According to the Panorama programme, which first aired the clips over the weekend, the woman Mr Otárola can be heard speaking to is Yaziré Pinedo, 25... Ms Pinedo was reportedly awarded two contracts for work in the defence ministry in 2023 that earned her a total of 53,000 sol ($14,000; £11,000)...
Tuesday, March 12, 2024
Peru PM Resigns After Recording with Woman Leaked
According to the Panorama programme, which first aired the clips over the weekend, the woman Mr Otárola can be heard speaking to is Yaziré Pinedo, 25... Ms Pinedo was reportedly awarded two contracts for work in the defence ministry in 2023 that earned her a total of 53,000 sol ($14,000; £11,000)...
Wednesday, February 9, 2022
Leaked Tapes Reveal Corporate Espionage
Testimony that Vatican officials engaged in corporate espionage sheds new light on the breakdown of the London property deal.
Luciano Capaldo is a property developer who was closely involved in the Vatican’s Secretariat of State plans for the London London property deal at 60 Sloane Avenue...
Capaldo told investigators that he had access to surveillance cameras inside Torzi’s offices for some time.
So he passed information and images to Monsignor Mauro Carlino, a former official at the Secretariat of State currently indicted for extortion and abuse of office. The access, Capaldo said, came via a mobile phone app for which he had the login details. more
Thursday, January 7, 2021
Leaked Phone Call Cautionary Tale: Trump’s Phone Call With Georgia Election Officials
The president pressured Secretary of State Brad Raffensperger to overturn the results of the election in an hour-long phone conversation. Here is a transcript of the audio recording.
Chilling.
Covert recording of your phone calls is easy. There are smartphone apps, push-button recording features on business desk phones, and cheap add-on gadgets (1) (2) (3) which do the job very well. Everyone with an inclination to record your call, can. Instantly. And post it to social media, news media, or twist your arm with it, just as quickly. Also chilling.
You can mitigate the possibility of your call being leaked (by the party to whom you are speaking). Just think before you speak.
Thwarting someone spying on your call requires some technical assistance. Contact a Technical Surveillance Countermeasures (TSCM) consultant. Their specialty is inspecting workplaces, residences, vehicles, and off-site meeting locations for wiretap, bugs, and covert video surveillance devices.
UPDATE
The fact that the Jan. 2 call was recorded and leaked to the news media also spurred a claim that Raffensperger "faces espionage charges."
The claim was made in a widely shared Facebook post that was flagged as part of Facebook’s efforts to combat false news and misinformation on its News Feed.
Legal experts told us it would not be illegal for anyone on either
end of the call to record it, or to disseminate the recording.
Furthermore, the conversation did not bear on sensitive national
security matters covered by the federal Espionage Act. more
Monday, May 18, 2020
Leaked Phone Call Uncovers Possibly Moldy Marijuana | Fact or Business Espionage Trick?
 The conversation cannot be confirmed as legitimate, and could even be business espionage...
The conversation cannot be confirmed as legitimate, and could even be business espionage...In the audio, a person who appears to be a manager of one of Anchorage’s largest marijuana stores admits that his company sold 100 pounds of possibly moldy marijuana, and that CBD oil that was supposed to have a low psychoactive level of THC was found to, in fact, contain high amounts...
The video can be viewed by searching for Bobb Dogg on YouTube. The audio is labeled “Weedileaks.” more
Tuesday, September 3, 2019
Protecting Your Engineering Business from Industrial Espionage
As a business grows and begins to compete at a higher level, the stakes grow and their corporate secrets become more valuable. It isn’t just other businesses that might want this information, hackers who think they can sell the information will also be sniffing about.
Even if you can’t eliminate the risk entirely, there are certain things you can do to reduce the risk of a security breach in your business. more
A Very Short List...
Shred Documents
Don’t Print Sensitive Information if You Don’t Have to
Keep Your Schematics (designs, strategies, etc.) Under Wraps
Keep it Need to Know
 and my favorite...
and my favorite...
Because... If you don't look,
you may never know.
Carrie's on-the-Lam Comment via a Leaked Recording
 The embattled leader of Hong Kong was caught on a leaked audio recording reportedly saying she would “quit” if she could after causing “unforgivable havoc,” but on Tuesday reiterated that she hasn’t resigned because it would be the easy way out.
The embattled leader of Hong Kong was caught on a leaked audio recording reportedly saying she would “quit” if she could after causing “unforgivable havoc,” but on Tuesday reiterated that she hasn’t resigned because it would be the easy way out.In a press conference, Carrie Lam slammed the audio, recorded during a private meeting with a group of businesspeople, saying it was “unacceptable.”
The recording was published Monday by Reuters. In it, she is heard apparently blaming herself for igniting Hong Kong’s political crisis. more
Kevin's Tips for Management
- Assume your discussions are being recorded.
- Before proceeding, ask if they are recording.
- Be professional. If you would not say it in a courtroom, don’t say it.
- Red Flag – When an employee tries to recreate a previous conversation with you.
- Have an independent sweep team conduct periodic due diligence debugging inspections.
Create a Workplace Recording Policy
Wednesday, July 10, 2019
FREE - Security Message Screen Savers
- Reminders work.
- Put your idle computer screens to work.
- Three backgrounds to choose from, or commission custom screens.
Monday, July 8, 2019
Porcelain — An Industrial Espionage Story
 Another remarkable use for porcelain is the lithophane,
a sheet of porcelain so thin as to be translucent, with artwork etched
into it. The lithophane is thin enough that the art can only be seen
when backlit, but just thick enough that the image can have depth.
Lithophanes began to appear in several parts of Europe in the 1820s, but
they’re believed to have originated in China a millennia earlier during
the Tang Dynasty. Later Ming Dynasty scholars wrote of Tang bowls “as
thin as paper” that included secret images.
Another remarkable use for porcelain is the lithophane,
a sheet of porcelain so thin as to be translucent, with artwork etched
into it. The lithophane is thin enough that the art can only be seen
when backlit, but just thick enough that the image can have depth.
Lithophanes began to appear in several parts of Europe in the 1820s, but
they’re believed to have originated in China a millennia earlier during
the Tang Dynasty. Later Ming Dynasty scholars wrote of Tang bowls “as
thin as paper” that included secret images.
Monday, June 17, 2019
Business Espionage - Thought of the Day - Loose Lips
One of the most shocking things for me entering the corporate world after serving on several Special Forces teams was how lax many organizations in highly competitive industries were with information about their operations.
It doesn’t take industrial espionage to sabotage a company, just poor operation security. In World War II, the posters warned us that “Loose Lips Sink Ships” and that’s just as true today as it was then.
Operational Security, or OPSEC as we called it in the military, should be a part of your organizational culture, from the bottom to the top. Simple things such as reminding people not to discuss projects or clients in the elevator or at lunch reduce the amount of exposure and risk of compromise for both yourself and your stakeholders.
It’s far less likely that nefarious agents or bad actors are going to give up sensitive information than the possibility you’ll be compromised by the careless and/or reckless behavior of your employees. more
Saturday, October 6, 2018
Print Centers Leak Information
 confusing their users, and opening up vulnerabilities to the company. Although copying may be the main business of the machines, they can also scan, fax, send and receive vital company information — all in one place. Essentially, these machines have become a networking hub within the workplace, where each new action or service provides a new opportunity for exploitation wirelessly, by ethernet cable, or by both.
confusing their users, and opening up vulnerabilities to the company. Although copying may be the main business of the machines, they can also scan, fax, send and receive vital company information — all in one place. Essentially, these machines have become a networking hub within the workplace, where each new action or service provides a new opportunity for exploitation wirelessly, by ethernet cable, or by both.Researchers have recently been investigating access on printer/copiers as a potential opportunity for information leakage or industrial espionage, or even sabotage. In a January 2017 Quocira survey of 200 US and European businesses, more than half reported some data loss through intercepted print jobs (50%), access and loss or theft of printer hard disk data (48%), documents emailed externally (44%), or outright hacking of the printer system to gain company network access (18%). Some hackers have been very clever in attacking these systems. more
Wednesday, September 12, 2018
Industrial Espionage: The Deafening Sounds of a Rip-Off
Motorola wanted one, too.
Industrial espionage?!?!
You decide.
Welcome to the business zoo.
Friday, April 20, 2018
Detective Science: Fingerprinting Text to Discover Data Leakers
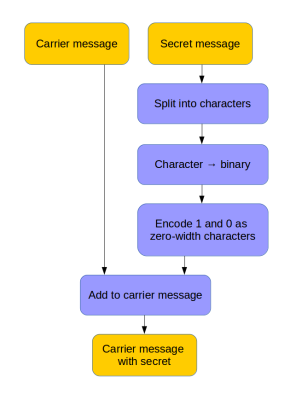
Fingerprinting text; the ability to encode hidden data within a string of characters opens up a large number of opportunities.
Spybuster Tip: For example, someone within your team is leaking confidential information but you don’t know who. Simply send each team member some classified text with their name encoded in it. Wait for it to be leaked, then extract the name from the text — the classic canary trap.
Here’s a method that hides data in text using zero-width characters. Unlike various other ways of text fingerprinting, zero width characters are not removed if the formatting is stripped, making them nearly impossible to get rid of without re-typing the text or using a special tool. In fact you’ll have a hard time detecting them at all – even terminals and code editors won’t display them. more
Saturday, June 24, 2017
Things We See — Blue Bucket Blues

Tuesday, June 20, 2017
Be Successful Like Apple - Get Serious About Information Security
 The briefing, titled “Stopping Leakers - Keeping Confidential at Apple,” was led by Director of Global Security David Rice, Director of Worldwide Investigations Lee Freedman, and Jenny Hubbert, who works on the Global Security communications and training team...
The briefing, titled “Stopping Leakers - Keeping Confidential at Apple,” was led by Director of Global Security David Rice, Director of Worldwide Investigations Lee Freedman, and Jenny Hubbert, who works on the Global Security communications and training team...The briefing, which offers a revealing window into the company’s obsession with secrecy, was the first of many Apple is planning to host for employees. In it, Rice and Freedman speak candidly about Apple’s efforts to prevent leaks...
Director of Global Security, David Rice...“We deal with very talented adversaries. They're very creative and so as good as we get on our security controls, they get just as clever.” more
If your security plan does not include Technical Information Security Surveys, contact me. ~Kevin
Wednesday, June 7, 2017
Yellow Printer Dots Nail Spy Agency Leaker
 According to Rob Graham, who writes for the blog Errata Security, the Intercept’s scanned images of the intelligence report contained tracking dots – small, barely visible yellow dots that show “exactly when and where documents, any document, is printed.” Nearly all modern color printers feature such tracking markers, which are used to identify a printer’s serial number and the date and time a page was printed.
According to Rob Graham, who writes for the blog Errata Security, the Intercept’s scanned images of the intelligence report contained tracking dots – small, barely visible yellow dots that show “exactly when and where documents, any document, is printed.” Nearly all modern color printers feature such tracking markers, which are used to identify a printer’s serial number and the date and time a page was printed. “Because the NSA logs all printing jobs on its printers, it can use this to match up precisely who printed the document,” Graham wrote. more
Long term readers of the Security Scrapbook already knew about this.
From 10 years ago... Is Your Printer Spying on You? Good!
Sunday, January 29, 2017
Congressional Republicans' Private Meeting Bugged & Leaked
 The recordings below were first provided to The Washington Post and other news outlets through an anonymous email sent Friday evening.
The recordings below were first provided to The Washington Post and other news outlets through an anonymous email sent Friday evening. The author of that message asked that the recipients not publish the audio files out of concern that the author could lose his or her job.
On Saturday afternoon, the person wrote again and granted permission to publish the files, explaining that he or she had more closely reviewed the recordings and had concluded that they could not be used to identify him or her.
Washington Post reporters who reviewed the files on Thursday and Friday found revealing details within. more
Tuesday, September 20, 2016
One Spy Outs Another at City Council Meeting
Paulien Lombard, who has since left the church, addressed a City Council meeting in Garden Grove, describing how she and candidate Clay Bock had been sent by Scientology’s spy wing, the Office of Special Affairs, to intimidate a man who’d been protesting outside the group’s “Int Base,”...

Bock was actually in attendance when Lombard outed him as a Scientology spy, and the stunned City Council candidate nervously addressed the meeting afterward.
“I had no idea Paulien would be here or that this would be an issue,” Bock said. more
Friday, August 21, 2015
He's Back... The Air Gap Computer Hack
Air-gapped computers are isolated -- separated both logically and physically from public networks -- ostensibly so they cannot be hacked over the Internet or within company networks.
Led by BGU Ph.D. student Mordechai Guri, the research team discovered how to turn an ordinary air-gapped computer into a cellular transmitting antenna using software that modifies the CPU firmware. GSMem malicious software uses the electromagnetic waves from phones to receive and exfiltrate small bits of data, such as security keys and passwords...
This is the third threat the BGU cyber team has uncovered related to what are supposed to be secure, air-gapped computers. Last year, the researchers created a method called Air-Hopper, which utilizes FM waves for data exfiltration. Another research initiative, BitWhisper, demonstrated a covert bi-directional communication channel between two close-by air-gapped computers using heat to communicate. more
Thursday, February 5, 2015
Security Director Alert - DarkLeaks - The Espionage Bazaar
A new WikiLeaks-style website has recently been announced that will reward its contributors with Bitcoins in exchange for information.
If the most valuable commodity is information then it is about to get its own hypermarket; DarkLeaks will allow uses to sell leaked data to the highest bidder in an anonymous blockchain-powered environment where anything goes.
DarkLeaks is being developed by unSystem who are behind DarkWallet, and DarkMarket an anonymous ebay-style marketplace which unlike Silk Road operates on the P2P model so that there is no central point of failure for law enforcement to take down.
The DarkLeaks system is so secure that it does not even allow communication between the seller and the buyer of information. Their website states: “The software uses bitcoin’s blockchain to encrypt files which are released when payment is claimed by the leaker. Files are split into segments and encrypted. These segments are unlocked only when the leaker reveals the key by claiming his bitcoins.”
There are also no limits on the type of content that can be bought and sold. Everything from evidence of corporate corruption to naked pictures of celebrities is up for grabs. UnSystem developer Amir Taaki has told CoinDesk that platforms like DarkLeaks provide a financial incentive for insiders to reveal information thereby “devaluing business models based around proprietary secrecy”.
(more)
This is going to be a BIG problem for corporations.
Those without a counterespionage strategy will hurt first.
Wednesday, January 21, 2015
Two Canadian Spy Opportunities
CSEC has started a hiring campaign targeting colleges and universities a few months ahead of the inauguration of its new headquarters in Ottawa (see list of opportunities). The building, with an astronomical price tag of $1.2 billion, is the most expensive government complex in Canadian history, dubbed the spy "Taj Mahal" by several critics. The immense campus is located next to the Canadian Security Intelligence Service (CSIS) headquarters, and the two will be joined by a walkway. The veritable "spy nest" will house 4,000 cryptographers, secret agents and information specialists of all kinds in Gloucester, a suburb of the nation's capital.
(more)
The new headquarters of Canada’s electronic surveillance agency had an “extreme vulnerability” which was inadvertently breached by firefighters responding to an emergency call, the Toronto Star reports. The Canadian Communications Security Establishment (CSE) revealed the vulnerability by sending uncensored documents in response to an access to information request by the Star about the fire.
The sensitive information contained in the documents was highlighted, but not censored, compounding one security breakdown with another.
During the construction of the $800 million CAD (about $660 million USD) building for the CSE, a routine call in response to a small fire lead local firefighters to different entrance than the one they were expected at. Finding no-one there, they cut a padlock to access the building.
The documents also reveal vulnerabilities such as inoperative security cameras and a long-missing visitor pass. At least some of those vulnerabilities have since been addressed, and the agency told the Star that the construction access point used in the incident no longer exists, now that the building is complete and occupied.
(more)