MD - A Maryland delegate is proposing changes to state wiretap law after he was inspired by two filmmakers who claimed to be a pimp and prostitute seeking tax advice while surreptitiously taping ACORN staffers in Baltimore.
MD - A Maryland delegate is proposing changes to state wiretap law after he was inspired by two filmmakers who claimed to be a pimp and prostitute seeking tax advice while surreptitiously taping ACORN staffers in Baltimore.Delegate Richard Sossi, an Eastern Shore Republican, wants to provide immunity for people who intercept a wire, oral or electronic communication that provides evidence of the commission of a felony.
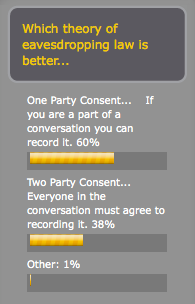
Right now in Maryland, it is illegal to record private conversations unless both parties consent to the taping. (more)
This is one way to deter James O'Keefe from showing up at your political headquarters with a team of fake telephone technicians with hidden cameras.
Pssst... (BARTNICKI v. VOPPER (99-1687) 200 F.3d 109) already accomplished this in a 2001 Supreme Court ruling.
"Privacy of communication is an important interest. However, in this suit, privacy concerns give way when balanced against the interest in publishing matters of public importance. One of the costs associated with participation in public affairs is an attendant loss of privacy."
See Extortionography.
Pssst... (BARTNICKI v. VOPPER (99-1687) 200 F.3d 109) already accomplished this in a 2001 Supreme Court ruling.
"Privacy of communication is an important interest. However, in this suit, privacy concerns give way when balanced against the interest in publishing matters of public importance. One of the costs associated with participation in public affairs is an attendant loss of privacy."
See Extortionography.