Estonia - A wiretapping device has been found in a cultural center for Russian-speaking Estonian citizens in Tallinn. The NGO is run by the mother of the city’s vice mayor, who is suspected of lobbying for Russian interests in the Baltic country.
The wiretap, discovered Tuesday, is the second such device found in the Lira cultural and sports center, after a thorough inspection carried out by center’s security.
The first eavesdropping device, which was clumsily wired into the facility’s alarm system, was found on May 15. Inspectors believe the bugs were installed between September and December 2011. The police opened an investigation but so far no official statements have been made on the issue. (more)
Thursday, May 24, 2012
Wednesday, May 23, 2012
No Sir'ee. No Siri here. Seri-ously!
If you work for IBM, you can bring your iPhone to work, but forget about using the phone’s voice-activated digital assistant. Siri isn’t welcome on Big Blue’s networks.
 The reason? Siri ships everything you say to her to a big data center in Maiden, North Carolina. And the story of what really happens to all of your Siri-launched searches, e-mail messages and inappropriate jokes is a bit of a black box.
The reason? Siri ships everything you say to her to a big data center in Maiden, North Carolina. And the story of what really happens to all of your Siri-launched searches, e-mail messages and inappropriate jokes is a bit of a black box.
IBM CIO Jeanette Horan told MIT’s Technology Review this week that her company has banned Siri outright because, according to the magazine, “The company worries that the spoken queries might be stored somewhere.”
It turns out that Horan is right to worry. In fact, Apple’s iPhone Software License Agreement spells this out: “When you use Siri or Dictation, the things you say will be recorded and sent to Apple in order to convert what you say into text,” Apple says. Siri collects a bunch of other information — names of people from your address book and other unspecified user data, all to help Siri do a better job.
How long does Apple store all of this stuff, and who gets a look at it? Well, the company doesn’t actually say. (ask Siri!) (more)
 The reason? Siri ships everything you say to her to a big data center in Maiden, North Carolina. And the story of what really happens to all of your Siri-launched searches, e-mail messages and inappropriate jokes is a bit of a black box.
The reason? Siri ships everything you say to her to a big data center in Maiden, North Carolina. And the story of what really happens to all of your Siri-launched searches, e-mail messages and inappropriate jokes is a bit of a black box. IBM CIO Jeanette Horan told MIT’s Technology Review this week that her company has banned Siri outright because, according to the magazine, “The company worries that the spoken queries might be stored somewhere.”
It turns out that Horan is right to worry. In fact, Apple’s iPhone Software License Agreement spells this out: “When you use Siri or Dictation, the things you say will be recorded and sent to Apple in order to convert what you say into text,” Apple says. Siri collects a bunch of other information — names of people from your address book and other unspecified user data, all to help Siri do a better job.
How long does Apple store all of this stuff, and who gets a look at it? Well, the company doesn’t actually say. (ask Siri!) (more)
Cell Phone Door Key App?!?!
via Gizmodo.com...
"The UniKey app transmits a Bluetooth signal from the user’s iPhone, Android or BlackBerry smartphone, which is picked up by a paired UniKey deadbolt lock as it is approached by the user.
All the user has to do when they subsequently reach the door is simply touch the outer surface of the lock, at which point the bolt will electronically withdraw. A touch of the lock can likewise be used to engage it when the user is leaving.
While not having to dig out a key and stick it in the lock may be somewhat convenient, what’s more intriguing is the system’s ability to send, revoke, and limit access to virtual “copies” of the key." (more)
While not having to dig out a key and stick it in the lock may be somewhat convenient, what’s more intriguing is the system’s ability to send, revoke, and limit access to virtual “copies” of the key." (more)
Cell Phone Tracking Trick Explained
Stingrays locate a mobile phone even when it's not being used to make a call.
The Federal Bureau of Investigation considers the devices to be so critical that it has a policy of deleting the data gathered in their use, mainly to keep suspects in the dark about their capabilities, an FBI official told The Wall Street Journal in response to inquiries. (more)
The Federal Bureau of Investigation considers the devices to be so critical that it has a policy of deleting the data gathered in their use, mainly to keep suspects in the dark about their capabilities, an FBI official told The Wall Street Journal in response to inquiries. (more)
Out of Bond - Spy Movie Web Site Just Launched
via spymaniac.com...
"Spymaniac.com, the ultimate online guide to all your favorite spy flicks.
What’s fact, what’s fiction? History or fantasy? Which are the best spy films and why? The outrageous duds? Did the James Bond movies have any impact on real life? And would Angelina Jolie’s Evelyn Salt have learned all those stunts at the Farm?
Get answers to these and other questions here. Share your faves and reviews on Spymaniac.com, and discover great films you may never have heard about. Spymaniac is your community for exploring and sharing spy films, which are rated from zero daggers (worst) to five daggers (best)." (more)
"Spymaniac.com, the ultimate online guide to all your favorite spy flicks.
What’s fact, what’s fiction? History or fantasy? Which are the best spy films and why? The outrageous duds? Did the James Bond movies have any impact on real life? And would Angelina Jolie’s Evelyn Salt have learned all those stunts at the Farm?
Get answers to these and other questions here. Share your faves and reviews on Spymaniac.com, and discover great films you may never have heard about. Spymaniac is your community for exploring and sharing spy films, which are rated from zero daggers (worst) to five daggers (best)." (more)
Turkey Bird Spy Found Dead
Turkey - In the latest bizarre espionage claim leveled at Israeli intelligence services, Turkish authorities claimed that a dead bird found by a Turkish farmer in a field may have been conducting covert surveillance for Israel.
The dead Merops apiaster bird -- commonly known as the European Bee-Eater -- was discovered by the Turkish farmer wearing a band on its leg with the word "Israel" written on it.
The bird also had "unusually large nostrils," leading to speculation that it was implanted with a surveillance device and sent to Turkey on an aerial espionage mission. (more)
 |
| Merops apiaster |
The bird also had "unusually large nostrils," leading to speculation that it was implanted with a surveillance device and sent to Turkey on an aerial espionage mission. (more)
Labels:
aerial,
drone,
espionage,
government,
Hack,
humor,
nature,
spybot,
spycam,
weird,
X-Ray Vision
Tuesday, May 22, 2012
"How Much Is Your Privacy Worth?"
"How Much Is Your Privacy Worth?" just opened at The Dutch Museum of Communications located in The Hague, Netherlands.
Illustrator and graphic designer Noma Bar designed this and other posters for the museum, which conducted research into the theme of privacy for its latest exhibition.
...the museum conducted an official survey, the results of which are now displayed in the museum and on its website. They also conducted a series of street interviews. Bar used some of the findings to create the posters.
The following is a little cryptic due to Google's translation abilities, but you'll get the idea...
"The Museum for Communication pays special attention to the issue of privacy. Ruigrok research was commissioned by the museum research into the value of privacy among the Dutch public. Following this study, street interviews. The street interviews are presented in the museum, including exhibitions in the WE Blog, the Empire of back and forth Letter Secrets is the theme.
Labels:
art,
business,
data,
FutureWatch,
miscellaneous,
mores,
privacy,
survey
Private Investigator Blogs Worth Checking Out
I came across a blog by Sheer Investigations. It is worth checking out. Don't know how they scooped me with this photo. Well done! Many more interesting posts there, too.
Other well respected investigations blogs. (As compiled by PInow.com; and a great blog in and of itself.) and many more. Explore!
Monday, May 21, 2012
Security Tip: On Keeping Your Perscriptions Private
via a Security Scrapbook Blue Blaze Irregular... (Thanks!)
"To get the label off the bottle just fill the empty pill bottle with boiling hot water. The glue will soften and you can then pull it off the bottle easy. You can then apply the label to a piece of scrap paper and shred it.
What one does with the now empty and very clean pill bottle is up to the person."
Breaking Spy Cam News - Rutgers Student Sentenced
11:27 AM - Dharun Ravi could face 10 years in prison and be deported to his native India when he is sentenced Monday for spying on and intimidating his gay Rutgers University roommate, who then killed himself by jumping off New York's George Washington Bridge.
12:49 PM - Ex-Rutgers student Dharun Ravi gets 30 days in jail for using webcam to spy on roommate who later killed himself. (more)
12:49 PM - Ex-Rutgers student Dharun Ravi gets 30 days in jail for using webcam to spy on roommate who later killed himself. (more)
Android Malware ...using real apps as disguise 'wrappers'
The ominous trend is that quarter-on-quarter malware is not only getting more common but more sophisticated.
An important technique is the use app ‘wrappers’ to allay the suspicion of users that rogue software might have been installed. These work by bundling legitimate apps with malware in order to gain permissions without the user understanding what it is being granted for. (more) (sing-a-long)
An important technique is the use app ‘wrappers’ to allay the suspicion of users that rogue software might have been installed. These work by bundling legitimate apps with malware in order to gain permissions without the user understanding what it is being granted for. (more) (sing-a-long)
Trend Spotting - Chief Spies Become Political Leaders
Croatia's main opposition party HDZ elected former spy chief Tomislav Karamarko as its leader on Monday... (more)
George H.W. Bush, ex-CIA; former American President
Heydar Aliyev, Former head of Azerbaijan SSR KGB; former Azerbaijani President
George H.W. Bush, ex-CIA; former American President
Heydar Aliyev, Former head of Azerbaijan SSR KGB; former Azerbaijani President
Vladimir Putin, Lieutenant colonel KGB, FSB director; Russian President (again)
Leonid Tibilov, former KGB chief; President, South Ossetia
Industrial Espionage Charges - A Public Relations Nightmare
John Donovan says, "Shell is notorious for its predatory appetite for the intellectual property of other organizations, its business partners, contractors, etc. Industrial espionage is a way of life at Shell. Shell management has apparently even targeted the US defense establishment," and then he goes on to post: Another alleged case of IP theft hits Royal Dutch Shell
How can you protect your organization against accusations of industrial espionage?
Step 1. Start by writing business ethics into your corporate Credo. This codifies your standards for all the world to see. It is an especially good anchor for employees.
Step 1. Start by writing business ethics into your corporate Credo. This codifies your standards for all the world to see. It is an especially good anchor for employees.
Don't have a Credo?
Don't know where it fits into the picture?
"The Credo ties the company’s Vision to the company’s Mission and Values Statements. The Vision could be seen as the way the entrepreneur sees his company in the future general business environment. The Mission is what he intends to create to secure his place in the Vision. The Values statement indicates what the parameters of operation look like while attempting to achieve these goals. The Credo tells the reader how the company intends to execute these goals. It could be seen as the way the objectives can be reached to realize the Mission inside of the Vision while adhering to certain Values."
Step 2. Post your Credo where it can be see and read by all employees, often. Johnson & Johnson is one company which does this very well.
Step 3. Aggressively investigate all alleged deviations. Make corrections swiftly if the allegations are true.
Step 4. Institute a regular schedule of intellectual property (IP) security surveys, coupled with Technical Surveillance Countermeasures (TSCM) audits.
Don't be covert about it. The benefits are many...
• The impression that IP theft is bad, as opposed to being an unspoken business practice, is reinforced.
• Employees see you caring about their privacy. They appreciate that.
• They see that you value the IP assets which makes your company strong, and assures their continued employment.
• Caring is contagious. If you care, employees will care, and they will assist and support your security initiatives with more enthusiasm. Apple is an excellent example of Step 4.
• You create a safe environment where ideas and strategies can be discussed and developed without fear or compromise.
• And, maybe most important of all, you will thwart IP theft, thus making your company more profitable. Stockholders love that.
Cell Phone SpyWare App is Vulnerable to... being spied upon!
The irony is too significant to ignore: A smartphone app that enables customers to spy on others' phones may itself be vulnerable to attackers looking to spy on them.
 The surveillance app, called "Mobile Spy," is designed to let its customers monitor the information, including text messages, GPS location and call logs, of other phones installed with the app. That private info is then uploaded to the app user's account and can be viewed in any Web browser, either on a computer or phone.
The surveillance app, called "Mobile Spy," is designed to let its customers monitor the information, including text messages, GPS location and call logs, of other phones installed with the app. That private info is then uploaded to the app user's account and can be viewed in any Web browser, either on a computer or phone.
Unfortunately for those doing the watching, Mobile Spy contains several security vulnerabilities that allow an attacker to inject malicious code into the target's phone, via SMS message, and hijack their spy session, according to researchers at Vulnerability Lab, who disclosed the flaws. (more)
 The surveillance app, called "Mobile Spy," is designed to let its customers monitor the information, including text messages, GPS location and call logs, of other phones installed with the app. That private info is then uploaded to the app user's account and can be viewed in any Web browser, either on a computer or phone.
The surveillance app, called "Mobile Spy," is designed to let its customers monitor the information, including text messages, GPS location and call logs, of other phones installed with the app. That private info is then uploaded to the app user's account and can be viewed in any Web browser, either on a computer or phone. Unfortunately for those doing the watching, Mobile Spy contains several security vulnerabilities that allow an attacker to inject malicious code into the target's phone, via SMS message, and hijack their spy session, according to researchers at Vulnerability Lab, who disclosed the flaws. (more)
Sunday, May 20, 2012
UK - A recording device that looks like a small piece of cardboard was planted at the home of a Premiership footballer to record details about his private life, MPs were told yesterday during an inquiry into the murky world of private investigators.
The transmitter was picked up during a security sweep of the player's house after he became suspicious about stories in the media, said Gerry Hall, managing director of security company IPS. He declined to name the footballer, who is still playing in the league.
 |
| RFID tags look similar and are often mistaken for bugs. |
Mr Hall said the small square of cardboard had a transmitter embedded in it that worked at a range of up to 100 yards. "It could easily be dropped into a wastepaper basket and transmit for 30 hours," he told MPs on the Home Affairs Select Committee...
Mr Hall said an investigator could easily persuade a company receptionist to let them in and would need just seconds to plant the device. He said his company had just found one in a chairman's office. (more)
Mr Hall said an investigator could easily persuade a company receptionist to let them in and would need just seconds to plant the device. He said his company had just found one in a chairman's office. (more)
Meet Your New Back Door Friend...
Will Congress require social networks, online voice over IP (VoIP) services, and Webmail providers to build in backdoors that could be used for electronic surveillance purposes by the FBI?
According to one news report, FBI officials have been meeting with Facebook, Google, Microsoft (which owns Skype and Hotmail), and Yahoo, among other companies. The goal apparently isn't to promote the bureau's push for expanded wiretapping capabilities, but rather to ask how that be implemented while causing minimal disruption for the companies with networks that would be directly accessed...
Six Key Points to Consider
1. Bureau Warns About Going Dark. The bureau has already been asking Congress for broader surveillance powers to help it keep up with new technologies....
Six Key Points to Consider
1. Bureau Warns About Going Dark. The bureau has already been asking Congress for broader surveillance powers to help it keep up with new technologies....
2. Proposed CALEA Revisions Would Update 1994 Law. Accordingly, the FBI wants Congress to expand the Communications Assistance for Law Enforcement Act (CALEA)...
3. Questions Remain Over Wiretapping Scope. Just how often does the FBI need to use wiretapping during an investigation? That's not clear. According to an FBI website about CALEA, wiretapping "is used infrequently and then only to combat the most serious crimes and terrorism."...
4. Civil Liberties Groups See Slippery Slope. Civil rights groups have warned that granting law enforcement agencies new surveillance powers could lead to a decrease in the privacy protections that people currently enjoy...
5. Will Technology Companies Back CALEA Expansion?...
6. Backdoors May Facilitate Unauthorized Access. Wiretapping backdoors could also make online services more vulnerable to attackers.... (more)
Labels:
CALEA,
computer,
eavesdropping,
email,
FBI,
FutureWatch,
government,
Internet,
law,
privacy,
surveillance,
wiretapping
Bustin' A Move Could Get One Busted
TX - Galveston police are on the lookout for the “dancing burglar” who was captured on video busting some moves during the break-in of a Duck Tours amphibious vehicle.
The 38-second video released by Galveston police Capt. Jeff Heyse on Wednesday shows a man apparently chatting with someone before he busts the dance moves.
The dancer (later identified as a juvenile) is one of three people sought in connection with the March 27 burglary of a Duck Tours amphibious automobile, which takes sightseers along Galveston streets and the bay. (more)
The 38-second video released by Galveston police Capt. Jeff Heyse on Wednesday shows a man apparently chatting with someone before he busts the dance moves.
The dancer (later identified as a juvenile) is one of three people sought in connection with the March 27 burglary of a Duck Tours amphibious automobile, which takes sightseers along Galveston streets and the bay. (more)
"One can never be too far away, or too thin. Besides, what's in a name?"
NJ - An appeals court has ruled that police in New Jersey can wiretap a suspect in another state without obtaining a warrant from the judge of that state.
Thursday’s ruling also confirms the murder conviction of Edward Ates, a Florida man who was sentenced to life in prison after failing to persuade a jury of the argument that he was too fat to have committed the 2006 murder of his son-in-law.
Ates was convicted in 2009 of fatally shooting his former son-in-law. An investigation by Bergen County prosecutors included wiretapping calls Ates made from Florida to his mother and sister in Louisiana. (more)
Thursday’s ruling also confirms the murder conviction of Edward Ates, a Florida man who was sentenced to life in prison after failing to persuade a jury of the argument that he was too fat to have committed the 2006 murder of his son-in-law.
Ates was convicted in 2009 of fatally shooting his former son-in-law. An investigation by Bergen County prosecutors included wiretapping calls Ates made from Florida to his mother and sister in Louisiana. (more)
Saturday, May 19, 2012
Security Tops Boardroom Agendas
via the Financial Times...
Securing corporate intellectual property assets, customer data and other information in the face of an onslaught of attacks from cyber thieves, spies and “hactivists” is now a top priority for most chief information officers and – increasingly – for the corporate boardroom.
“It is definitely something I think about all the time,” says the chief information officer of a US-based consumer goods multinational that, like many other companies, particularly those in the financial services sector, now has an IT security team led by a chief information security officer (CISO.)...
“Our companies are targeted for insider information and our universities and national laboratories are targeted for their research and development,” Robert Mueller, Federal Bureau of Investigations director told a US congressional panel last year...
Meanwhile companies and other organizations have begun to spend more on identifying and protecting their key data using multiple layers of defense and, perhaps most importantly, monitoring and detection systems that can identify security breaches quickly and efficiently. (one example) (more)
Securing corporate intellectual property assets, customer data and other information in the face of an onslaught of attacks from cyber thieves, spies and “hactivists” is now a top priority for most chief information officers and – increasingly – for the corporate boardroom.
“It is definitely something I think about all the time,” says the chief information officer of a US-based consumer goods multinational that, like many other companies, particularly those in the financial services sector, now has an IT security team led by a chief information security officer (CISO.)...
“Our companies are targeted for insider information and our universities and national laboratories are targeted for their research and development,” Robert Mueller, Federal Bureau of Investigations director told a US congressional panel last year...
Meanwhile companies and other organizations have begun to spend more on identifying and protecting their key data using multiple layers of defense and, perhaps most importantly, monitoring and detection systems that can identify security breaches quickly and efficiently. (one example) (more)
This Time the Janitor is Spied Upon
AK - Educators at Gilson Junior High were shocked and outraged to learn
janitorial supervisors had planted a hidden camera in the ceiling tiles
of the teacher lounge above a computer workplace, ostensibly in hopes of
catching janitors goofing off on the computer rather than working.
Outrage spread when a second camera hidden in a clock was discovered in a
custodial closet at Valdez High School. It was later learned the same
camera had been located in the teacher lounge at the junior high days
before it was found at the high school. (more)
Possible Surveillance Drone Strike? In Colorado?!?!
CO - A mystery object, thought to be a military or law enforcement drone, flying in controlled airspace over Denver almost caused a catastrophic mid air crash with a commercial jet Monday.
The pilot of the Cessna jet radioed air traffic controllers to warn them that “A remote controlled aircraft” had flown past his plane far too close for comfort.
“Something just went by the other way … About 20 to 30 seconds ago. It was like a large remote-controlled aircraft.” the pilot said in the transmission that was captured on the live air traffic audio website liveatc.net (Look for 2012-05-16 15:00:51 in the archive section. Free registration required.) (more)
The pilot of the Cessna jet radioed air traffic controllers to warn them that “A remote controlled aircraft” had flown past his plane far too close for comfort.
“Something just went by the other way … About 20 to 30 seconds ago. It was like a large remote-controlled aircraft.” the pilot said in the transmission that was captured on the live air traffic audio website liveatc.net (Look for 2012-05-16 15:00:51 in the archive section. Free registration required.) (more)
"Spy, the Secret World of Espionage" Now open in NYC
The mysterious cloak and dagger world of international espionage and its real-life heros and villains are exposed in a new exhibition, the first to be sanctioned by U.S. intelligence agencies.
"Spy, the Secret World of Espionage," which opens at the Discovery Times Square on Friday, includes hundreds of artifacts, some from the vaults of the CIA and FBI and the National Reconnaissance Office (NRO).
They range from a World War Two-era collapsible motorbike that could be dropped by parachute and deployed in 10 seconds and a German ENIGMA machine to create secret messages to a camel saddle used by one of the first CIA agents in Afghanistan after the 9/11 attacks to bugging devices, microdots and surveillance equipment.
"This is the first and only time these items will ever travel. It is kind of an unparalleled cooperation and collaboration with the CIA and FBI," said H. Keith Melton, author, intelligence historian and expert on spy technology who contributed items from his own collection. (more)
"Spy, the Secret World of Espionage," which opens at the Discovery Times Square on Friday, includes hundreds of artifacts, some from the vaults of the CIA and FBI and the National Reconnaissance Office (NRO).
They range from a World War Two-era collapsible motorbike that could be dropped by parachute and deployed in 10 seconds and a German ENIGMA machine to create secret messages to a camel saddle used by one of the first CIA agents in Afghanistan after the 9/11 attacks to bugging devices, microdots and surveillance equipment.
"This is the first and only time these items will ever travel. It is kind of an unparalleled cooperation and collaboration with the CIA and FBI," said H. Keith Melton, author, intelligence historian and expert on spy technology who contributed items from his own collection. (more)
Friday, May 18, 2012
Facebook's Trading Day Begins with... a Wiretap Lawsuit
Facebook is being sued for $15 billion for tracking users, even after they have logged out of the social network, and violating federal wiretap laws.
Today’s lawsuit, filed in Federal Court in San Jose, California, combines 21 separate cases across the U.S. in 2011 and early 2012... If the claimants are successful in their case against Facebook, they could prevent Menlo Park from collecting the huge amount of data it collects about its users to serve ads back to them.
Like the previous lawsuits, Facebook is once again being accused of violating the Federal Wiretap Act, which provides statutory damages per user of $100 per day per violation, up to a maximum per user of $10,000. The complaint also asserts claims under the Computer Fraud and Abuse Act, the Stored Communications Act, various California Statutes, and California common law. It’s worth noting that similar cases against Facebook and others filed under the wiretap law have been thrown out because browser cookies are simply not considered wiretaps and plaintiffs have difficulty proving any harm. (more)
Today’s lawsuit, filed in Federal Court in San Jose, California, combines 21 separate cases across the U.S. in 2011 and early 2012... If the claimants are successful in their case against Facebook, they could prevent Menlo Park from collecting the huge amount of data it collects about its users to serve ads back to them.
Like the previous lawsuits, Facebook is once again being accused of violating the Federal Wiretap Act, which provides statutory damages per user of $100 per day per violation, up to a maximum per user of $10,000. The complaint also asserts claims under the Computer Fraud and Abuse Act, the Stored Communications Act, various California Statutes, and California common law. It’s worth noting that similar cases against Facebook and others filed under the wiretap law have been thrown out because browser cookies are simply not considered wiretaps and plaintiffs have difficulty proving any harm. (more)
Android Cell Phone Users Security Alert
Malware targeting Android users has nearly quadrupled since 2011. As you can see in the graph, 10 Android malware families were detected in Q1 2011. This number increased for two quarters in a row, then dipped for one, and then finally settled at 37 in Q1 2012. That means a year-over-year growth of 270 percent.
The data comes from security firm F-Secure. The trend was revealed today in the company’s 47-page Mobile Threat Report Q1 2012 (PDF).
 It makes sense that both the number of malware families and malicious Android APKs is increasing, but it’s still staggering to see that the latter number is now over 3,000, whereas last year it was just above 100.
It makes sense that both the number of malware families and malicious Android APKs is increasing, but it’s still staggering to see that the latter number is now over 3,000, whereas last year it was just above 100.
The increase in malware numbers is indicative of a wider increase in mobile threats, according to F-Secure. Even more worrying, however, is that the Finnish security firm warned many of the apps are targeting Android users’ financial data, noting that 34 of the current malware families are designed to steal money from infected smartphones. (more)
Tip: Do not download, open or install anything unless you absolutely need it and are 100% confident it is coming to you from a trusted source. ~Kevin
The data comes from security firm F-Secure. The trend was revealed today in the company’s 47-page Mobile Threat Report Q1 2012 (PDF).
 It makes sense that both the number of malware families and malicious Android APKs is increasing, but it’s still staggering to see that the latter number is now over 3,000, whereas last year it was just above 100.
It makes sense that both the number of malware families and malicious Android APKs is increasing, but it’s still staggering to see that the latter number is now over 3,000, whereas last year it was just above 100. The increase in malware numbers is indicative of a wider increase in mobile threats, according to F-Secure. Even more worrying, however, is that the Finnish security firm warned many of the apps are targeting Android users’ financial data, noting that 34 of the current malware families are designed to steal money from infected smartphones. (more)
Tip: Do not download, open or install anything unless you absolutely need it and are 100% confident it is coming to you from a trusted source. ~Kevin
Password Evaluation Program Will Surprise You
Passfault evaluates the strength of passwords accurately enough to predict the time to crack. It makes creating passwords and password policies significantly more intuitive and simple.
When setting a password, Passfault examines the password, looking for common patterns. Passfault than measures the strength of the patterns and combinations of patterns. The end result is a more academic and accurate measurement of password strength. (more) (test your password)
You might think a password like 123!@#qweQWE would provide excellent protection. Wrongo. It can be cracked in a day according to Passfault. Why? Because it contains a readily identifiable pattern of keystrokes. Now try something easy to remember like ToBeOrNotToBe. Surprised? Thought so. ~Kevin
Friday, May 11, 2012
America Begins to Strike Back Publicly Against Trade Secret Thefts (Plus, an idea for a change in the law.)
The Federal Bureau of Investigation's spy hunters usually shy away from drawing attention. But they're hoping the public takes notice of a new campaign trying to stop foreign spies from stealing trade secrets from U.S. companies.
The FBI, which is responsible for investigating breaches by foreign intelligence agencies, Friday will unveil billboards in nine cities around the country with the message: Protect America's Trade Secrets. The billboards direct the public to a section of the FBI website where the bureau provides warning signs to look for in the cubicle next to you.
Behind the campaign is the government's view that state-sponsored espionage targeting companies is growing so fast it is a national security concern. Lost trade secrets lead to lost jobs and in a time of economic struggle poses a national threat, says Frank Figliuzzi, the FBI's assistant director for counterintelligence. (more)
Note to FBI... Awareness is good, but it is not enough. Some private-sector intellectual property is so vital it should be classified as a National Security Resource.
The centuries-old, lopsided, 'punish the spy' model of protecting intellectual property has never worked. (more) (more) Caretakers of national security level proprietary information need to be held legally accountable for its protection. Doing this will give the law the balance and weight it needs to be effective.
Recommendation: Amend the Espionage Act to include mandatory, pro-active, business counterespionage security requirements. ~Kevin
The centuries-old, lopsided, 'punish the spy' model of protecting intellectual property has never worked. (more) (more) Caretakers of national security level proprietary information need to be held legally accountable for its protection. Doing this will give the law the balance and weight it needs to be effective.
Recommendation: Amend the Espionage Act to include mandatory, pro-active, business counterespionage security requirements. ~Kevin
Labels:
advice,
business,
counterespionage,
FBI,
government,
historical,
law,
mores,
trade secret
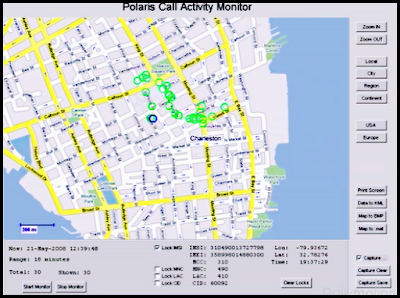
Cell Phone Tracking Insight - You're In Sight
This week at the CTIA show in New Orleans, Polaris Wireless unveiled Altus Mobile, an application that lets law-enforcement personnel track suspects via their cellphone numbers or mobile equipment identifier — a 56-bit identification number that is burned into the device and is extremely difficult to modify. The application leverages Polaris’s Wireless Location Signatures platform, which simultaneously can locate all subscriber devices on a wireless network, both in real time and historically.
That means law-enforcement officers will know where a suspect is, where he has been and where he is heading at any given moment, said Mahesh Patel, Polaris’s senior vice president of products and technology.
“Previously, this information was available to them on their desktops through our Altus surveillance solution, but now officers can take this information into the field with them,” Patel said. “Real-time access to this kind of intelligence will be a big plus for tactical operations.” (more)
“Previously, this information was available to them on their desktops through our Altus surveillance solution, but now officers can take this information into the field with them,” Patel said. “Real-time access to this kind of intelligence will be a big plus for tactical operations.” (more)
Verizon Mates With Cellcrypt - Bet You Can't Hear Me Now
UK mobile security firm Cellcrypt is partnering with carrier giant Verizon to sell its voice encryption technology for mobiles and smartphones to the US Government, the pair have announced.
Already in testing with unnamed US Government departments the service will be formally released later in 2012 as a co-branded product that marks a major foot in the door for Cellcrypt.
Working on Android, iPhone and BlackBerrys, the company’s software encrypts GSM mobile, WiFi and satellite phone calls to FIPS 140-2 level between handsets running the same software, defeating the potential for man-in-the-middle eavesdropping. (more)
Already in testing with unnamed US Government departments the service will be formally released later in 2012 as a co-branded product that marks a major foot in the door for Cellcrypt.
Working on Android, iPhone and BlackBerrys, the company’s software encrypts GSM mobile, WiFi and satellite phone calls to FIPS 140-2 level between handsets running the same software, defeating the potential for man-in-the-middle eavesdropping. (more)
Wednesday, May 9, 2012
FBI - Beware of Software Update Messages when Traveling
Recent analysis from the FBI and other government agencies demonstrates that malicious actors are targeting travelers abroad through pop-up windows while establishing an Internet connection in their hotel rooms.
Recently, there have been instances of travelers' laptops being infected with malicious software while using hotel Internet connections. In these instances, the traveler was attempting to setup the hotel room Internet connection and was presented with a pop-up window notifying the user to update a widely-used software product. If the user clicked to accept and install the update, malicious software was installed on the laptop. The pop-up window appeared to be offering a routine update to a legitimate software product for which updates are frequently available.
The FBI recommends that all government, private industry, and academic personnel who travel abroad take extra caution before updating software products on their hotel Internet connection. (more)
Recently, there have been instances of travelers' laptops being infected with malicious software while using hotel Internet connections. In these instances, the traveler was attempting to setup the hotel room Internet connection and was presented with a pop-up window notifying the user to update a widely-used software product. If the user clicked to accept and install the update, malicious software was installed on the laptop. The pop-up window appeared to be offering a routine update to a legitimate software product for which updates are frequently available.
The FBI recommends that all government, private industry, and academic personnel who travel abroad take extra caution before updating software products on their hotel Internet connection. (more)
Spook Summer School Saturday
Spy School — a Tampa Bay History Center program specially designed for teens — will instruct youngsters about surveillance, information gathering and disguise
 Agents and experts will teach children ages 12 to 18, offering tips on how to enter the espionage career field.
Agents and experts will teach children ages 12 to 18, offering tips on how to enter the espionage career field.
The program costs $60 per student but history center members get a $5 discount. Spy School begins Saturday and offers a guided tour with curator Rodney Kite-Powell.
The Tampa Bay area might not seem like an obvious spy hub. But many retired FBI, CIA and military members live in the area, and one of the nation's more high-profile spy court cases unfolded in 2001 in a U.S. District Court in Tampa. Also, United States Special Operations Command is based in Tampa.
For information on Spy School, call (813) 675-8960 or email Jennifer Tyson, the center's assistant curator of education, at jtyson @tampabayhistorycenter .org. (more)
 Agents and experts will teach children ages 12 to 18, offering tips on how to enter the espionage career field.
Agents and experts will teach children ages 12 to 18, offering tips on how to enter the espionage career field. The program costs $60 per student but history center members get a $5 discount. Spy School begins Saturday and offers a guided tour with curator Rodney Kite-Powell.
The Tampa Bay area might not seem like an obvious spy hub. But many retired FBI, CIA and military members live in the area, and one of the nation's more high-profile spy court cases unfolded in 2001 in a U.S. District Court in Tampa. Also, United States Special Operations Command is based in Tampa.
For information on Spy School, call (813) 675-8960 or email Jennifer Tyson, the center's assistant curator of education, at jtyson @tampabayhistorycenter .org. (more)
P.S. This is part of the International Spy Museum's traveling road show, "Spies,
Traitors, Saboteurs: Fear and Freedom in America." One of the show's features are historical artifacts on loan from Murray Associates / Spybusters, LLC; an APL Badge and ID Card (1917) carried by
operatives of the American Protective League (APL) who spied on their
fellow Americans on behalf of the U.S. Justice Department during World
War I. (see them here)
Tuesday, May 8, 2012
Spybusters Tip #834 - Singing the Butt-Dialing Blues
Spybusters Tip #834 - Stop butt-dialing by using your phone's password feature.
Here's what happens when you don't...
Druggie butt-dials police. Busted.
T-Mobile's Butt Dialing commercial.
"Butt" Dialing Becoming A Problem For 911 Dispatchers.
T-Mobile's Butt Dialing commercial.
"Butt" Dialing Becoming A Problem For 911 Dispatchers.
Free Security e-Book of the Week
FREE book: Fundamentals of Media Security (110 pages)
The most interesting chapters...
• Steganography
• Digital Watermarking
• Digital Scrambling
• Digital Surveillance
Enter your email address in #1. (The other three questions are benign.) The ebook will download as a pdf.
Labels:
book,
data,
encryption,
FREE,
spy school,
steganography,
Tips
Monday, May 7, 2012
"The secret of life is honesty and fair dealing. If you can fake that, you've got it made."
 India - Government today dismissed as "outrageous lie" a media report that at the behest of Home Minister P Chidambaram and his ministry telephones of key government functionaries were bugged. An official statement said attention of the Government has been drawn to a news story published in 'Chauthi Duniya' recently. "The story contains outrageous, baseless and defamatory allegations. There is no truth in the story whatsoever. The allegations that telephones were bugged at the instance of the Home Minister or the Ministry of Home Affairs is an outrageous lie," it said. The statement said that the government reserves its right to take appropriate action against the offending newspaper. Government would like to caution other newspapers and media not to reproduce or repeat the aforesaid story, it said. (more) (alternate quote)
India - Government today dismissed as "outrageous lie" a media report that at the behest of Home Minister P Chidambaram and his ministry telephones of key government functionaries were bugged. An official statement said attention of the Government has been drawn to a news story published in 'Chauthi Duniya' recently. "The story contains outrageous, baseless and defamatory allegations. There is no truth in the story whatsoever. The allegations that telephones were bugged at the instance of the Home Minister or the Ministry of Home Affairs is an outrageous lie," it said. The statement said that the government reserves its right to take appropriate action against the offending newspaper. Government would like to caution other newspapers and media not to reproduce or repeat the aforesaid story, it said. (more) (alternate quote)
Town Clerk Charged for Recording Colleagues
MI - Augusta Township Clerk Kathy Giszczak has been charged with eavesdropping for tape recording a conversation between the township supervisor and former deputy treasurer.
She turned herself in for the warrant on these charges by coming to the walk-in arraignment...Giszczak is free on a personal recognizance bond.
She has been charged with one count each of eavesdropping and using or disclosing information obtained through eavesdropping. Both counts each carry a maximum penalty of two years in prison and a $2,000 fine. (more)
She turned herself in for the warrant on these charges by coming to the walk-in arraignment...Giszczak is free on a personal recognizance bond.
She has been charged with one count each of eavesdropping and using or disclosing information obtained through eavesdropping. Both counts each carry a maximum penalty of two years in prison and a $2,000 fine. (more)
Ra-Parents Forcing Kids to Live Undercover
Kids are desperate to flee from their parents’ spying, reports the Wall Street Journal. In a piece about “Tweens’ Secret Lives Online,” the Journal tracks the online lengths kids are going to in order to get away from their stalkerish parents.
Digital anthropologist danah boyd told me last year that teens then were fleeing from Facebook to Twitter to escape the prying eyes of adults. WSJ journo Katherine Rosman says that Instagram is now one of the tools kids use to exchange messages in a semi-public way (where the public doesn’t include nosy adults)...
My own parents certainly didn’t have that luxury. I would disappear with my bike (Me too. With no freakin' helmet, of course.) on a Saturday and be completely out of touch, my whereabouts unknown for hours at a time.
Let’s hope that digitally enabled overparenting doesn’t completely crush kids’ freedom of exploration. Let tweens actually have a little bit of a secret life. (more)
Digital anthropologist danah boyd told me last year that teens then were fleeing from Facebook to Twitter to escape the prying eyes of adults. WSJ journo Katherine Rosman says that Instagram is now one of the tools kids use to exchange messages in a semi-public way (where the public doesn’t include nosy adults)...
My own parents certainly didn’t have that luxury. I would disappear with my bike (Me too. With no freakin' helmet, of course.) on a Saturday and be completely out of touch, my whereabouts unknown for hours at a time.
Let’s hope that digitally enabled overparenting doesn’t completely crush kids’ freedom of exploration. Let tweens actually have a little bit of a secret life. (more)
Illegal Watergate Wiretaps Requsted to be Released
A historian of the Richard Nixon presidency wants to review sealed wiretap materials stemming from the 1972 burglary at the Watergate hotel and subsequent criminal prosecutions.
In a pending case in Washington's federal trial court, the U.S. Justice Department on May 3 said "the request for the content of illegally obtained wiretaps poses an unusual legal issue that the department intends to address in its response."
Justice Department lawyer Elizabeth Shapiro asked Chief Judge Royce Lamberth of U.S. District Court for the District of Columbia for two more weeks to respond to the request from Luke Nichter, an assistant professor of history at Texas A&M University. The earlier deadline was May 5.
“These and other sealed materials may be the key to determining why the Watergate break-in occurred, who ordered it, and what the burglars were looking [for],” Nichter, who specializes in American political history, wrote in a letter (PDF) to Lamberth in 2010. Nichter is researching whether exposing a prostitution ring was the real reason for the Watergate burglary. (more)
In a pending case in Washington's federal trial court, the U.S. Justice Department on May 3 said "the request for the content of illegally obtained wiretaps poses an unusual legal issue that the department intends to address in its response."
Justice Department lawyer Elizabeth Shapiro asked Chief Judge Royce Lamberth of U.S. District Court for the District of Columbia for two more weeks to respond to the request from Luke Nichter, an assistant professor of history at Texas A&M University. The earlier deadline was May 5.
“These and other sealed materials may be the key to determining why the Watergate break-in occurred, who ordered it, and what the burglars were looking [for],” Nichter, who specializes in American political history, wrote in a letter (PDF) to Lamberth in 2010. Nichter is researching whether exposing a prostitution ring was the real reason for the Watergate burglary. (more)
Weakness of U.S. Counterespionage Law Examined
...a recent US court ruling that dealt a blow to the fight against corporate espionage in saying the download of proprietary data does not amount to a criminal offense. (more)
Sunday, May 6, 2012
Would you use spy gadgets in order to get custody of your kids?
On Thursday, "ABC World News with Diane Sawyer" explored the increasing use of surveillance equipment among exes in divorce and custody cases, from hiding a camera in a child's teddy bear to installing tape recorders in the home of an ex. (more)
CALEA Seeks New Orifices
The FBI is asking Internet companies not to oppose a controversial proposal that would require the firms, including Microsoft, Facebook, Yahoo, and Google, to build in backdoors for government surveillance.
In meetings with industry representatives, the White House, and U.S. senators, senior FBI officials argue the dramatic shift in communication from the telephone system to the Internet has made it far more difficult for agents to wiretap Americans suspected of illegal activities, CNET has learned.
The FBI general counsel's office has drafted a proposed law that the bureau claims is the best solution: requiring that social-networking Web sites and providers of VoIP, instant messaging, and Web e-mail alter their code to ensure their products are wiretap-friendly.
The FBI's proposal would amend a 1994 law, called the Communications Assistance for Law Enforcement Act, or CALEA, that currently applies only to telecommunications providers, not Web companies. The Federal Communications Commission extended CALEA in 2004 to apply to broadband networks. (more)
In meetings with industry representatives, the White House, and U.S. senators, senior FBI officials argue the dramatic shift in communication from the telephone system to the Internet has made it far more difficult for agents to wiretap Americans suspected of illegal activities, CNET has learned.
The FBI general counsel's office has drafted a proposed law that the bureau claims is the best solution: requiring that social-networking Web sites and providers of VoIP, instant messaging, and Web e-mail alter their code to ensure their products are wiretap-friendly.
The FBI's proposal would amend a 1994 law, called the Communications Assistance for Law Enforcement Act, or CALEA, that currently applies only to telecommunications providers, not Web companies. The Federal Communications Commission extended CALEA in 2004 to apply to broadband networks. (more)
Friday, May 4, 2012
The Wiretap Garrote
 |
| Courtesy Murray Associates - Click to Enlarge |
The 5-2 Court of Appeals ruling is a victory for law enforcement, said Brian Kleinbord, chief of criminal appeals division for the Maryland Attorney General's Office. "It means that drug dealers can't evade a wiretap by driving their cars across the state line."
But dissenters argued that multi-state wiretaps are the latest example of police using advances in technology to chip away at privacy rights.
Randy E. McDonald, a Washington-based lawyer who argued the case for a man convicted on drug charges, said police have gone too far and he is considering an appeal to the U.S. Supreme Court. (more)
The Gist of the Constable Eavesdropping Case Strikes Back
TX - A former Galveston County deputy constable (James P. Gist), who resigned last year after the district attorney’s office launched a criminal investigation into allegations that he bugged Precinct 7 Constable Pam Matranga’s office, filed a lawsuit Wednesday accusing the constable of sexual harassment...
In a series of allegations listed in the lawsuit, Gist maintains Matranga would lift her shirt over his head and press his head into her cleavage. He also alleges the constable would make crude statements and gestures...
...The lawsuit also states Gist had a recording device on his desk “in an effort to record and collect evidence of defendant Matranga’s sexual harassment.” (more)
In a series of allegations listed in the lawsuit, Gist maintains Matranga would lift her shirt over his head and press his head into her cleavage. He also alleges the constable would make crude statements and gestures...
...The lawsuit also states Gist had a recording device on his desk “in an effort to record and collect evidence of defendant Matranga’s sexual harassment.” (more)
Skipping the PI, they DIY spy!
The spy shop has become a new tool in the arsenal for feuding couples calling it quits in America. From phone tracking and GPS, to hidden cameras and microphones, America’s divorce lawyers have seen technology play a prominent role in their cases.
More than 80 percent of the nation’s top divorce attorneys say they’ve seen an increase in the role electronic data and social networking sites play in divorces, according to the American Academy of Matrimonial Lawyers.
One of the primary reasons is that do-it-yourself snooping has become relatively cheap and easy. Surveillance equipment can cost less than $300. It is simple to mount a microphone in a child’s blue jeans, as one Texas mother did, or hide a camera in a child’s favorite doll. (more)
More than 80 percent of the nation’s top divorce attorneys say they’ve seen an increase in the role electronic data and social networking sites play in divorces, according to the American Academy of Matrimonial Lawyers.
One of the primary reasons is that do-it-yourself snooping has become relatively cheap and easy. Surveillance equipment can cost less than $300. It is simple to mount a microphone in a child’s blue jeans, as one Texas mother did, or hide a camera in a child’s favorite doll. (more)
Labels:
amateur,
eavesdropping,
espionage,
FutureWatch,
GSM,
Hack,
mores,
product,
spycam,
spyware,
surveillance,
tracking,
wiretapping
Watch Over Me Requests Up 10%
US - In a letter to the Senate, the Justice Department reports it made 1,745 requests to the Foreign Intelligence Surveillance Court for special authority for wiretaps last year. That’s 10% more than 2010. None of those requests were denied, although judges did require changes to 30 requests.
The FBI also issued 16,511 national security letters seeking information like financial and phone records on 7,200 people. (more) (sing-a-long)
The FBI also issued 16,511 national security letters seeking information like financial and phone records on 7,200 people. (more) (sing-a-long)
Another Surveillance Concern - SMS Intercept Via CCTV
Australia - Surveillance cameras used during last year's Rugby World Cup could zoom in on individual spectators and camera operators could read their text messages, a privacy forum has heard... Privacy Commissioner Marie Shroff says reading someone's text messages
in public could cause concern, but the legitimacy of the action could
depend on what it was used for. (more)
Sunday, April 29, 2012
The Great Seal Bug Story (updated)
 Our compendium of first and second-hand accounts about The Great Seal Bug continues to grow. The latest contribution has just been posted, along with this rare schematic of the bug from Scientific American, and a video newsreel of Henry Cabot Lodge, Jr. showing off the device at the United Nations in 1960.
Our compendium of first and second-hand accounts about The Great Seal Bug continues to grow. The latest contribution has just been posted, along with this rare schematic of the bug from Scientific American, and a video newsreel of Henry Cabot Lodge, Jr. showing off the device at the United Nations in 1960.
Our latest voice of history begins... "I am a former Foreign Service Officer.
I have a certain amount of first hand, and a larger amount of 2nd hand knowledge about the thing, having worked for a couple of years in the early 1960s in the organization that was responsible for dealing with it and all similar problems - the division of technical services of the office of security of the department of state: abbreviated as O:SY/T.
I knew the tech who actually discovered the thing (slightly), and heard from him in detail exactly how he found it." (more)
I have a certain amount of first hand, and a larger amount of 2nd hand knowledge about the thing, having worked for a couple of years in the early 1960s in the organization that was responsible for dealing with it and all similar problems - the division of technical services of the office of security of the department of state: abbreviated as O:SY/T.
I knew the tech who actually discovered the thing (slightly), and heard from him in detail exactly how he found it." (more)
Subscribe to:
Posts (Atom)