A recently retired city police captain is now facing a felony charge of eavesdropping.
Brian Wentland, a former training captain who left the Lockport Police Department in February, was charged Friday, according to Niagara County District Attorney Caroline A. Wojtaszek.
The charges relate to a May 6, 2013 phone call involving his ex-wife and another person.
The timing of the charges was critical in the case.Wentland’s arrest was just two days before the five-year statute of limitations expired on the charge. more
Monday, May 7, 2018
Technical Surveillance Countermeasures (TSCM) and Cell Phone Security Presentation
 As part of the New Jersey Association for Justice Boardwalk Seminar, Murray Associates president Kevin D. Murray will present a session entitled, “Technical Surveillance Countermeasures (TSCM) and Cell Phone Security.”
As part of the New Jersey Association for Justice Boardwalk Seminar, Murray Associates president Kevin D. Murray will present a session entitled, “Technical Surveillance Countermeasures (TSCM) and Cell Phone Security.”Eavesdropping, wiretapping, snooping, voyeurism, and espionage are covert activities. The victim rarely knows when it happens. Kevin D. Murray explores the world of corporate espionage, explaining how many companies are bleeding profits for lack of a counterespionage strategy.
Regularly scheduled TSCM inspections narrow the window-of-vulnerability, spot new security loopholes, identify decaying security measures and practices, disrupt the spy’s intelligence collection phase, and keep counterespionage awareness levels elevated.
"Success-to-failure ratios are similar… most airplanes don’t crash; most people don’t drown in their baths; most houses don’t burn to the ground whenever the stove is used… and, most spying goes undiscovered." ~Kevin more
Thursday, May 3, 2018
Audio Adversarial Examples: Targeted Attacks on Speech-to-Text
 We construct targeted audio adversarial examples on automatic speech recognition.
We construct targeted audio adversarial examples on automatic speech recognition. Given any audio waveform, we can produce another that is over 99.9% similar, but transcribes as any phrase we choose (recognizing up to 50 characters per second of audio).
We apply our white-box iterative optimization-based attack to Mozilla’s implementation DeepSpeech end-to-end, and show it has a 100% success rate.
The feasibility of this attack introduces a new domain to study adversarial examples. more audio examples
From one of our Blue Blaze irregulars... "Audio
Adversarialism is the practice of fooling voice-to-text and voice
recognition systems by effectively embedding ‘hidden’ commands in audio
files which are inaudible to human ears but which are picked up by
speakers and mean, in theory, that we might hear the telly saying
“Should have gone to Specsavers!” where instead our Amazon Echo is in
fact hearing “Alexa, lock all the doors, turn on the gas and start
sparking all the bogs in 00:59, 00:58…”. This is...not scary at all, oh
no. Hi Siri! Hi Alexa!"
Thursday, April 26, 2018
Spycam Found in Starbucks Restroom... again.
GA - Police have launched an investigation after a camera was discovered last week inside a restroom at a Starbucks store in an Atlanta suburb.
A 25-year-old customer reportedly found the device Tuesday, taped under a baby changing station.
According to a police report, the woman removed the camera and alerted the manager. The manager then notified Starbucks’ corporate office...
The manager gave the camera to police for inspection. Authorities reportedly found 25 videos stored on the camera, including several that reportedly showed people using the restroom. more
N.B. Starbucks, you and any business with restrooms really need to read this.
 |
| http://tinyurl.com/ya5xvns2 |
According to a police report, the woman removed the camera and alerted the manager. The manager then notified Starbucks’ corporate office...
The manager gave the camera to police for inspection. Authorities reportedly found 25 videos stored on the camera, including several that reportedly showed people using the restroom. more
N.B. Starbucks, you and any business with restrooms really need to read this.
Wednesday, April 25, 2018
A.I. vs. Human Spies - Guess who wins
Human spies will soon be relics of the past, and the CIA knows it. Dawn Meyerriecks, the Agency’s deputy director for technology development, recently told an audience at an intelligence conference in Florida the CIA was adapting to a new landscape where its primary adversary is a machine, not a foreign agent.
 Meyerriecks, speaking to CNN after the conference, said other countries have relied on AI to track enemy agents for years. She went on to explain the difficulties encountered by current CIA spies trying to live under an assumed identity in the era of digital tracking and social media, indicating the modern world is becoming an inhospitable environment to human spies.
Meyerriecks, speaking to CNN after the conference, said other countries have relied on AI to track enemy agents for years. She went on to explain the difficulties encountered by current CIA spies trying to live under an assumed identity in the era of digital tracking and social media, indicating the modern world is becoming an inhospitable environment to human spies.
But the CIA isn’t about to give up...
Today’s spies have the same problem as yesterday’s: the need to be invisible. What’s changed is the adversary. Instead of fooling people with fake documents and well-told lies, agents have to fool computers capable of picking out a single face in a crowd.
According to Meyerriecks at least 30 countries have the capability to do this with current CCTV camera systems...
We’ve always thought spies, like James Bond, had the coolest gadgets. Now they’re being replaced by them. more
 Meyerriecks, speaking to CNN after the conference, said other countries have relied on AI to track enemy agents for years. She went on to explain the difficulties encountered by current CIA spies trying to live under an assumed identity in the era of digital tracking and social media, indicating the modern world is becoming an inhospitable environment to human spies.
Meyerriecks, speaking to CNN after the conference, said other countries have relied on AI to track enemy agents for years. She went on to explain the difficulties encountered by current CIA spies trying to live under an assumed identity in the era of digital tracking and social media, indicating the modern world is becoming an inhospitable environment to human spies. But the CIA isn’t about to give up...
Today’s spies have the same problem as yesterday’s: the need to be invisible. What’s changed is the adversary. Instead of fooling people with fake documents and well-told lies, agents have to fool computers capable of picking out a single face in a crowd.
According to Meyerriecks at least 30 countries have the capability to do this with current CCTV camera systems...
We’ve always thought spies, like James Bond, had the coolest gadgets. Now they’re being replaced by them. more
Politician: His Office Was Bugged and I am Really Pissed
Ghana - Maverick Politician and Member of Parliament for Assin South, Ken Agyapong has said he would have shot to death the Security Coordinator of Metro Mass Transit (MMT) Company if he were to be the Managing Director, Bennet Aboagye...
 The Security Coordinator, Fusseini Lawal Laah has confessed to bugging the office of the MMT Boss, Bennet Aboagye by secretly installing a recording device.
The Security Coordinator, Fusseini Lawal Laah has confessed to bugging the office of the MMT Boss, Bennet Aboagye by secretly installing a recording device.
“The Security Coordinator had the confidence to go and meet with the National Security Coordinator and other big men and has confessed that he bugged the MD’s office. What is going on in this country, and you entertain such person, that guy has to be arrested. He bugged the office and has transcribed all the recording and he’s moving about with it. The guy, I’m warning him, if this country were to be America, they would have taken care of him easily," Ken Agyapong said. more
 The Security Coordinator, Fusseini Lawal Laah has confessed to bugging the office of the MMT Boss, Bennet Aboagye by secretly installing a recording device.
The Security Coordinator, Fusseini Lawal Laah has confessed to bugging the office of the MMT Boss, Bennet Aboagye by secretly installing a recording device.“The Security Coordinator had the confidence to go and meet with the National Security Coordinator and other big men and has confessed that he bugged the MD’s office. What is going on in this country, and you entertain such person, that guy has to be arrested. He bugged the office and has transcribed all the recording and he’s moving about with it. The guy, I’m warning him, if this country were to be America, they would have taken care of him easily," Ken Agyapong said. more
Corporate Espionage: Spying on X-Ray Machines
 A mysterious hacking group has been spying on the healthcare sector by going as far to infect computers that control X-ray and MRI machines with malware.
A mysterious hacking group has been spying on the healthcare sector by going as far to infect computers that control X-ray and MRI machines with malware. Fortunately, sabotage and patient data collection doesn't appear to be a motive behind the hacking. The attackers were probably focused on corporate espionage and studying how the medical software onboard the computers worked, the security firm Symantec said on Monday.
Evidence shows that the hackers were focused on collecting data about the infected computers and their networks. DiMaggio speculates this may have been done to learn how to pirate the medical software onboard. more
Digital Assistants: The Eavesdropping Attacks Begin
It's important not to overstate the security risks of the Amazon Echo and other so-called smart speakers. They're useful, fun, and generally have well thought-out privacy protections.
 Then again, putting a mic in your home naturally invites questions over whether it can be used for eavesdropping—which is why researchers at the security firm Checkmarx started fiddling with Alexa, to see if they could turn it into a spy device. They did, with no intensive meddling required.
Then again, putting a mic in your home naturally invites questions over whether it can be used for eavesdropping—which is why researchers at the security firm Checkmarx started fiddling with Alexa, to see if they could turn it into a spy device. They did, with no intensive meddling required.
The attack, which Amazon has since fixed, follows the intended flow of using and programming an Echo. Because an Echo's mic only activates to send sound over the internet when someone says a wake word—usually "Alexa"— the researchers looked to see if they could piggyback on one of those legitimate reactions to listen in. A few clever manipulations later, they'd achieved their goal...
There are clear limitations to this eavesdropping approach. It would only have given attackers transcriptions, not audio recordings, of a target's conversations. more
Our advice to clients, "Keep these things out of offices and conference rooms where confidential discussions are held." ~Kevin
 Then again, putting a mic in your home naturally invites questions over whether it can be used for eavesdropping—which is why researchers at the security firm Checkmarx started fiddling with Alexa, to see if they could turn it into a spy device. They did, with no intensive meddling required.
Then again, putting a mic in your home naturally invites questions over whether it can be used for eavesdropping—which is why researchers at the security firm Checkmarx started fiddling with Alexa, to see if they could turn it into a spy device. They did, with no intensive meddling required.The attack, which Amazon has since fixed, follows the intended flow of using and programming an Echo. Because an Echo's mic only activates to send sound over the internet when someone says a wake word—usually "Alexa"— the researchers looked to see if they could piggyback on one of those legitimate reactions to listen in. A few clever manipulations later, they'd achieved their goal...
There are clear limitations to this eavesdropping approach. It would only have given attackers transcriptions, not audio recordings, of a target's conversations. more
Our advice to clients, "Keep these things out of offices and conference rooms where confidential discussions are held." ~Kevin
Saturday, April 21, 2018
Friday, April 20, 2018
FutureWatch: Coming Soon to a Surveillance Van Laptop Near You? EarthNow
Of interest to anyone in surveillance, anyone...
EarthNow LLC announces intent to deploy a large constellation of advanced imaging satellites that will deliver real-time, continuous video of almost anywhere on Earth...
According to EarthNow’s founder and CEO, Russell Hannigan, “EarthNow is ambitious and unprecedented, but our objective is simple; we want to connect you visually with Earth in real-time...
 EarthNow represents a dramatic leap forward in capability compared to other Earth observation satellite systems which deliver pictures and sometimes video clips to users many minutes, hours and even days after they are requested. Hannigan said, “With existing systems, users can see only what has happened in the past. With EarthNow’s constellation of satellites, you will see events unfold as they happen in real-time.” ...
EarthNow represents a dramatic leap forward in capability compared to other Earth observation satellite systems which deliver pictures and sometimes video clips to users many minutes, hours and even days after they are requested. Hannigan said, “With existing systems, users can see only what has happened in the past. With EarthNow’s constellation of satellites, you will see events unfold as they happen in real-time.” ...
Initially, EarthNow will offer commercial video and intelligent vision services to a range of government and enterprise customers...
In parallel, EarthNow plans to create compelling “live Earth video” mass market applications that can be accessed instantly from a smartphone or tablet. “We are excited by the prospect of giving everyone a stunningly-beautiful real-time window on your world from space. With EarthNow, we will all become virtual astronauts,” said Hannigan. more
EarthNow LLC announces intent to deploy a large constellation of advanced imaging satellites that will deliver real-time, continuous video of almost anywhere on Earth...
According to EarthNow’s founder and CEO, Russell Hannigan, “EarthNow is ambitious and unprecedented, but our objective is simple; we want to connect you visually with Earth in real-time...
 EarthNow represents a dramatic leap forward in capability compared to other Earth observation satellite systems which deliver pictures and sometimes video clips to users many minutes, hours and even days after they are requested. Hannigan said, “With existing systems, users can see only what has happened in the past. With EarthNow’s constellation of satellites, you will see events unfold as they happen in real-time.” ...
EarthNow represents a dramatic leap forward in capability compared to other Earth observation satellite systems which deliver pictures and sometimes video clips to users many minutes, hours and even days after they are requested. Hannigan said, “With existing systems, users can see only what has happened in the past. With EarthNow’s constellation of satellites, you will see events unfold as they happen in real-time.” ...Initially, EarthNow will offer commercial video and intelligent vision services to a range of government and enterprise customers...
In parallel, EarthNow plans to create compelling “live Earth video” mass market applications that can be accessed instantly from a smartphone or tablet. “We are excited by the prospect of giving everyone a stunningly-beautiful real-time window on your world from space. With EarthNow, we will all become virtual astronauts,” said Hannigan. more
What is the resolution?
"The native video resolution, combined with image enhancement
techniques, is designed to enable event monitoring and tracking
applications consistent with existing and future customer requirements." hummmm
Labels:
#spycam,
aerial,
business,
FutureWatch,
privacy,
product,
surveillance,
tracking
Quote of the Week - Made-in-China Warning
From the Congressional study: Supply Chain Vulnerabilities from China in U.S. Federal Information and Communications Technology - APRIL 2018
 "The supply chain threat to U.S. national security stems from products produced, manufactured, or assembled by entities that are owned, directed, or subsidized by national governments or entities known to pose a potential supply chain or intelligence threat to the United States, including China. These products could be modified to (1) perform below expectations or fail, (2) facilitate state or corporate espionage, or (3) otherwise compromise the confidentiality, integrity, or availability of a federal information technology system." more
"The supply chain threat to U.S. national security stems from products produced, manufactured, or assembled by entities that are owned, directed, or subsidized by national governments or entities known to pose a potential supply chain or intelligence threat to the United States, including China. These products could be modified to (1) perform below expectations or fail, (2) facilitate state or corporate espionage, or (3) otherwise compromise the confidentiality, integrity, or availability of a federal information technology system." more
 "The supply chain threat to U.S. national security stems from products produced, manufactured, or assembled by entities that are owned, directed, or subsidized by national governments or entities known to pose a potential supply chain or intelligence threat to the United States, including China. These products could be modified to (1) perform below expectations or fail, (2) facilitate state or corporate espionage, or (3) otherwise compromise the confidentiality, integrity, or availability of a federal information technology system." more
"The supply chain threat to U.S. national security stems from products produced, manufactured, or assembled by entities that are owned, directed, or subsidized by national governments or entities known to pose a potential supply chain or intelligence threat to the United States, including China. These products could be modified to (1) perform below expectations or fail, (2) facilitate state or corporate espionage, or (3) otherwise compromise the confidentiality, integrity, or availability of a federal information technology system." more
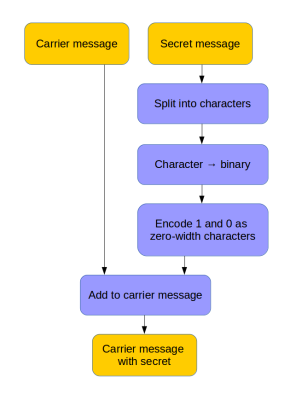
Detective Science: Fingerprinting Text to Discover Data Leakers
Fingerprinting text; the ability to encode hidden data within a string of characters opens up a large number of opportunities.
Spybuster Tip: For example, someone within your team is leaking confidential information but you don’t know who. Simply send each team member some classified text with their name encoded in it. Wait for it to be leaked, then extract the name from the text — the classic canary trap.
Here’s a method that hides data in text using zero-width characters. Unlike various other ways of text fingerprinting, zero width characters are not removed if the formatting is stripped, making them nearly impossible to get rid of without re-typing the text or using a special tool. In fact you’ll have a hard time detecting them at all – even terminals and code editors won’t display them. more
Thursday, April 19, 2018
Denny Hatch is Pissed at 451 Privacy Sucking Companies... under one roof!
Denny Hatch* warns... Verizon's OATH is a consortium of 451 "marketing partners" engaged in massive snoop operations to steal every scintilla of data about you, your family, your children, friends, business associates, enemies, even your pets.
Up for grabs: your most intimate secrets, correspondence, searches, downloads, purchases, trysts, travels, travails and browsing.
Any and all Internet intercourse by and about you is captured and spread...
For 27,679 words describing the details of Oath, click here.
Be sure to click on all permutations. more
* Denny's Note to Readers: May I send you an alert when each new blog is being published? If so, kindly give me the okay by sending your First Name, Last Name and e-mail to me. I guarantee your personal information will not be shared with anyone at any time for any reason. I look forward to being in touch! Cheers!
 |
| Click to enlarge. |
Any and all Internet intercourse by and about you is captured and spread...
For 27,679 words describing the details of Oath, click here.
Be sure to click on all permutations. more
* Denny's Note to Readers: May I send you an alert when each new blog is being published? If so, kindly give me the okay by sending your First Name, Last Name and e-mail to me. I guarantee your personal information will not be shared with anyone at any time for any reason. I look forward to being in touch! Cheers!
Wednesday, April 18, 2018
Butt Dialing Causes a Stink
Former state employee James Stephens, from Cedartown, Georgia, accidentally butt-dialed his boss and now he has a new job and is suing his ex-boss...
"His boss called my client's private cell phone from his own private cell phone," Guldenschuh said. "They were both at home when the conversation took place, which tangentially was work related. When the conversation ended, my client walked into the kitchen and, after a time, touched his phone and pocket-dialed his boss.
 "The boss determined my client was not talking to him but listened for about 12 and a half minutes," Guldenschuh said. "James and his wife spoke about the phone call he just had with his boss. Mrs. Stevens made some unflattering comments about his boss which the boss took negatively. So the boss ended up firing my client."...
"The boss determined my client was not talking to him but listened for about 12 and a half minutes," Guldenschuh said. "James and his wife spoke about the phone call he just had with his boss. Mrs. Stevens made some unflattering comments about his boss which the boss took negatively. So the boss ended up firing my client."...
It was shortly after that that Stephens decided to sue his ex-boss for eavesdropping and invading his privacy. more
"His boss called my client's private cell phone from his own private cell phone," Guldenschuh said. "They were both at home when the conversation took place, which tangentially was work related. When the conversation ended, my client walked into the kitchen and, after a time, touched his phone and pocket-dialed his boss.
 "The boss determined my client was not talking to him but listened for about 12 and a half minutes," Guldenschuh said. "James and his wife spoke about the phone call he just had with his boss. Mrs. Stevens made some unflattering comments about his boss which the boss took negatively. So the boss ended up firing my client."...
"The boss determined my client was not talking to him but listened for about 12 and a half minutes," Guldenschuh said. "James and his wife spoke about the phone call he just had with his boss. Mrs. Stevens made some unflattering comments about his boss which the boss took negatively. So the boss ended up firing my client."...It was shortly after that that Stephens decided to sue his ex-boss for eavesdropping and invading his privacy. more
School Super Suspended over Eavesdropping on Testimony Against Him
MI - The superintendent of Hale Area Schools (HAS) is facing one felony count of eavesdropping, which is punishable by up to two years of incarceration and/or fines of $2,000...
...the HAS Board of Education placed Vannest on paid administrative leave, following allegations that he had recorded a closed session meeting of the board in a manner contrary to Michigan law.
...a formal complaint had been filed against Vannest by the parent of a student.
 ...the recording begins as the meeting is called into a closed session. None of the recording takes place during the “open” portion of the meeting.
...the recording begins as the meeting is called into a closed session. None of the recording takes place during the “open” portion of the meeting.
Vannest’s phone was allegedly left in the room, recording the testimony of witnesses and board members’ questions to those witnesses.
The statement in support reads that it is believed that Vannest intentionally left the device in the room to record/eavesdrop on the conversation and testimony of the witnesses and teachers who were called in for the complaint filed against him.
When police interviewed Vannest, he allegedly stated that he felt the recording was gathered by himself in error. more
...the HAS Board of Education placed Vannest on paid administrative leave, following allegations that he had recorded a closed session meeting of the board in a manner contrary to Michigan law.
...a formal complaint had been filed against Vannest by the parent of a student.
 ...the recording begins as the meeting is called into a closed session. None of the recording takes place during the “open” portion of the meeting.
...the recording begins as the meeting is called into a closed session. None of the recording takes place during the “open” portion of the meeting.Vannest’s phone was allegedly left in the room, recording the testimony of witnesses and board members’ questions to those witnesses.
The statement in support reads that it is believed that Vannest intentionally left the device in the room to record/eavesdrop on the conversation and testimony of the witnesses and teachers who were called in for the complaint filed against him.
When police interviewed Vannest, he allegedly stated that he felt the recording was gathered by himself in error. more
Subscribe to:
Comments (Atom)