Canada - A judge has certified and approved a class action settlement against a late former Belleville orthodontist, who was alleged to have made video recordings of patients without their consent or knowledge. Dr. Anthony Garry Solomon had been charged with making and possessing child pornography, and voyeurism in 2017, but criminal charges were withdrawn following his death a short time later and a civil class action case has been underway for the past two and a half years. more
LA - More than 10 people who worked in the past for a Plaquemine snowball
stand manager accused of videotaping people in the shop's bathroom have
contacted the Iberville Parish Sheriff's Office since the manager's
arrest on May 2, making a current total of 24 employees who may have
been affected, Sheriff Brett Stassi said Friday. more more
LA - The Assumption Parish Chamber of Commerce chairman was arrested in St.
Gabriel this week after filming a man in public bathroom without
consent, authorities said. more
Canada - Multiple charges relating to voyeurism and child pornography have been
laid against a Clarington resident who police say formerly worked as a
self-employed handyman. more
Namibia - Up to 34 children could be involved in a case in which a Windhoek resident yesterday appeared in cour..."The videos contain various children performing sexual acts in a
bathroom where a covert camera was [suspected to have been] set up,"
Shikwambi said. "Videos were also obtained from a covert camera placed
in a toilet at a sporting event inWindhoek recording minor boys visiting
the toilet at a municipal swimming pool."
UK - A man has appeared in court accused of killing his wife in an arson
attack after spying on her with secret cameras and posting sexually
explicit images of her online. more
FL - A Pensacola man is accused of secretly filming women in a Lowe's bathroom, according to a sheriff's report. more
UK - Coronation Street (a TV show) fans were left frustrated last
night after the police failed to find Geoff's hidden camera. During the
months that Geoff has been abusing Yasmeen, he set up a secret camera to
spy on his wife. more
You know spy cameras are a big problem it becomes a popular TV show plot.
Updated: Spy Camera Detectors – Do they work?
Saturday, May 9, 2020
Tuesday, May 5, 2020
Air-Gapped PC Power Supplies Spills the Screens
One of the most secure system arrangements today consists of air-gapped PCs. The reason being their total disconnection from the internet.
In February this year, it was reported that hackers can steal data from air-gapped PC using screen brightness and now the same can be done through their power supply.
Mordechai Guri, a cybersecurity researcher from the Israeli Ben Gurion of the Negev University has conducted an experiment that shows how power supply units (PSUs) can be exploited to extract information from both an air-gapped & audio-gapped computer.
Termed as POWER-SUPPLaY; the malware exploits the PSU using it as an “out-of-band, secondary speaker with limited capabilities”. The data that can be extracted includes different files & information of the user’s keystrokes transmittable up to 1 meters away along with passwords and encryption keys that the attacker could receive with a device that is five meters away from such as a smartphone...
The research does not deal with the question of how the malware will be implemented in the first place. The technique is very clever nonetheless. more
In February this year, it was reported that hackers can steal data from air-gapped PC using screen brightness and now the same can be done through their power supply.
Mordechai Guri, a cybersecurity researcher from the Israeli Ben Gurion of the Negev University has conducted an experiment that shows how power supply units (PSUs) can be exploited to extract information from both an air-gapped & audio-gapped computer.
Termed as POWER-SUPPLaY; the malware exploits the PSU using it as an “out-of-band, secondary speaker with limited capabilities”. The data that can be extracted includes different files & information of the user’s keystrokes transmittable up to 1 meters away along with passwords and encryption keys that the attacker could receive with a device that is five meters away from such as a smartphone...
The research does not deal with the question of how the malware will be implemented in the first place. The technique is very clever nonetheless. more
TSCM Nightmares Today, Reality Tomorrow
These give some technical surveillance countermeasures specialists nightmares.
Emerging technologies like the ones below are interesting. They could be used for illegal eavesdropping in the future. Combining the first two could produce a wireless bug that never has to have its batteries replaced. It could also be incredibly small.
Some people say, "the bad guys are always one step ahead of us."
I say, "do your homework and you will be one step ahead of them."
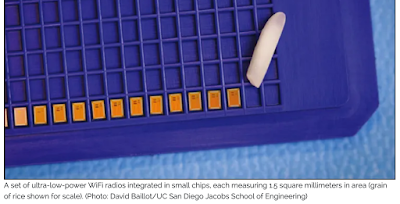
Ultra-Low-Power WiFi Radio Enables IoT Devices
It consumes just 28 microwatts of power and does so while transmitting data at a rate of 2 megabits per second (a connection fast enough to stream music and most YouTube videos) over a range of up to 21 meters.
New Green Technology from UMass Amherst Generates Electricity ‘Out of Thin Air’
 The laboratories of electrical engineer Jun Yao and microbiologist Derek
Lovley at UMass Amherst have created a device they call an “Air-gen.”
or air-powered generator, with electrically conductive protein nanowires
produced by the microbe Geobacter.
The laboratories of electrical engineer Jun Yao and microbiologist Derek
Lovley at UMass Amherst have created a device they call an “Air-gen.”
or air-powered generator, with electrically conductive protein nanowires
produced by the microbe Geobacter.
The Air-gen connects electrodes to the protein nanowires in such a way that electrical current is generated from the water vapor naturally present in the atmosphere. “We are literally making electricity out of thin air,” says Yao.
Seeing Around Corners to Detect Object Shapes
Special light sources and sensors see around corners or through gauzy filters, enabling reconstruction of the shapes of unseen objects.
A technique was developed that enables reconstruction of images in great detail. Researchers computed millimeter- and micrometer-scale shapes of curved objects, providing an important component to a larger suite of non-line-of-sight (NLOS) imaging techniques.
Most of what people see — and what cameras detect — comes from light that reflects off an object and bounces directly to the eye or the lens. But light also reflects off the objects in other directions, bouncing off walls and objects.

Emerging technologies like the ones below are interesting. They could be used for illegal eavesdropping in the future. Combining the first two could produce a wireless bug that never has to have its batteries replaced. It could also be incredibly small.
Some people say, "the bad guys are always one step ahead of us."
I say, "do your homework and you will be one step ahead of them."
Ultra-Low-Power WiFi Radio Enables IoT Devices
- Housed in a chip, it lets IoT devices communicate with existing WiFi networks.
- Housed in a chip smaller than a grain of rice.
- The radio could last for years on a single coin cell battery.
It consumes just 28 microwatts of power and does so while transmitting data at a rate of 2 megabits per second (a connection fast enough to stream music and most YouTube videos) over a range of up to 21 meters.
New Green Technology from UMass Amherst Generates Electricity ‘Out of Thin Air’
 The laboratories of electrical engineer Jun Yao and microbiologist Derek
Lovley at UMass Amherst have created a device they call an “Air-gen.”
or air-powered generator, with electrically conductive protein nanowires
produced by the microbe Geobacter.
The laboratories of electrical engineer Jun Yao and microbiologist Derek
Lovley at UMass Amherst have created a device they call an “Air-gen.”
or air-powered generator, with electrically conductive protein nanowires
produced by the microbe Geobacter.The Air-gen connects electrodes to the protein nanowires in such a way that electrical current is generated from the water vapor naturally present in the atmosphere. “We are literally making electricity out of thin air,” says Yao.
Seeing Around Corners to Detect Object Shapes
Special light sources and sensors see around corners or through gauzy filters, enabling reconstruction of the shapes of unseen objects.
A technique was developed that enables reconstruction of images in great detail. Researchers computed millimeter- and micrometer-scale shapes of curved objects, providing an important component to a larger suite of non-line-of-sight (NLOS) imaging techniques.
Most of what people see — and what cameras detect — comes from light that reflects off an object and bounces directly to the eye or the lens. But light also reflects off the objects in other directions, bouncing off walls and objects.

Monday, May 4, 2020
Trade Secret Protection in a Nutshell
 |
| Trade Secret Law in a Nutshell (book) |
- The information is actually secret,
- the business has taken "reasonable measures" to keep it so,
- and the information has "independent economic value" because it's unknown to others who could profit from it.
Spy vs. Spy - The Movie
The Spy vs. Spy comic strip has been a regular fixture in Mad magazine for almost sixty years. In that time, the two identical birdlike espionage agents — Black Spy and White Spy — have also featured in video games and cartoons, but a live-action big-screen adaptation has continually eluded the warring duo. However, that could all finally change, if new developments go according to plan.
According to Collider, Rawson Marshall Thurber is in talks to direct the movie for Warner Bros. and Imagine Entertainment. Ron Howard and Brian Grazer are on board as producers, which makes sense as they’ve been attached to the project since its inception. It remains to be seen if Dwayne Johnson will star, but that wouldn’t be surprising as he’s Thurber’s go-to guy...
The movie, as silly as it will undoubtedly be, might also be very smart and biting. The original comics are rife with political satire, often taking aim at America’s involvement in wars. Given that there’s still plenty of real-life drama to comment on, don’t be surprised if the movie pokes fun at current affairs...
If the film lives up to its potential, Spy vs. Spy will be one entertaining, wacky ride. more
According to Collider, Rawson Marshall Thurber is in talks to direct the movie for Warner Bros. and Imagine Entertainment. Ron Howard and Brian Grazer are on board as producers, which makes sense as they’ve been attached to the project since its inception. It remains to be seen if Dwayne Johnson will star, but that wouldn’t be surprising as he’s Thurber’s go-to guy...
The movie, as silly as it will undoubtedly be, might also be very smart and biting. The original comics are rife with political satire, often taking aim at America’s involvement in wars. Given that there’s still plenty of real-life drama to comment on, don’t be surprised if the movie pokes fun at current affairs...
If the film lives up to its potential, Spy vs. Spy will be one entertaining, wacky ride. more
Labels:
#cartoon,
#espionage,
#weird,
cautionary tale,
fun,
FutureWatch,
movie,
spy
Friday, May 1, 2020
Spycam Detection Course | Now With Korean Closed Captions
The highly rated Spycam Detection video training course now has Korean closed captions, as well as English. Spanish is coming soon.
The demand for a Korean translation was fueled by their epidemic spy camera problem. They even have a special word for it, Molka. The problem is so bad the government created special inspection squads and a safety handbook for the public.
In other countries the problem is also epidemic.
This one-hour, self-paced course was originally created for businesses and other organizations to train their security and facilities employees. Having these people conduct periodic inspections reduces risk and legal exposure. A Certificate-of-Completion is awarded at the end.
The training is also beneficial for police, private investigators and executive protection professionals.
Personal protection is the most effective prevention. Knowing what to look for is important. The course is open to everyone. Any individual with a little knowledge can conduct their own inspections of:
As more people become knowledgeable, fewer people will become victims.
The demand for a Korean translation was fueled by their epidemic spy camera problem. They even have a special word for it, Molka. The problem is so bad the government created special inspection squads and a safety handbook for the public.
In other countries the problem is also epidemic.
This one-hour, self-paced course was originally created for businesses and other organizations to train their security and facilities employees. Having these people conduct periodic inspections reduces risk and legal exposure. A Certificate-of-Completion is awarded at the end.
The training is also beneficial for police, private investigators and executive protection professionals.
Personal protection is the most effective prevention. Knowing what to look for is important. The course is open to everyone. Any individual with a little knowledge can conduct their own inspections of:
- hotel rooms,
- public restroom,
- store changing rooms,
- locker rooms,
- vacation rentals,
- and their own domiciles.
As more people become knowledgeable, fewer people will become victims.
Eavesdropper Scams Financial Advisor | Prevention Tips
Early in April, a financial advisor and her team met with an insurance company wholesaler via the video conferencing platform Zoom.
Unbeknownst to them, another participant had joined the virtual meeting.
As the hacker captured details, the wholesaler named the price of a new policy and the advisor agreed to the terms.
 ...It’s likely that even before the meeting ended the eavesdropper generated an email to the advisor so that it appeared to come from the insurer. In a later forensic analysis, an overlooked detail revealed the spoof: a single letter the hacker changed in the insurance company’s name.
...It’s likely that even before the meeting ended the eavesdropper generated an email to the advisor so that it appeared to come from the insurer. In a later forensic analysis, an overlooked detail revealed the spoof: a single letter the hacker changed in the insurance company’s name.
After the meeting ended, the advisor received the message with instructions to wire money — in the low six figures — to a New York bank account. She did as instructed, sending the money to the hacker. more
———How to prevent Zoombombing in your video chats in 4 easy steps———
1. Don't use your Personal Meeting ID for the meeting. Instead, use a per-meeting ID, exclusive to a single meeting. Zoom's support page offers a video walk-through on how to generate a random meeting ID for extra security.
2. Enable the "Waiting Room" feature so that you can see who is attempting to join the meeting before allowing them access. Like many other privacy functions, a skillful disrupter can sometimes bypass this control, but it helps to put another hurdle in their route to chaos.
Zoom offers a support article here as well. To enable the Waiting Room feature, go to Account Management > Account Settings. Click on Meeting, then click Waiting Room to enable the setting.
3. Disable other options, including the ability for others to Join Before Host (it should be disabled by default, but check to be sure -- see below). Then disable screen-sharing for nonhosts, and also the remote control function. Finally, disable all file transferring, annotations and the autosave feature for chats...
4. Once the meeting begins and everyone is in, lock the meeting to outsiders ... and assign at least two meeting co-hosts. The co-hosts will be able to help control the situation in case anyone bypasses your efforts and gets into the meeting. more
Unbeknownst to them, another participant had joined the virtual meeting.
As the hacker captured details, the wholesaler named the price of a new policy and the advisor agreed to the terms.
 ...It’s likely that even before the meeting ended the eavesdropper generated an email to the advisor so that it appeared to come from the insurer. In a later forensic analysis, an overlooked detail revealed the spoof: a single letter the hacker changed in the insurance company’s name.
...It’s likely that even before the meeting ended the eavesdropper generated an email to the advisor so that it appeared to come from the insurer. In a later forensic analysis, an overlooked detail revealed the spoof: a single letter the hacker changed in the insurance company’s name.After the meeting ended, the advisor received the message with instructions to wire money — in the low six figures — to a New York bank account. She did as instructed, sending the money to the hacker. more
———How to prevent Zoombombing in your video chats in 4 easy steps———
1. Don't use your Personal Meeting ID for the meeting. Instead, use a per-meeting ID, exclusive to a single meeting. Zoom's support page offers a video walk-through on how to generate a random meeting ID for extra security.
2. Enable the "Waiting Room" feature so that you can see who is attempting to join the meeting before allowing them access. Like many other privacy functions, a skillful disrupter can sometimes bypass this control, but it helps to put another hurdle in their route to chaos.
Zoom offers a support article here as well. To enable the Waiting Room feature, go to Account Management > Account Settings. Click on Meeting, then click Waiting Room to enable the setting.
3. Disable other options, including the ability for others to Join Before Host (it should be disabled by default, but check to be sure -- see below). Then disable screen-sharing for nonhosts, and also the remote control function. Finally, disable all file transferring, annotations and the autosave feature for chats...
4. Once the meeting begins and everyone is in, lock the meeting to outsiders ... and assign at least two meeting co-hosts. The co-hosts will be able to help control the situation in case anyone bypasses your efforts and gets into the meeting. more
Wednesday, April 29, 2020
Robot 'Spy' Gorilla Records Wild Gorillas Singing and Farting
This is the first time that singing mountain gorillas have been caught on camera.
 (Image: © Copyright John Downer Productions)
(Image: © Copyright John Downer Productions)
Mountain gorillas have been caught on camera as they "sing" during their supper, a behavior that has never before been documented on video. Filmmakers captured the astonishing footage of the primate crooners with a little help from a very special camera: a robotic "spy" designed to look like a young gorilla.
The singing apes make their television debut on April 29 in the returning PBS series, "Nature: Spy in the Wild 2."
Like its predecessor, which first aired in 2017, the program documents remarkable up-close glimpses of elusive wildlife behavior, seen through the "eyes" of robots that are uncanny lookalikes of the creatures that they film. more sing-a-long
 (Image: © Copyright John Downer Productions)
(Image: © Copyright John Downer Productions) Mountain gorillas have been caught on camera as they "sing" during their supper, a behavior that has never before been documented on video. Filmmakers captured the astonishing footage of the primate crooners with a little help from a very special camera: a robotic "spy" designed to look like a young gorilla.
The singing apes make their television debut on April 29 in the returning PBS series, "Nature: Spy in the Wild 2."
Like its predecessor, which first aired in 2017, the program documents remarkable up-close glimpses of elusive wildlife behavior, seen through the "eyes" of robots that are uncanny lookalikes of the creatures that they film. more sing-a-long
'Zoom-bombed' | Salary Cuts Call Eavesdropped on by Rival Company
Mark Di Stefano, a reporter with the Financial Times, allegedly entered meetings held over the video conferencing app by the Independent and the Evening Standard.
Stefano, according to the Independent, brazenly joined the meeting by using his work email address. This caused Stefano’s name to appear on the call, although his camera remained disabled.
The journalist reportedly joined for 16 seconds before logging out but returned soon after by logging in with his phone number.
Not long after the call, Stefano sent out a series of tweets describing topics that the Independent says were discussed during the staff meeting.
Stefano described information on everything from pay cuts to the outlet’s issues with falling ad revenue. more
Related News...
DHS Reportedly Concerned Zoom May be Vulnerable to Foreign Spies
The feds are concerned that Zoom’s security flaws could make the popular videoconferencing platform vulnerable to foreign spies, a new report says.
An intelligence analysis from the Department of Homeland Security found that Zoom’s explosive growth and its well-known security problems make it a “target-rich environment” for government spy services and other hackers, ABC News reported Tuesday.
“Any organization currently using — or considering using — Zoom should evaluate the risk of its use,” the department warned in the analysis, which was reportedly distributed to law enforcement agencies around the US. more
...and much more.
Labels:
#eavesdropping,
#espionage,
#hack,
business,
cybersecurity,
dumb,
employee,
spy,
video,
wiretapping
Spies Keep Sneaking Malware Into Google Play
Google's Play Store for Android apps has never had a reputation for the strictest protections from malware. Shady adware and even banking trojans have managed over the years to repeatedly defy Google's security checks.
Now security researchers have found what appears to be a more rare form of Android abuse: state-sponsored spies who repeatedly slipped their targeted hacking tools into the Play Store and onto victims' phones.
At a remote virtual version of its annual Security Analyst Summit, researchers from the Russian security firm Kaspersky today plan to present research about a hacking campaign they call PhantomLance, in which spies hid malware in the Play Store...
Once Kaspersky had identified the PhantomLance apps, its researchers were able to match their code with older malware used by OceanLotus, which has been active since at least 2013. more
Now security researchers have found what appears to be a more rare form of Android abuse: state-sponsored spies who repeatedly slipped their targeted hacking tools into the Play Store and onto victims' phones.
At a remote virtual version of its annual Security Analyst Summit, researchers from the Russian security firm Kaspersky today plan to present research about a hacking campaign they call PhantomLance, in which spies hid malware in the Play Store...
Once Kaspersky had identified the PhantomLance apps, its researchers were able to match their code with older malware used by OceanLotus, which has been active since at least 2013. more
New Spy Podcast
Labels:
#espionage,
App,
fun,
government,
GRU,
miscellaneous,
Spy Museum
Thursday, April 23, 2020
A Sad Case Highlights Perception of Privacy Loss and Mental Health
WA - A suicidal man who was shot and killed by police officers at a Loves truck stop in Ritzville called police twice to report that his car was bugged and that he was being tracked, according to a release by the Columbia Basin Investigative Team. more
A Global Recession Will Fuel Cyber-Espionage
While the current pandemic crisis presents businesses with unprecedented
economic challenges to their very existence, it has also created a
tremendous level of cyber-risks.
Heightened risks are present not only due to the significant numbers of individuals working from home, increasing the vulnerability landscape, but also because as states fall deeper into recessions, some may resort to cyber-espionage in an attempt to position better their post-pandemic political, economic, and industrial structures.
Regardless of the industry, the intellectual property (IP) of any organization is likely to be a precious target for foreign government-sponsored hackers...
Managing the crisis, in reality, can be much more complex and a nightmare for decision-makers. However, flexible, agile, and governments that are being flexible and adaptable while at the same time prioritizing their cybersecurity measures and counter-espionage efforts are more prone to survive the crisis as well as sustain domestic business operations with minimal loss. more
Heightened risks are present not only due to the significant numbers of individuals working from home, increasing the vulnerability landscape, but also because as states fall deeper into recessions, some may resort to cyber-espionage in an attempt to position better their post-pandemic political, economic, and industrial structures.
Regardless of the industry, the intellectual property (IP) of any organization is likely to be a precious target for foreign government-sponsored hackers...
Managing the crisis, in reality, can be much more complex and a nightmare for decision-makers. However, flexible, agile, and governments that are being flexible and adaptable while at the same time prioritizing their cybersecurity measures and counter-espionage efforts are more prone to survive the crisis as well as sustain domestic business operations with minimal loss. more
This Week in Spycam News
UVM Medical Center Doctor Hid Camera in Staff Bathroom
The emergency department doctor and assistant professor is facing several voyeurism charges after hospital security discovered the hidden camera. more
Man faces felony accusation of viewing girl through camera in alarm clock...
When interviewed by police, the girl said she knew the camera was there because of a "dot" on the front of the clock and that camera's presence made her "uncomfortable" and "creeped out." On Valentine's Day, the girl placed a series of heart-shaped stickers on the clock to decorate it, while also blocking the camera's view. more
Former head golf professional classified as Tier I sex offender...
Mohawk Golf & Country Club’s former head golf professional who was charged after a recording device was found in a women’s locker room was classified as a Tier I sex offender today. more
The emergency department doctor and assistant professor is facing several voyeurism charges after hospital security discovered the hidden camera. more
Man faces felony accusation of viewing girl through camera in alarm clock...
When interviewed by police, the girl said she knew the camera was there because of a "dot" on the front of the clock and that camera's presence made her "uncomfortable" and "creeped out." On Valentine's Day, the girl placed a series of heart-shaped stickers on the clock to decorate it, while also blocking the camera's view. more
Former head golf professional classified as Tier I sex offender...
Mohawk Golf & Country Club’s former head golf professional who was charged after a recording device was found in a women’s locker room was classified as a Tier I sex offender today. more
IR Eye of Ra, or The Drone Patrol
Police in Westport, Connecticut, announced this week that they’re testing a so-called “pandemic drone” that can detect when people on the ground have fevers.
The new drone platform will also be used to determine when people are closer than six feet to each other. Police will be able to deliver a verbal warning through the drone’s speaker to anyone not practicing social distancing.
The new drone technology was developed by a company called Draganfly Inc., which has been around since the late 1990s, and uses Westport PD’s existing quadcopter drones with Draganfly’s software. Draganfly worked with a deep-learning company called Vital Intelligence Inc. and researchers from the University of South Australia to develop the new tech, according to a press release. more
The new drone platform will also be used to determine when people are closer than six feet to each other. Police will be able to deliver a verbal warning through the drone’s speaker to anyone not practicing social distancing.
The new drone technology was developed by a company called Draganfly Inc., which has been around since the late 1990s, and uses Westport PD’s existing quadcopter drones with Draganfly’s software. Draganfly worked with a deep-learning company called Vital Intelligence Inc. and researchers from the University of South Australia to develop the new tech, according to a press release. more
Wednesday, April 22, 2020
What 007 is Doing These Days
British Spy Unit Kills 2,000 COVID-19 Scams In Just One Month
Across the world, law enforcement and intelligence agencies are waging a different kind of war on COVID-19, one taking on scammers who’re exploiting fear around the coronavirus.
In the U.K., an arm of the GCHQ intelligence agency, has spent the last month wiping COVID-19 crooks from the web, with the National Cyber Security Centre (NCSC) announcing Monday that it had taken down more than 2,000 scams in a single month. more
Across the world, law enforcement and intelligence agencies are waging a different kind of war on COVID-19, one taking on scammers who’re exploiting fear around the coronavirus.
In the U.K., an arm of the GCHQ intelligence agency, has spent the last month wiping COVID-19 crooks from the web, with the National Cyber Security Centre (NCSC) announcing Monday that it had taken down more than 2,000 scams in a single month. more
Some Landlords Illegally Spying On Tenants’ Stimulus Check Status
While millions are awaiting their payments to help with necessities,
landlords are also eager for their tenants to receive stimulus checks,
so they can pay rent. Unfortunately, some landlords have not just been
waiting patiently...
In order to help Americans to track the status of their stimulus payments, the IRS and Treasury Department launched a new tool, Get My Payment. The tool provides individuals “with the status of your payment, including the date your payment is scheduled to be deposited into your bank account or mailed.”...
In order to check the status of a stimulus payment, one only needs to provide basic information, including name, date of birth, street address, and Social Security Number (SSN) ... This basic information is readily available on the dark web ... it is also readily available to many landlords through the applications that tenants complete when applying to rent a property.
You may want to speak with a lawyer to evaluate options if your landlord checks your payment status on the IRS portal. You may also want to consider filing a police report. more
In order to help Americans to track the status of their stimulus payments, the IRS and Treasury Department launched a new tool, Get My Payment. The tool provides individuals “with the status of your payment, including the date your payment is scheduled to be deposited into your bank account or mailed.”...
In order to check the status of a stimulus payment, one only needs to provide basic information, including name, date of birth, street address, and Social Security Number (SSN) ... This basic information is readily available on the dark web ... it is also readily available to many landlords through the applications that tenants complete when applying to rent a property.
You may want to speak with a lawyer to evaluate options if your landlord checks your payment status on the IRS portal. You may also want to consider filing a police report. more
Monday, April 20, 2020
7 Espionage Tricks to Avoid While Working From Home
Don't get tricked into giving away personal information.
Why? Because this is what you use for your passwords.
Why? Because this is what you use for your passwords.
- Facebook Quizzes
Quizzes are all over Facebook: What does your eye color say about you? What kind of dog are you according to your zodiac sign? (Facebook says these were questions the criminals used.) - 10 Things About You
As people try to connect during the stay-at-home order, they are answering cut-and-paste questionnaires from their friends. They usually start with something like “Tell me 10 things I don’t know about you” and go on to ask questions like: Who was your first love? ... Here's the problem: those are the exact same questions asked when you forget your password. So, be wary of posting the answers on social media.
- Posting Information about Your Passwords
People are posting all sorts of information about what’s going on at their homes with their children or with their pets. That’s fine, unless they use those same names as their passwords. - Photos of the Home Work Station
At this point, people are pretty proud of their work from home stations. They have a new webcam, a makeshift desk, and maybe even a good microphone. But posting photos of that home work station might give criminals too much information. Can someone see the screen from a window? Are they giving away the brands and models of their IoT devices (which might or might not have exploitable vulnerabilities)? - Clicking Questionable Links
There are a lot of questionable links on the internet. Users should be wary of sites they don’t recognize. While this is rudimentary advice, it’s a good reminder that the headline “New Pandemic Cure No One Is Talking About” likely leads to a malicious site. - Be Aware of What’s Public
Savvy users have changed their Facebook and Instagram profile settings to make them more private. But as soon as you post to a group or comment on someone’s post without strong privacy settings, folks outside your friend's group can see what you’re doing. And, other sites like Twitter and Reddit are not generally private. more
Labels:
#espionage,
#hack,
advice,
amateur,
business,
cybersecurity,
employee,
privacy,
Tips
Sunday, April 19, 2020
10 Best Spy Comedy Films, Ranked (According To IMDb)
There are better things to do other than watch CNN (Covid-19 News) 24/7.
Here are some suggestions. ~Kevin
A Few Others
Here are some suggestions. ~Kevin
- Mr. & Mrs. Smith (6.5)
- Burn After Reading (7.0)
- Red (7.0)
- Spy (7.0)
- Austin Powers: International Man Of Mystery (7.0)
- Top Secret! (7.2) *****
- True Lies (7.2)
- The Man From U.N.C.L.E. (7.3)
- Despicable Me (7.6)
- Kingsman: The Secret Service (7.7)
A Few Others
- Spies Like Us
- The Man Who Knew Too Little
- The Spy Who Dumped Me
- Despicable Me 2 / 3
- My Spy
- Johnny English / Strikes Again / Reborn
- Keeping Up with the Joneses
- This Means War
- Central Intelligence
- Kingsmen: The Golden Circle
- The Spy Next Door
- Austin Powers: The Spy Who Shagged Me / Goldmember
- Get Smart
- OSS 117 Cairo (subtitles)
- Casino Royale
- Spy Hard
- Knight and Day
- Agent Cody Banks / Destination London
- Spy Kids / 2 / All the time in the World (kids)
- Our Man Flint / In Like Flint
- Confessions of a Dangerous Mind
- The Tailor Of Panama
- Undercover Blues
- Undercover Brother
- The Man With One Red Shoe
- The Tall Blond Man with One Black Shoe (subtitles)
- If Looks Could Kill
- Red 2
- The President's Analyst
- Spies in Disguise (kids)
- What’s Up, Tiger Lily?
- Gotcha!
- Jumpin' Jack Flash
- My Favorite Spy
- Real Men
- The Glass Bottom Boat
- The In-Laws
- Rio Rita
- A Southern Yankee
- The Tuxedo
- One Of Our Dinosaurs Is Missing
- Rendezvous
- The Fastest Guitar Alive (one star)
"The Warehouse" by Rob Hart (book)
"A chilling and all-too-believable portrait of a not-so-far-off future where free will succumbs to big business."--Alafair Burke, New York Times bestselling author of The Better Sister

more
The Machine Never Blinks: A Graphic History of Spying and Surveillance (book)
In The Machine Never Blinks, the story of surveillance is presented from its earliest days, to help you more fully understand today's headlines about every-increasing, constant, and unrelenting monitoring and global data collection.
This book spans surveillance from the Trojan Horse, through 9/11 and to the so-called War on Terror, which enabled the exponential growth of government and corporate intercepts and databases.
It also explains spying as entertainment (reality TV) and convenience (smart speakers). Take a look around... Who's watching you right now? Black & white illustrations. more
This book spans surveillance from the Trojan Horse, through 9/11 and to the so-called War on Terror, which enabled the exponential growth of government and corporate intercepts and databases.
It also explains spying as entertainment (reality TV) and convenience (smart speakers). Take a look around... Who's watching you right now? Black & white illustrations. more
Office Printers: The Ticking IT Time Bomb
Unsecured printers are one of the items on our inspection checklist. Why? Because it is a very common problem. Normally buttoned-up networks put out a hacker welcome mat with just one unsecured printer. ~Kevin
Office printers don’t have to be security threats: with foresight and maintenance they’re very easily threat-proofed. The problem is that system administrators rarely give the humble printer (or scanner, or multifunction printer) much attention.
Hackers haven’t forgotten about printers – not by a long shot. Last summer, a Russian hacker group penetrated numerous organizations by first infiltrating unprotected printers, which were connected to the same network as every other device, and then laddering up to exploit increasingly sensitive areas.
Furthermore, according to a recent report, foreign governments can also easily conduct industrial espionage by targeting this under-the-radar beachhead into the organizational networks...
Using third parties to continually help identify security risks is a smart course of action for enterprises that are truly serious about security measures. more
Office printers don’t have to be security threats: with foresight and maintenance they’re very easily threat-proofed. The problem is that system administrators rarely give the humble printer (or scanner, or multifunction printer) much attention.
Hackers haven’t forgotten about printers – not by a long shot. Last summer, a Russian hacker group penetrated numerous organizations by first infiltrating unprotected printers, which were connected to the same network as every other device, and then laddering up to exploit increasingly sensitive areas.
Furthermore, according to a recent report, foreign governments can also easily conduct industrial espionage by targeting this under-the-radar beachhead into the organizational networks...
Using third parties to continually help identify security risks is a smart course of action for enterprises that are truly serious about security measures. more
Managers: Don’t Rush to Workplace Spyware during Pandemic
A Rutgers organizational psychologist explains ramifications of putting spy software in place.
With millions of employees working remotely due to the coronavirus pandemic, managers—likely new to virtual management—are scrambling to find the best ways to oversee them online.
Computer performance monitoring may interest those looking for “an extra set of eyes,” but workplace surveillance is not that simple, according to John Aiello, an expert in organizational psychology at Rutgers School of Arts and Sciences.“While spy software may relieve the manager’s anxieties, organizations will see an increase in stress on employees and it could decrease productivity,” said Aiello, who has researched the electronic monitoring of workers over the last three decades.
Topics addressed...
How does monitoring software affect productivity?
How does implementing this surveillance affect managers?
Can electronic monitoring be used for “the greater good?”
If employers are thinking about implementing this surveillance, what might be done first?
more
With millions of employees working remotely due to the coronavirus pandemic, managers—likely new to virtual management—are scrambling to find the best ways to oversee them online.
Computer performance monitoring may interest those looking for “an extra set of eyes,” but workplace surveillance is not that simple, according to John Aiello, an expert in organizational psychology at Rutgers School of Arts and Sciences.“While spy software may relieve the manager’s anxieties, organizations will see an increase in stress on employees and it could decrease productivity,” said Aiello, who has researched the electronic monitoring of workers over the last three decades.
Topics addressed...
How does monitoring software affect productivity?
How does implementing this surveillance affect managers?
Can electronic monitoring be used for “the greater good?”
If employers are thinking about implementing this surveillance, what might be done first?
more
Thursday, April 16, 2020
Gad Zoox - Tesla Settles Trade Secret Theft Law Suit
Zoox Inc. said on Tuesday it had settled a lawsuit with Tesla Inc. after admitting that some new hires from the electric carmaker were in possession of certain Tesla documents when they joined the U.S. self-driving car startup.
Tesla lawyers filed a lawsuit in March last year against four former employees and Zoox, alleging the employees stole proprietary information and trade secrets for developing warehousing, logistics and inventory control operations.
Zoox said the settlement required it to pay Tesla an undisclosed amount and undergo an audit to ensure that none of its employees had retained or are using Tesla's confidential information. more
Tesla lawyers filed a lawsuit in March last year against four former employees and Zoox, alleging the employees stole proprietary information and trade secrets for developing warehousing, logistics and inventory control operations.
Zoox said the settlement required it to pay Tesla an undisclosed amount and undergo an audit to ensure that none of its employees had retained or are using Tesla's confidential information. more
Zeroing in on Zoom’s Threat to Financial Services
COVID-19 has induced a significant shift in the way we work. Remote is the new reality.
There may be, however, a tremendous cost to Zoom’s convenience... For many, Zoom has been the answer to staying connected in the workplace.
Simply put, the widespread adoption of Zoom amid a global pandemic might be the security vulnerability of the decade.
In fact, any financial services organization using the service should immediately assume their user credentials are under malicious parties’ control.
In recent weeks, New York Attorney General Letitia James has probed Zoom’s data security strategy, and whether the company’s security protections can keep up with the spike in users. It is also our understanding the FBI, among other federal government agencies, has also prohibited the use of Zoom and WebEx due to security concerns. more
Suit Claims Facebook, LinkedIn Eavesdropped on Zoom Calls
More Zoom news.
There may be, however, a tremendous cost to Zoom’s convenience... For many, Zoom has been the answer to staying connected in the workplace.
Simply put, the widespread adoption of Zoom amid a global pandemic might be the security vulnerability of the decade.
In fact, any financial services organization using the service should immediately assume their user credentials are under malicious parties’ control.
In recent weeks, New York Attorney General Letitia James has probed Zoom’s data security strategy, and whether the company’s security protections can keep up with the spike in users. It is also our understanding the FBI, among other federal government agencies, has also prohibited the use of Zoom and WebEx due to security concerns. more
Suit Claims Facebook, LinkedIn Eavesdropped on Zoom Calls
More Zoom news.
Business Espionage - You Staying in Jail
U.S. District Judge Ronnie Greer Wednesday temporarily stayed – or
postponed – the pretrial release of Xiorong “Shannon” You, a 56-year-old
Chinese-born chemical engineer accused of stealing $17 million in trade
secrets from Eastman Chemical Company and more than $100 million more
while working for Coca-Cola in Atlanta, according to court documents. more
Spycam Story # 834 - Deputy Danner Investigates Rectangular Turd
FL - Citrus County Sheriff’s Office deputies following up on a tip ... led to an investigation and arrest of a Dunnellon man for
video voyeurism, according to a Citrus County Sheriff’s Office arrest
affidavit...
Upon observing the interior of the portable toilet, the deputies could observe a black box-type object floating in the water, the report stated. (a la Caddyshack pool scene)
Deputy Danner was able to safely retrieve the object from the toilet. Deputies noted the item was a portable Brickhouse security camera. They were able to remove the subscriber identity module (SIM) card (more accurately an SD card) located inside the camera.
Deputies observed multiple files on the SIM card and opened one. At the 16:39.48 timestamp mark deputies observed a white male subject wearing a collared white, red, blue and green striped shirt with white/khaki shorts affixing the camera to the inside of the toilet...
Deputies confirmed he was wearing the same clothing found on the file located on the SIM card where he placed the camera in the toilet. more (You can't make this sh-t up. Perp gets the Darwin Award from us for filming himself.)
Upon observing the interior of the portable toilet, the deputies could observe a black box-type object floating in the water, the report stated. (a la Caddyshack pool scene)
Deputy Danner was able to safely retrieve the object from the toilet. Deputies noted the item was a portable Brickhouse security camera. They were able to remove the subscriber identity module (SIM) card (more accurately an SD card) located inside the camera.
Deputies observed multiple files on the SIM card and opened one. At the 16:39.48 timestamp mark deputies observed a white male subject wearing a collared white, red, blue and green striped shirt with white/khaki shorts affixing the camera to the inside of the toilet...
Deputies confirmed he was wearing the same clothing found on the file located on the SIM card where he placed the camera in the toilet. more (You can't make this sh-t up. Perp gets the Darwin Award from us for filming himself.)
Wednesday, April 15, 2020
China May Be Tapped Out
The Trump administration is continuing with actions that cut telecom ties with China, including a new filing from the National Telecommunications and Information Administration that recommends that the Federal Communications Commission revoke China Telecom’s ability to carry international voice traffic between the U.S. and other countries...
China Telecom was authorized in 2007 to operate in the U.S. and it provides a suite of services that include voice, data television and business network services. It also operates a mobile virtual network operator, CTExcel, that targets Chinese Americans and Chinese tourists and students, according to the filing—but times and risks have changed, NTIA has concluded.
It also said that 80% of the DoJ’s economic espionage cases where a foreign entity or government would benefit, have involved China. more
It also said that 80% of the DoJ’s economic espionage cases where a foreign entity or government would benefit, have involved China. more
Attorney Approved - A Strange Reality Hollywood Spy Camera Story
Aaron Kaplan,
the prolific TV producer, has been accused in a lawsuit of installing
cameras in his sister-in-law’s bedroom — with one focused on her closet —
in order to spy on her...
Aaron Kaplan, producer of “The Chi,” “Santa Clarita Diet” and other shows, has been embroiled in a probate fight with his sister-in-law since the death of his brother, Joe, in July 2018.
In a probate filing in February, Aaron Kaplan acknowledged that he arranged for the cameras to be placed in the closet because he worried that Elizabeth Kaplan would break into a safe that held valuables belonging to her late husband’s trust...
According to Elizabeth Kaplan’s lawsuit, two weeks after she returned to the couple’s home in Malibu, she and her mother discovered two cameras in her husband’s closet in the master bedroom. The suit alleges that the second camera was positioned such that it pointed at Elizabeth Kaplan’s closet...
In his probate filing, Aaron Kaplan said he became suspicious soon after his brother’s death, when he heard that Elizabeth’s friends had been seen entering the Malibu house and that artwork had been removed from the walls.
“Based on consultations with his attorney, the Trustee understood that he could — and should — have motion-activated cameras installed in Joe’s personal closet to monitor and protect those assets for the beneficiaries of Joe’s Trust,” Aaron Kaplan’s attorneys wrote.
According to the filing, the cameras captured Elizabeth Kaplan and her mother rifling through Joe Kaplan’s belongings in search of cash. They also allegedly hired a locksmith to try to break into the safe, in spite of instructions from Aaron’s attorney that the contents belonged to the separate trust.
The video also captured Elizabeth discovering $10,000 in cash, counting it out, and pocketing it, according to the filing.
The recordings stopped once Elizabeth and her mother discovered and disabled the cameras. more
Aaron Kaplan, producer of “The Chi,” “Santa Clarita Diet” and other shows, has been embroiled in a probate fight with his sister-in-law since the death of his brother, Joe, in July 2018.
In a probate filing in February, Aaron Kaplan acknowledged that he arranged for the cameras to be placed in the closet because he worried that Elizabeth Kaplan would break into a safe that held valuables belonging to her late husband’s trust...
According to Elizabeth Kaplan’s lawsuit, two weeks after she returned to the couple’s home in Malibu, she and her mother discovered two cameras in her husband’s closet in the master bedroom. The suit alleges that the second camera was positioned such that it pointed at Elizabeth Kaplan’s closet...
In his probate filing, Aaron Kaplan said he became suspicious soon after his brother’s death, when he heard that Elizabeth’s friends had been seen entering the Malibu house and that artwork had been removed from the walls.
“Based on consultations with his attorney, the Trustee understood that he could — and should — have motion-activated cameras installed in Joe’s personal closet to monitor and protect those assets for the beneficiaries of Joe’s Trust,” Aaron Kaplan’s attorneys wrote.
According to the filing, the cameras captured Elizabeth Kaplan and her mother rifling through Joe Kaplan’s belongings in search of cash. They also allegedly hired a locksmith to try to break into the safe, in spite of instructions from Aaron’s attorney that the contents belonged to the separate trust.
The video also captured Elizabeth discovering $10,000 in cash, counting it out, and pocketing it, according to the filing.
The recordings stopped once Elizabeth and her mother discovered and disabled the cameras. more
Daughter Saves Mom from Video Voyeurism
UT - A Kamas man has been charged with multiple offenses after he allegedly hid cameras in the heat vents of a woman’s Summit County residence.
Matthew Ryan Ingoldsby, 48, was arrested on March 31 and is facing charges of:
Matthew Ryan Ingoldsby, 48, was arrested on March 31 and is facing charges of:
- Burglary of a dwelling, a second-degree felony
- Voyeurism by electronic equipment concealed or disguised, a class A misdemeanor
- Stalking, a third-degree felony
- Tampering with a witness, a third-degree felony
Corporate Privacy & Information Security Challenges from Covid-19
This is an excellent information security article written by a respected colleague. ~Kevin
via Charles Patterson - Exec Security
The CoVid-19 response has had serious and often devastating effects on individuals and businesses throughout the world... But there are a number of side-effects from this, many of which affect privacy and information security...
Company offices may be left mostly empty with a skeleton crew, and access being granted to maintenance staff or a few lone employees who may still be carrying out basic operations or some who may have just needed to return to pick up something from their desk to help them work better from home. This means the employees, cleaners, and other staff will be largely unsupervised and may have easy access to areas not normally permitted...
When reviewing your security during this period, here are some very important points to consider:
via Charles Patterson - Exec Security
The CoVid-19 response has had serious and often devastating effects on individuals and businesses throughout the world... But there are a number of side-effects from this, many of which affect privacy and information security...
Company offices may be left mostly empty with a skeleton crew, and access being granted to maintenance staff or a few lone employees who may still be carrying out basic operations or some who may have just needed to return to pick up something from their desk to help them work better from home. This means the employees, cleaners, and other staff will be largely unsupervised and may have easy access to areas not normally permitted...
When reviewing your security during this period, here are some very important points to consider:
- How secure was your facility during the down time?
- Note what areas were weakened, where was less manpower deployed?
- Who continued to have access?
- What types of staff were still given access? Were employees still allowed back in?
- Were any private or classified areas left open and unattended?
- Pay particular attention to board rooms, conference areas, and C-suites. Look for any signs of unauthorized activity.
- What incidents may have occurred during the period?
- Review logs of any security incidents, look for any correlations that could indicate suspicious activity.
- Were there any areas accessed by unauthorized personnel?
- Investigate thoroughly any reports of employees found in unauthorized areas.
- Did any break-ins or vandalism occur?
- Security breaches or other incidents could be used as a cover for actual espionage activity. If a break-in or theft was reported, pay attention to any nearby areas that may have been accessed as well.
Google Searches for "Wiretap" Up 100% in the Past Week
A lot of people have too much time on their hands.
Or, interest in knowing someone else's business is mirroring the uptick in phone calls.
Or, interest in protecting one's business is mirroring the uptick in phone calls.
Or, all of the above.
We'll put this in the You Decide file.
Or, interest in knowing someone else's business is mirroring the uptick in phone calls.
Or, interest in protecting one's business is mirroring the uptick in phone calls.
Or, all of the above.
We'll put this in the You Decide file.
Tuesday, April 14, 2020
500,000 Hacked Zoom Accounts Given Away - Free On The Dark Web
New users have flocked to the Zoom video conferencing platform as businesses, schools, and other organizations look for ways to meet safely during the Coronavirus pandemic. Unfortunately many of those brand new accounts appear to have been secured with old passwords.
The cyber risk assessment experts at Cyble recently discovered a hacker selling stolen Zoom credentials at dirt-cheap prices — and in some cases giving them away for free.
Cyble purchased more than 530,000 on an underground hacking forum for next to nothing. Several of the company’s clients were among the stolen credentials, which also included personal meeting URLs and Zoom host keys. Cyble reached out and confirmed that the credentials were indeed valid.
Password re-use remains a huge security issue for the general public. Fatigued users feel like they can’t remember yet another password so they set up new accounts using an old stand-by.
The problem is that by now all of those old stand-by passwords have been filed away in databases by criminal hackers. They’re actively using them to break into accounts using brute force attacks.
Usernames, email addresses, and passwords have been exposed by the billions over the past several years. Creating a new account on Zoom — or any service, for that matter — is simply not a good idea.
Hackers will come knocking. It’s not a question of if. It’s a question of when. more
Spybuster Tip # 053 - Upgrade all your passwords.
Spybuster Tip # 054 - Don't worry about having to remember all your passwords. Use a password vault.
The cyber risk assessment experts at Cyble recently discovered a hacker selling stolen Zoom credentials at dirt-cheap prices — and in some cases giving them away for free.
Cyble purchased more than 530,000 on an underground hacking forum for next to nothing. Several of the company’s clients were among the stolen credentials, which also included personal meeting URLs and Zoom host keys. Cyble reached out and confirmed that the credentials were indeed valid.
Password re-use remains a huge security issue for the general public. Fatigued users feel like they can’t remember yet another password so they set up new accounts using an old stand-by.
The problem is that by now all of those old stand-by passwords have been filed away in databases by criminal hackers. They’re actively using them to break into accounts using brute force attacks.
Usernames, email addresses, and passwords have been exposed by the billions over the past several years. Creating a new account on Zoom — or any service, for that matter — is simply not a good idea.
Hackers will come knocking. It’s not a question of if. It’s a question of when. more
Spybuster Tip # 053 - Upgrade all your passwords.
Spybuster Tip # 054 - Don't worry about having to remember all your passwords. Use a password vault.
Monday, April 13, 2020
FREE - The Murray Associates "Spycam Detection Training Course"
I've created a special Covid coupon so anyone can take our Spycam Detection in Workplace Expectation of Privacy Areas, absolutely FREE. (Normally $24.99)
The coupon code is our main website address: COUNTERESPIONAGE.COM
This is a one-hour, self-paced video course, with Certificate-of-Completion. More details about the course at spycamdetection.training or Udemy.
Or, jump straight to the start with this coupon encoded link:
https://www.udemy.com/course/spycam-detection/?couponCode=COUNTERESPIONAGE.COM
Feel free to pass along this limited time offer on to anyone you know: co-workers, friends, and family—anyone who does not want to be a victim of video voyeurs.
(Expires 04/16/2020 06:04 AM PDT (GMT -7))
The coupon code is our main website address: COUNTERESPIONAGE.COM
This is a one-hour, self-paced video course, with Certificate-of-Completion. More details about the course at spycamdetection.training or Udemy.
Or, jump straight to the start with this coupon encoded link:
https://www.udemy.com/course/spycam-detection/?couponCode=COUNTERESPIONAGE.COM
Feel free to pass along this limited time offer on to anyone you know: co-workers, friends, and family—anyone who does not want to be a victim of video voyeurs.
(Expires 04/16/2020 06:04 AM PDT (GMT -7))
How Not to be Seen - Evading CCTV Surveillance
It's theoretically possible to become invisible to cameras. But can it catch on?

Right now, you're more than likely spending the vast majority of your time at home. Someday, however, we will all be able to leave the house once again and emerge, blinking, into society to work, travel, eat, play, and congregate in all of humanity's many bustling crowds.
The world, when we eventually enter it again, is waiting for us with millions of digital eyes—cameras, everywhere, owned by governments and private entities alike. Pretty much every state out there has some entity collecting license plate data from millions of cars—parked or on the road—every day. Meanwhile all kinds of cameras—from police to airlines, retailers, and your neighbors' doorbells—are watching you every time you step outside, and unscrupulous parties are offering facial recognition services with any footage they get their hands on.
In short, it's not great out there if you're a person who cares about privacy, and it's likely to keep getting worse. In the long run, pressure on state and federal regulators to enact and enforce laws that can limit the collection and use of such data is likely to be the most efficient way to effect change. But in the shorter term, individuals have a conundrum before them: can you go out and exist in the world without being seen?
Bottom line as of now...
All of the digital simulations run on the cloak worked with 100-percent effectiveness, he added. But in the real world, "the reliability degrades." The tech has room for improvement.
"How good can they get? Right now I think we're still at the prototype stage," he told Ars. "You can produce these things that, when you wear them in some situations, they work. It's just not reliable enough that I would tell people, you know, you can put this on and reliably evade surveillance." more

Right now, you're more than likely spending the vast majority of your time at home. Someday, however, we will all be able to leave the house once again and emerge, blinking, into society to work, travel, eat, play, and congregate in all of humanity's many bustling crowds.
The world, when we eventually enter it again, is waiting for us with millions of digital eyes—cameras, everywhere, owned by governments and private entities alike. Pretty much every state out there has some entity collecting license plate data from millions of cars—parked or on the road—every day. Meanwhile all kinds of cameras—from police to airlines, retailers, and your neighbors' doorbells—are watching you every time you step outside, and unscrupulous parties are offering facial recognition services with any footage they get their hands on.
In short, it's not great out there if you're a person who cares about privacy, and it's likely to keep getting worse. In the long run, pressure on state and federal regulators to enact and enforce laws that can limit the collection and use of such data is likely to be the most efficient way to effect change. But in the shorter term, individuals have a conundrum before them: can you go out and exist in the world without being seen?
Bottom line as of now...
All of the digital simulations run on the cloak worked with 100-percent effectiveness, he added. But in the real world, "the reliability degrades." The tech has room for improvement.
"How good can they get? Right now I think we're still at the prototype stage," he told Ars. "You can produce these things that, when you wear them in some situations, they work. It's just not reliable enough that I would tell people, you know, you can put this on and reliably evade surveillance." more
Thursday, April 9, 2020
Allen Garfield, Character Actor in ‘The Conversation,’ Dies at 80
Allen Garfield, a stocky character actor who lent an intense naturalism to celebrated 1970s films such as “The Conversation” and “Nashville,” died April 7 in Los Angeles. He was 80.
His sister, Lois Goorwitz, said the cause was complications from covid-19. Mr. Garfield had been a resident at the Motion Picture Television Fund Home, the industry retirement facility in Los Angeles where several staffers and some residents have tested positive for the coronavirus.
Mr. Garfield grew up in New Jersey and first set out as a boxer and a sportswriter. While covering sports for the Newark Star-Ledger, he studied acting at night and was eventually accepted by the Actors Studio workshop and studied under Lee Strasberg. more
State-Backed Hackers Using Virus to Increase Spying
State-backed hackers are seizing on the coronavirus pandemic to lead cyber espionage.
In a rare joint assessment released on Wednesday, Britain’s National Cyber Security Centre — a branch of signals intelligence agency GCHQ — and the US’ Cybersecurity and Infrastructure Security Agency — part of the Department of Homeland Security — highlighted the “growing use” of Covid-19 in state-sponsored cyber attacks.
The frequency and severity of these initiatives is likely to “increase over the coming weeks and months”, the NCSC said. more
By monitoring network activity one can document and quantify this type of spying activity. Other spying methods—bugging, and physical intrusions—are covert, thus undetected. Makes sense these would be on the rise as well. Maybe more so. Something to think about while your offices are empty and vulnerable. ~Kevin
In a rare joint assessment released on Wednesday, Britain’s National Cyber Security Centre — a branch of signals intelligence agency GCHQ — and the US’ Cybersecurity and Infrastructure Security Agency — part of the Department of Homeland Security — highlighted the “growing use” of Covid-19 in state-sponsored cyber attacks.
The frequency and severity of these initiatives is likely to “increase over the coming weeks and months”, the NCSC said. more
By monitoring network activity one can document and quantify this type of spying activity. Other spying methods—bugging, and physical intrusions—are covert, thus undetected. Makes sense these would be on the rise as well. Maybe more so. Something to think about while your offices are empty and vulnerable. ~Kevin
Attorney Warns Business Against Relaxing Security Standards
 via Seyfarth Shaw LLP -
Jeremy A. Cohen
via Seyfarth Shaw LLP -
Jeremy A. Cohen And, of course, there are bad actors taking advantage of the current situation.
Relaxed security make systems and information far more susceptible to hacking and other data breaches, which often carry mandatory reporting obligations and hefty penalties, and invariably lead to class action lawsuits, not to mention privacy concerns.
Accordingly, companies should think twice before loosening these security standards. By all accounts, the current COVID-19 crisis will be relatively short-lived (whether that means weeks or months is, of course, unknown), but as the saying goes, once a secret is known, it cannot be unknown.
And when this is all said and done, while courts will likely give some leeway as a result of the emergency situation, if basic safeguards were disregarded, courts may have a hard time concluding that a company undertook reasonable efforts to safeguard its information, as is required in all jurisdictions to merit trade secret protection. more
Wednesday, April 8, 2020
Interesting Article in Food Safety Magazine
In addition to nation-state industrial espionage, companies face a wide range of threats.
“Hacktivists” launch attacks for ideological, political, or religious reasons, or simply for the challenge.
Criminal organizations attack for profit, trying to extract payment from the victim.
In addition, companies sometimes become victims even if they are not the intended target, such as the notpetya attack, which targeted a software company but had much broader impact, including the food and agriculture industry.
It is important to know that nation states and criminal organizations both do target corporations, and this article will provide solutions on how companies can better protect themselves. more
“Hacktivists” launch attacks for ideological, political, or religious reasons, or simply for the challenge.
Criminal organizations attack for profit, trying to extract payment from the victim.
In addition, companies sometimes become victims even if they are not the intended target, such as the notpetya attack, which targeted a software company but had much broader impact, including the food and agriculture industry.
It is important to know that nation states and criminal organizations both do target corporations, and this article will provide solutions on how companies can better protect themselves. more
Spy Satellites Shelter in Place, or “Don’t Stop Me Now" Stopped
The rapid spread of COVID-19 around the globe has delayed the launch of three US intelligence payloads from New Zealand until at least April 23, launch provider Rocket Lab confirmed April 6.
Rocket Lab announced that they were pausing the scheduled March 30 launch of three National Reconnaissance Office payloads following the New Zealand government’s March 23 announcement that the country would enter Alert Level 4. This forced most businesses to close and the government ordered people to stay at home...
Dubbed “Don’t Stop Me Now," the March 30 launch would have been the second NRO mission launch from Rocket Lab’s New Zealand facility. more
Rocket Lab announced that they were pausing the scheduled March 30 launch of three National Reconnaissance Office payloads following the New Zealand government’s March 23 announcement that the country would enter Alert Level 4. This forced most businesses to close and the government ordered people to stay at home...
Dubbed “Don’t Stop Me Now," the March 30 launch would have been the second NRO mission launch from Rocket Lab’s New Zealand facility. more
The Spy - Pre-Release Trailer
The trailer for an upcoming WWII-set action-drama titled The Spy has been released online through Signature Entertainment. The film will be released on digital in June. more
Subscribe to:
Comments (Atom)