• I'm not feeling very social right now!
• A warning to spies that you are protected against electronic surveillance.
You too can find hidden spy cameras. more
U.S. Secretary of State, Mike Pompeo, claimed that TikTok sends user data to China, exerting pressure on the video-sharing social networking service. Pompeo brought attention to the fact that if personal information flows across a Chinese server, it will eventually end up in the hands of the Chinese Communist Party which he calls an “Evil Empire”.
TikTok has denied U.S. allegations but a report by cyber experts at ProtonMail says otherwise. The report is more a warning as it states – “Beware, the social media giant not only collects troves of personal data on you, but also cooperates with the CCP, extending China’s surveillance and censorship reach beyond its borders.” more
In other news...
Microsoft said Sunday it will continue talks to buy short-form video app, TikTok after its chief executive spoke with President Trump, following a weekend of uncertainty clouding the future of the Chinese-owned app. more
Connect the Dots...
When Microsoft bought Skype, Wired Magazine noted, "The Skype client itself is written almost as if it were a piece of malware, using complex obfuscation and anti-reverse engineering techniques, and it would be disquieting for Microsoft to release something that behaved in such a shady way; at the very least, the client would surely have to be rewritten to avoid the obfuscation and outright hostility to
managed networks that Skype currently has... Ultimately, it's hard to see how the Skype purchase is worthwhile from a
technology or user-access perspective. The technology isn't good enough
and the users aren't lucrative enough or plentiful enough to justify
it. more
Pure Conjecture Disguised as Analysis...
TikTok, it appears, is also giving government fits. Who ya gonna call?
Britain on Wednesday named its former ambassador to Turkey as the new director of the MI6 Secret Intelligence Service.
Richard Moore succeeds Alex Younger, who was a career intelligence officer and became Britain's top spy in 2014. moore
The entire system weighs around a tenth of a playing card, uses minimal
power, and keeps the frame pointed at where the bug looks by mimicking
its steering mechanisms. more

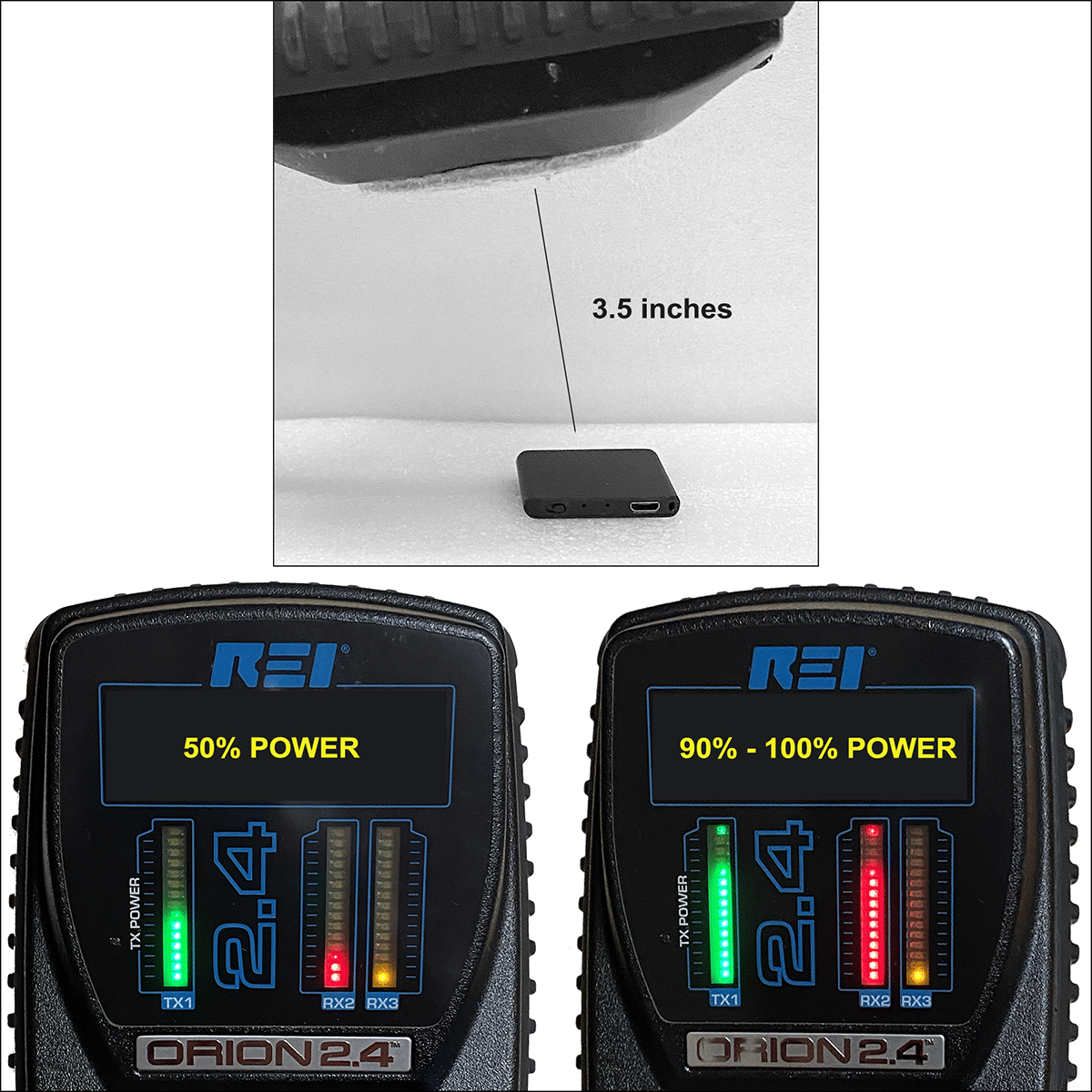 Testing Our Defenses
Testing Our Defenses Three stories.
Three stories.
 Mozilla says it will fix the bug later this year, in October.
Mozilla says it will fix the bug later this year, in October. |
| Click to enlarge. Go to website to explore. Wired article here. |
 To spot transgressions, researchers at the University of Darmstadt, North Carolina State University, and the University of Paris Saclay developed LeakyPick, a platform that periodically probes microphone-equipped devices and monitors subsequent network traffic for patterns indicating audio transmission.
To spot transgressions, researchers at the University of Darmstadt, North Carolina State University, and the University of Paris Saclay developed LeakyPick, a platform that periodically probes microphone-equipped devices and monitors subsequent network traffic for patterns indicating audio transmission.  New Zealand’s plans to host the 2021 America’s Cup are in disarray amid allegations of fraud, spying and a government decision to suspend funding for the world’s most famous yachting event.
New Zealand’s plans to host the 2021 America’s Cup are in disarray amid allegations of fraud, spying and a government decision to suspend funding for the world’s most famous yachting event. “It is a deliberate, sinister, and highly orchestrated attack which includes anonymous tip-offs, recordings and document leaks. ‘Informants’ orchestrate unfair accusations, bypassing normal processes, and going straight to external authorities,” he said.
“It is a deliberate, sinister, and highly orchestrated attack which includes anonymous tip-offs, recordings and document leaks. ‘Informants’ orchestrate unfair accusations, bypassing normal processes, and going straight to external authorities,” he said.
 This has been a week that TikTok—the Chinese viral video giant that has soared under lockdown—will want to put quickly behind it...
This has been a week that TikTok—the Chinese viral video giant that has soared under lockdown—will want to put quickly behind it...  “There is a level of apathy and a lack of awareness when it comes to securing the home office environment....they’re seeing double the failure rates on their security tests than they saw pre-COVID,” warns Mathew Newfield, Chief Information Security Officer at Unisys...
“There is a level of apathy and a lack of awareness when it comes to securing the home office environment....they’re seeing double the failure rates on their security tests than they saw pre-COVID,” warns Mathew Newfield, Chief Information Security Officer at Unisys... 1977 - S. Korea - The foreign ministry delivers a letter of protest to Washington
over the wiretapping of the office of President Park Chung-hee by the
U.S. Central Intelligence Agency. The agency was investigating an
allegation that a South Korean lobbyist paid bribes of up to US$1
million to high-level U.S. politicians at the behest of the South Korean
president, who did not get along with his U.S. counterpart, Jimmy
Carter. more
1977 - S. Korea - The foreign ministry delivers a letter of protest to Washington
over the wiretapping of the office of President Park Chung-hee by the
U.S. Central Intelligence Agency. The agency was investigating an
allegation that a South Korean lobbyist paid bribes of up to US$1
million to high-level U.S. politicians at the behest of the South Korean
president, who did not get along with his U.S. counterpart, Jimmy
Carter. more
 |
| Click to enlarge. |
 A team of scientists hunting dark matter has recorded suspicious pings
coming from a vat of liquid xenon underneath a mountain in Italy.
A team of scientists hunting dark matter has recorded suspicious pings
coming from a vat of liquid xenon underneath a mountain in Italy. 
 A new camera app has been released for iOS that, unlike basically every other photography app, is designed to hide the photo’s subject rather than highlight them. Called Anonymous Camera, this app works to protect the people captured in a video or photo by blurring or otherwise hiding their faces — or, in cases where it is necessary, by removing their bodies entirely.
A new camera app has been released for iOS that, unlike basically every other photography app, is designed to hide the photo’s subject rather than highlight them. Called Anonymous Camera, this app works to protect the people captured in a video or photo by blurring or otherwise hiding their faces — or, in cases where it is necessary, by removing their bodies entirely.