 Thank you!
Thank you!~Kevin
 When the talks shifted to a luxury hotel in Vienna, the microwave radiation from the surveillance efforts of competing intelligence agencies was so intense that diplomats had to walk some distance from the venue to use their mobile phones.
When the talks shifted to a luxury hotel in Vienna, the microwave radiation from the surveillance efforts of competing intelligence agencies was so intense that diplomats had to walk some distance from the venue to use their mobile phones.  The National Security Agency celebrates its 64th birthday today.
The National Security Agency celebrates its 64th birthday today. Researchers report in a paper to be made public on Thursday that they have uncovered a flaw in a wireless technology that is often included in smart home devices like lights, switches, locks, thermostats...
Researchers report in a paper to be made public on Thursday that they have uncovered a flaw in a wireless technology that is often included in smart home devices like lights, switches, locks, thermostats... She would start with a telephone pitch, before offering to send more detailed information on a CD.
She would start with a telephone pitch, before offering to send more detailed information on a CD.  was once owned by English novelist Ian Fleming’s dear friend Ivar Felix C. Bryce — a real-life British spy and, in Fleming’s James Bond books, 007’s best friend, Felix.
was once owned by English novelist Ian Fleming’s dear friend Ivar Felix C. Bryce — a real-life British spy and, in Fleming’s James Bond books, 007’s best friend, Felix. [T]he Government agency agrees not to use the data as evidence in any judicial or administrative proceedings unless there is no other available and admissible probative evidence. The Government Agency shall make every effort to insure that information provided by the Contractor is non-attributable to AT&T if the data is provided to a third-party.In other words, the first rule of Hemisphere is: you do not talk about Hemisphere. more
 Alex Younger, the real-life head of M16, the British intelligence agency where the fictional super spy works, tells the British website Black History Month that Bond doesn’t have the qualities he wants for his spies.
Alex Younger, the real-life head of M16, the British intelligence agency where the fictional super spy works, tells the British website Black History Month that Bond doesn’t have the qualities he wants for his spies. Its members are a collection of anarchists, hackers, libertarians and web geeks. It sets policy through online polls – and thinks the government should do the same. It wants to make Iceland “a Switzerland of bits,” free of digital snooping.
Its members are a collection of anarchists, hackers, libertarians and web geeks. It sets policy through online polls – and thinks the government should do the same. It wants to make Iceland “a Switzerland of bits,” free of digital snooping.  The IoT insecurity trend has been building for a long time. Few paid attention. When it knocked out the Internet people start taking notice.
The IoT insecurity trend has been building for a long time. Few paid attention. When it knocked out the Internet people start taking notice. After the Royal Air Force refused the dangerous mission, code-named Operation GREENUP, John Billings, then a lieutenant in the U.S. Army Air Corps, was given the job.
After the Royal Air Force refused the dangerous mission, code-named Operation GREENUP, John Billings, then a lieutenant in the U.S. Army Air Corps, was given the job.  |
| App asking for access. |
 The tested Frequency Division Duplexing LTE network is more popular than TDD-LTE and operates in Britain, the US, and Australia. The competing Time Division Duplexing (TDD) LTE network is more common in Asian countries and in regions where population densities are higher.
The tested Frequency Division Duplexing LTE network is more popular than TDD-LTE and operates in Britain, the US, and Australia. The competing Time Division Duplexing (TDD) LTE network is more common in Asian countries and in regions where population densities are higher.  On Jan. 4 the renters met with a host, whom police believe is Rogers’ employee. They noticed security cameras in the common areas of the home and were told the private rooms had no cameras, according to the police report.
On Jan. 4 the renters met with a host, whom police believe is Rogers’ employee. They noticed security cameras in the common areas of the home and were told the private rooms had no cameras, according to the police report. of spying on his ex-girlfriend.
of spying on his ex-girlfriend. |
| My conception photo of his home office. |
 The answer, as you may have guessed, is not so simple. As the saying goes, the internet is forever, and smart, dedicated stalkers will always be able to track you down. But if you're committed — and patient — you can come awfully close to removing your digital footprint. Here's how to do it.
The answer, as you may have guessed, is not so simple. As the saying goes, the internet is forever, and smart, dedicated stalkers will always be able to track you down. But if you're committed — and patient — you can come awfully close to removing your digital footprint. Here's how to do it.
 Virtually all connected devices are susceptible to hacking, which is why the UK government banned smartphones from cabinet meetings over fears that they could be used by foreign agents to eavesdrop on sessions. Now, the ban has been extended to cover Apple Watches and similar wearables.
Virtually all connected devices are susceptible to hacking, which is why the UK government banned smartphones from cabinet meetings over fears that they could be used by foreign agents to eavesdrop on sessions. Now, the ban has been extended to cover Apple Watches and similar wearables.  Dave and Reba Williams also allege that their Water Street neighbors, Randall and Elizabeth Bean and their two adult sons, Christopher and Matthew, may also be disseminating their recordings and photographs electronically and in other ways.
Dave and Reba Williams also allege that their Water Street neighbors, Randall and Elizabeth Bean and their two adult sons, Christopher and Matthew, may also be disseminating their recordings and photographs electronically and in other ways. some users are having a hard time switching to any of Yahoo's competitors.
some users are having a hard time switching to any of Yahoo's competitors. The feature works as a way of letting people search with their voice, and storing those recordings presumably lets Google improve its language recognition tools as well as the results that it gives to people.
The feature works as a way of letting people search with their voice, and storing those recordings presumably lets Google improve its language recognition tools as well as the results that it gives to people.  According to the influential Kommersant newspaper, the Federal Security Service (FSB) planted the bug as part of an investigation into senior officials of the Russian Investigations Committee (SKR) who were said to be taking bribes. The samovar - engraved with the letters "FSB" and the organisation's logo - been presented to the head of the Investigations Committee's Internal Security Directorate, Mikhail Maksimenko, and was left sitting in his office, Moscow daily Izvestiya reports.
According to the influential Kommersant newspaper, the Federal Security Service (FSB) planted the bug as part of an investigation into senior officials of the Russian Investigations Committee (SKR) who were said to be taking bribes. The samovar - engraved with the letters "FSB" and the organisation's logo - been presented to the head of the Investigations Committee's Internal Security Directorate, Mikhail Maksimenko, and was left sitting in his office, Moscow daily Izvestiya reports. |
| Click to enlarge. |
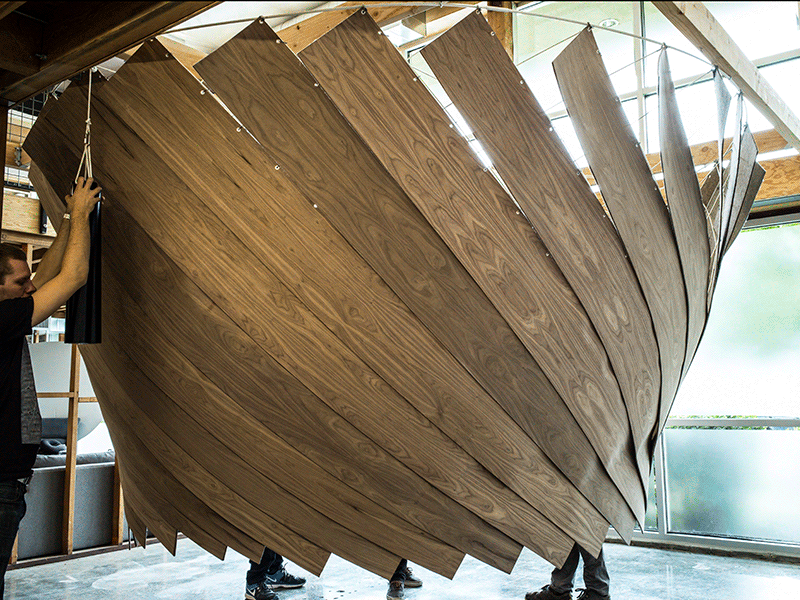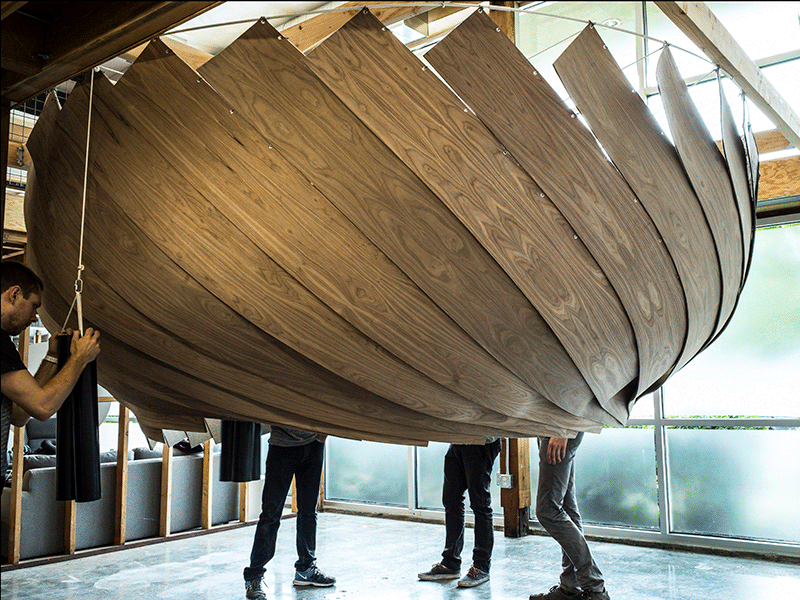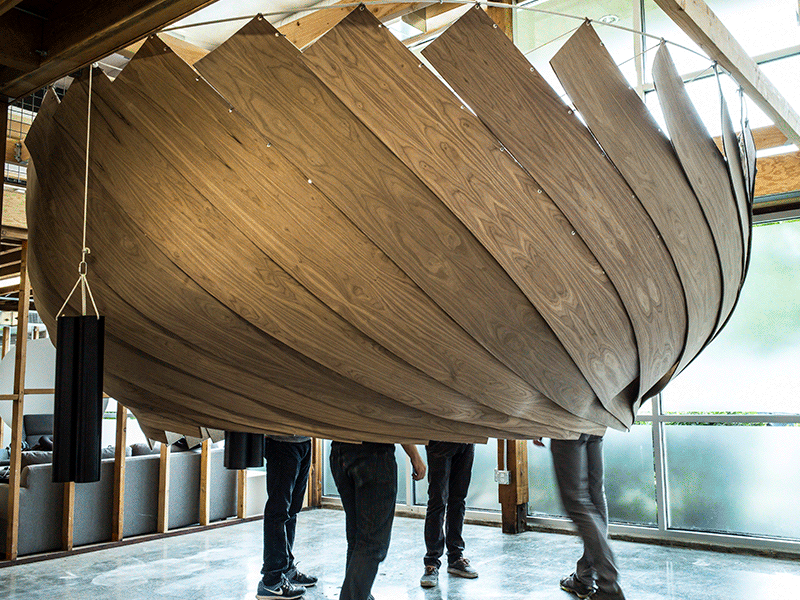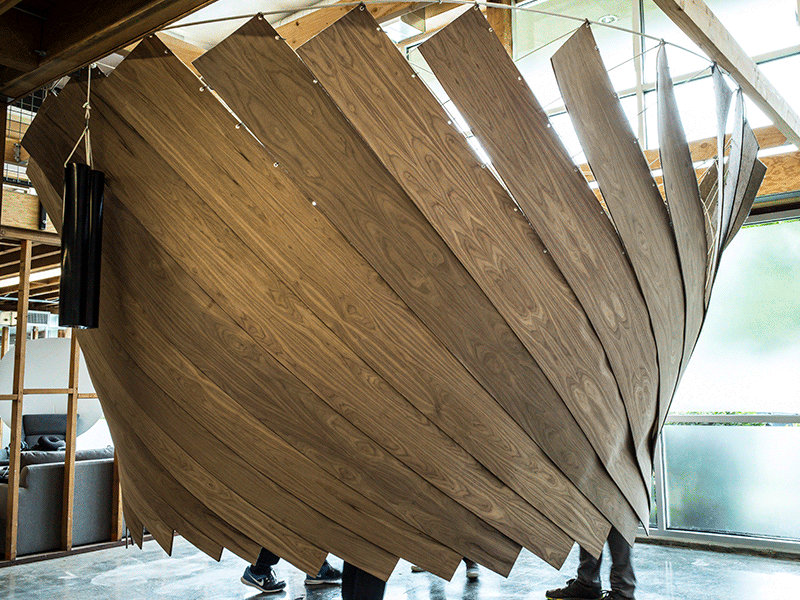 It's increasingly viewed by employees as a stressful, noisy nuisance, but with real estate prices soaring, it's not an easy trend for many companies to reverse. That's why some of the best solutions have been small-scale interventions that reconfigure existing open-plan spaces to fit employees' needs in the moment.
It's increasingly viewed by employees as a stressful, noisy nuisance, but with real estate prices soaring, it's not an easy trend for many companies to reverse. That's why some of the best solutions have been small-scale interventions that reconfigure existing open-plan spaces to fit employees' needs in the moment.  |
| The original Cone of Silence. |
 Yes, that Theremin — the creator of the musical instrument you play without even touching.
Yes, that Theremin — the creator of the musical instrument you play without even touching. But this is only one cell of a much bigger definition, in recent years the definition of what is seen as industrial espionage has increased to cover such areas as; attempts to sabotage a corporation, in some cases, malware and spyware has even entered the arena of corporate espionage. And as earlier mentioned there are the more obvious kinds of industrial espionage such as theft of trade secrets, bribery, blackmail, and technological surveillance. more
But this is only one cell of a much bigger definition, in recent years the definition of what is seen as industrial espionage has increased to cover such areas as; attempts to sabotage a corporation, in some cases, malware and spyware has even entered the arena of corporate espionage. And as earlier mentioned there are the more obvious kinds of industrial espionage such as theft of trade secrets, bribery, blackmail, and technological surveillance. more ...the most recent addition to the site has garnered less interest than the memorial, or the souvenir stalls nearby — but serves as a tangible testament to China’s perennial preoccupation: espionage.
...the most recent addition to the site has garnered less interest than the memorial, or the souvenir stalls nearby — but serves as a tangible testament to China’s perennial preoccupation: espionage.
 According to his leaked resignation letter, Tom Norris left his £80,000 a year post last year over the bus company’s covert monitoring of staff.
According to his leaked resignation letter, Tom Norris left his £80,000 a year post last year over the bus company’s covert monitoring of staff.
 The state intelligence and army officers were inspecting the pigeon that might have flown across border from Pakistan and landed in Punjab's Hoshiarpur district with some words in Urdu inscribed on its wings.
The state intelligence and army officers were inspecting the pigeon that might have flown across border from Pakistan and landed in Punjab's Hoshiarpur district with some words in Urdu inscribed on its wings. Burns said he first thought that someone was prank-calling the Port Hadlock business, but then he looked on the business’s Facebook account and “it was blowing up with disgusting comments.”
Burns said he first thought that someone was prank-calling the Port Hadlock business, but then he looked on the business’s Facebook account and “it was blowing up with disgusting comments.” Researchers at the University of Calgary in Canada, led by professor Wolfgang Tittel, set a new record for distance of transferring a quantum state by teleportation, using fibre optics cable infrastructure.
Researchers at the University of Calgary in Canada, led by professor Wolfgang Tittel, set a new record for distance of transferring a quantum state by teleportation, using fibre optics cable infrastructure.
 "They didn't go through the post office, it looks as they he hand-delivered them," said John Herrell, with the Lake County Sheriff's Office.
"They didn't go through the post office, it looks as they he hand-delivered them," said John Herrell, with the Lake County Sheriff's Office.  As modified, Rule 41 will permit federal judges to authorize expanded remote searches of electronic devices including computers and smartphones. Senator Wyden contends that the revised rule will enable federal judges to issue search warrants to permit remote searches of virtually any device, and the material accessible through that device, no matter where the device is located.
As modified, Rule 41 will permit federal judges to authorize expanded remote searches of electronic devices including computers and smartphones. Senator Wyden contends that the revised rule will enable federal judges to issue search warrants to permit remote searches of virtually any device, and the material accessible through that device, no matter where the device is located. Harinder Pal Singh, who returned from the UK three years ago, claimed British police had installed chips in his body for spying...
Harinder Pal Singh, who returned from the UK three years ago, claimed British police had installed chips in his body for spying... US District Court Judge Beryl Howell said at a hearing Friday morning that absent an objection by government attorneys (the maybe), the court would post to its website next week a list of all case numbers from 2012 in which federal prosecutors in Washington, DC applied for an order to install a pen register or a trap and trace device.
US District Court Judge Beryl Howell said at a hearing Friday morning that absent an objection by government attorneys (the maybe), the court would post to its website next week a list of all case numbers from 2012 in which federal prosecutors in Washington, DC applied for an order to install a pen register or a trap and trace device. Once a proof-of-concept, the pocket-sized USB stick now fits in any security tester's repertoire of tools and hacks, says the Hong Kong-based company that developed it.
Once a proof-of-concept, the pocket-sized USB stick now fits in any security tester's repertoire of tools and hacks, says the Hong Kong-based company that developed it. For the first time, engineers have developed a fast random number generator based on a quantum mechanical process that could deliver the world’s most secure encryption keys in a package tiny enough to use in a mobile device.
For the first time, engineers have developed a fast random number generator based on a quantum mechanical process that could deliver the world’s most secure encryption keys in a package tiny enough to use in a mobile device.