Just for fun, here are four of the...
13 Hidden Spy Cams That Might Be Watching You Right Now
Tuesday, September 18, 2012
Friday, September 14, 2012
Security Director Alert - BYOD is way different than BYOB - Time to learn.
BYOD is an acronym the IT folks are using. It means Bring Your Own Device; the security process for allowing employees to use their personal electronics at work without jeopardizing company information or compromising the networks.
While IT continues to munch your lunch, take a moment to oversee their efforts. You have valuable insights to contribute. The last thing you want is to be left out of your own game. In fact, the security department should be the leader here, with IT carrying out your marching orders.
FREE Quick Study...
"Bring Your Own Device is here to stay. Don't be a lamb led to the slaughter, instead lead your users to the promised land of mobile device management.
1. Thou Shalt Allow BYOD
The rapid proliferation of mobile devices entering the workplace feels like divine intervention to many IT leaders. It's as if a voice boomed down from the mountain ordering all of the employees you support to procure as many devices as possible and connect them to corporate services en masse. Bring Your Own Device (BYOD) was born and employees followed with fervor."
You can download the full version here... The Ten Commandments of BYOD It is an easy read, and provides a logical roadmap for instituting BYOD.
Of course, nothing is really FREE. You will be asked for your name, email, etc. I did it and found the trade-off worthwhile. Within minutes I received a polite email... "My name is John Kerestus Account Executive here with Fiberlink MaaS360..." with an offer to see a demo. Impressive response.
Other companies who offer BYOD solutions also provide "free" education. Do comics get the point across better than white papers and webinars? You decide...
• White Paper 1
• Webinar
• White Paper 2
• White Paper 3
• White Paper 4
Have a wonderful weekend, find a cozy restaurant, and BYOB. ~Kevin
Security Directors: FREE Security White Paper - "Surreptitious Workplace Recording ...and what you can do about it."
While IT continues to munch your lunch, take a moment to oversee their efforts. You have valuable insights to contribute. The last thing you want is to be left out of your own game. In fact, the security department should be the leader here, with IT carrying out your marching orders.
FREE Quick Study...
"Bring Your Own Device is here to stay. Don't be a lamb led to the slaughter, instead lead your users to the promised land of mobile device management.
1. Thou Shalt Allow BYOD
The rapid proliferation of mobile devices entering the workplace feels like divine intervention to many IT leaders. It's as if a voice boomed down from the mountain ordering all of the employees you support to procure as many devices as possible and connect them to corporate services en masse. Bring Your Own Device (BYOD) was born and employees followed with fervor."
You can download the full version here... The Ten Commandments of BYOD It is an easy read, and provides a logical roadmap for instituting BYOD.
Of course, nothing is really FREE. You will be asked for your name, email, etc. I did it and found the trade-off worthwhile. Within minutes I received a polite email... "My name is John Kerestus Account Executive here with Fiberlink MaaS360..." with an offer to see a demo. Impressive response.
Other companies who offer BYOD solutions also provide "free" education. Do comics get the point across better than white papers and webinars? You decide...
• White Paper 1
• Webinar
• White Paper 2
• White Paper 3
• White Paper 4
Have a wonderful weekend, find a cozy restaurant, and BYOB. ~Kevin
Security Directors: FREE Security White Paper - "Surreptitious Workplace Recording ...and what you can do about it."
Labels:
book,
business,
cell phone,
computer,
employee,
FutureWatch,
IT
Thursday, September 13, 2012
Emergency Phone - 15 Year Standby Battery Life
The $70 SpareOne emergency phone from Xpal Power, which uses a standard AA lithium battery, claims a standby time of up to 15 years. (10 hours talk time.)
The phone has only the barest of features. No text, no Web, just phone calls and a dedicated 911 button. Indicators, like if you have a network connection, are provided by blinking colored lights. It saves a lot of power, but you’ll have to memorize what the color combinations mean.
The phone doesn’t even come with a SIM card, which you will need before you can use it, although you can make a 911 call using the emergency button even without the SIM card.
The phone is built for a GSM network, which means that in the United States it will work with T-Mobile, AT&T or companies that resell those networks. (more)
Bonus: It can not be infected with spyware. Too dumb. ~Kevin
 |
| Click to enlarge. |
The phone doesn’t even come with a SIM card, which you will need before you can use it, although you can make a 911 call using the emergency button even without the SIM card.
The phone is built for a GSM network, which means that in the United States it will work with T-Mobile, AT&T or companies that resell those networks. (more)
Bonus: It can not be infected with spyware. Too dumb. ~Kevin
Industrial Espionage? You decide...
Just coincidence? There are many car designers in the world, but how many could independently come up designs this similar for 2012-2013?
"Ford puts a great deal of emphasis on styling with the new Mondeo, saying that its sports coupe profile provides “visual lightness.” The lines are more angular than previous versions with a sharper crease along the side breaking the lines and providing a bit of visual flair. Up front, there’s a trapezoidal grille like something stolen off an Aston Martin..." (more)
Could they be right?
You decide.
While you're deciding, think about this. What are you doing to protect your bright ideas, business strategies and private conversations? Help is available. Give Murray Associates a call.
 |
| Click to enlarge. |
 |
| Click to enlarge. |
You decide.
While you're deciding, think about this. What are you doing to protect your bright ideas, business strategies and private conversations? Help is available. Give Murray Associates a call.
False Security is Worse than a Healthy Sense of Caution
McAfee Social protection is a soon to be released app and browser plug-in for Facebook that gives users the ability to securely share their photos.
As it stands today, if you upload a photo to Facebook, anyone viewing that photo can simply download it or take a screen capture and alter or share it to their wherever they want, however they want. With McAfee Social Protection installed though, users viewing your images will not be able to copy or capture them. (more, with video)
Just aiming a high-res cell phone camera at the screen defeats this app, of course. But here is the bigger issue here... security solutions that only partially work actually increase risk. In this case, people who believe in this app's effectiveness may now feel safe to post even riskier photos.
False sense of security examples abound in my field; eavesdropping detection gadgets, under-trained TSCM providers, window film to block electronic eavesdropping are but three.
Moral: No matter what security solution your employ – from "fully" effective to completely bogus – keep your healthy sense of caution. ~Kevin
 |
| Product of a standard screen capture. |
Just aiming a high-res cell phone camera at the screen defeats this app, of course. But here is the bigger issue here... security solutions that only partially work actually increase risk. In this case, people who believe in this app's effectiveness may now feel safe to post even riskier photos.
False sense of security examples abound in my field; eavesdropping detection gadgets, under-trained TSCM providers, window film to block electronic eavesdropping are but three.
Moral: No matter what security solution your employ – from "fully" effective to completely bogus – keep your healthy sense of caution. ~Kevin
Labels:
advice,
App,
cautionary tale,
Hack,
privacy,
X-Ray Vision
Pool of Likely Phone-Hacking Victims Skyrockets
UK - The number of likely victims of phone hacking by people working for Rupert Murdoch's London media empire has jumped to more than 1,000, the top police officer working on the case said Tuesday.
Police have identified another 3,706 potential victims of illegal eavesdropping by journalists in search of stories, Metropolitan Police Deputy Assistant Commissioner Sue Akers told lawmakers.
Authorities had earlier put the number of "likely" victims at around 600, but now say it is 1,069. (more)
Police have identified another 3,706 potential victims of illegal eavesdropping by journalists in search of stories, Metropolitan Police Deputy Assistant Commissioner Sue Akers told lawmakers.
Authorities had earlier put the number of "likely" victims at around 600, but now say it is 1,069. (more)
Sunday, September 9, 2012
Create Your Own Headline For This One...
Chinese telecoms equipment maker Huawei Technologies Ltd. has issued a report on cybersecurity that includes a pledge never to cooperate with spying in a fresh effort to allay concerns in the United States and elsewhere that threaten to hamper its expansion.
The report, written by a Huawei executive who is a former British official, calls for global efforts to create legal and technical security standards. It makes no recommendations for what standards to adopt but says current laws are inconsistent or fail to address important threats.
Huawei, founded by a former Chinese military engineer in 1987, has grown to become the world's second-largest supplier of telecoms network gear after Sweden's LM Ericsson.
Suspicions that Huawei might be controlled by China's Communist Party or military have slowed its expansion in the United States and it was barred from bidding to take part in an Australian broadband project.
The company denies it is a security threat. (more)
The report, written by a Huawei executive who is a former British official, calls for global efforts to create legal and technical security standards. It makes no recommendations for what standards to adopt but says current laws are inconsistent or fail to address important threats.
Huawei, founded by a former Chinese military engineer in 1987, has grown to become the world's second-largest supplier of telecoms network gear after Sweden's LM Ericsson.
Suspicions that Huawei might be controlled by China's Communist Party or military have slowed its expansion in the United States and it was barred from bidding to take part in an Australian broadband project.
The company denies it is a security threat. (more)
Saturday, September 8, 2012
Vector Technologies, LLC patent number 8203850 for an Anti-Eavesdropping Device
The United States Patent and Trademark Office has awarded Vector Technologies, LLC patent number 8203850 for an Anti-Eavesdropping Device, i.e. Portable Electronic Device (PED) Countermeasures Box.
Vector Technologies' product has already been purchased by various government agencies, including key defense agencies, defense contractors and the White House as a solution to the growing number of PEDs in the workplace and the grave technical espionage threat that PEDs pose to classified and sensitive information. (more)
Vector Technologies' product has already been purchased by various government agencies, including key defense agencies, defense contractors and the White House as a solution to the growing number of PEDs in the workplace and the grave technical espionage threat that PEDs pose to classified and sensitive information. (more)
Intercepting Unencrypted WiFi Not Wiretapping
A federal judge in Illinois has ruled that intercepting traffic on unencrypted WiFi networks is not wiretapping. The decision runs counter to a 2011 decision that suggested Google may have violated the law when its Street View cars intercepted fragments of traffic from open WiFi networks around the country.
The ruling is a preliminary step in a larger patent trolling case. A company called Innovatio IP Ventures has accused various "hotels, coffee shops, restaurants, supermarkets," and other businesses that offer WiFi service to the public of infringing 17 of its patents. Innovatio wanted to use packet sniffing gear to gather WiFi traffic for use as evidence in the case. It planned to immediately delete the contents of the packets, only keeping the headers. Still, the firm was concerned that doing so might violate federal privacy laws, so it sought a preliminary ruling on the question.
Federal law makes it illegal to intercept electronic communications, but it includes an important exception. It's not illegal to intercept communications "made through an electronic communication system that is configured so that such electronic communication is readily accessible to the general public." (more)
The ruling is a preliminary step in a larger patent trolling case. A company called Innovatio IP Ventures has accused various "hotels, coffee shops, restaurants, supermarkets," and other businesses that offer WiFi service to the public of infringing 17 of its patents. Innovatio wanted to use packet sniffing gear to gather WiFi traffic for use as evidence in the case. It planned to immediately delete the contents of the packets, only keeping the headers. Still, the firm was concerned that doing so might violate federal privacy laws, so it sought a preliminary ruling on the question.
Federal law makes it illegal to intercept electronic communications, but it includes an important exception. It's not illegal to intercept communications "made through an electronic communication system that is configured so that such electronic communication is readily accessible to the general public." (more)
Thursday, September 6, 2012
Spy Project Corporate Espionage Case Settles Out Of Court
CO - Paragon Dynamics Inc., an Aurora defense contractor, is paying $1.15 million to settle allegations it stole bid information from Raytheon Corp. about spy agency projects over which the companies competed in 2009...
Around July 31, 2009, an unidentified senior software director for Paragon used computer access to Raytheon’s systems in Aurora to obtain Raytheon’s bids for two NRO projects — code named Antietam and Savannah — plus other information, the settlement agreement says.
Security cameras caught the employee faxing some of the information to the president of Paragon Dynamics, who forwarded it to someone at a company Paragon partnered with to compete against Raytheon for the NRO’s Antietam contract, the government said. (more)
Security cameras caught the employee faxing some of the information to the president of Paragon Dynamics, who forwarded it to someone at a company Paragon partnered with to compete against Raytheon for the NRO’s Antietam contract, the government said. (more)
International Hotel Rooms: The Enemy's Gateway To Economic And Industrial Espionage
by Luke Bencie
"For most international business travelers, overseas hotel accommodations can conjure up an array of images. Depending on the region of the world they travel, frequent fliers know that lodging is never consistent.
For example, Southeast Asian hotels deliver a personal attention to detail that can only be found in the Orient, while hotels in the Middle Eastern Gulf states compete against one another through stunning opulence to attract powerful sheiks and wealthy oil barons. Closer to home, Latin America and Caribbean provide relaxing, tropical beach resort, while Europe still offers old world charm in quaint surroundings..." Read the whole article here.
Mr. Bencie also conducts instructional seminars for executives who travel overseas. (more)
If the above article applies to you, you should also read:
• Top Five Ways Business Executives are Spied Upon Overseas and How They Can Protect Themselves (Luke Bencie)
• The Top Twenty Information Security Tips for Business Travelers to Closed Society Countries (Kevin D. Murray)
• Staying Safe Abroad: Traveling, Working & Living in a Post-9/11 World (Edward Lee)
"For most international business travelers, overseas hotel accommodations can conjure up an array of images. Depending on the region of the world they travel, frequent fliers know that lodging is never consistent.
For example, Southeast Asian hotels deliver a personal attention to detail that can only be found in the Orient, while hotels in the Middle Eastern Gulf states compete against one another through stunning opulence to attract powerful sheiks and wealthy oil barons. Closer to home, Latin America and Caribbean provide relaxing, tropical beach resort, while Europe still offers old world charm in quaint surroundings..." Read the whole article here.
Mr. Bencie also conducts instructional seminars for executives who travel overseas. (more)
If the above article applies to you, you should also read:
• Top Five Ways Business Executives are Spied Upon Overseas and How They Can Protect Themselves (Luke Bencie)
• The Top Twenty Information Security Tips for Business Travelers to Closed Society Countries (Kevin D. Murray)
• Staying Safe Abroad: Traveling, Working & Living in a Post-9/11 World (Edward Lee)
Sunday, September 2, 2012
Spy Tie Helps Make the Collar
via GeekAlerts.com...
Are you a spy and in need of a new camera that others won’t notice? This Spy Camera Tie with Wireless Remote will help and make you a well dressed James Bond.
It looks just like a regular tie, but it records audio & video. It comes with a remote control and a built-in 4GB DVR. The built in USB port makes it easy to transfer data. This spy gadget will record up to 3 hours per single charge so you can get plenty of footage.
($70 at Amazon.com)
Why do I mention it?
So you will know what you are up against.
~Kevin
Are you a spy and in need of a new camera that others won’t notice? This Spy Camera Tie with Wireless Remote will help and make you a well dressed James Bond.
 |
| Click to enlarge. |
($70 at Amazon.com)
Why do I mention it?
So you will know what you are up against.
~Kevin
Saints Vindicated
LA - Louisiana State Police investigators have found no evidence that the Saints or general manager Mickey Loomis rigged Superdome wiring so opposing coaches' radio communications could be intercepted.
 ''This has been an intensive investigation, and after numerous interviews we have determined that there is no evidence that state laws have been violated,'' State Police Col. Mike Edmonson said Monday after meeting with Saints owner Tom Benson in New Orleans to brief him on the status of the probe.
''This has been an intensive investigation, and after numerous interviews we have determined that there is no evidence that state laws have been violated,'' State Police Col. Mike Edmonson said Monday after meeting with Saints owner Tom Benson in New Orleans to brief him on the status of the probe.
State police investigators have been working in conjunction with the FBI since the eavesdropping allegations surfaced in news reports in April.
''We found no corroborating evidence that Mickey Loomis or anybody in the Saints was engaged in wiretapping or eavesdropping,'' Edmonson said. (more)
 ''This has been an intensive investigation, and after numerous interviews we have determined that there is no evidence that state laws have been violated,'' State Police Col. Mike Edmonson said Monday after meeting with Saints owner Tom Benson in New Orleans to brief him on the status of the probe.
''This has been an intensive investigation, and after numerous interviews we have determined that there is no evidence that state laws have been violated,'' State Police Col. Mike Edmonson said Monday after meeting with Saints owner Tom Benson in New Orleans to brief him on the status of the probe. State police investigators have been working in conjunction with the FBI since the eavesdropping allegations surfaced in news reports in April.
''We found no corroborating evidence that Mickey Loomis or anybody in the Saints was engaged in wiretapping or eavesdropping,'' Edmonson said. (more)
Fin for Fino - Argentine Ex-Police Chief Indited for Spying
Argentina - A court confirmed the indictment of former Metropolitan Police head Jorge “Fino” Palacios, who is accused of using the NOSIS system to spy on opposition city lawmakers...
The victims of the alleged spying were City lawmakers Silvia La Ruffa, Diana Maffia and Gonzalo Ruanova, and Patricio Datarmini, head of the City public employees union.
Palacios is accused of leading an illicit organization aimed at wiretapping opposition lawmakers. City Mayor Mauricio Macri is also accused of taking part of the illicit organization. (more)
The victims of the alleged spying were City lawmakers Silvia La Ruffa, Diana Maffia and Gonzalo Ruanova, and Patricio Datarmini, head of the City public employees union.
Palacios is accused of leading an illicit organization aimed at wiretapping opposition lawmakers. City Mayor Mauricio Macri is also accused of taking part of the illicit organization. (more)
Hello Moto - Ex-employee Sentenced for Spying
IL - A federal judge sentenced a Chinese-born American to four years in prison for stealing millions of dollars in trade secrets from Motorola, describing her as a soft-spoken, unassuming woman who carried out a ‘‘very purposeful raid’’ on the company in the dead of night.
 In a barely audible voice and heavily accented English, 41-year-old Hanjuan Jin told the judge she was ‘‘so sorry for what happened’’ and pleaded for a second chance. Her lawyers had argued that she took the files merely to refresh her knowledge after a long absence from work and was not spying for China. They appealed for leniency and asked that Jin receive probation, in part because of her poor health. ( more)
In a barely audible voice and heavily accented English, 41-year-old Hanjuan Jin told the judge she was ‘‘so sorry for what happened’’ and pleaded for a second chance. Her lawyers had argued that she took the files merely to refresh her knowledge after a long absence from work and was not spying for China. They appealed for leniency and asked that Jin receive probation, in part because of her poor health. ( more)
But before you pull out your hankerchef...
Jin, who worked as a software engineer for Motorola Inc. for nine years, was stopped during a random security search at Chicago’s O'Hare International Airport on Feb. 28, 2007, before she could board a flight to China. Prosecutors say she was carrying $31,000 and more than 1,000 confidential Motorola documents, many stored on a laptop, four external hard drives, thumb drives and other devices.
 In a barely audible voice and heavily accented English, 41-year-old Hanjuan Jin told the judge she was ‘‘so sorry for what happened’’ and pleaded for a second chance. Her lawyers had argued that she took the files merely to refresh her knowledge after a long absence from work and was not spying for China. They appealed for leniency and asked that Jin receive probation, in part because of her poor health. ( more)
In a barely audible voice and heavily accented English, 41-year-old Hanjuan Jin told the judge she was ‘‘so sorry for what happened’’ and pleaded for a second chance. Her lawyers had argued that she took the files merely to refresh her knowledge after a long absence from work and was not spying for China. They appealed for leniency and asked that Jin receive probation, in part because of her poor health. ( more)But before you pull out your hankerchef...
Jin, who worked as a software engineer for Motorola Inc. for nine years, was stopped during a random security search at Chicago’s O'Hare International Airport on Feb. 28, 2007, before she could board a flight to China. Prosecutors say she was carrying $31,000 and more than 1,000 confidential Motorola documents, many stored on a laptop, four external hard drives, thumb drives and other devices.
Tuesday, August 28, 2012
Global TrapWire, INDECT protest planned Saturday, October 20
The TrapWire surveillance system and Europe's INDECT are the subject of a global protest planned for Saturday, October 20.
Information about the protest is being shared by Operation INDECT (OpINDECT International) and there is an #OpINDECT/#TrapWire Facebook Event Page.
It is not the first INDECT protest - but recent news about TrapWire from the Wikileaks leak of private intelligence firm Stratfor's documents has added a tanker of gas to the fire.
News and locations of the protest are being shared on various forums and social media sites primarily with a Google Map showing locations of protesters joining the efforts to raise awareness and intent to stop use of the surveillance technologies. (more)
Information about the protest is being shared by Operation INDECT (OpINDECT International) and there is an #OpINDECT/#TrapWire Facebook Event Page.
It is not the first INDECT protest - but recent news about TrapWire from the Wikileaks leak of private intelligence firm Stratfor's documents has added a tanker of gas to the fire.
News and locations of the protest are being shared on various forums and social media sites primarily with a Google Map showing locations of protesters joining the efforts to raise awareness and intent to stop use of the surveillance technologies. (more)
Monday, August 27, 2012
Espionage Research Institute International Conference - September 7th-9th
This is a counterespionage conference you don't want to miss...
 The Espionage Research Institute International's (ERII) annual conference will be held 7-9 September 2012 in Herndon, VA. The ERII conference provides a forum for ERII members to meet and discuss news and information related to the threats and recent discoveries in the fields of espionage and information security.
The Espionage Research Institute International's (ERII) annual conference will be held 7-9 September 2012 in Herndon, VA. The ERII conference provides a forum for ERII members to meet and discuss news and information related to the threats and recent discoveries in the fields of espionage and information security.
...and they make it easy to attend by holding it from Friday-Sunday (9/7-9).
The membership of ERII consists of TSCM, Counterespionage & Counterintelligence professionals and associates. TSCM is the abbreviation for "Technical Surveillance Counter Measures", it is the industry term for work that includes de-bugging sweeps, wiretap detection, and related counter-surveillance work. The purpose of TSCM is to help businesses,corporations and individuals protect themselves from unauthorized and illegal spying activities. One of the main functions of ERII is to help maintain high ethical standards in the TSCM, Counterespionage / Counterintelligence field.
 The Espionage Research Institute International's (ERII) annual conference will be held 7-9 September 2012 in Herndon, VA. The ERII conference provides a forum for ERII members to meet and discuss news and information related to the threats and recent discoveries in the fields of espionage and information security.
The Espionage Research Institute International's (ERII) annual conference will be held 7-9 September 2012 in Herndon, VA. The ERII conference provides a forum for ERII members to meet and discuss news and information related to the threats and recent discoveries in the fields of espionage and information security....and they make it easy to attend by holding it from Friday-Sunday (9/7-9).
A sneak peak...
David G. Major, President of the CI Centre, will be featured as a keynote speaker. Mr. Major's presentation on the topic of "2011/2012 Espionage Debrief: A
Worldwide Year in Review" will be on the first day of the conference
from 0900-1200 hrs.
Paul Turner of PDTG Inc.,
will be running a one (1) day Kestrel TSCM Professional Software
familiarization and basic operation day at the Espionage Research
Institute International (ERII) annual conference on Sunday September 09,
2012. His custom TSCM software is getting rave reviews.
Other presentations...
• Understanding the TSCM (RF) Spectrum Environment
• Surveillance Device Intelligence Briefing
• Nation State Espionage Briefing
• Cyber Espionage Briefing
• Surveillance Device Intelligence Briefing
• Nation State Espionage Briefing
• Cyber Espionage Briefing
The conference is always a worthwhile event. Join ERII and attend. The conference fee is $150.00 and hotel rooms are still available at $99.00 - until 8/30/12. Mention ERII when making reservations.
Where & When
Embassy Suites Dulles Airport
13341 Woodland Park Road
Herndon, VA 20171
Ph: 1-703-464-0200
September 7th through 9th, 2012
8:30AM-5:00PM
Where & When
Embassy Suites Dulles Airport
13341 Woodland Park Road
Herndon, VA 20171
Ph: 1-703-464-0200
September 7th through 9th, 2012
8:30AM-5:00PM
The membership of ERII consists of TSCM, Counterespionage & Counterintelligence professionals and associates. TSCM is the abbreviation for "Technical Surveillance Counter Measures", it is the industry term for work that includes de-bugging sweeps, wiretap detection, and related counter-surveillance work. The purpose of TSCM is to help businesses,corporations and individuals protect themselves from unauthorized and illegal spying activities. One of the main functions of ERII is to help maintain high ethical standards in the TSCM, Counterespionage / Counterintelligence field.
Labels:
counterespionage,
ERI,
fun,
miscellaneous,
spy school,
TSCM
Saturday, August 25, 2012
Eavesdropping Find: Bandera City Hall Bugged
TX - No accusations were made last week at a budget workshop but evidence was brought to light that city security may be at risk...
Bandera City Hall was checked for breaches recently, reported Mayor Pro Tem Maggie Schumacher during the city's Aug. 9 budget meeting. An unnamed security company scanned City Hall for listening “bugs” and other devices.
“There is no doubt by the (security) firm that offices had been bugged,” Schumacher said. “There were wires going into the police department.” The firm also found “cameras in the city secretary's office.”
“The report said there was so much evidence that [the City Hall] side of the building had been compromised,” Schumacher said...
“There is no doubt by the (security) firm that offices had been bugged,” Schumacher said. “There were wires going into the police department.” The firm also found “cameras in the city secretary's office.”
“The report said there was so much evidence that [the City Hall] side of the building had been compromised,” Schumacher said...
Security at City Hall has been considered a potential problem since last year when former Bandera City Police Lt. Neil McLean allegedly told Schumacher that nothing was private in city offices, Councilmember John Hegemier told the Bulletin Monday.
Hegemier said Schumacher interpreted McLean's statement as meaning the offices had been bugged, though former City Police Chief Jim Eigner said they were not. (more)
Business Espionage: The Apple Bonkers Get Theirs
Apple won a decisive victory on Friday in a lawsuit against Samsung,
a verdict that will give Apple ammunition in a far-flung patent war with its global competitors in the smartphone business.
The nine jurors in the case, who faced the daunting task of answering more than 700 questions on sometimes highly technical matters, returned a verdict after just three days of deliberations at a federal courthouse in San Jose, Calif. They found that Samsung infringed on a series of Apple’s patents on mobile devices, awarding Apple more than $1 billion in damages.
That is not a big financial blow to Samsung, one of the world’s largest electronics companies. But the decision could essentially force it and other smartphone makers to redesign their products to be less Apple-like, or risk further legal defeats. (more)
 |
| Click to enlarge. |
The nine jurors in the case, who faced the daunting task of answering more than 700 questions on sometimes highly technical matters, returned a verdict after just three days of deliberations at a federal courthouse in San Jose, Calif. They found that Samsung infringed on a series of Apple’s patents on mobile devices, awarding Apple more than $1 billion in damages.
That is not a big financial blow to Samsung, one of the world’s largest electronics companies. But the decision could essentially force it and other smartphone makers to redesign their products to be less Apple-like, or risk further legal defeats. (more)
Wednesday, August 22, 2012
Business Espionage on CNBC - Thu, 23rd 9p & 12a ET
I participated in the making
of CNBC series, Crime, Inc. ("Secrets for Sale") and thought
you might like to see it. Some of our advanced electronic surveillance
detection instrumentation is shown, and business espionage issues are
discussed. ~ Kevin
 on CNBC. “CRIME INC #9 - SECRETS FOR SALE”
on CNBC. “CRIME INC #9 - SECRETS FOR SALE”
Premieres Thursday, August 23rd 9p | 12a ET
Re-broadcast: Sunday, August 26th 11p
Spying is an ever-present threat in the workplace.
From the
coworker in the next cubicle to foreign governments, the faces of
corporate espionage are all around us. Boeing, Intel and Coca-Cola have
all been targets. The losses - estimated by the FBI to be more than 13
billion dollars a year in the United States - can go undetected for
years despite sophisticated security. Crime Inc. follows cases where livelihoods are threatened, reputations ruined and trade secrets are bought and sold. (more)
Security Directors: FREE Security White Paper - "Surreptitious Workplace Recording ...and what you can do about it."
 on CNBC. “CRIME INC #9 - SECRETS FOR SALE”
on CNBC. “CRIME INC #9 - SECRETS FOR SALE” Premieres Thursday, August 23rd 9p | 12a ET
Re-broadcast: Sunday, August 26th 11p
Spying is an ever-present threat in the workplace.
 |
| Kevin D. Murray discusses business espionage prevention with Carl Quintanilla. |
Security Directors: FREE Security White Paper - "Surreptitious Workplace Recording ...and what you can do about it."
Monday, August 20, 2012
Business Counterintelligence Conference at Kwa Maritane Bush Lodge, South Africa - September 17-19
CBIA will be hosting South Africa’s first conference on business counterintelligence September 17-19, 2012, at the Kwa Maritane Bush Lodge in the Pilanesberg, North West Province...
 |
| Click to enlarge. |
One of the key aims of the conference is to involve and to provide decision makers, managers and business unit leaders with the insight to understand business counterintelligence and how it differs from other streams of information management and security practices.
Corporate information gathering is a fact of life, even more so during hard and tough economic times...
Corporate information gathering is a fact of life, even more so during hard and tough economic times...
The conference will take participants on an eye-opening journey regarding information protection issues. Attendees will gain a practical understanding of the value added role counterintelligence plays in competitive strategy and the protection of business information.
 |
| Click to enlarge. |
Conference Topics
• What is the scope of the business espionage and information theft threat to businesses;
• Non-cyber methods of information gathering and economic espionage;
• Social engineering, tradecraft and other psychological tricks used to penetrate a target company;
• The “insider” threat and motivational factors;
• Importance of information security awareness training;
• How to protect sensitive data and high value employees;
• Countering electronic espionage in business;
• Technical surveillance countermeasures (TSCM) risk management;
• The evolving cyber threat. The cyberspace is now providing relative small scale operators the opportunity to become involved in business espionage and information theft;
• Background screening and vetting, pre-employment and existing employee screening;
• The dark side of social media and what it means for business;
• The threat of consumerisation and BYOD;
• Policies, procedures and guidelines on how to build an effective business counterintelligence capability;
• A corporate case study;
• Active dialogue session (Ask the Expert) – An interactive brainstorming session to solve common challenges and to share innovative solutions;
• Technical security product demonstrations.
• What is the scope of the business espionage and information theft threat to businesses;
• Non-cyber methods of information gathering and economic espionage;
• Social engineering, tradecraft and other psychological tricks used to penetrate a target company;
• The “insider” threat and motivational factors;
• Importance of information security awareness training;
• How to protect sensitive data and high value employees;
• Countering electronic espionage in business;
• Technical surveillance countermeasures (TSCM) risk management;
• The evolving cyber threat. The cyberspace is now providing relative small scale operators the opportunity to become involved in business espionage and information theft;
• Background screening and vetting, pre-employment and existing employee screening;
• The dark side of social media and what it means for business;
• The threat of consumerisation and BYOD;
• Policies, procedures and guidelines on how to build an effective business counterintelligence capability;
• A corporate case study;
• Active dialogue session (Ask the Expert) – An interactive brainstorming session to solve common challenges and to share innovative solutions;
• Technical security product demonstrations.
Labels:
advice,
counterespionage,
espionage,
fun,
nature,
spy school,
Tips,
trade secret
Security Alert: Conference room reservation system - Arrive® InfoPoint™
Affected Murray Associates clients can receive special attention due to our working relationship with DigitalSecurus.
DigitalSecurus has discovered that some touch screen smart devices for conference rooms have arrived in the United States infected with a computer virus/malware (malicious software).
The infection was discovered during a recent investigation into suspicious activity on a network belonging to a DigitalSecurus client. Further analysis in a lab environment by DigitalSecurus revealed a variant of the malware known as “Downadup/Conficker” virus in unopened InfoPoint AI-101 touch screen computers. DigitalSecurus contacted the manufacturer of the device, Arrive Systems, and has been working with them closely to investigate the circumstances surrounding the infection.
This malware is particularly dangerous to a network environment as it will attempt to spread itself to other computers. The virus also attempts to communicate with unauthorized computers on the Internet, possibly allowing unauthorized access to corporate files and other sensitive data.
The infection appears to have been installed onto the devices prior to shipping into the United States...
Companies using the InfoPoint AI-101 devices are advised to consider removing them from their network until they can be properly analyzed, made harmless, and patched with software updates. For further instructions on specific steps that can be taken users are encouraged to contact the manufacturer, Arrive Systems, at this link.
DigitalSecurus is an Alaskan based network security consulting firm that provides computer security consulting, analysis, forensics, security training, and computer incident response to corporations and organizations in the United States.
Hacker Targets: Computer, Smartphone, and now... Your Car
A team of top hackers working for Intel Corp's security division toil away in a West Coast garage searching for electronic bugs that could make automobiles vulnerable to lethal computer viruses...
It's scary business. Security experts say that automakers have so far failed to adequately protect these systems, leaving them vulnerable to hacks by attackers looking to steal cars, eavesdrop on conversations, or even harm passengers by causing vehicles to crash.
"You can definitely kill people," said John Bumgarner, chief technology officer of the U.S. Cyber Consequences Unit, a non-profit organization that helps companies analyze the potential for targeted computer attacks on their networks and products. (more)
It's scary business. Security experts say that automakers have so far failed to adequately protect these systems, leaving them vulnerable to hacks by attackers looking to steal cars, eavesdrop on conversations, or even harm passengers by causing vehicles to crash.
"You can definitely kill people," said John Bumgarner, chief technology officer of the U.S. Cyber Consequences Unit, a non-profit organization that helps companies analyze the potential for targeted computer attacks on their networks and products. (more)
Another Butt Dialing Lands Man in the Can
PA - A Scranton man faces drug charges after he accidentally dialed 911 while he met with a drug dealer, recording the entire conversation at Lackawanna County dispatch center Wednesday, Scranton police said...
The Lackawanna County Communications Center called Scranton police to say there was an open line to a phone that was recording a conversation inside a vehicle on the 100 block of West Market Street regarding narcotics activity and a man named "Rick," according to the complaint.
Police tracked Mr. Kryzanowski to his apartment, where they found him talking with slow and slurred speech. Police also saw pill bottles and a bottle cap with water in it in plain sight, according to the complaint. (more) (more butt dialing stories)
Police tracked Mr. Kryzanowski to his apartment, where they found him talking with slow and slurred speech. Police also saw pill bottles and a bottle cap with water in it in plain sight, according to the complaint. (more) (more butt dialing stories)
Saturday, August 18, 2012
Secrets for Sale — Premieres Thursday, August 23rd 9p | 12a ET
 on CNBC Thursday, August 23rd 9p | 12a ET
on CNBC Thursday, August 23rd 9p | 12a ET“CRIME INC #9 - SECRETS FOR SALE”
Spying is an ever-present threat in the workplace.
 |
| Kevin D. Murray discusses business espionage prevention with Carl Quintanilla. |
A 20-Year Battery Will Power the Next Generation Bugs
Imagine a battery powered bugging device, voice recorder, or GPS tracker that never needs to have it's battery changed or charged.
 |
| Current generation. |
City Labs says, "...the company’s team of scientists and engineers has developed batteries
with a 20+ year lifetime of continuous power without the requirement
for replacement or recharging. The NanoTritium™ battery can energize a
broad range of devices where battery replacement is difficult,
impractical, or even life-threatening."
The power cell generates electricity using a layer of the radioactive-element tritium, mounted onto a semiconductor.
 |
| Next generation. |
The City Labs’ battery produces nanowatts of power; it is not strong enough to power a cell phone or laptop. This is a low-power battery that can run micro-electronics, anywhere that is hard, dangerous or expensive to reach. Applications include implants such as pacemakers as well as devices in industry (sensors on deep-water oil drills) and defense. (more)
Currently, these batteries, "...are used to keep encryption keys alive in SRAM for more than 20 years...". A second generation (coming soon) will be able to do a whole lot more.
Talk Like A Spy with Throw-Away Phone Numbers
Spybusters Tip # 723: The new Burner app for iPhone generates throw-away phone numbers, which can be used for undercover operations or by those who simply prefer a deep layer of privacy.
With Burner, users can create multiple new phone numbers for a day, a week, a month, or longer, and manage all inbound calls, SMS messages, and voicemails for each number. Once you are finished with the number, you can "burn" it by taking it out of service and wiping it from your phone, as if it never existed.
Each number is a separate line within the iPhone, which can be redirected to your main mobile number, or go straight to voicemail, according to the Burner app blog...
When your phone rings, it will display details about the caller's recent social updates and check the weather where they are. The feature is also available for SMS texts. Even if you're not interested in the bells and whistles, the app also provides stripped-down caller ID information.
The White Pages app is available for free download in the Google Play store. (more)
Each number is a separate line within the iPhone, which can be redirected to your main mobile number, or go straight to voicemail, according to the Burner app blog...
Android users may not yet have access to Burner, but they can shield themselves from unwanted calls with the White Pages' new Current Caller ID app, which provides a directory of information about the incoming call.
When your phone rings, it will display details about the caller's recent social updates and check the weather where they are. The feature is also available for SMS texts. Even if you're not interested in the bells and whistles, the app also provides stripped-down caller ID information.
The White Pages app is available for free download in the Google Play store. (more)
Labels:
App,
cell phone,
FREE,
fun,
privacy,
product,
spy school,
spyware,
Tips
Thursday, August 16, 2012
Cell Phone Eavesdropping is Back... and inexpensive
A small box, known in the Czech Republic as Agáta, may be listening in on your mobile phone calls at any moment. Agáta, or IMSI Catcher, is essentially an eavesdropping device that, by using relatively simple hardware, can track phone calls and SMS messages coming in and out of mobile phones in a specific radius...
Former head of the Czech Military Intelligence Agency and a security analyst Andor Šándor underscored the danger of the widespread sale of Agátas:
"It’s been a known fact for a few years now that some companies do sell these devices. But if their use will not be in any way regulated, and access to these devices will not be in any way controlled, then a regular citizen can do absolutely nothing."
...Mr. Šándor claims that the most likely private users of Agátas are security firms or rival businesses, or even companies trying to win high-stakes tenders. (more) (home-brew IMSI Catcher)
"It’s been a known fact for a few years now that some companies do sell these devices. But if their use will not be in any way regulated, and access to these devices will not be in any way controlled, then a regular citizen can do absolutely nothing."
...Mr. Šándor claims that the most likely private users of Agátas are security firms or rival businesses, or even companies trying to win high-stakes tenders. (more) (home-brew IMSI Catcher)
Tuesday, August 14, 2012
Security Quote of the Day
"...we're at a critical moment where we need to find a different approach if we're going to protect intellectual property and the things we have at risk." — Peter G. George, President and Chief Executive Officer, Fidelis Security Systems, Inc. (more) (a different approach)
Monday, August 13, 2012
8th Raleigh Spy Conference August 22-24
Dramatic Revelations: Castro, J. Edgar Hoover, Deep Throat, CIA Secrets From the Deep and the New Profile of Today’s Terrorist Fidel Castro had foreknowledge of the JFK assassination.
Who was the real J Edgar Hoover? Deep Throat's motives were not what the public thought. How did the CIA scoop a satellite 12,000 below the sea? What is the new profile of today's terrorist? These are the topics for the 8th Raleigh Spy Conference August 22-24 at the NC Museum of History, presented by top experts drawing on the latest in declassified information. And the public is invited to learn and ask question and get to know each speaker personally...
The Raleigh Spy Conference was founded in 2003 by
magazine editor and publisher Bernie Reeves to address the increasing
flow of declassified information available since the end of the Cold
War. The Raleigh Spy Conference is recognized as the top intelligence
conference specifically for the lay public by the Association of Former
Intelligence Officers (AFIO). Three of the six conferences have been
filmed and aired on C-SPAN. (more) (video)
James Bond turns 50
It’s the big 5-0 for 007 film franchise
One of the most successful film franchises of all time, featured in Friday’s Olympic opening ceremonies, is celebrating its golden anniversary this year. TODAY’s Matt Lauer takes a look back at half a century of Bond, James Bond.
One of the most successful film franchises of all time, featured in Friday’s Olympic opening ceremonies, is celebrating its golden anniversary this year. TODAY’s Matt Lauer takes a look back at half a century of Bond, James Bond.
Need to contact the CIA from your cell phone? There's an app for that...
The Central Intelligence Agency has joined the ranks of federal agencies offering mobile applications to the public with the release of a mobile version of CIA.gov.
Included in the online exhibits are technologies developed for the CIA that eventually led to public benefits. For instance, improvements in battery technology for the agency later were incorporated into medical devices such as pacemakers and consumer products such as digital cameras.
Other items on display demonstrate the role the CIA has played in the evolution of product miniaturization. Those include a 35-mm camera designed to fit inside a pack of cigarettes; a radio receiver that fit into the stem of a pipe and that the user could "hear" through bone conduction from the jaw to the ear canal; the "insectothopter," an insect-shaped micro-drone invented in the 1970s as a proof-of-concept; and a microdot camera.
The mobile version of the CIA Museum includes dozens of images and captions of museum artifacts, articles on topics such as the hunt for Osama Bin Laden, and a timeline of events related to the work of the CIA and other U.S. intelligence agencies. (more)
Sunday, August 12, 2012
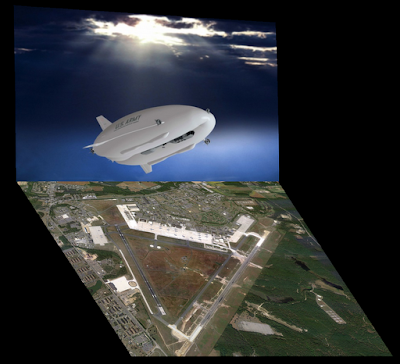
This Week on Jersey Shore - "Lemiv da Blimp"
NJ - The Army is testing its $517 million spy blimp in the skies over the New Jersey military base where the German airship Hindenburg crashed in 1937.
The Long Endurance Multi-Intelligence Vehicle spent more than 90 minutes around Joint Base McGuire-Dix-Lakehurst in Ocean County on Tuesday.
Manufacturer Northrop Grumman says the 302-foot long airship is designed to be a high altitude observation platform.
It can be operated by a crew or by remote control. (more and video) (previous blimp news)
The Long Endurance Multi-Intelligence Vehicle spent more than 90 minutes around Joint Base McGuire-Dix-Lakehurst in Ocean County on Tuesday.
Manufacturer Northrop Grumman says the 302-foot long airship is designed to be a high altitude observation platform.
It can be operated by a crew or by remote control. (more and video) (previous blimp news)
If successful, the blimp will stay in the air for up to three weeks at a time, using 2500 pounds’ worth of “sensors, antennas, data links and signals intelligence equipment” to capture still and video images of civilians and adversaries below and send the pictures to troops’ bases.
Sports World Business Espionage - Saints or Sinners
LA - A report (in April) on ESPN claimed General Manager Mickey Loomis had the ability to listen to opposing coaches during games with an electronic device installed in the team's suite at the Superdome.
Wednesday, Louisiana State Police Superintendent Col. Mike Edmonson confirmed the state's investigation into the eavesdropping claim "has moved within the FBI."
"As far as our case on the eavesdropping portion of it, we've been involved in interviews with the FBI," said Edmonson. "They brought us under their wing. We've been working closely with them. I've looked at it from a state perspective and all our findings have been turned over to the U.S. Attorney's Office who will be reviewing that along with the FBI."
Edmonson would not say if any of the information gathered and now in the possession of the FBI pointed to alleged wrongdoing by Loomis or the Saints. (more)
The fact that the case is still being investigated, and the FBI has been called in, is not a good sign. - Kevin
 |
| Mickey Loomis, before it hit the fans. |
"As far as our case on the eavesdropping portion of it, we've been involved in interviews with the FBI," said Edmonson. "They brought us under their wing. We've been working closely with them. I've looked at it from a state perspective and all our findings have been turned over to the U.S. Attorney's Office who will be reviewing that along with the FBI."
Edmonson would not say if any of the information gathered and now in the possession of the FBI pointed to alleged wrongdoing by Loomis or the Saints. (more)
Sports World Business Espionage - Gladiator PI
Australia - The South Sydney patriarch George Piggins has accused the Rabbitohs co-owners Russell Crowe and Peter Holmes a Court of sending private investigators to spy on him and search in the garbage bins of those opposed to their takeover of the club - and this is why Piggins now refuses to return to the fold.
In an open letter to South Sydney supporters, penned exclusively for The Sun-Herald, Piggins outlines his reasons for distancing himself from the club he saved from the brink of oblivion. In the letter, he states: ''Crowe and Holmes a Court used the services of Palladino and Sutherland, an American private investigation firm, to come to Australia to investigate us, as well as using other local investigators to secretly search garbage bins of those opposed to the takeover bid, and secretly photograph me, my family and friends.'' (more)
In an open letter to South Sydney supporters, penned exclusively for The Sun-Herald, Piggins outlines his reasons for distancing himself from the club he saved from the brink of oblivion. In the letter, he states: ''Crowe and Holmes a Court used the services of Palladino and Sutherland, an American private investigation firm, to come to Australia to investigate us, as well as using other local investigators to secretly search garbage bins of those opposed to the takeover bid, and secretly photograph me, my family and friends.'' (more)
Saturday, August 11, 2012
SO this Russian goes to work and finds a bug in his office...
Russia - Alexei Navalny showed up to work in Moscow on Monday to discover he was being bugged. He called the police, like many perhaps would, but not before tweeting photos and video of himself and his colleagues taking the Kremlin’s monitoring devices apart.
It’s not hard to figure out why Navalny was bugged. He’s one of Russia’s most influential anti-corruption bloggers and is at the center of a protest movement aimed at toppling the regime of President Vladimir Putin.
Since late July, the 36-year-old lawyer has faced possible arrest, trial and up to 10 years in prison for charges Putin’s prosecutors claim stem from an embezzlement scheme, but which Navalny and his supporters claim is an attempt to silence him. (more)
Bug Found in Ceiling of Jail's Chief of Operations
WV - A bugging device uncovered in an air duct in the office of the Regional Jail Authority's chief of operations has become the target of an FBI investigation, a key legislator disclosed Friday.
 The first inkling of the bizarre episode came when Delegate Dave Perry, D-Fayette, as co-chairman of a legislative interims committee, quizzed acting Regional Jail Authority Director Joe DeLong if he was aware of any inquiry - internal or external - involving his agency. DeLong is a Hancock County native.
The first inkling of the bizarre episode came when Delegate Dave Perry, D-Fayette, as co-chairman of a legislative interims committee, quizzed acting Regional Jail Authority Director Joe DeLong if he was aware of any inquiry - internal or external - involving his agency. DeLong is a Hancock County native.
...the device allegedly turned up in John Lopez' office in Charleston...
Perry said he learned that Lopez found the device July 12 after spying some residue from a ceiling tile in the chair of his office.
"It was up overhead, and it had both audio and visual, in an air duct," Perry said...
"Almost like Watergate," Perry added, characterizing the alleged bugging incident, but again emphasized his committee, when meeting Monday, will not pursue it. (more)
Perry said he learned that Lopez found the device July 12 after spying some residue from a ceiling tile in the chair of his office.
"It was up overhead, and it had both audio and visual, in an air duct," Perry said...
"Almost like Watergate," Perry added, characterizing the alleged bugging incident, but again emphasized his committee, when meeting Monday, will not pursue it. (more)
Subscribe to:
Posts (Atom)