A silent film shows MI6 staff members at a site linked to the code-breaking facility Bletchley Park during World War II.
Like a home movie reel, the silent footage shows young people at candid moments: playing soccer and cricket, sunbathing, smiling and making faces at the camera...
But they were not ordinary office colleagues: They were off-duty secret British communications staffers, linked to code-breakers who decrypted German ciphers and helped the Allies win World War II.
The newly revealed footage features staff members of the MI6 Section VIII — the British spy agency’s communications staff — filmed at a site associated with the famous code-breaking facility Bletchley Park. more
Tuesday, April 7, 2020
New iPad Pro Prevents Eavesdropping or Spying
Apple beefs up iPad Pro security by disabling the microphone when the case is closed, a feature which was previously reserved for the Mac.
Apple introduced a feature with the 2018 MacBook lineup, allowing the microphone to be disabled whenever the display lid was closed. This measure was put in place to prevent eavesdropping, preventing malicious apps to tap into the microphone to gather extra data about you.
Fast forward to 2020 and the feature has come to the new iPad Pro lineup. The way it works is pretty simple - just close the lid of the case on the iPad Pro, which has to be MFi compliant, and the microphone is physically disconnected to prevent any sort of eavesdropping or malicious code from running if iPadOS is compromised in some way. more
Apple introduced a feature with the 2018 MacBook lineup, allowing the microphone to be disabled whenever the display lid was closed. This measure was put in place to prevent eavesdropping, preventing malicious apps to tap into the microphone to gather extra data about you.
Fast forward to 2020 and the feature has come to the new iPad Pro lineup. The way it works is pretty simple - just close the lid of the case on the iPad Pro, which has to be MFi compliant, and the microphone is physically disconnected to prevent any sort of eavesdropping or malicious code from running if iPadOS is compromised in some way. more
Friday, April 3, 2020
Facebook Tried to Buy Controversial Tool to Spy on iPhone Users, Court Filing Reveals
Over the last few years, Facebook has had a slew of privacy and security blunders and more details about one of them have come to light through a new court filing as the social media company is suing the spyware company NSO Group. It turns out Facebook tried to buy controversial government spyware to monitor iPhone and iPad users.
Reported by Motherboard, when Facebook was starting to build its spyware cloaked in a VPN product, Onavo Protect for iOS and Android, the social media company reached out to the controversial company NSO Group that creates spyware for government agencies...
Apple made Facebook remove Onavo Protect from the App Store in August of 2018.
Then in 2019 Facebook repackaged it as a “Research app” and tried to pay teens to sideload it on their devices.
The Research app was shut down as well and Facebook finally shutdown Onavo completely in February 2019. more
Reported by Motherboard, when Facebook was starting to build its spyware cloaked in a VPN product, Onavo Protect for iOS and Android, the social media company reached out to the controversial company NSO Group that creates spyware for government agencies...
Apple made Facebook remove Onavo Protect from the App Store in August of 2018.
Then in 2019 Facebook repackaged it as a “Research app” and tried to pay teens to sideload it on their devices.
Zoom’s Encryption Is “Not Suited for Secrets” and Has Surprising Links To China, Researchers Discover
Meetings on Zoom, the increasingly
popular video conferencing service, are encrypted using an algorithm
with serious, well-known weaknesses, and sometimes using keys issued by
servers in China, even when meeting participants are all in North
America, according to researchers at the University of Toronto.
The
researchers also found that Zoom protects video and audio content using
a home-grown encryption scheme, that there is a vulnerability in Zoom’s
“waiting room” feature, and that Zoom appears to have at least 700
employees in China spread across three subsidiaries. They conclude, in a report for the university’s Citizen Lab
— widely followed in information security circles — that Zoom’s service
is “not suited for secrets” and that it may be legally obligated to
disclose encryption keys to Chinese authorities and “responsive to
pressure” from them.Zoom could not be reached for comment. more
4/15/2020 UPDATE - More top companies ban Zoom following security fears. more
Thursday, April 2, 2020
Think Your Smart Speaker is Spying On You... get Paranoid
(Note: As of this date the manufacturer is only accepting pre-orders. Gauging demand before going into production is not uncommon. The following is just an interesting bit of news; not a product endorsement. Also, it might be an April Fool's prank.)
Their headline reads, "Blocks smart speakers from listening, while keep them voice-activated. Just say "Paranoid" before your usual commands." more
"How?" ...you may ask.
A. In one of three ways.
Their headline reads, "Blocks smart speakers from listening, while keep them voice-activated. Just say "Paranoid" before your usual commands." more
"How?" ...you may ask.
A. In one of three ways.
- The BUTTON model begins with the mute button pressed. When it hears you say, "Paranoid" it presses again, thus letting your next command to pass through. After your command is finished it re-mutes with another press.
- The HOME model (it appears) uses ultrasound to block the speakers microphones. Click here to learn how ultrasound blocking works. The volume needed for this application is very low so it shouldn't be a health risk.
- The MAX model requires you sending them your smart speaker so they can physically install their solution. People who use this option are not true paranoids. True privacy paranoids would be afraid the unit might come back, bugged!
Wednesday, April 1, 2020
Guest Wi-Fi Access Comes with Risks for Organizations
Reported this week: A convicted sex offender downloaded indecent child images at a hostel where he was staying after using another resident's wi-fi code. more
In this case, a stolen access code was used to gain access. In many organizations the same guest code is given out to all guests. Sometimes it is even posted. Often it is never changed. Once the password is out, there is no telling who will access the system, or when, or for what purpose.
Downloading illegal images is only one of many guest access risks.
While hiding behind a reputable IP address unauthorized and anonymous "guests" can also conduct: drug transactions, video voyeurism, blackmail, financial scams, hacking, and more. The finger points at the organization's network. They might be legally held responsible. And, these are just the outward facing threats. Guest access can also be a pivot point to internal information theft.
Take this 15 second assessment.
Does your organization...
Legal defense is expensive. Reputational damage is hard to quantify. A proactive professsional analysis is easy. Reduce risk and keep profits where they belong, in the bottom line.
In this case, a stolen access code was used to gain access. In many organizations the same guest code is given out to all guests. Sometimes it is even posted. Often it is never changed. Once the password is out, there is no telling who will access the system, or when, or for what purpose.
Downloading illegal images is only one of many guest access risks.
While hiding behind a reputable IP address unauthorized and anonymous "guests" can also conduct: drug transactions, video voyeurism, blackmail, financial scams, hacking, and more. The finger points at the organization's network. They might be legally held responsible. And, these are just the outward facing threats. Guest access can also be a pivot point to internal information theft.
Take this 15 second assessment.
Does your organization...
- Provide guest Wi-Fi access?
- Does guest access use the organization's network?
- Is access unencrypted?
- Do all guests use the same password?
- Is the password posted anywhere, as in a conference room?
- If posted, can it be seen from outside with binoculars or a drone?
- Has the password remained the same for over a month?
Legal defense is expensive. Reputational damage is hard to quantify. A proactive professsional analysis is easy. Reduce risk and keep profits where they belong, in the bottom line.
The Potato Chip Bag Spy
Back in 2014, the potato chip bag became an audio eavesdropping device...
Want to listen in on a juicy conversation? Researchers from the Massachusetts Institute of Technology, Microsoft, and Adobe have designed an algorithm that can pick up conversation by analyzing the vibrations from speech as they ripple through a potato chip bag, MIT News reports. more
In 2020, the potato chip bag became a visual eavesdropping device too...
Mirrors aren't the only shiny objects that reflect our surroundings. Turns out a humble bag of potato chips can pull off the same trick, as scientists from the University of Washington, Seattle have made it possible to recreate detailed images of the world from reflections in the snack's glossy wrapping.
The scientists took their work a step further by predicting how a room's likeness might appear from different angles, essentially "exploring" the room's reflection in a bag of chips as if they were actually present. This is analogous to a classical problem in computer vision and graphics: view synthesis, or the ability to create a new, synthetic view of a specific subject based on other images, taken at various angles. more
The future?
Want to listen in on a juicy conversation? Researchers from the Massachusetts Institute of Technology, Microsoft, and Adobe have designed an algorithm that can pick up conversation by analyzing the vibrations from speech as they ripple through a potato chip bag, MIT News reports. more
In 2020, the potato chip bag became a visual eavesdropping device too...
Mirrors aren't the only shiny objects that reflect our surroundings. Turns out a humble bag of potato chips can pull off the same trick, as scientists from the University of Washington, Seattle have made it possible to recreate detailed images of the world from reflections in the snack's glossy wrapping.
The scientists took their work a step further by predicting how a room's likeness might appear from different angles, essentially "exploring" the room's reflection in a bag of chips as if they were actually present. This is analogous to a classical problem in computer vision and graphics: view synthesis, or the ability to create a new, synthetic view of a specific subject based on other images, taken at various angles. more
The future?
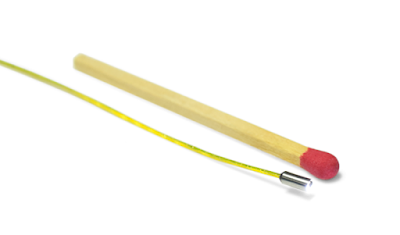
How Small Can a Video Camera Be?
Currently, one of the smallest we know is 1.66mm in size. It has a built-in high-intensity LED light. If you don't need the light it shrinks to .97mm in diameter.
Specs: Color, 120 degree lens, 200 x 200 @ 30fps resolution
Monday, March 30, 2020
Bosses Panic-Buy Spy Software...
... to keep tabs on remote workers.
“Companies have been scrambling,” said Brad Miller, CEO of surveillance-software maker InterGuard. “They’re trying to allow their employees to work from home but trying to maintain a level of security and productivity.”...
“It’s not because of lack of trust,” Miller said, who compared the software to banks using security cameras. “It’s because it’s imprudent not to do it.” more
“Companies have been scrambling,” said Brad Miller, CEO of surveillance-software maker InterGuard. “They’re trying to allow their employees to work from home but trying to maintain a level of security and productivity.”...
“It’s not because of lack of trust,” Miller said, who compared the software to banks using security cameras. “It’s because it’s imprudent not to do it.” more
Being Zoom'ed on Zoom has Organizations Worried, or they should be...
...experts warn that a rush to hold virtual meetings through
Zoom, which has close to 13m monthly active users, could pose security
risks.
The threat is so significant that British
Ministry of Defence staff were told this week that the use of Zoom was
being suspended with immediate effect while "security implications" were
investigated.
The biggest worry is that a sudden reliance on Zoom could allow
opportunistic hackers to quietly observe video calls as executives are
focused on responding to the spread of coronavirus.
...the idea of strangers barging into virtual meeting rooms should raise alarm. more
Online Zoom classes were disrupted by individuals spewing racist,
misogynistic or vulgar content. Experts say professors using Zoom should
familiarize themselves with the program's settings. more
Mysterious Hacker Group Eavesdropping on Corporate Email & FTP traffic
 Since at least early December 2019, a mysterious hacker group has been taking over DrayTek enterprise routers to eavesdrop on FTP and email traffic inside corporate networks...
Since at least early December 2019, a mysterious hacker group has been taking over DrayTek enterprise routers to eavesdrop on FTP and email traffic inside corporate networks...Instead of abusing the device to launch DDoS attacks or re-route traffic as part of a proxy network, the hackers turned into a spy-box...
...researchers didn't speculate why hackers were collecting FTP and email traffic. But speaking to ZDNet over the phone, a security researcher pointed out that this looked like a classic reconnaissance operation...
"It's obvious they're logging traffic to collect login credentials for FTP and email accounts," the researcher told ZDNet. "Those creds are flying unencrypted over the network. They're easy pickings." more
Tuesday, March 24, 2020
BBC Spycam Documentary
In a new BBC documentary Stacey Dooley Investigates: Spycam Sex Criminals.
The crime no doubt happens all over the world, but is actually one that has been sweeping South Korea lately, as many have been found guilty of planting recording equipment in public places and then charging people to view the footage online...
The upcoming documentary will see our fave reporter look into the subject head on to give us an insight into the voyeuristic practice and how now, with such advanced technology, it's easier than ever to hide cameras in public places.
Some of the cameras being used are as small as the head of a needle and are so difficult to spot, but Stacey will be taken on patrol with an experienced spy cam hunters to uncover hiding places.
Stacey Dooley Investigates: Spycam Sex Criminals will be available on iPlayer from 6am on 1st April - something to add to your quarantined watch list. more
The crime no doubt happens all over the world, but is actually one that has been sweeping South Korea lately, as many have been found guilty of planting recording equipment in public places and then charging people to view the footage online...
The upcoming documentary will see our fave reporter look into the subject head on to give us an insight into the voyeuristic practice and how now, with such advanced technology, it's easier than ever to hide cameras in public places.
Some of the cameras being used are as small as the head of a needle and are so difficult to spot, but Stacey will be taken on patrol with an experienced spy cam hunters to uncover hiding places.
Stacey Dooley Investigates: Spycam Sex Criminals will be available on iPlayer from 6am on 1st April - something to add to your quarantined watch list. more
Coronavirus Surveillance Escalates, Personal Privacy Plummets
Tracking entire populations to combat the pandemic now could open the doors to more invasive forms of government snooping later.
...government agencies are harnessing surveillance-camera footage, smartphone location data and credit card purchase records to help trace the recent movements of coronavirus patients and establish virus transmission chains...
...authorities are analyzing location data transmitted by citizens’ mobile phones to determine how many people are obeying a government lockdown order and the typical distances they move every day. About 40 percent are moving around “too much,” an official recently said.
...internal security agency is poised to start using a cache of mobile phone location data — originally intended for counterterrorism operations — to try to pinpoint citizens who may have been exposed to the virus...
...ratcheting up surveillance to combat the pandemic now could permanently open the doors to more invasive forms of snooping later. It is a lesson Americans learned after the terrorist attacks of Sept. 11, 2001, civil liberties experts say. more
...government agencies are harnessing surveillance-camera footage, smartphone location data and credit card purchase records to help trace the recent movements of coronavirus patients and establish virus transmission chains...
...authorities are analyzing location data transmitted by citizens’ mobile phones to determine how many people are obeying a government lockdown order and the typical distances they move every day. About 40 percent are moving around “too much,” an official recently said.
...internal security agency is poised to start using a cache of mobile phone location data — originally intended for counterterrorism operations — to try to pinpoint citizens who may have been exposed to the virus...
...ratcheting up surveillance to combat the pandemic now could permanently open the doors to more invasive forms of snooping later. It is a lesson Americans learned after the terrorist attacks of Sept. 11, 2001, civil liberties experts say. more
8 Steps to Control Cybersecurity Risk in a Work From Home Environment
During the COVID-19 pandemic and response, workers are heading home in record numbers. In this short 23-min. webinar, CI Security CTO Mike Simon covers the the critical work-from-home cybersecurity risks that employees need help with now.
The material is geared toward InfoSec and IT professionals, technical users, and team managers.
Top 8 Work From Home (WFH) Cybersecurity Priorities...
Step 1: Control the WFH Environment
Step 2: Control the WFH Computer
Step 3: Up Your Phishing Game
Step 4: Worry About Sensitive Documents and Regulated Data
Step 5: Watch for Cyber-Threats
Step 6: Expanding VPN
Step 7: Say No to Split-Tunnels
Step 8: Keep Great Records
The material is geared toward InfoSec and IT professionals, technical users, and team managers.
Top 8 Work From Home (WFH) Cybersecurity Priorities...
Step 1: Control the WFH Environment
Step 2: Control the WFH Computer
Step 3: Up Your Phishing Game
Step 4: Worry About Sensitive Documents and Regulated Data
Step 5: Watch for Cyber-Threats
Step 6: Expanding VPN
Step 7: Say No to Split-Tunnels
Step 8: Keep Great Records
Saturday, March 21, 2020
Remote Work, Security & Is Your Office Being Bugged While You're Home
It's a rule of thumb in cybersecurity that the more sensitive your system, the less you want it to touch the internet. But as the US hunkers down to limit the spread of Covid-19, cybersecurity measures present a difficult technical challenge to working remotely for employees... In some cases, working from home isn't an option at all...
Late last week, the US government's Cybersecurity and Infrastructure Security Agency issued an advisory to critical infrastructure companies to prepare for remote work scenarios as Covid-19 spreads...
But cybersecurity consultants who actually work with those high-stakes clients—including electric utilities, oil and gas firms, and manufacturing companies—say that it's not always so simple. For many of their most critical customers, and even more so for intelligence agencies, remote work and security don't mix. more
Special note to the business community...
Planting bugs is easy when your offices are empty. Business espionage types know this.
Quality TSCM sweep teams will be in demand and hard to book when Covid-19 subsides. Prepare now. Put your team on retainer.
If you don't have a quality provider contact us. We'll create a back-to-work inspection strategy, and a no-obligation estimate for you. ~Kevin
Late last week, the US government's Cybersecurity and Infrastructure Security Agency issued an advisory to critical infrastructure companies to prepare for remote work scenarios as Covid-19 spreads...
But cybersecurity consultants who actually work with those high-stakes clients—including electric utilities, oil and gas firms, and manufacturing companies—say that it's not always so simple. For many of their most critical customers, and even more so for intelligence agencies, remote work and security don't mix. more
Special note to the business community...
Planting bugs is easy when your offices are empty. Business espionage types know this.
Quality TSCM sweep teams will be in demand and hard to book when Covid-19 subsides. Prepare now. Put your team on retainer.
If you don't have a quality provider contact us. We'll create a back-to-work inspection strategy, and a no-obligation estimate for you. ~Kevin
Subscribe to:
Comments (Atom)