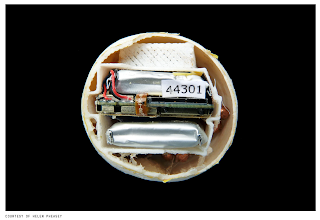
Blue Box, 1972. An original first iteration "blue box"
populated circuit board made by Steve Wozniak and marketed by Steve Jobs
and Wozniak, 51 x 72 mm, with speaker wire and 9volt battery connector.
Provenance: Purchased directly from Steve Wozniak by the consignor in Autumn 1972 during a drive together from Sunnyvale to Los Angeles.
Bid estimate:
US$ 4,000 - 6,000
£ 3,100 - 4,600
While "phone phreakers" (hobbyists who were fascinated by the phone
system) had used a "blue box" since the 1950s to avail themselves of
free phone service, the first digital blue box was designed by Steve
Wozniak in 1972.
It was marketed and sold by Wozniak (who took the phone
phreak name "Berkeley Blue"), Jobs (known as "Oaf Tobar"), and friends
in Berkeley and throughout California in 1972 and 1973.
Wozniak cites
the number of boxes they produced at 40 or 50, while Jobs put the number
at 100; but certainly many of those were confiscated as phone phreaking
arrests increased throughout 1973 to 1975, in part due to the
commercial distribution of the devices.
These blue boxes represent the
first commercial collaboration between the two Apple computer giants,
and the circuit boards the first printed boards by Woz.
Very few of the
Wozniak originals have survived and even fewer of these first iteration
boards as Wozniak soon changed the circuit board layout to accommodate a
less expensive membrane keypad. The early models would have been made
by Wozniak himself. more
Back Story: I examined the photos closely. The IC chips have manufacturing dates of 1973 & 1974, thus the provenance appeared misleading. I advised the specialist at Bonhams. To his credit, and that of the auction house, they very quickly researched it further. The auction now has an addendum which clears up the mystery...
"PCB was purchased unpopulated directly from Steve Wozniak by consignor
and parts were later added by consignor. Wozniak confirmed in an email
to the consignor that this was one of his boards and that Steve Jobs had
it printed."