Nearly 4,000 federal and state wiretaps were authorized last year, an increase of 34 percent from the previous year, according to an annual government report.
The administrative office of the United States Courts released a report last month that found an all-time high of 3,194 wiretaps were reported as authorized in 2010 – 1,207 by federal judges and 1,987 by state judges – and only one application was denied...
Wiretap applications in California, New York and New Jersey accounted for 68 percent of all applications authorized by state judges, the study found... Drug offenses were cited most often for using wiretaps in investigations -- 84 percent of all applications were drug-related. Homicides came next, followed by racketeering.
The Electronic Privacy Information Center noted that the report does not include “interceptions regulated by the Foreign Intelligence Surveillance Act (FISA) or interceptions approved by the president outside the exclusive authority of the federal wiretap law and the FISA." (more)
Monday, August 22, 2011
SpyCam Story #617 - Bed & Breakfast, and a show
Australia - A landlord has pleaded guilty to indecently filming his tenants at bed and breakfast premises in Adelaide.
A court heard the man set up hidden cameras in smoke detectors and had been watching his victims for months.
Frederick Payne pleaded guilty to 18 counts of indecent filming. ...Payne, who is an electrician, installed cameras in smoke detectors in the master bedroom, and a bedroom used by the victim's daughter. ...the victim's boyfriend had discovered the cameras and they moved out of the Maslin Beach premises immediately.
Wires from the hidden cameras led to a television and DVD player in Payne's bedroom in the house he lived in next door. Police found hours of footage... (more)
A court heard the man set up hidden cameras in smoke detectors and had been watching his victims for months.
Frederick Payne pleaded guilty to 18 counts of indecent filming. ...Payne, who is an electrician, installed cameras in smoke detectors in the master bedroom, and a bedroom used by the victim's daughter. ...the victim's boyfriend had discovered the cameras and they moved out of the Maslin Beach premises immediately.
Wires from the hidden cameras led to a television and DVD player in Payne's bedroom in the house he lived in next door. Police found hours of footage... (more)
Media Wiretapping did not start with News of the World
How far would the media of the time go for a story or some inside information?
The FBI of the 1930s was concerned about newspapers and magazine personnel tapping the telephones of FBI Offices, especially the Chicago Division.
In this 1935 memo from E. A. Tamm, these fears are set out with efforts of the Bureau to code their conversations to thwart the Chicago American, and also to purposely "test" the system.
 According to the Encyclopedia Of Chicago website, "In 1900, Chicago had nine general circulation newspapers when William Randolph Hearst's sensationalistic evening Chicago American appeared, followed by his morning Chicago Examiner (1902). The American upheld the raucous Hearstian/Chicago tradition of “The Front Page,” even after it was sold to the Chicago Tribune in 1956, renamed Chicago Today, and turned into a tabloid. Today died in 1974. The morning Examiner became the Herald-Examiner in 1918 and died in 1939, never able to overtake the Tribune." (more)
According to the Encyclopedia Of Chicago website, "In 1900, Chicago had nine general circulation newspapers when William Randolph Hearst's sensationalistic evening Chicago American appeared, followed by his morning Chicago Examiner (1902). The American upheld the raucous Hearstian/Chicago tradition of “The Front Page,” even after it was sold to the Chicago Tribune in 1956, renamed Chicago Today, and turned into a tabloid. Today died in 1974. The morning Examiner became the Herald-Examiner in 1918 and died in 1939, never able to overtake the Tribune." (more)
The FBI 1935 Tamm memo – taken from the Dillinger file.
The FBI of the 1930s was concerned about newspapers and magazine personnel tapping the telephones of FBI Offices, especially the Chicago Division.
In this 1935 memo from E. A. Tamm, these fears are set out with efforts of the Bureau to code their conversations to thwart the Chicago American, and also to purposely "test" the system.
 According to the Encyclopedia Of Chicago website, "In 1900, Chicago had nine general circulation newspapers when William Randolph Hearst's sensationalistic evening Chicago American appeared, followed by his morning Chicago Examiner (1902). The American upheld the raucous Hearstian/Chicago tradition of “The Front Page,” even after it was sold to the Chicago Tribune in 1956, renamed Chicago Today, and turned into a tabloid. Today died in 1974. The morning Examiner became the Herald-Examiner in 1918 and died in 1939, never able to overtake the Tribune." (more)
According to the Encyclopedia Of Chicago website, "In 1900, Chicago had nine general circulation newspapers when William Randolph Hearst's sensationalistic evening Chicago American appeared, followed by his morning Chicago Examiner (1902). The American upheld the raucous Hearstian/Chicago tradition of “The Front Page,” even after it was sold to the Chicago Tribune in 1956, renamed Chicago Today, and turned into a tabloid. Today died in 1974. The morning Examiner became the Herald-Examiner in 1918 and died in 1939, never able to overtake the Tribune." (more)The FBI 1935 Tamm memo – taken from the Dillinger file.
Saturday, August 20, 2011
Caller ID Spoofing and Your Privacy
via The New York Times...
For all of the palace intrigue recently about who in Rupert Murdoch’s News Corporation kingdom knew what about phone hacking when, one fundamental question about the scandal has gone mostly unanswered: Just how vulnerable are everyday United States residents to similarly determined snoops? The answer is, more than you might think.
AT&T, Sprint and T-Mobile do not require cellphone customers to use a password on their voice mail boxes, and plenty of people never bother to set one up. But if you don’t, people using a service colloquially known as caller ID spoofing could disguise their phone as yours and get access to your messages. This is possible because voice mail systems often grant access to callers who appear to be phoning from their own number.
Meanwhile, as Edgar Dworsky, a consumer advocate who founded ConsumerWorld.org, discovered recently, someone armed with just a bit of personal information about a target can also gain access to the automated phone systems for Bank of America and Chase credit card holders. (more)
Friday, August 19, 2011
So, what are your "friends" saying about you?
 |
| The real Banjo |
Banjo, for those unaware, is a new social discovery service which reveals the social network present at any given location at a particular time. To be clear, it’s not another social network, it’s a layer on top of social networks. With Banjo, you don’t have to create a profile, add friends or collect followers, or perform any of the other typical social networking behaviors.
Instead, to use Banjo, you simply launch the app to see what the people around you are saying and doing right now. The app pulls its data from social networking services like Facebook, Twitter, Foursquare, Gowalla, TwitPic and Instagram, accessing both the publicly available check-ins and the geotags that accompany status updates and posts. (more) sing-a-long
From our no free lunch department - Smartphone Juice Jacking
It certainly seems innocent enough at first glance: a free charging kiosk at an airport, hotel or shopping mall.
Most people wouldn't hesitate to charge their dying smartphones - even though the kiosk could theoretically be configured to read most of the data on a device and upload malware.
To demonstrate the potential threat, Brian Markus, president of Aires Security, along with fellow researchers Joseph Mlodzianowski and Robert Rowley, built a juice jacking kiosk at Defcon 2011 to educate the masses about the risks associated with blindly plugging in mobile devices. (more)
Tip: This trick will not work on most devices if they are powered down entirely before charging.
Most people wouldn't hesitate to charge their dying smartphones - even though the kiosk could theoretically be configured to read most of the data on a device and upload malware.
To demonstrate the potential threat, Brian Markus, president of Aires Security, along with fellow researchers Joseph Mlodzianowski and Robert Rowley, built a juice jacking kiosk at Defcon 2011 to educate the masses about the risks associated with blindly plugging in mobile devices. (more)
Tip: This trick will not work on most devices if they are powered down entirely before charging.
Thursday, August 18, 2011
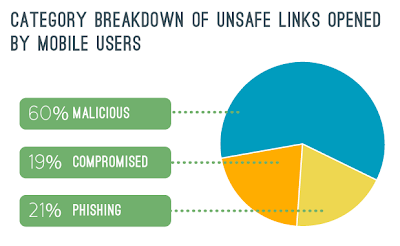
Free Mobile Phone Threat Report
Click on illustrations to enlarge...
Prepared by Lookout, "a smartphone security company dedicated to making the mobile experience safe for everyone."
News of the World Phone Hacking - Another Arrest
U.K. police arrested a 38-year-old man Thursday in connection with the ongoing investigation into alleged phone hacking by News Corp.'s now-closed News of the World tabloid.
View Interactive
More photos and interactive graphics
The arrest relates to the scandal stemming from allegations that the News of the World illegally intercepted the voice mails of celebrities, politicians and crime victims, through a practice known as phone hacking. Police also are probing possible police bribery by News of the World staff in exchange for information. The weekly tabloid was closed last month amid the scandal.
The arrested man couldn't immediately be identified. His marks the 13th arrest authorities have made since reopening their investigation into phone hacking in January. (more)
View Interactive
More photos and interactive graphics
The arrest relates to the scandal stemming from allegations that the News of the World illegally intercepted the voice mails of celebrities, politicians and crime victims, through a practice known as phone hacking. Police also are probing possible police bribery by News of the World staff in exchange for information. The weekly tabloid was closed last month amid the scandal.
The arrested man couldn't immediately be identified. His marks the 13th arrest authorities have made since reopening their investigation into phone hacking in January. (more)
Get in on the laptop privacy survey - Get free privacy software!
Oculis is running a mobile worker privacy survey to collect useful data about attitudes and experiences with display privacy. Their thesis is that display privacy is a significant security industry issue and that most people have strong but unfulfilled desires for a more private experience. They intend to use the results of the survey to generate new awareness with the press, and to answer typical customer questions about why end users need PrivateEye or Chameleon.
Take the survey and you receive a FREE license for their PrivateEye screen protector, a very cool piece of software that alerts you to shoulder surfers, and blurs your screen when you are not looking at it. How? The secret is your computer's camera. It watches your back and recognizes your face! (FAQs)
Take the survey and you receive a FREE license for their PrivateEye screen protector, a very cool piece of software that alerts you to shoulder surfers, and blurs your screen when you are not looking at it. How? The secret is your computer's camera. It watches your back and recognizes your face! (FAQs)
The survey link is: https://www.surveymonkey.com/s/OculisPrivacySurvey
Here are the preliminary results from a few selected questions:
The Most Extensive Radio and Technical Museum List
If you have an interest in antique radios, TVs, computers and other technical equipment, this is the list to bookmark. Over 100 radio and technical museums around the world. Sponsored by radiomuseum.org
FutureWatch Prediction Comes True - Tampa Redux
Tampa - "You are only a stranger here once."
August 2011 - The Tampa Police Department plans to circle its downtown area with surveillance cameras prior to the 2012 Republican National Convention, but Assistant Police Chief Mark Hamlin says the locations will not be disclosed in order to keep potential troublemakers from gaining a tactical advantage. A local political activist has publicly stated he is troubled by this decision.
September 2008 - FutureWatch - Although facial recognition and tracking didn't catch on the first go-around (the Tampa, Florida experiment), it is ripe for a come-back. 5 years from now, this will be commonplace – along with automatic license plate readers and motion-intention evaluators.
August 2003 - It is with sadness we note the demise of our favorite city motto... Tampa - "You're only a stranger here once." Tampa police have scrapped their controversial security camera system that scanned city streets for criminals, citing its failure over two years to recognize anyone wanted by authorities.
History - July 2001 - The Tampa City Council took a fully-informed look at Ybor City's controversial high-tech face-scanning software. When the dust settled, the council split down the middle with a 3-3 vote on whether or not to do away with the face-scanning software.
History - July 2001 - The Tampa City Council took a fully-informed look at Ybor City's controversial high-tech face-scanning software. When the dust settled, the council split down the middle with a 3-3 vote on whether or not to do away with the face-scanning software.
 |
| Tampa Police Radio Room c.1920's |
Wednesday, August 17, 2011
News of The World Spying - More Threads
UK - MPs have reignited the News of the World phone-hacking scandal with the publication of new documents which suggest News International was involved in a four-year cover-up.
The Guardian says Rupert Murdoch, James Murdoch and their former editor Andy Coulson "face embarrassing new allegations of dishonesty and cover-up after the publication of an explosive letter written by the News of the World's disgraced royal correspondent, Clive Goodman".
In the article by Nick Davies, who broke the original story, he says Goodman makes the following claims: "that phone hacking was 'widely discussed' at editorial meetings at the paper until Coulson himself banned further references to it; that Coulson offered to let him keep his job if he agreed not to implicate the paper in hacking when he came to court; and that his own hacking was carried out with 'the full knowledge and support' of other senior journalists, whom he named." (more)
The Guardian says Rupert Murdoch, James Murdoch and their former editor Andy Coulson "face embarrassing new allegations of dishonesty and cover-up after the publication of an explosive letter written by the News of the World's disgraced royal correspondent, Clive Goodman".
In the article by Nick Davies, who broke the original story, he says Goodman makes the following claims: "that phone hacking was 'widely discussed' at editorial meetings at the paper until Coulson himself banned further references to it; that Coulson offered to let him keep his job if he agreed not to implicate the paper in hacking when he came to court; and that his own hacking was carried out with 'the full knowledge and support' of other senior journalists, whom he named." (more)
News of The World Spying - Like Pulling a Sweater Thread
Revelations that U.K. tabloid journalists may have graduated to hacking computers in addition to mobile phones may form the next scandal facing Rupert Murdoch's News Corp., a U.K. lawmaker investigating privacy violations by the now-defunct News of the World said.
Police and parliament have mostly focused their probes on how journalists illegally accessed the voicemails of celebrities, politicians and crime victims, and who at the company knew about it. More revelations of computer hacking and other forms of spying could emerge, Tom Watson, a Labour Party lawmaker, said yesterday.
“My own concerns are that this will lead to other forms of covert surveillance, and I think the next scandal will be computer hacking and we're going to be living with this for weeks and months to come,” said Mr. Watson, who is also a member of the Culture, Media and Sport Committee that is investigating phone hacking. (more)
The News of The World case is slowly unraveling into a textbook case of corporate espionage, thus proving the reality of it. This is the tip of the iceberg. Only failed spying becomes headlines.
FutureWatch: Bugs, wiretaps, more bribes, blackmail and sex.
Police and parliament have mostly focused their probes on how journalists illegally accessed the voicemails of celebrities, politicians and crime victims, and who at the company knew about it. More revelations of computer hacking and other forms of spying could emerge, Tom Watson, a Labour Party lawmaker, said yesterday.
“My own concerns are that this will lead to other forms of covert surveillance, and I think the next scandal will be computer hacking and we're going to be living with this for weeks and months to come,” said Mr. Watson, who is also a member of the Culture, Media and Sport Committee that is investigating phone hacking. (more)
If you are not one of our clients, you may not know these espionage secrets...
• When you are a target, you won't be spied upon just using one method – a variety of tactics will be used.
• The reasons electronic surveillance is investigated first is because it is a common tactic, easy to discover, and must be eliminated before one starts accusing people directly.
• A successful counterespionage strategy will take all your vulnerabilities, and all their tactics into consideration.
Control Anything Cellular or WiFi in Your Enterprise
AirPatrol Corp. today unveiled ZoneDefense, a new mobile monitoring and policy enforcement technology that lets enterprises support the use of consumer and mobile devices on premises while also ensuring that end users are adhering to company security policies.
ZoneDefense is a security technology that can detect any mobile device in an enterprise, track its location, check its compliance with company policy and enforce rules based on where the user is located and who is nearby. (more)
In addition to the release of ZoneDefense, AirPatrol issued a new white paper that offers guidelines on implementing wireless security policies. For a free copy, click here.
Disclosure: I use AirPatrol technology in my counterespionage inspections, but do not profit in any way by bringing their products to your attention.
ZoneDefense is a security technology that can detect any mobile device in an enterprise, track its location, check its compliance with company policy and enforce rules based on where the user is located and who is nearby. (more)
In addition to the release of ZoneDefense, AirPatrol issued a new white paper that offers guidelines on implementing wireless security policies. For a free copy, click here.
Disclosure: I use AirPatrol technology in my counterespionage inspections, but do not profit in any way by bringing their products to your attention.
Labels:
business,
cell phone,
computer,
counterespionage,
leaks,
product,
spybot,
tracking,
Wi-Fi,
wireless
"Page Eight" - Modern Intelligence Practices Scrutinized
Canada - Spies and assassins will get moviegoers' adrenaline pumping at the Toronto International Film Festival this year...
The 10-day festival opens on September 8 and will close with David Hare's "Page Eight", a contemporary spy film that casts a critical eye on modern intelligence practices. (more) (synopsis)
The 10-day festival opens on September 8 and will close with David Hare's "Page Eight", a contemporary spy film that casts a critical eye on modern intelligence practices. (more) (synopsis)
Subscribe to:
Comments (Atom)