The FBI's Office of Private Sector, Counterintelligence Division and Training Division present this 30-minute film entitled Made in Beijing: The Plan for Global Market Domination. In the world of global adversaries, the People’s Republic of China stands at the forefront with its sustained and brazen campaign of industrial espionage, posing the single greatest threat to our freedom, national security, and economic vitality. Made in Beijing: The Plan for Global Market Domination sounds the alarm, helping private sector partners recognize the urgent need to protect their crown jewels against industrial espionage. more
Saturday, March 12, 2022
Friday, March 11, 2022
Shocking Security Discovery: Fake Surveillance Cameras Don't Deter Crime
TX - Mount Bonnell is known for its spectacular views of Austin, but it’s also getting a reputation as a hot spot for car break-ins...
From Jan. 1 – March 7, there have been 100 car burglaries within 2,000 feet of the park according to the Austin Police Department’s Crime map...
Austin Parks and Recreation told KXAN after a rash of incidents in July, August and September, it installed dummy cameras at Mount Bonnell as a theft deterrent...
The department told us the fake cameras were later removed since crime did not decrease. more
Thursday, February 17, 2022
Spybuster Tip # 712: How to Thwart Off-Site Meeting Spies
The National Executive Council of the Academic Staff Union of
Universities, on Sunday, changed the venue of the meeting... A reliable source said the venue was changed due to the fear of
bugging of the auditorium by secret agents of the Nigerian government. more
RIP: Peter Earnest
Mr. Earnest acknowledged that his personality sometimes made it difficult to spend years working undercover. “It’s hard when you’re an open person by nature,” he told Washingtonian magazine in 2013. “In some cases, people say, ‘You don’t seem like a spy.’
“The best spies don’t seem like spies.”
In a video interview for the Spy Museum,
Mr. Earnest described what he called “my Bond moment” at the CIA, in
which he slipped out of a black-tie reception at the home of an asset
and bugged the person’s office. Lying on his back, with a handkerchief
positioned on his chest to catch the shavings, he drilled small holes in
the bottom of the target’s desk and installed a recording device. more
US Football Team Settles Video Voyeurism Suit for $2.4 Million
Each
of the women received $399,523.27 after the incident. One of the
cheerleaders alleged that she clearly saw Richard Dalrymple, the
Cowboys' longtime senior vice president for public relations and
communications, standing behind a partial wall in their locker room with
his iPhone extended toward them while they were changing their clothes... Dalrymple
gained entry to the back door of the cheerleaders' locked dressing room
by using a security key card.
more
What Could be the Penalty for Posting a Spycam Video to the Net?
Monday, February 14, 2022
An Update on AirTag and Unwanted Tracking
Apple has been working closely with various safety groups and law enforcement agencies. Through our own evaluations and these discussions, we have identified even more ways we can update AirTag safety warnings and help guard against further unwanted tracking...
Advancements Coming to AirTag and the Find My Network
The following updates represent important steps Apple is taking... more
Saturday, February 12, 2022
Why You Rarely Hear About Corporate Espionage
Corporations really hate publicity about their information security failures.
The smart ones sweep to mitigate the chances of failures.
The others just sweep the failures under the rug.
Case in point...
Spanish power company Iberdrola is suing the holding company of business news site El Confidencial over coverage of an industrial espionage case, a move the site's director says threatens its survival.The multinational energy firm, which is seeking $20 million in damages, said that for more than two years up to November 2021, El Confidencial published 225 stories on the espionage case, including 68 that harmed the company and 12 that were untrue.
The company contends the reports were a "violation of its right to honour," a term that in Spanish law refers to reputational damage. more
VR Headset Hacks Could Steal Sensitive Information
Researchers at Rutgers University-New Brunswick have published “Face-Mic,” the first work examining how voice command features on virtual reality headsets could lead to major privacy leakages, known as “eavesdropping attacks.”
The research shows that hackers could use popular virtual reality (AR/VR) headsets with built in motion sensors to record subtle, speech-associated facial dynamics to steal sensitive information communicated via voice-command, including credit card data and passwords.
Foreign Spies Use Dating Apps... to access government secrets
Foreign spies are using Tinder and other dating apps to recruit Australians with access to sensitive government secrets. ASIO boss Mike Burgess made the alarming revelation while delivering his annual threat assessment, in which he also warned identifying anti-vaccine activists who could turn violent was proving difficult. more
---
The National Security Service of Armenia (HAAT) has detained 19 people suspected of being members of an "espionage network" in the South Caucasus nation. The HAAT said on February 10 that dozens of servicemen in different units of the the armed forces may have been involved in the activities of the spy network, which worked for an unspecified nation.
According to the security agency, recruitment took place via an
online dating service through which Armenian servicemen who possessed
classified data and documents would eventually join the spy ring. more
9 Potential Signs of Corporate Espionage
If you suspect that your business has been a target of corporate espionage, it's essential to take action immediately — from doing an in-house investigation to hiring a private professional.
If you see any of the below signs, don't ignore them, but also take care not to make any unfounded accusations or statements. Keep your thoughts closely held and get the evidence first...
1. Unexplained or sudden changes in practices
2. Changes in business relationships
3. Unusual computer activity
4. Becoming defensive or secretive about work
5. Equipment or files go missing
6. Unexplained drops in sales or profits
7. Employees quitting suddenly
8. Accessing computer files without permission
9. Corporate secrets leaked to the press more
School Principal Arrested - Facing Felony Eavesdropping Charge
The Lee County Virtual School Principal faces charges for illegally recording a meeting.
It is an unusual case of consent because Florida Statute 934.03 talks
specifically about the interception and disclosure of wire, oral or
electronic communications prohibited. “Florida is a two-party consent state,” said FGCU Professor Dr. David Thomas. Lee County Sheriff’s deputies arrested (him) for recording a meeting without permission. more
Ford Wants to Hide Spy Drones in Autonomous Cars
Among the many challenges facing the autonomous car industry is how to keep an eye on the condition of the vehicles while they're out and about.
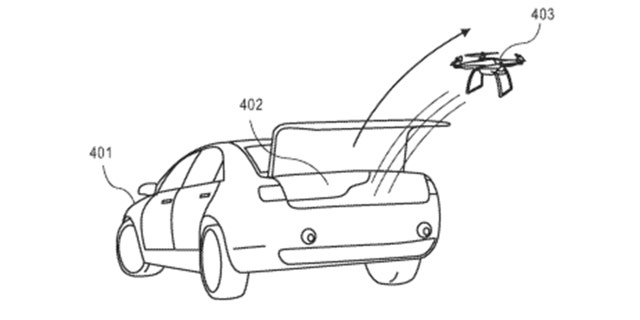
Ford, which co-owns the Argo AI autonomous car company that's planning to launch a ride-hailing service soon, has now patented a way to do just that. more
Hidden Wisconsin Restaurant Serves Espionage Fun With Food
A truly exceptional themed restaurant needs to go further than some wall decor and select menu items, it needs to provide a full theme experience, something that the SafeHouse Restaurant and Bar in Milwaukee, Wisconsin seems to have nailed completely. Let's put it this way, when you arrive at the 'hidden' SafeHouse, you need to provide a password to gain entry, but once you get inside the real show begins. morePersonal recommendation... The Mission Impossible - Go rogue with this mission. A large fishbowl filled with Bacardi Superior Rum, Roaring Dan's Dark Rum, orgeat, lemon, orange, pineapple, and grenadine - serves 2 spies nicely or 1 brave agent. more
Wednesday, February 9, 2022
GSM Eavesdropping Bugs: A Recent Find in a Corporate Office
While on lockdown, businesses and individuals must think about their unoccupied premises and possessions. Now that we are coming out of this lockdown and going back to work, Gurpreet Thathy and Mike Moran give their thoughts and go through a recent case with a client last week...
Mike and his team conducted a ‘sweep’ of the offices in conjunction with our Cyber Audit. We identified a GSM eavesdropping device planted within a boardroom during the critical areas’ in-depth physical and electronic search. This device was cunningly disguised as a 3-way extension adapter which was fully operational.
A closer examination of the adapter revealed a SIM card and a microphone connected. The client was immediately informed, and as per our standard operating procedure (SOPs), the device was isolated from the infrastructure, bagged, tagged, and handed over to our internal forensic team to investigate.
The forensic investigation of the SIM card revealed dialled and received calls. more
What is a GSM Bug? When was the last time your organization conducted an inspection for one?












