Facebook is being sued for $15 billion for tracking users, even after they have logged out of the social network, and violating federal wiretap laws.
Today’s lawsuit, filed in Federal Court in San Jose, California, combines 21 separate cases across the U.S. in 2011 and early 2012... If the claimants are successful in their case against Facebook, they could prevent Menlo Park from collecting the huge amount of data it collects about its users to serve ads back to them.
Like the previous lawsuits, Facebook is once again being accused of violating the Federal Wiretap Act, which provides statutory damages per user of $100 per day per violation, up to a maximum per user of $10,000. The complaint also asserts claims under the Computer Fraud and Abuse Act, the Stored Communications Act, various California Statutes, and California common law. It’s worth noting that similar cases against Facebook and others filed under the wiretap law have been thrown out because browser cookies are simply not considered wiretaps and plaintiffs have difficulty proving any harm. (more)
Friday, May 18, 2012
Android Cell Phone Users Security Alert
Malware targeting Android users has nearly quadrupled since 2011. As you can see in the graph, 10 Android malware families were detected in Q1 2011. This number increased for two quarters in a row, then dipped for one, and then finally settled at 37 in Q1 2012. That means a year-over-year growth of 270 percent.
The data comes from security firm F-Secure. The trend was revealed today in the company’s 47-page Mobile Threat Report Q1 2012 (PDF).
 It makes sense that both the number of malware families and malicious Android APKs is increasing, but it’s still staggering to see that the latter number is now over 3,000, whereas last year it was just above 100.
It makes sense that both the number of malware families and malicious Android APKs is increasing, but it’s still staggering to see that the latter number is now over 3,000, whereas last year it was just above 100.
The increase in malware numbers is indicative of a wider increase in mobile threats, according to F-Secure. Even more worrying, however, is that the Finnish security firm warned many of the apps are targeting Android users’ financial data, noting that 34 of the current malware families are designed to steal money from infected smartphones. (more)
Tip: Do not download, open or install anything unless you absolutely need it and are 100% confident it is coming to you from a trusted source. ~Kevin
The data comes from security firm F-Secure. The trend was revealed today in the company’s 47-page Mobile Threat Report Q1 2012 (PDF).
 It makes sense that both the number of malware families and malicious Android APKs is increasing, but it’s still staggering to see that the latter number is now over 3,000, whereas last year it was just above 100.
It makes sense that both the number of malware families and malicious Android APKs is increasing, but it’s still staggering to see that the latter number is now over 3,000, whereas last year it was just above 100. The increase in malware numbers is indicative of a wider increase in mobile threats, according to F-Secure. Even more worrying, however, is that the Finnish security firm warned many of the apps are targeting Android users’ financial data, noting that 34 of the current malware families are designed to steal money from infected smartphones. (more)
Tip: Do not download, open or install anything unless you absolutely need it and are 100% confident it is coming to you from a trusted source. ~Kevin
Password Evaluation Program Will Surprise You
Passfault evaluates the strength of passwords accurately enough to predict the time to crack. It makes creating passwords and password policies significantly more intuitive and simple.
When setting a password, Passfault examines the password, looking for common patterns. Passfault than measures the strength of the patterns and combinations of patterns. The end result is a more academic and accurate measurement of password strength. (more) (test your password)
You might think a password like 123!@#qweQWE would provide excellent protection. Wrongo. It can be cracked in a day according to Passfault. Why? Because it contains a readily identifiable pattern of keystrokes. Now try something easy to remember like ToBeOrNotToBe. Surprised? Thought so. ~Kevin
Friday, May 11, 2012
America Begins to Strike Back Publicly Against Trade Secret Thefts (Plus, an idea for a change in the law.)
The Federal Bureau of Investigation's spy hunters usually shy away from drawing attention. But they're hoping the public takes notice of a new campaign trying to stop foreign spies from stealing trade secrets from U.S. companies.
The FBI, which is responsible for investigating breaches by foreign intelligence agencies, Friday will unveil billboards in nine cities around the country with the message: Protect America's Trade Secrets. The billboards direct the public to a section of the FBI website where the bureau provides warning signs to look for in the cubicle next to you.
Behind the campaign is the government's view that state-sponsored espionage targeting companies is growing so fast it is a national security concern. Lost trade secrets lead to lost jobs and in a time of economic struggle poses a national threat, says Frank Figliuzzi, the FBI's assistant director for counterintelligence. (more)
Note to FBI... Awareness is good, but it is not enough. Some private-sector intellectual property is so vital it should be classified as a National Security Resource.
The centuries-old, lopsided, 'punish the spy' model of protecting intellectual property has never worked. (more) (more) Caretakers of national security level proprietary information need to be held legally accountable for its protection. Doing this will give the law the balance and weight it needs to be effective.
Recommendation: Amend the Espionage Act to include mandatory, pro-active, business counterespionage security requirements. ~Kevin
The centuries-old, lopsided, 'punish the spy' model of protecting intellectual property has never worked. (more) (more) Caretakers of national security level proprietary information need to be held legally accountable for its protection. Doing this will give the law the balance and weight it needs to be effective.
Recommendation: Amend the Espionage Act to include mandatory, pro-active, business counterespionage security requirements. ~Kevin
Labels:
advice,
business,
counterespionage,
FBI,
government,
historical,
law,
mores,
trade secret
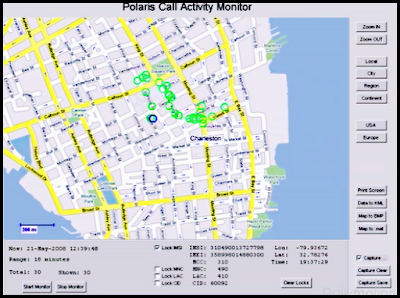
Cell Phone Tracking Insight - You're In Sight
This week at the CTIA show in New Orleans, Polaris Wireless unveiled Altus Mobile, an application that lets law-enforcement personnel track suspects via their cellphone numbers or mobile equipment identifier — a 56-bit identification number that is burned into the device and is extremely difficult to modify. The application leverages Polaris’s Wireless Location Signatures platform, which simultaneously can locate all subscriber devices on a wireless network, both in real time and historically.
That means law-enforcement officers will know where a suspect is, where he has been and where he is heading at any given moment, said Mahesh Patel, Polaris’s senior vice president of products and technology.
“Previously, this information was available to them on their desktops through our Altus surveillance solution, but now officers can take this information into the field with them,” Patel said. “Real-time access to this kind of intelligence will be a big plus for tactical operations.” (more)
“Previously, this information was available to them on their desktops through our Altus surveillance solution, but now officers can take this information into the field with them,” Patel said. “Real-time access to this kind of intelligence will be a big plus for tactical operations.” (more)
Verizon Mates With Cellcrypt - Bet You Can't Hear Me Now
UK mobile security firm Cellcrypt is partnering with carrier giant Verizon to sell its voice encryption technology for mobiles and smartphones to the US Government, the pair have announced.
Already in testing with unnamed US Government departments the service will be formally released later in 2012 as a co-branded product that marks a major foot in the door for Cellcrypt.
Working on Android, iPhone and BlackBerrys, the company’s software encrypts GSM mobile, WiFi and satellite phone calls to FIPS 140-2 level between handsets running the same software, defeating the potential for man-in-the-middle eavesdropping. (more)
Already in testing with unnamed US Government departments the service will be formally released later in 2012 as a co-branded product that marks a major foot in the door for Cellcrypt.
Working on Android, iPhone and BlackBerrys, the company’s software encrypts GSM mobile, WiFi and satellite phone calls to FIPS 140-2 level between handsets running the same software, defeating the potential for man-in-the-middle eavesdropping. (more)
Wednesday, May 9, 2012
FBI - Beware of Software Update Messages when Traveling
Recent analysis from the FBI and other government agencies demonstrates that malicious actors are targeting travelers abroad through pop-up windows while establishing an Internet connection in their hotel rooms.
Recently, there have been instances of travelers' laptops being infected with malicious software while using hotel Internet connections. In these instances, the traveler was attempting to setup the hotel room Internet connection and was presented with a pop-up window notifying the user to update a widely-used software product. If the user clicked to accept and install the update, malicious software was installed on the laptop. The pop-up window appeared to be offering a routine update to a legitimate software product for which updates are frequently available.
The FBI recommends that all government, private industry, and academic personnel who travel abroad take extra caution before updating software products on their hotel Internet connection. (more)
Recently, there have been instances of travelers' laptops being infected with malicious software while using hotel Internet connections. In these instances, the traveler was attempting to setup the hotel room Internet connection and was presented with a pop-up window notifying the user to update a widely-used software product. If the user clicked to accept and install the update, malicious software was installed on the laptop. The pop-up window appeared to be offering a routine update to a legitimate software product for which updates are frequently available.
The FBI recommends that all government, private industry, and academic personnel who travel abroad take extra caution before updating software products on their hotel Internet connection. (more)
Spook Summer School Saturday
Spy School — a Tampa Bay History Center program specially designed for teens — will instruct youngsters about surveillance, information gathering and disguise
 Agents and experts will teach children ages 12 to 18, offering tips on how to enter the espionage career field.
Agents and experts will teach children ages 12 to 18, offering tips on how to enter the espionage career field.
The program costs $60 per student but history center members get a $5 discount. Spy School begins Saturday and offers a guided tour with curator Rodney Kite-Powell.
The Tampa Bay area might not seem like an obvious spy hub. But many retired FBI, CIA and military members live in the area, and one of the nation's more high-profile spy court cases unfolded in 2001 in a U.S. District Court in Tampa. Also, United States Special Operations Command is based in Tampa.
For information on Spy School, call (813) 675-8960 or email Jennifer Tyson, the center's assistant curator of education, at jtyson @tampabayhistorycenter .org. (more)
 Agents and experts will teach children ages 12 to 18, offering tips on how to enter the espionage career field.
Agents and experts will teach children ages 12 to 18, offering tips on how to enter the espionage career field. The program costs $60 per student but history center members get a $5 discount. Spy School begins Saturday and offers a guided tour with curator Rodney Kite-Powell.
The Tampa Bay area might not seem like an obvious spy hub. But many retired FBI, CIA and military members live in the area, and one of the nation's more high-profile spy court cases unfolded in 2001 in a U.S. District Court in Tampa. Also, United States Special Operations Command is based in Tampa.
For information on Spy School, call (813) 675-8960 or email Jennifer Tyson, the center's assistant curator of education, at jtyson @tampabayhistorycenter .org. (more)
P.S. This is part of the International Spy Museum's traveling road show, "Spies,
Traitors, Saboteurs: Fear and Freedom in America." One of the show's features are historical artifacts on loan from Murray Associates / Spybusters, LLC; an APL Badge and ID Card (1917) carried by
operatives of the American Protective League (APL) who spied on their
fellow Americans on behalf of the U.S. Justice Department during World
War I. (see them here)
Tuesday, May 8, 2012
Spybusters Tip #834 - Singing the Butt-Dialing Blues
Spybusters Tip #834 - Stop butt-dialing by using your phone's password feature.
Here's what happens when you don't...
Druggie butt-dials police. Busted.
T-Mobile's Butt Dialing commercial.
"Butt" Dialing Becoming A Problem For 911 Dispatchers.
T-Mobile's Butt Dialing commercial.
"Butt" Dialing Becoming A Problem For 911 Dispatchers.
Free Security e-Book of the Week
FREE book: Fundamentals of Media Security (110 pages)
The most interesting chapters...
• Steganography
• Digital Watermarking
• Digital Scrambling
• Digital Surveillance
Enter your email address in #1. (The other three questions are benign.) The ebook will download as a pdf.
Labels:
book,
data,
encryption,
FREE,
spy school,
steganography,
Tips
Monday, May 7, 2012
"The secret of life is honesty and fair dealing. If you can fake that, you've got it made."
 India - Government today dismissed as "outrageous lie" a media report that at the behest of Home Minister P Chidambaram and his ministry telephones of key government functionaries were bugged. An official statement said attention of the Government has been drawn to a news story published in 'Chauthi Duniya' recently. "The story contains outrageous, baseless and defamatory allegations. There is no truth in the story whatsoever. The allegations that telephones were bugged at the instance of the Home Minister or the Ministry of Home Affairs is an outrageous lie," it said. The statement said that the government reserves its right to take appropriate action against the offending newspaper. Government would like to caution other newspapers and media not to reproduce or repeat the aforesaid story, it said. (more) (alternate quote)
India - Government today dismissed as "outrageous lie" a media report that at the behest of Home Minister P Chidambaram and his ministry telephones of key government functionaries were bugged. An official statement said attention of the Government has been drawn to a news story published in 'Chauthi Duniya' recently. "The story contains outrageous, baseless and defamatory allegations. There is no truth in the story whatsoever. The allegations that telephones were bugged at the instance of the Home Minister or the Ministry of Home Affairs is an outrageous lie," it said. The statement said that the government reserves its right to take appropriate action against the offending newspaper. Government would like to caution other newspapers and media not to reproduce or repeat the aforesaid story, it said. (more) (alternate quote)
Town Clerk Charged for Recording Colleagues
MI - Augusta Township Clerk Kathy Giszczak has been charged with eavesdropping for tape recording a conversation between the township supervisor and former deputy treasurer.
She turned herself in for the warrant on these charges by coming to the walk-in arraignment...Giszczak is free on a personal recognizance bond.
She has been charged with one count each of eavesdropping and using or disclosing information obtained through eavesdropping. Both counts each carry a maximum penalty of two years in prison and a $2,000 fine. (more)
She turned herself in for the warrant on these charges by coming to the walk-in arraignment...Giszczak is free on a personal recognizance bond.
She has been charged with one count each of eavesdropping and using or disclosing information obtained through eavesdropping. Both counts each carry a maximum penalty of two years in prison and a $2,000 fine. (more)
Ra-Parents Forcing Kids to Live Undercover
Kids are desperate to flee from their parents’ spying, reports the Wall Street Journal. In a piece about “Tweens’ Secret Lives Online,” the Journal tracks the online lengths kids are going to in order to get away from their stalkerish parents.
Digital anthropologist danah boyd told me last year that teens then were fleeing from Facebook to Twitter to escape the prying eyes of adults. WSJ journo Katherine Rosman says that Instagram is now one of the tools kids use to exchange messages in a semi-public way (where the public doesn’t include nosy adults)...
My own parents certainly didn’t have that luxury. I would disappear with my bike (Me too. With no freakin' helmet, of course.) on a Saturday and be completely out of touch, my whereabouts unknown for hours at a time.
Let’s hope that digitally enabled overparenting doesn’t completely crush kids’ freedom of exploration. Let tweens actually have a little bit of a secret life. (more)
Digital anthropologist danah boyd told me last year that teens then were fleeing from Facebook to Twitter to escape the prying eyes of adults. WSJ journo Katherine Rosman says that Instagram is now one of the tools kids use to exchange messages in a semi-public way (where the public doesn’t include nosy adults)...
My own parents certainly didn’t have that luxury. I would disappear with my bike (Me too. With no freakin' helmet, of course.) on a Saturday and be completely out of touch, my whereabouts unknown for hours at a time.
Let’s hope that digitally enabled overparenting doesn’t completely crush kids’ freedom of exploration. Let tweens actually have a little bit of a secret life. (more)
Illegal Watergate Wiretaps Requsted to be Released
A historian of the Richard Nixon presidency wants to review sealed wiretap materials stemming from the 1972 burglary at the Watergate hotel and subsequent criminal prosecutions.
In a pending case in Washington's federal trial court, the U.S. Justice Department on May 3 said "the request for the content of illegally obtained wiretaps poses an unusual legal issue that the department intends to address in its response."
Justice Department lawyer Elizabeth Shapiro asked Chief Judge Royce Lamberth of U.S. District Court for the District of Columbia for two more weeks to respond to the request from Luke Nichter, an assistant professor of history at Texas A&M University. The earlier deadline was May 5.
“These and other sealed materials may be the key to determining why the Watergate break-in occurred, who ordered it, and what the burglars were looking [for],” Nichter, who specializes in American political history, wrote in a letter (PDF) to Lamberth in 2010. Nichter is researching whether exposing a prostitution ring was the real reason for the Watergate burglary. (more)
In a pending case in Washington's federal trial court, the U.S. Justice Department on May 3 said "the request for the content of illegally obtained wiretaps poses an unusual legal issue that the department intends to address in its response."
Justice Department lawyer Elizabeth Shapiro asked Chief Judge Royce Lamberth of U.S. District Court for the District of Columbia for two more weeks to respond to the request from Luke Nichter, an assistant professor of history at Texas A&M University. The earlier deadline was May 5.
“These and other sealed materials may be the key to determining why the Watergate break-in occurred, who ordered it, and what the burglars were looking [for],” Nichter, who specializes in American political history, wrote in a letter (PDF) to Lamberth in 2010. Nichter is researching whether exposing a prostitution ring was the real reason for the Watergate burglary. (more)
Weakness of U.S. Counterespionage Law Examined
...a recent US court ruling that dealt a blow to the fight against corporate espionage in saying the download of proprietary data does not amount to a criminal offense. (more)
Sunday, May 6, 2012
Would you use spy gadgets in order to get custody of your kids?
On Thursday, "ABC World News with Diane Sawyer" explored the increasing use of surveillance equipment among exes in divorce and custody cases, from hiding a camera in a child's teddy bear to installing tape recorders in the home of an ex. (more)
CALEA Seeks New Orifices
The FBI is asking Internet companies not to oppose a controversial proposal that would require the firms, including Microsoft, Facebook, Yahoo, and Google, to build in backdoors for government surveillance.
In meetings with industry representatives, the White House, and U.S. senators, senior FBI officials argue the dramatic shift in communication from the telephone system to the Internet has made it far more difficult for agents to wiretap Americans suspected of illegal activities, CNET has learned.
The FBI general counsel's office has drafted a proposed law that the bureau claims is the best solution: requiring that social-networking Web sites and providers of VoIP, instant messaging, and Web e-mail alter their code to ensure their products are wiretap-friendly.
The FBI's proposal would amend a 1994 law, called the Communications Assistance for Law Enforcement Act, or CALEA, that currently applies only to telecommunications providers, not Web companies. The Federal Communications Commission extended CALEA in 2004 to apply to broadband networks. (more)
In meetings with industry representatives, the White House, and U.S. senators, senior FBI officials argue the dramatic shift in communication from the telephone system to the Internet has made it far more difficult for agents to wiretap Americans suspected of illegal activities, CNET has learned.
The FBI general counsel's office has drafted a proposed law that the bureau claims is the best solution: requiring that social-networking Web sites and providers of VoIP, instant messaging, and Web e-mail alter their code to ensure their products are wiretap-friendly.
The FBI's proposal would amend a 1994 law, called the Communications Assistance for Law Enforcement Act, or CALEA, that currently applies only to telecommunications providers, not Web companies. The Federal Communications Commission extended CALEA in 2004 to apply to broadband networks. (more)
Friday, May 4, 2012
The Wiretap Garrote
 |
| Courtesy Murray Associates - Click to Enlarge |
The 5-2 Court of Appeals ruling is a victory for law enforcement, said Brian Kleinbord, chief of criminal appeals division for the Maryland Attorney General's Office. "It means that drug dealers can't evade a wiretap by driving their cars across the state line."
But dissenters argued that multi-state wiretaps are the latest example of police using advances in technology to chip away at privacy rights.
Randy E. McDonald, a Washington-based lawyer who argued the case for a man convicted on drug charges, said police have gone too far and he is considering an appeal to the U.S. Supreme Court. (more)
The Gist of the Constable Eavesdropping Case Strikes Back
TX - A former Galveston County deputy constable (James P. Gist), who resigned last year after the district attorney’s office launched a criminal investigation into allegations that he bugged Precinct 7 Constable Pam Matranga’s office, filed a lawsuit Wednesday accusing the constable of sexual harassment...
In a series of allegations listed in the lawsuit, Gist maintains Matranga would lift her shirt over his head and press his head into her cleavage. He also alleges the constable would make crude statements and gestures...
...The lawsuit also states Gist had a recording device on his desk “in an effort to record and collect evidence of defendant Matranga’s sexual harassment.” (more)
In a series of allegations listed in the lawsuit, Gist maintains Matranga would lift her shirt over his head and press his head into her cleavage. He also alleges the constable would make crude statements and gestures...
...The lawsuit also states Gist had a recording device on his desk “in an effort to record and collect evidence of defendant Matranga’s sexual harassment.” (more)
Skipping the PI, they DIY spy!
The spy shop has become a new tool in the arsenal for feuding couples calling it quits in America. From phone tracking and GPS, to hidden cameras and microphones, America’s divorce lawyers have seen technology play a prominent role in their cases.
More than 80 percent of the nation’s top divorce attorneys say they’ve seen an increase in the role electronic data and social networking sites play in divorces, according to the American Academy of Matrimonial Lawyers.
One of the primary reasons is that do-it-yourself snooping has become relatively cheap and easy. Surveillance equipment can cost less than $300. It is simple to mount a microphone in a child’s blue jeans, as one Texas mother did, or hide a camera in a child’s favorite doll. (more)
More than 80 percent of the nation’s top divorce attorneys say they’ve seen an increase in the role electronic data and social networking sites play in divorces, according to the American Academy of Matrimonial Lawyers.
One of the primary reasons is that do-it-yourself snooping has become relatively cheap and easy. Surveillance equipment can cost less than $300. It is simple to mount a microphone in a child’s blue jeans, as one Texas mother did, or hide a camera in a child’s favorite doll. (more)
Labels:
amateur,
eavesdropping,
espionage,
FutureWatch,
GSM,
Hack,
mores,
product,
spycam,
spyware,
surveillance,
tracking,
wiretapping
Watch Over Me Requests Up 10%
US - In a letter to the Senate, the Justice Department reports it made 1,745 requests to the Foreign Intelligence Surveillance Court for special authority for wiretaps last year. That’s 10% more than 2010. None of those requests were denied, although judges did require changes to 30 requests.
The FBI also issued 16,511 national security letters seeking information like financial and phone records on 7,200 people. (more) (sing-a-long)
The FBI also issued 16,511 national security letters seeking information like financial and phone records on 7,200 people. (more) (sing-a-long)
Another Surveillance Concern - SMS Intercept Via CCTV
Australia - Surveillance cameras used during last year's Rugby World Cup could zoom in on individual spectators and camera operators could read their text messages, a privacy forum has heard... Privacy Commissioner Marie Shroff says reading someone's text messages
in public could cause concern, but the legitimacy of the action could
depend on what it was used for. (more)
Sunday, April 29, 2012
The Great Seal Bug Story (updated)
 Our compendium of first and second-hand accounts about The Great Seal Bug continues to grow. The latest contribution has just been posted, along with this rare schematic of the bug from Scientific American, and a video newsreel of Henry Cabot Lodge, Jr. showing off the device at the United Nations in 1960.
Our compendium of first and second-hand accounts about The Great Seal Bug continues to grow. The latest contribution has just been posted, along with this rare schematic of the bug from Scientific American, and a video newsreel of Henry Cabot Lodge, Jr. showing off the device at the United Nations in 1960.
Our latest voice of history begins... "I am a former Foreign Service Officer.
I have a certain amount of first hand, and a larger amount of 2nd hand knowledge about the thing, having worked for a couple of years in the early 1960s in the organization that was responsible for dealing with it and all similar problems - the division of technical services of the office of security of the department of state: abbreviated as O:SY/T.
I knew the tech who actually discovered the thing (slightly), and heard from him in detail exactly how he found it." (more)
I have a certain amount of first hand, and a larger amount of 2nd hand knowledge about the thing, having worked for a couple of years in the early 1960s in the organization that was responsible for dealing with it and all similar problems - the division of technical services of the office of security of the department of state: abbreviated as O:SY/T.
I knew the tech who actually discovered the thing (slightly), and heard from him in detail exactly how he found it." (more)
Board of Directors' Communication Portals
by Jason Clark, CSO, Websense
Imagine that criminals broke into headquarters and bugged your executive offices for insider information—and then made millions trading on that information. That's what can happen if you jump into a Board Communication Systems too quickly. It has already happened: They silently monitor your Board of Directors communications until they hear insider information that they can use to strike it rich on the stock market.
Imagine that criminals broke into headquarters and bugged your executive offices for insider information—and then made millions trading on that information. That's what can happen if you jump into a Board Communication Systems too quickly. It has already happened: They silently monitor your Board of Directors communications until they hear insider information that they can use to strike it rich on the stock market.
 A Board Communication System, often called a Board Portal, is supposed to be a secure cloud system that your CEO, CFO and board of directors use to communicate with one another to make sure any highly sensitive information about the company is protected—from insiders, the IT department, and bad guys. Information that is shared between board members can range from company strategy, to M&A plans, to non-public financial performance details. Imagine the havoc that could ensue if anyone was able to access sensitive knowledge and then use it to their advantage.
A Board Communication System, often called a Board Portal, is supposed to be a secure cloud system that your CEO, CFO and board of directors use to communicate with one another to make sure any highly sensitive information about the company is protected—from insiders, the IT department, and bad guys. Information that is shared between board members can range from company strategy, to M&A plans, to non-public financial performance details. Imagine the havoc that could ensue if anyone was able to access sensitive knowledge and then use it to their advantage.
Why BCSs Need Proper Security Measures
...If a Board Portal is breached, this could mean every one of your shareholders is a potential plaintiff (arguing that their investment has been placed at increased risk of harm due to insider trading or other stock price manipulation)... And this doesn't just affect public companies. Private companies that do business with public companies may need to start disclosing breaches to keep corporate customers as clients. (more)
...If a Board Portal is breached, this could mean every one of your shareholders is a potential plaintiff (arguing that their investment has been placed at increased risk of harm due to insider trading or other stock price manipulation)... And this doesn't just affect public companies. Private companies that do business with public companies may need to start disclosing breaches to keep corporate customers as clients. (more)
Labels:
business,
eavesdropping,
employee,
espionage,
Hack,
law,
lawsuit,
leaks,
privacy,
trade secret,
wiretapping
Saturday, April 28, 2012
SpyCam Story #659 - This Week in SpyCam News
SpyCam stories have become commonplace and the techniques used, repetitive. We
continue to keep lose track of the subject for statistical purposes,
but won't bore you with too many details. Only links to the stories will be
supplied unless there is something useful to be learned.
AZ - School principal and assistant caught passionately kissing via student cell phone.
Australia - Father jailed for hidden camera in the bathroom where his daughters showered.
CA - Maintenance man at Sears arrested for allegedly filming women in changing rooms.
Internet - Spycam Magazine - A new magazine focusing on hidden and spycam products.
AZ - School principal and assistant caught passionately kissing via student cell phone.
Australia - Father jailed for hidden camera in the bathroom where his daughters showered.
CA - Maintenance man at Sears arrested for allegedly filming women in changing rooms.
Internet - Spycam Magazine - A new magazine focusing on hidden and spycam products.
FL - Teacher accused of using a pen camera to video girls changing for gym.
UK - Man rigged up a spy camera to secretly watch a teenage girl in the bath.
IN - Notre Dame pen SpyCam Man escapes jail time.
UK - Man convicted of using spycam pen in toilet.
WA - Voyeurism evidence against father-in-law of missing mother Susan Powell admitted.
CA - York University - At least six incidents of voyeurism this year on campus.
ID - Former high school teacher made plea deal he secretly videotaped students
FL - Man accused of cellphone video of women in Target, Walmart and Publix.
IN - Mom files half-million dollar lawsuit against a former high school janitor accused of secretly filming her son and 41 other boys in a school locker room
UK - Web designer who spied on three young women given a community order.
IN - High school basketball player charged. Cell phone video in the locker room.
MS - Complainant found videos of herself fully naked of her taking a bath on computer.
TN - A 33-year-old Baptist youth evangelist investigated in three states for video voyeurism.
UK - Man rigged up a spy camera to secretly watch a teenage girl in the bath.
IN - Notre Dame pen SpyCam Man escapes jail time.
UK - Man convicted of using spycam pen in toilet.
WA - Voyeurism evidence against father-in-law of missing mother Susan Powell admitted.
CA - York University - At least six incidents of voyeurism this year on campus.
ID - Former high school teacher made plea deal he secretly videotaped students
FL - Man accused of cellphone video of women in Target, Walmart and Publix.
IN - Mom files half-million dollar lawsuit against a former high school janitor accused of secretly filming her son and 41 other boys in a school locker room
UK - Web designer who spied on three young women given a community order.
IN - High school basketball player charged. Cell phone video in the locker room.
MS - Complainant found videos of herself fully naked of her taking a bath on computer.
TN - A 33-year-old Baptist youth evangelist investigated in three states for video voyeurism.
Friday, April 27, 2012
CISPA: Big Brother's Best Friend
The Cyber Intelligence Sharing and Protection Act (CISPA) passed the House yesterday, amended but barely improved. (more)
The government would be able to search information it collects under
CISPA for the purposes of investigating American citizens with complete
immunity from all privacy protections as long as they can claim someone
committed a "cybersecurity crime". Basically it says the 4th Amendment
does not apply online, at all. (more)
CISPA
would "waive every single privacy law ever enacted in the name of
cybersecurity," Rep. Jared Polis, a Colorado Democrat and onetime Web
entrepreneur, said during the debate. "Allowing the military and NSA to
spy on Americans on American soil goes against every principle this
country was founded on." (more)
Sports Quote of the Week
"In my 28 or 29 years in the NFL, I have never listened to an opposing team's communication," ... "I have never asked for the capability to listen to an opposing team's communications. I have never inquired as to the possibility of listening in on an opposing team's communications. And I have never been aware of any capability to listen in on an opposing team's communications at the Superdome or at any NFL stadium." New Orleans Saints, General Manager, Mickey Loomis responding to an ESPN report that accuses him of wiretapping the opposing coaches' booth in the Superdome during the 2002-04 seasons. (more)
"I thought that was an excellent opportunity to share resources to
see if federal or state wiretapping laws were in fact broken," Edmonson
said by phone from Baton Rouge. (more)
A joint Louisiana state police and FBI task force is investigating
allegations that the New Orleans Saints set up general manager Mickey
Loomis' booth in the Superdome so he could listen in on opposing
coaches.
State police Col. Mike Edmonson confirmed the joint effort today
after discussing the matter with Dave Welker, special agent in charge at
the FBI's New Orleans field office.
Autistic Boy Wears Wire to Get Help
Stuart Chaifetz is mad. He's so mad, he took his story to YouTube.
Confused as to why his "sweet and gentle" autistic son Akian, 10, was suddenly kicking school employees and throwing chairs, Chaifetz decided to wire the boy. He stuck a digital recorder in his son's pocket and was able to tape 6.5 hours of class time.
What he heard was shocking. The teacher and aide were yelling at Akian and calling him names.
When the district's response wasn't enough, MSNBC reports Stuart Chaifetz posted the following video on the web:
The above audio includes the teachers talking about having a hangover, calling Akian a bastard and telling him to shut up. At one point, the aide angrily tells the autistic boy, "Go ahead and scream, because guess what? You are going to get nothing until your mouth is shut."
This sounds bad, but it gets worse. (more)
Confused as to why his "sweet and gentle" autistic son Akian, 10, was suddenly kicking school employees and throwing chairs, Chaifetz decided to wire the boy. He stuck a digital recorder in his son's pocket and was able to tape 6.5 hours of class time.
What he heard was shocking. The teacher and aide were yelling at Akian and calling him names.
When the district's response wasn't enough, MSNBC reports Stuart Chaifetz posted the following video on the web:
The above audio includes the teachers talking about having a hangover, calling Akian a bastard and telling him to shut up. At one point, the aide angrily tells the autistic boy, "Go ahead and scream, because guess what? You are going to get nothing until your mouth is shut."
This sounds bad, but it gets worse. (more)
Show of hands. Feeling sorry for Rupert yet? Hands? Anyone???
UK - Rupert Murdoch used his testimony before a U.K. inquiry on Thursday to portray himself as the victim, not perpetrator, of a cover-up over phone hacking -- a twist that could certainly anger those suing his company for invading their privacy to sell newspapers.
The 81-year-old media magnate apologized. He said he had failed. He noted that the corporate cleanup of the British phone hacking scandal had cost his New York-based News Corp. hundreds of millions of dollars and transformed its culture.
"I failed, and I'm sorry about it," Murdoch said, adding later: "We are now a new company altogether." (more)
The 81-year-old media magnate apologized. He said he had failed. He noted that the corporate cleanup of the British phone hacking scandal had cost his New York-based News Corp. hundreds of millions of dollars and transformed its culture.
"I failed, and I'm sorry about it," Murdoch said, adding later: "We are now a new company altogether." (more)
Hiding all Spies in a "Central" Intelligence Agency was Just Too Obvious to Work
The Pentagon confirmed it would be establishing a new intelligence agency, the Defense Clandestine Service, meant to work with the CIA, that would establish spy networks to monitor long-term threats to U.S. national security interests, pointing to places like Iran and North Korea. Defense Secretary Leon Panetta approved the program Friday. The DCS would bring the federal government’s intelligence agency total to 17. (more)
Just for the record...
The 16 federal intelligence agencies are: the CIA, the FBI, and, in the Department of Defense, the Defense Intelligence Agency, the National Security Agency, the National Geospatial-Intelligence Agency, the National Reconnaissance Office, the U.S. Army’s Intelligence and Security Command, the Office of Naval Intelligence, the Marine Corps Intelligence Agency, and the Air Force Intelligence, Surveillance and Reconnaissance Agency, the Department of State's Bureau of Intelligence and Research, the Department of Homeland Security's Office of Intelligence and Analysis the Coast Guard Intelligence, the Drug Enforcement Agdministration's Office of National Security Intelligence, the Treasury Department's Office of Terrorism and Financial Intelligence, and the Energy Department's Office of Intelligence and Counterintelligence
The 16 federal intelligence agencies are: the CIA, the FBI, and, in the Department of Defense, the Defense Intelligence Agency, the National Security Agency, the National Geospatial-Intelligence Agency, the National Reconnaissance Office, the U.S. Army’s Intelligence and Security Command, the Office of Naval Intelligence, the Marine Corps Intelligence Agency, and the Air Force Intelligence, Surveillance and Reconnaissance Agency, the Department of State's Bureau of Intelligence and Research, the Department of Homeland Security's Office of Intelligence and Analysis the Coast Guard Intelligence, the Drug Enforcement Agdministration's Office of National Security Intelligence, the Treasury Department's Office of Terrorism and Financial Intelligence, and the Energy Department's Office of Intelligence and Counterintelligence
"Chief, I've cracked the case. Would you believe..."
UK - A yoga expert says a British spy found dead in a sports bag could have zipped himself in, though a colleague had failed in more than 100 attempts to do it.
Gareth Williams worked for Britain's secret eavesdropping service GCHQ but was attached to the MI6 overseas spy agency when his remains were found in August 2010 inside the bag, which was found in a bathtub at his London apartment. (more)
Gareth Williams worked for Britain's secret eavesdropping service GCHQ but was attached to the MI6 overseas spy agency when his remains were found in August 2010 inside the bag, which was found in a bathtub at his London apartment. (more)
Labels:
employee,
espionage,
government,
humor,
weird,
X-Ray Vision
China - When Hu Jintao, China’s top leader, picked up the telephone last August to talk to a senior anticorruption official visiting Chongqing, special devices detected that he was being wiretapped — by local officials in that southwestern metropolis.
The discovery of that and other wiretapping led to an official investigation that helped topple Chongqing’s charismatic leader, Bo Xilai, in a political cataclysm that has yet to reach a conclusion.
Until now, the downfall of Mr. Bo has been cast largely as a tale of a populist who pursued his own agenda too aggressively for some top leaders in Beijing and was brought down by accusations that his wife had arranged the murder of Neil Heywood, a British consultant, after a business dispute. But the hidden wiretapping, previously alluded to only in internal Communist Party accounts of the scandal, appears to have provided another compelling reason for party leaders to turn on Mr. Bo.
The story of how China’s president was monitored also shows the level of mistrust among leaders in the one-party state. To maintain control over society, leaders have embraced enhanced surveillance technology. But some have turned it on one another — repeating patterns of intrigue that go back to the beginnings of Communist rule. (more)
The discovery of that and other wiretapping led to an official investigation that helped topple Chongqing’s charismatic leader, Bo Xilai, in a political cataclysm that has yet to reach a conclusion.
Until now, the downfall of Mr. Bo has been cast largely as a tale of a populist who pursued his own agenda too aggressively for some top leaders in Beijing and was brought down by accusations that his wife had arranged the murder of Neil Heywood, a British consultant, after a business dispute. But the hidden wiretapping, previously alluded to only in internal Communist Party accounts of the scandal, appears to have provided another compelling reason for party leaders to turn on Mr. Bo.
The story of how China’s president was monitored also shows the level of mistrust among leaders in the one-party state. To maintain control over society, leaders have embraced enhanced surveillance technology. But some have turned it on one another — repeating patterns of intrigue that go back to the beginnings of Communist rule. (more)
Wednesday, April 18, 2012
Camera Trap Snares Man Allegedly Leaving Bizarre Trinkets for Neighbor
IA - A West Des Moines man who for five years has allegedly been leaving raw meat, dolls and other trinkets on a neighbor’s property has been caught on film and now faces harassment charges, according to police.
The victim, a 45-year-old woman, first reported to police in 2007 that someone was depositing odd items — a plastic bag containing raw meat, a Christmas ornament and small dolls, for example — on her property... Last fall, police installed a trail camera, commonly used to track deer and other wildlife, in hopes of catching the suspect in the act.
The victim, a 45-year-old woman, first reported to police in 2007 that someone was depositing odd items — a plastic bag containing raw meat, a Christmas ornament and small dolls, for example — on her property... Last fall, police installed a trail camera, commonly used to track deer and other wildlife, in hopes of catching the suspect in the act.
 |
| Police Navidad |
Last week, the woman reported to police she had watched via the camera as the suspect left items on a fire hydrant, including food, Vaseline petroleum jelly, paper clips, a tape measure, a plastic container full of what appears to be motor oil and two caulking tubes...
The investigation is continuing. (more)
Tuesday, April 17, 2012
PI's Spy Plane Vanishes on Easter. Divine Intervention?
 Swaziland - A spy plane worth E20 000, belonging to Private Investigator Hunter Shongwe has gone missing.
Swaziland - A spy plane worth E20 000, belonging to Private Investigator Hunter Shongwe has gone missing. Shongwe says the unmanned craft which had only three days disappeared while on a mission around Lobamba on Thursday afternoon.
The gadget operates as a spy camera to take pictures of people and places without raising suspicion.
By remote control, he flew the small aircraft in the direction of Somhlolo National Stadium where members of the League of Churches were arriving for the Easter services.
The small plane was on a mission to record everything that was happening at the stadium and surrounding areas during the night.
His mission of spying on the Christians failed when the gadget got lost. (more)
How much information about yourself are you putting online?
As a business owner, you are doubly responsible in safekeeping the information you put online. But before you can protect you business data, you need to learn to protect your personal data first.
Read the Trend Micro Digital Lifestyle e-guide, Be Privy to Online Privacy, and be a better informed digital citizen.
You’ll learn:
 How online advertisers are tracking your browsing behavior,
How online advertisers are tracking your browsing behavior,
 The consequences of what you post in your social media.
The consequences of what you post in your social media.
 How mobile apps can access the information stored in your mobile device, if you allow them.
How mobile apps can access the information stored in your mobile device, if you allow them.
Irony Alert: You'll have to give up some information about yourself to get it. ~Kevin
Read the Trend Micro Digital Lifestyle e-guide, Be Privy to Online Privacy, and be a better informed digital citizen.
You’ll learn:
Irony Alert: You'll have to give up some information about yourself to get it. ~Kevin
Cyber Intelligence Sharing and Protection Act of 2011 (CISPA) Protest
 Civil liberties organizations are launching a week of Internet-wide protests against the Cyber Intelligence Sharing and Protection Act of 2011 (CISPA), the controversial cybersecurity legislation that would negate existing privacy laws and allow companies to share user data with the government without a court order.
Civil liberties organizations are launching a week of Internet-wide protests against the Cyber Intelligence Sharing and Protection Act of 2011 (CISPA), the controversial cybersecurity legislation that would negate existing privacy laws and allow companies to share user data with the government without a court order.The coalition is urging the public to take part in a Twitter protest directed at their lawmakers. The Electronic Frontier Foundation (EFF) has created an interactive tool for people to find their representatives and their Twitter handles, and to share how CISPA's privacy invasions would affect their day-to-day lives. (more)
Labels:
cautionary tale,
computer,
data,
government,
Internet,
law,
mores,
police,
political,
tracking
Monday, April 16, 2012
Indonesia Now a Business Espionage Target
As Indonesia’s economy soars at an impressive rate and with the defense budget expanding aggressively, several state companies and government agencies have increasingly become targets of espionage.
National Intelligence Agency (BIN) head Lt. Gen. Marciano Norman said recently there were indications that espionage activities have been increasing lately.
“We’re worried with such activities. More resources are now allocated to prevent them. It’s part of my priorities,” Marciano said, refusing to elaborate further. He said there were two Asian countries — one of which is a neighboring nation — that have become more aggressive in spying into Indonesia’s economy. (more)
National Intelligence Agency (BIN) head Lt. Gen. Marciano Norman said recently there were indications that espionage activities have been increasing lately.
“We’re worried with such activities. More resources are now allocated to prevent them. It’s part of my priorities,” Marciano said, refusing to elaborate further. He said there were two Asian countries — one of which is a neighboring nation — that have become more aggressive in spying into Indonesia’s economy. (more)
Belgium - Reuters reported that ArcelorMittal workers involved in a bitter dispute over the closure of furnaces in Belgium pointed the finger at the company after discovering that a union meeting was recorded with a camera pen and after being sent secretly filmed footage of workers.
Belgium's heavy industry has been in decline for years and Liege has been the scene of acrimonious protests by workers after ArcelorMittal, the world's biggest steelmaker, said it planned to close operations there. (more)
Belgium's heavy industry has been in decline for years and Liege has been the scene of acrimonious protests by workers after ArcelorMittal, the world's biggest steelmaker, said it planned to close operations there. (more)
A Memory Stick that Self-Destructs
 Technology has now created the ultimate USB stick - used by the secret service. If you lose it you can track its location and if it falls into the wrong hands you can even remotely scramble its content. (video) (product)
Technology has now created the ultimate USB stick - used by the secret service. If you lose it you can track its location and if it falls into the wrong hands you can even remotely scramble its content. (video) (product)
Sunday, April 15, 2012
What are spies really like?
 via the BBC...
via the BBC...Most people have watched a spy film, but few have ever met someone from the intelligence community. So how close are real spies to the Bournes and the Bonds? Peter Taylor looks at the world of the modern day secret agent... (more)
What does a spy look like? There is no exact answer, but a composite picture was developed by the Business Espionage Controls and Countermeasures Association... (more)
The Cybercrime Wave That Wasn’t
via The New York Times...
In less than 15 years, cybercrime has moved from obscurity to the spotlight of consumer, corporate and national security concerns. Popular accounts suggest that cybercrime is large, rapidly growing, profitable and highly evolved; annual loss estimates range from billions to nearly $1 trillion...
Yet in terms of economics, there’s something very wrong with this picture...
Yet in terms of economics, there’s something very wrong with this picture...
...in numeric surveys, errors are almost always upward: since the amounts
of estimated losses must be positive, there’s no limit on the upside,
but zero is a hard limit on the downside. As a consequence, respondent
errors — or outright lies — cannot be canceled out. Even worse, errors
get amplified when researchers scale between the survey group and the
overall population...
The cybercrime surveys we have examined exhibit exactly this pattern of
enormous, unverified outliers dominating the data. In some, 90 percent
of the estimate appears to come from the answers of one or two
individuals. In a 2006 survey of identity theft by the Federal Trade
Commission, two respondents gave answers that would have added $37
billion to the estimate, dwarfing that of all other respondents
combined...
Among dozens of surveys, from security vendors, industry analysts and
government agencies, we have not found one that appears free of this
upward bias. As a result, we have very little idea of the size of
cybercrime losses. (more)
Thus proving once again, fear-mongering is profitable.
• Keep a cool head.
• View the risk holistically.
Your valuable information was/is available elsewhere, before it is ever entered into a computer.
• Balance your security budgets appropriately.
Information risk management isn't solely an IT issue... no matter what the IT security vendors and other vested interests tell you. ~Kevin
Thursday, April 12, 2012
Teen Taps Top Cops
A teenager eavesdropped on highly-sensitive police counter-terror conversations after bypassing technology from the 1980s, hackers have claimed.
The leader of an anarchist group known as Team Poison said it was "easy" to drop "a 24-hour phone bomb" on elite security officers...
The leader of an anarchist group known as Team Poison said it was "easy" to drop "a 24-hour phone bomb" on elite security officers...
 |
| Is that, at, at, at you Bryce? |
In another recording officers appear to be discussing counter-terror operations while Team Poison listens in. The group - which uses the Twitter name @_TeaMp0isoN - claimed the calls were made to MI6 - but it is understood they were in fact picked up by the Metropolitan Police's counter-terrorism command.
Trick, reportedly a 17-year-old who launched Team Poison in 2010, emailed the Press Association, saying the group bypassed outdated technology to compromise a server from Malaysia to record conversations. He wrote: "Yes, it was easy :)"
Trick said: "The phone denial of service was done via a custom script for Asterisk which was installed on an overseas server. The conversation was tapped into via a private phreaking method, their phone system is old and we found a way to get in via basic but private phreaking technique." (more)
Trick, reportedly a 17-year-old who launched Team Poison in 2010, emailed the Press Association, saying the group bypassed outdated technology to compromise a server from Malaysia to record conversations. He wrote: "Yes, it was easy :)"
Trick said: "The phone denial of service was done via a custom script for Asterisk which was installed on an overseas server. The conversation was tapped into via a private phreaking method, their phone system is old and we found a way to get in via basic but private phreaking technique." (more)
Privacy Journal 2012 Privacy Law Compilation Updated
With
a surge in the final days of the 2011 session, the California legislature
enacted several new privacy protections that clearly keep the state at the top
of the privacy-protecting states in the U.S., according to a new survey of the
states by Privacy Journal.
The
monthly newsletter reports on new privacy laws enacted by states and Congress
each year. The information is available in its Compilation of State and FederalPrivacy Laws, updated yearly. (more)
Two Cell Phone Eavesdropping Attacks Reported
• Security firm Cryptography Research showed how it's possible to eavesdrop on any smartphone or tablet PC as it is being used to make a purchase, conduct online banking or access a company's virtual private network.
• Researchers at security firm McAfee, a division of chipmaker Intel, highlighted several ways to remotely hack into Apple iOS, the operating system for iPads and iPhones.
McAfee's research team remotely activated microphones on a variety of test devices and recorded conversations taking place nearby. They also showed that it's possible to steal secret keys and passwords, and pilfer sensitive data, including call histories, e-mail and text messages.
"This can be done with absolutely no indication to the device user," says Ryan Permeh, McAfee's principal security architect. (more)

• Researchers at security firm McAfee, a division of chipmaker Intel, highlighted several ways to remotely hack into Apple iOS, the operating system for iPads and iPhones.
McAfee's research team remotely activated microphones on a variety of test devices and recorded conversations taking place nearby. They also showed that it's possible to steal secret keys and passwords, and pilfer sensitive data, including call histories, e-mail and text messages.
"This can be done with absolutely no indication to the device user," says Ryan Permeh, McAfee's principal security architect. (more)

Monday, April 9, 2012
IKEA Apologizes to Workers for Spying
The management of IKEA in France, where workers have sued the company for allegedly spying on employees, admitted that activities contravening its ethical standards had taken place and pledged to put a stop to them. (more)
Subscribe to:
Comments (Atom)