Friday, August 13, 2021
The Philadelphia Experiment Isn't the Only Thing Missing
This Week in Spy News
Germany Arrests British Embassy Worker Suspected of Spying for Russia
Prosecutors accuse the British man of handing over documents to Russian agents for cash, amid growing concerns that Germany is increasingly caught in the cross hairs of international spying. more
A Chinese court has sentenced Canadian businessman Michael Spavor to 11 years in prison for espionage, more than two years after he was first detained. Spavor, a Beijing-based businessman who regularly traveled to North Korea, was sentenced after being found guilty of spying and illegally providing state secrets to foreign countries, the Dandong Intermediate People's Court said in a statement Wednesday. more
Despite a lack of evidence, the National Security Agency will investigate whether the Fox host was illegally targeted. The National Security Agency’s Inspector General Robert Storch has announced a review of whether the agency illegally conducted cyber-espionage and collected the electronic communications of Fox News opinion-show host Tucker Carlson, who has accused the NSA of trying to capture embarrassing information that might lead to him being taken off the air. more
China Sighted by CIA
The Central Intelligence Agency is weighing proposals to create an independent “Mission Center for China” in an escalation of its efforts to gain greater insight into the U.S.’s top strategic rival, according to people familiar with the deliberations.
The proposal, part of a broader review of the
agency’s China capabilities by CIA Director William Burns, would elevate
the focus on China within the agency, where China has long been part of
a broader “Mission Center for East Asia and Pacific.” more
Tips for Closing Hard-to-Delete Online Accounts
via Consumer Reports
Tips for Deleting Old Accounts
- Check to see if anyone has figured out the steps. Google “how to delete [company name] account” and you’ll often find instructions. (A step-by-step guide to deleting two dozen common accounts.)
- Go to the Settings page first. Companies sometimes put the delete button in settings, account menus, or pages to edit your profile; it varies by company.
- Try the privacy policy. Privacy policies often include instructions, and you can search for words like “account,” “delete,” “close,” or “deletion.”
- Explore the Help menus. If there’s a Help menu or an FAQ section on a website, you can often find deletion instructions there.
- Try customer service. When available, text chats are usually faster than phone calls in my experience.
- Take advantage of privacy laws. California’s privacy law, the CCPA, requires most businesses to let state residents delete data collected from them. Companies don’t have to fulfill a deletion request if you’re not a resident, but some honor requests from anyone. Look for “California” or “CCPA” in privacy policies for details.
- Don’t forget the accounts you’ve forgotten. You may have registered for accounts years ago that have slipped your mind. A whole article
with detailed instructions on how to find them. Some tips to get
started: Google your email address and old usernames; check for saved
log-ins in your web browser or password manager; search your email inbox
for old “welcome” messages. Try variations on phrases like “welcome
to,” “new account,” “password,” or “confirm your email.” more
Tuesday, August 3, 2021
The NSA's Wireless Device Best Practices
Telework has become an essential component of business, and many people are teleworking from home or during travel. While the owners of home networks can take steps to secure those networks, it can be difficult to ensure public networks (e.g., conference or hotel Wi-Fi®) are secure. Protecting personal and corporate data is essential at all times, but especially when teleworking in public settings.
This infosheet gives National Security System (NSS), Department of Defense (DoD), and Defense Industrial Base (DIB) users the best practices for securing devices when conducting business in public settings. It describes how to identify potentially vulnerable connections and protect common wireless technologies, and lists steps users can take to help secure their devices and data.
While these best practices cannot ensure data and devices are fully protected, they do provide protective measures users can employ to improve their cybersecurity and reduce their risks. more
Friday, July 30, 2021
Florida Surveillance Techs Charged With Video Voyeurism
Police have arrested video surveillance technician Jeremy Dale Lewis for video voyeurism after a nearly year-long investigation...
A second suspect, Michael Reilly, is also facing a charge of video voyeurism. Police said Reilly, who also worked for Ask the Advisors, watched more than 600 live and archived videos over a five-day period in July 2020 of a woman undressing in her dressing room, and of a couple having sex...
This incident follows a high-profile case that saw an ADT technician receive a 52-month jail sentence for doing essentially the same thing. more
3 in 10 Home Sellers Use Spycams During House Tours
Spycams are reportedly being used by home sellers who want to ink a deal sooner rather than later.
According to a recent LendingTree survey, 3 in 10 home sellers admit to using hidden cameras when they host an open house.The survey, which was commissioned from the experience management firm Qualtrics, notably had a small sample size of home sellers – 346 – compared to home buyers – 1,160 – for a total sample size of 2,050.
Of those sellers who admit to using cameras without notifying buyers, 49% claim they do so to find out what buyers "do and don’t like about their home." more
Better Not Lose Your Laptop - A Cautionary Tale
via Dolos Group, LLC
What can you do with a stolen laptop?
Can you get access to our internal network?
That was the question a client wanted answered recently. Spoiler alert: Yes, yes you can. This post will walk you through how we took a “stolen” corporate laptop and chained several exploits together to get inside the client’s corporate network.
From the Man Who Brought Us Every Kid's First Spy Toy - Ron Popel (RIP)
How many Mr. Microphones wound up behind the couch when the younger brother's older sister brought her date home?
Tuesday, July 27, 2021
There’s Almost Certainly a Spy in Your Office
A recent paper from the US Senate suggests advanced actors now regularly plant individuals in large organizations, with a view to stealing data and research that can be used for economic, scientific or military gain.
China, for example, is said to operate more than 200 different recruitment programs, the most elaborate of which is the Thousand Talents Plan, which is estimated to have recruited 7,000 operatives or more. And China is by no means the only country to engage in these behaviors...
In rare instances, when recruiters fail to gain access to an employee, they have been known to train up an individual specifically for the task. Known as “embeds”, these imposters are much closer to traditional spies and have a full understanding of the ambitions of their handlers.
“Sometimes, these embeds are quiet for a long time, even years. Then all of a sudden they gain access to the information they were recruited to hunt down, before disappearing into thin air. There is another level of tradecraft on display here.” more
Note: Embeds are in the best position to plant eavesdropping devices (disguised voice recorders, Wi-Fi data leaches, USB spy cables, GPS trackers, GSM cellular bugs, etc.) Periodic searches for these devices thwarts their efforts. Sometimes just by them knowing the organization conducts searches. And, of course, by discovering the devices before they can do long-term harm.
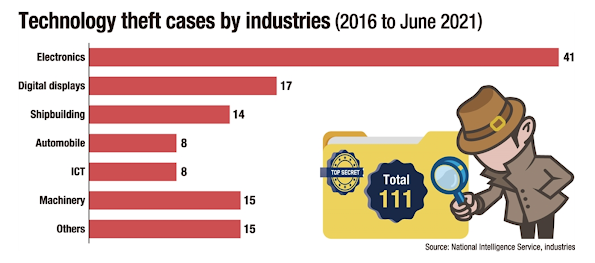
Corporate Espionage: Things are Tough All Over
Korea's tech industries are increasingly becoming the
target of technology and intellectual property theft that has been
growing in sophistication and harmfulness...
With
industrial espionage, competitors' poaching of skilled employees,
cyberattacks and other forms of theft being rampant, the world has been
introducing stricter rules to ban theft of competitors' technologies
across borders...
Industrial espionage and cyberattacks are still
favored forms of theft, with the targets changing from conglomerates to
their subcontractors, many of them small- and medium-sized enterprises
(SMEs) that are often ill-equipped in terms of security and management. more
Deadly Corporate Espionage Case Settled
Credit Suisse has reached an out-of-court settlement with former star banker Iqbal Khan over allegations of spying that led to the resignation of the Chief Executive Tidjane Thiam, a spokesperson for the Swiss bank said...
The affair became public when Khan, after defecting to UBS, confronted a private detective who was following him and his wife through Zurich.
What Credit Suisse initially described as a rogue spying case run by then-Chief Operating Officer Pierre-Olivier Bouee widened as details emerged of other instances of surveillance.
As
well as the departures of Bouee and Thiam, a private investigator who
organized the surveillance committed suicide after the affair came to
light. more
Pegasus v. iPhone Update - iOS 14.7.1 Plugs the Loophole
Apple has reportedly fixed the vulnerability in iOS 14.7.1.
The security notes don’t specifically mention Pegasus, but they refer
to “a memory corruption issue” that “may have been actively exploited.” more
Friday, July 23, 2021
Pegasus Spyware Update: How to Check Your iPhone
If you’re concerned about recent reports of the Pegasus spyware reportedly installed by the Israeli NSO Group to hack journalists and world leaders, there’s a tool to check if it’s hidden on your iPhone. But you probably have nothing to worry about...
But if you’re concerned, there’s a way to test whether your iPhone has
been targeted. It’s not an easy test, mind you, but if you’re using a Mac or Linux PC and have backed up your iPhone using it, Amnesty International’s the Mobile Verification Toolkit
will be able to detect whether your phone has the Pegasus spyware
installed on it. The tool, which TechCrunch tested, works using the
macOS Terminal app and searches your latest iPhone backup on your Mac,
“is not a refined and polished user experience and requires some basic
knowledge of how to navigate the terminal.” You’ll need to install
libusb as well as Python 3 using Homebrew. (You can learn more about the
installation here.) TechCrunch says the check only takes “about a minute or two to run” once it’s been set up. more
Monday, July 19, 2021
Private Espionage Is Booming - The US Needs a Spy Registry
via Wired Magazine...
Years ago, while stationed
in Moscow as the bureau chief for a major news magazine, I was
approached by a representative of a multinational company and presented
with a tantalizing offer. He said he had highly sensitive materials
exposing possible criminal activity by a Russian competitor. The
documents were mine with one condition: advance notice so he could be
out of the country when any story was published.
I had every reason to think the materials came from a private intelligence operative hired by the company—there were many such operatives in Moscow—but I didn’t ask my source for his source. Instead I embarked on a somewhat harrowing investigation of my own, and on corroborating the materials, I was able to publish a splashy story.
This episode came back to me while reading Barry Meier’s new book, Spooked: The Trump Dossier, Black Cube, and the Rise of Private Spies. A former New York Times investigative reporter, Meier casts a harsh light on both “private spies” and journalists who make frequent use of nuggets unearthed by these operatives. In the book’s afterword, he revives an idea for “a kind of ‘spy registry’ in which operatives for hire would have to disclose the names of their clients and assignments,” just as Congress now requires of lobbyists hired to influence legislators.Is this truly a problem in need of a solution? Or would a spy registry create worse problems?
It’s tempting to conclude that there is really nothing new here and that private spies may even supply a public service. In the original, late-19th-century Gilded Age, the Pinkerton Detective Agency devoted itself to the art of subterfuge. In 1890, a Pinkerton man went undercover on behalf of his client, the governor of North Dakota, and confirmed from rigorous barroom investigation that a fair amount of “boodle,” bribe money, was being dispensed by advocates of a state lottery opposed by the governor. The governor revealed the dirty dealings to the public, and the lottery scheme failed—all perhaps to the civic good.Today’s
circumstances are far different. Inexpensive, off-the-shelf
technologies for surveillance, hacking, and spoofing make the spy game
easier to play than ever before. What hired sleuth doesn’t now travel
with one of those metallic-fabric bags that blocks cellphone GPS
signals, like the GoDark Faraday model that sells online for $49.97?
It’s an insignificant item on the expense report. more