WA - A pastor and teacher at a Christian school in Washington state was
arrested earlier this week and charged with filming hundreds of
voyeurism videos of female staff and students.
more
UK - A voyeur was locked up after being caught with 169 video clips taken by a spy camera set up to film an unsuspecting woman. The penalties were imposed when he appeared before magistrates in the city. They were told the offence came to light when the camera was discovered and police were alerted.
more
ID - A Ketchum man has been charged with one felony count of video voyeurism. A recording device found in the bathroom
of a residence at the Wildwood condominium complex. The recording
device was found by a guest who was staying at the residence at points
between April and June, with her daughter. The woman told Lundergreen that the device was located in the bathroom wall outlet and disguised as a USB charger.
more
Japan - The secretary general of a local assembly in Yamagata Prefecture,
northwest Japan is fired for voyeurism in a women's bathroom at town
hall.
more
PA - A West Chester University student was arrested after police said he hid a
cellphone in public bathrooms in several locations, including one at
West Chester University, and recorded women in various stages of
undress.
more
LA - A former WAFB employee who secretly recorded two female station
employees using the restroom in 2017 was sentenced to four months in
prison Tuesday. He was immediately handcuffed and led to prison.
more
New Zealand -
The
man who filmed women using the shower in his Airbnb homestay then
uploaded the videos to a porn site has lost name suppression and has
been sent to prison for four years and four months. more
New Zealand - A
home handyman who used his position of trust to spy on a female friend
in her bedroom has been sentenced to three months of community
detention. The offending...involved Williamson hiding a camera inside a toolbox that he left in the
woman's bedroom, which he left there after performing maintenance
duties in her home. The device was discovered by the woman, who contacted the police.
more
FL - In a case involving allegations that a man placed hidden cameras in his
adult stepdaughter’s bedroom, an appeals court Friday overturned a
conviction on video-voyeurism charges because police improperly obtained
evidence from a laptop computer.
more
CT - A man who entered a neighbor's home through an unlocked door and
allegedly installed video cameras in four spots in the home has been
arrested by police. An investigation revealed that Pelgrift had entered the home and
installed the videos cameras while the woman was not home. She happened
to notice a camera and called the police, state police said.
more
FL - Investigators say they have uncovered an extensive amount of videos
and images of under-age students secretly filmed while undressing by a
Bloomingdale High School teacher who was arrested last month on a video
voyeurism charge. Mark Ackett, 50, who resigned as a fashion
design teacher, now faces an additional 353 charges. He
was first arrested on Sept. 11 — the same day a 17-year-old student in
his class discovered two cell phones hidden in the classroom changing
area where she and her classmates disrobed for fashion assignments.
more
S. Korea - South Korea is in the grip of a 'spycam'
epidemic, with covert footage of sex, nudity and urination posted online
in what amounts to a "social death penalty" for thousands of women
forced to live with a pornographic shadow. The
footage may be taken surreptitiously by boyfriends or captured on
covert devices as small as car keys. Daily camera checks are now part of
life for cleaners in many public toilets.
more
FL - A massage therapist was arrested over the weekend and charged with video
recording a female customer disrobing prior to an appointment. ... Further investigation indicates that Scott had placed a cellphone in the
massage room to video record the customer while she was undressing.
more
NM - A Dona Ana County man is facing time behind bars for hiding video
cameras in bathrooms and capturing video of victims using the restroom,
showering, and changing clothes. ... Police say Ikard's face was even seen on some of the videos as he worked to set up the cameras.
more
UK - A retired company director who covertly
filmed a young woman getting changed at his luxury home has been jailed
for eight months. Allan Austin, 66, installed a hidden spy camera at his home in Cheshire because he 'liked the figure' of the victim. When officers searched Austin's £500,000 detached house in the village
of High Legh, near Knutsford, Cheshire they found the hidden camera
which was linked to his computer and iPad.
more
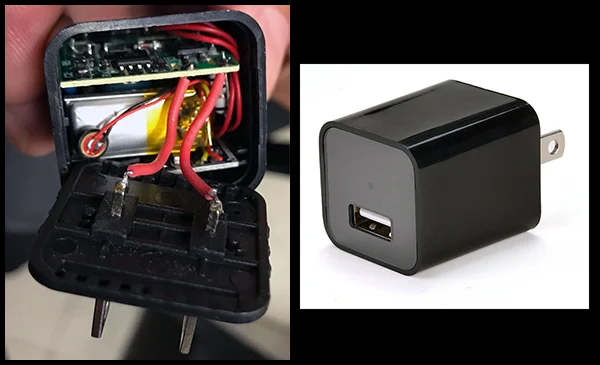
A video spycam (with audio recording) we found last Friday at a corporate location...
Now, on to the Extortionography cases. Hey, the elections are here, and the tech fists are flying.
ND - James O'Keefe's Project Veritas
released a new undercover video on Tuesday night showing vulnerable
Sen. Heidi Heitkamp's (D-ND) campaign staff exposing her as being a
far-left candidate while she has tried to portray herself as being
centrist, saying, "when she gets elected she's going to be super
liberal."
more
VA - A conservative group that creates undercover “sting” videos infiltrated
the campaign of Abigail Spanberger, a Democrat in a tight race with Rep.
Dave Brat in Virginia’s 7th District.
more
AZ - A right-wing operation that creates secretly recorded videos targeted
Democratic U.S. Rep. Kyrsten Sinema, who's running a tight race for U.S.
Senate, releasing a video Monday with several clips of the
representative and her campaign workers making candid off-the-cuff
comments.
more
MO
- An undercover video exposed a Democrat senator's re-election campaign
for secretly taking donations from Planned Parenthood. The video, from
conservative activist group Project Veritas, shows
campaign workers for Democrat Sen. Claire McCaskill of Missouri talking
about how Planned Parenthood funnels money to McCaskill's campaign
through other organizations.
more
CA - New undercover video appears to show signature gatherers pitching
falsehoods to voters get them to sign petitions that would force the
massive Newland Sierra development to a public vote.
more
Thanks for subscribing to Kevin's Security Scrapbook (see top right column). ~Kevin
 UK - An apartment unit manager was arrested on Friday after a tenant found a secret camera hidden in their bathroom.
UK - An apartment unit manager was arrested on Friday after a tenant found a secret camera hidden in their bathroom.