasure Against Unwanted Wireless Surveillance
To prevent possible surveillance of the movement profile within one’s home, researchers from the Max Planck Institute for Security and Privacy, the Horst Görtz Institute for IT Security at Ruhr-Universität Bochum and the Cologne University of Applied Sciences have developed a novel system for protecting privacy in wireless communication.
Almost all Internet-of-Things devices, such as voice assistants, locks and cameras, rely on wireless connections based on high-frequency radio signals... passive eavesdroppers can still exploit sensitive information from intercepted radio frequency signals... Attackers can perceive such effects from a distance and, by applying simple statistical methods, conclude, for example, that a person is currently moving in the monitored room... this method known as “adversarial wireless sensing”...
With their approach, the researchers are the first in the world to propose IRS as a practical countermeasure against passive wireless eavesdropping attacks. more
Thursday, September 23, 2021
Reasons You Should Never Connect To Public Wifi
There Are Too Many Risks
Put simply, the risks you take when you connect to Wifi in public places such as libraries, stations, cafes, and shopping malls are often too great to make the benefits worthwhile...
- Misuse of personal data Distribution of malware
- Insecure connection
- Online attacks on business
- Eavesdropping
Hackers or anyone with a sound knowledge about internet software and applications can eavesdrop on your personal data if they are using the same public Wi-Fi connection as you are...
- Try not to share your personal data while you are using a personal Wi-Fi connection.
- Avoid logging in to websites that involve your personal or bank credentials.
- Try using a VPN (virtual Private Network) service that will help you to encrypt all the data you receive or send.
- Use 2-Factor authorizations that will make your connection secure and prevent the risk of data loss.” more
Friday, October 9, 2020
The FBI Hotel Wi-Fi Security Checklist
The Federal Bureau of Investigation is issuing this announcement to encourage Americans to exercise caution when using hotel wireless networks (Wi-Fi) for telework. FBI has observed a trend where individuals who were previously teleworking from home are beginning to telework from hotels.
US hotels, predominantly in major cities, have begun to advertise daytime room reservations for guests seeking a quiet, distraction-free work environment. While this option may be appealing, accessing sensitive information from hotel Wi-Fi poses an increased security risk over home Wi-Fi networks.
Malicious actors can exploit inconsistent or lax hotel Wi-Fi security
and guests’ security complacency to compromise the work and personal
data of hotel guests. Following good cyber security practices can
minimize some of the risks associated with using hotel Wi-Fi for
telework. more
Wednesday, April 1, 2020
Guest Wi-Fi Access Comes with Risks for Organizations
In this case, a stolen access code was used to gain access. In many organizations the same guest code is given out to all guests. Sometimes it is even posted. Often it is never changed. Once the password is out, there is no telling who will access the system, or when, or for what purpose.
Downloading illegal images is only one of many guest access risks.
While hiding behind a reputable IP address unauthorized and anonymous "guests" can also conduct: drug transactions, video voyeurism, blackmail, financial scams, hacking, and more. The finger points at the organization's network. They might be legally held responsible. And, these are just the outward facing threats. Guest access can also be a pivot point to internal information theft.
Take this 15 second assessment.
Does your organization...
- Provide guest Wi-Fi access?
- Does guest access use the organization's network?
- Is access unencrypted?
- Do all guests use the same password?
- Is the password posted anywhere, as in a conference room?
- If posted, can it be seen from outside with binoculars or a drone?
- Has the password remained the same for over a month?
Legal defense is expensive. Reputational damage is hard to quantify. A proactive professsional analysis is easy. Reduce risk and keep profits where they belong, in the bottom line.
Friday, October 18, 2019
IT / Security Director Alert: Cisco Aironet Wi-Fi High-Severity Vulnerability Patch Available
 It also issued a slew of additional patches addressing other flaws in its products.
It also issued a slew of additional patches addressing other flaws in its products. “An exploit could allow the attacker to gain access to the device with elevated privileges,” said Cisco in a Wednesday advisory.
“An exploit could allow the attacker to gain access to the device with elevated privileges,” said Cisco in a Wednesday advisory. "...it could allow the attacker to view sensitive information and replace some options with values of their choosing, including wireless network configuration. It would also allow the attacker to disable the [access point], creating a denial of service (DoS) condition for clients associated with the [access point].” more
Tuesday, September 10, 2019
FutureWatch - Non-Public 5G Networks - Network Security via Isolation
Non-public 5G networks offer protection against industrial espionage. Data in non-public 5G networks is segregated and processed separately from public 5G networks. This ensures complete privacy protection of process -- and production-related data. more
Friday, August 23, 2019
The O.MG Cable™ — The Smartphone Electro-Leach
 The O.MG Cable™ is the result of months of work that has
resulted in a highly covert malicious USB cable. As soon as the cable is
plugged in, it can be controlled through the wireless network interface
that lives inside the cable.
The O.MG Cable™ is the result of months of work that has
resulted in a highly covert malicious USB cable. As soon as the cable is
plugged in, it can be controlled through the wireless network interface
that lives inside the cable.Friday, August 9, 2019
Warshipping - The Next Corporate Espionage Headache
Instead, writes Charles Henderson, global head of that security unit, they could simply ship you a package with a tiny, concealed device they can remotely control.
“In fact, they could ship multiple devices to their target location thanks to low build cost,” Henderson writes. “The device, a 3G-enabled, remotely controlled system, can be tucked into the bottom of a packaging box or stuffed in a toy (a device no bigger than the palm of your hand) and delivered right into the hands or desk of an intended victim.”...
 |
| Scheduled TSCM inspections find electronic surveillance items like this. Dead or alive. |
To avoid such attacks, Henderson’s team recommends companies set up policies to inspect and isolate packages and potentially discourage employees from getting personal shipments at work. more
Tuesday, July 23, 2019
Google: Wi-Spy Case Cashed Out
Thursday, February 7, 2019
Smart Light Bulbs May Not Be a Bright Idea
Not to mention, someone replacing your bulb and getting the password that way.
Yes, I know, the spy might not program the replacement bulb to operate like the old one. Dead give-a-way, right? My bet is that you'll think the bulb just forgot it's settings, or not notice at all.
This hack was publicized here, and originally researched here, if you want to know more.
Thanks to our Blue Blaze Irregular from the Jersey shore for this one.
Friday, November 2, 2018
Security Director IT Alert: New Corporate Network Attack Vulnerability
Two zero-day vulnerabilities in Bluetooth Low-Energy chips made by Texas Instruments (and used in millions of wireless access points) open corporate networks to crippling stealth attacks.
Adversaries can exploit the bugs by simply being approximately 100 to 300 feet from the vulnerable devices. A compromised access point can then lead to an attacker taking control of the access point, capturing all traffic, and then using the compromised device as a springboard for further internal attacks.
 The issue impacts Wi-Fi access points made by Cisco, Cisco Meraki and Hewlett-Packard Enterprise’s Aruba, accounting for a large percentage of hardware used in corporations, according to researchers at Israeli security firm Armis. The firm discovered the two bugs earlier this year and publicly disclosed them on Thursday.
The issue impacts Wi-Fi access points made by Cisco, Cisco Meraki and Hewlett-Packard Enterprise’s Aruba, accounting for a large percentage of hardware used in corporations, according to researchers at Israeli security firm Armis. The firm discovered the two bugs earlier this year and publicly disclosed them on Thursday. “Attacks can be devastating and carried out by unauthenticated users who can exploit these bugs and break into enterprise networks undetected while sitting in the company’s lobby,” said Ben Seri, head of research at Armis.
...there is concern that the BleedingBit vulnerabilities could impact a larger universe of BLE devices, such as smart locks used in hotel chains and point-of-sale hardware.
Last year, Armis discovered a nine zero-day Bluetooth-related vulnerabilities, dubbed BlueBorne, in Bluetooth chips used in smartphones, TVs, laptops and car audio systems. The scale of affected devices was massive, estimated to impact billions of Bluetooth devices. more
Recommendation: If your company uses devices made by the manufacturers mentioned, contact them for software patches. ~Kevin
Wednesday, October 3, 2018
Have Xfinity? Your Wi-Fi is Scared
 "In addition to saying “Help” into your Voice Remote, you can directly ask for what you need. For example, say “What’s my WiFi password?”
and your WiFi network name and password will show up on the tv screen.
"In addition to saying “Help” into your Voice Remote, you can directly ask for what you need. For example, say “What’s my WiFi password?”
and your WiFi network name and password will show up on the tv screen.Keep exploring your WiFi information and you will find different ways to manage your network, including viewing WiFi usage across devices in your home. You can also do this on-the-go with the Xfinty xFi app." more
Wi-Fi security is important, especially if you are using it in a business environment. ~Kevin
Friday, July 27, 2018
How Not to Write Your Name Electronically on Your Hotel Room Door