The European Union is secretly developing a "remote stopping" device to be fitted to all cars that would allow the police to disable vehicles at the flick of a switch from a control room.
Confidential documents from a committee of senior EU police officers, who hold their meetings in secret, have set out a plan entitled "remote stopping vehicles" as part of wider law enforcement surveillance and tracking measures.
"The project will work on a technological solution that can be a 'build in standard' for all cars that enter the European market," said a restricted document.
The devices, which could be in all new cars by the end of the decade, would be activated by a police officer working from a computer screen in a central headquarters. (more)
"Calling all hackers. Calling all hackers..."
Thursday, January 30, 2014
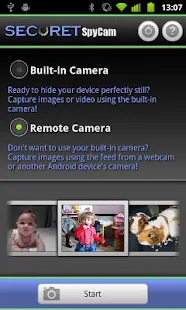
New SpyCam App for Android Phones and Tablets
via droidforums.net...
The new spycam app by "dooblou", SECuRET SpyCam, makes you an instant gum shoe!
There are maybe some not so ethical uses for this, but then again this app would make it easy to see who is stealing your juice out of the office cooler, or what exactly the babysitter is doing with your kid.
The app turns any Android phone or tablet camera as well as a remote camera into your very own motion triggered spycam. With this app your device will capture stills or video when activated by any motion within its field of view and then either save or email the photo or video.
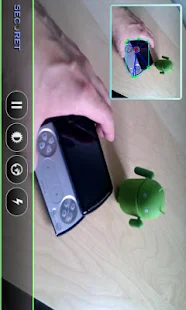
This app has apparently already caught several criminals in the act of stealing cars, and breaking into homes.
You don't have to use your phone you can use this app to control a laptops webcam or another device camera with the use of livestream.
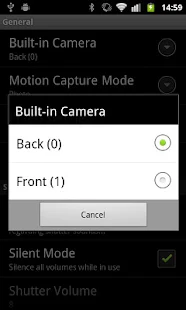
The app includes disguise mode and touch screen locking so your phone won't be detected, advanced settings to tweak performance and timings, ability to choose between the front and back cameras, choice of video and photo resolutions including resolutions photos and high def videos, quick start mode and more.
Pro version is $4.49, and there is a Demo version so you can see how it works before buying. (more)
Why do I mention it?
So you will know what you're up against.
The new spycam app by "dooblou", SECuRET SpyCam, makes you an instant gum shoe!
There are maybe some not so ethical uses for this, but then again this app would make it easy to see who is stealing your juice out of the office cooler, or what exactly the babysitter is doing with your kid.
The app turns any Android phone or tablet camera as well as a remote camera into your very own motion triggered spycam. With this app your device will capture stills or video when activated by any motion within its field of view and then either save or email the photo or video.
This app has apparently already caught several criminals in the act of stealing cars, and breaking into homes.
You don't have to use your phone you can use this app to control a laptops webcam or another device camera with the use of livestream.
The app includes disguise mode and touch screen locking so your phone won't be detected, advanced settings to tweak performance and timings, ability to choose between the front and back cameras, choice of video and photo resolutions including resolutions photos and high def videos, quick start mode and more.
Pro version is $4.49, and there is a Demo version so you can see how it works before buying. (more)
Why do I mention it?
So you will know what you're up against.
Not to be left out, tiny Malta has its own spy scandal...
Malta ...Home Affairs Minister Manuel Mallia was “caught eavesdropping” on an opposition meeting.
Reliable sources told this paper that Dr Mallia was last week caught “with his ears to the Opposition Parliament office” as a meeting was going on inside. At the time a meeting of the Opposition’s Committee for the South was being held. Chairman Stephen Spiteri and MPs Carm Mifsud Bonnici, Mario Galea, Jason Azzopardi and Anthony Bezzina were present.
The sources said that Dr Mallia was seen eavesdropping by another person, who is not a politician. (more)
Reliable sources told this paper that Dr Mallia was last week caught “with his ears to the Opposition Parliament office” as a meeting was going on inside. At the time a meeting of the Opposition’s Committee for the South was being held. Chairman Stephen Spiteri and MPs Carm Mifsud Bonnici, Mario Galea, Jason Azzopardi and Anthony Bezzina were present.
The sources said that Dr Mallia was seen eavesdropping by another person, who is not a politician. (more)
Tuesday, January 28, 2014
Proof Spying is Mainstream - The Walmart of India has a Spy Section
India - Naaptol with its “shop right, shop more” slogan has just announced its own list of the top 10 spy gadgets of 2014. And it’s just the start of the year!
They come in all shapes and sizes. Spy gadgets camouflaged as pens (Rs 2999 for 4 GB); sim card phone device ear bugs; and even cloth hooks spy cameras.
If that’s not enough, check out the video recording button camera. No one might suspect that it’s not part of your suit! You have an option of hidden cameras that fit in a car key-chain, the world’s smallest digital mini camera that is slightly bigger than your eye, motion sensor padlocks, anti-theft whistle key-chains, wall clocks that hide a CCTV camera, mini USB-shaped reader digital camera flash drive. (more) (store)
They come in all shapes and sizes. Spy gadgets camouflaged as pens (Rs 2999 for 4 GB); sim card phone device ear bugs; and even cloth hooks spy cameras.
If that’s not enough, check out the video recording button camera. No one might suspect that it’s not part of your suit! You have an option of hidden cameras that fit in a car key-chain, the world’s smallest digital mini camera that is slightly bigger than your eye, motion sensor padlocks, anti-theft whistle key-chains, wall clocks that hide a CCTV camera, mini USB-shaped reader digital camera flash drive. (more) (store)
Spy ‘Numbers Stations’ Still Baffle, Enthrall
In the early 1990s, at the end of the Cold War, before the onset of the Internet Age,
you could tune across the shortwave bands and hear the monotonous drone of an automated woman’s voice calling out long strings of numbers in Spanish. “Siete — Quatro — Cinqo — Cinqo — Cinqo,” the voice would say, pause, and then switch to a new set of numbers. The
Spanish-language
female voice station became known as “Attenćion,”
due to its repeated use of that phrase at the beginning of each
transmission.
These transmissions, which had started at the end of the Second World War, weren’t always in Spanish, nor were they always female. Other languages were used to broadcast entire strings of numbers, which many believed made up a coded message that could be heard by anyone with a shortwave radio. The consensus view at the time was they were meant for secret agents operating in foreign countries...
Today, with the Internet Age fully mature and the Cold War buried under 20 years of modern history, the numbers are still being transmitted. (more)
 |
| Courtesy, SpyArtStudios |
These transmissions, which had started at the end of the Second World War, weren’t always in Spanish, nor were they always female. Other languages were used to broadcast entire strings of numbers, which many believed made up a coded message that could be heard by anyone with a shortwave radio. The consensus view at the time was they were meant for secret agents operating in foreign countries...
Today, with the Internet Age fully mature and the Cold War buried under 20 years of modern history, the numbers are still being transmitted. (more)
Labels:
CIA,
government,
historical,
miscellaneous,
weird,
wireless
Surreptitous Workplace Recording - IT Guy Receives Sentence
PA - The Easton Area School District's former technology director has entered a first-time offenders program after being accused of illegally recording a private meeting.
That's according to the Morning Call, which says Thomas Drago's record will be expunged following a year on probation and a psychiatric evaluation.
Drago, 54, of Bushkill Township, resigned from his post in late 2012, just before the district began investigating whether he had been spying on his colleagues.
Police say investigators eventually learned Drago had used his iPhone to audio tape an "Act 93" meeting in March 2012. He was charged in August of last year with one count of felony wiretapping. (more)
Security Directors: FREE Security White Paper - "Surreptitious Workplace Recording ...and what you can do about it."
That's according to the Morning Call, which says Thomas Drago's record will be expunged following a year on probation and a psychiatric evaluation.
Drago, 54, of Bushkill Township, resigned from his post in late 2012, just before the district began investigating whether he had been spying on his colleagues.
Police say investigators eventually learned Drago had used his iPhone to audio tape an "Act 93" meeting in March 2012. He was charged in August of last year with one count of felony wiretapping. (more)
Security Directors: FREE Security White Paper - "Surreptitious Workplace Recording ...and what you can do about it."
Sunday, January 26, 2014
How to Stop Websites from Eavesdropping Via Google Chrome
...review the sites you've allowed to access your microphone and camera in Chrome.
1. Open Chrome, and type chrome://settings/contentExceptions#media-stream into the Omnibar.
2. You'll see the Media Exceptions screen, where you can see which host names have permissions to your microphone and camera, and which of those two each site has access to.
3. Highlight any site you want to remove, and click the "x" on the right side of the line.
4. Save your changed by clicking Done.
PCWorld also notes that if you prefer, you can just go to: chrome://settings/content Scroll down to Media, and instead of "Ask me when a site wants to use a plug-in to access my camera and microphone" (which is the default setting), select "Do not allow any sites to access my camera and microphone," which is kind of the nuclear option.
Doing this will also disable features like Google's Conversational Search, which can be pretty useful, likely break any voice integration with Google Now (which will arrive in Chrome any day now), and disable any other voice-activated features in Chrome or elsewhere on the web. (more) (background)
1. Open Chrome, and type chrome://settings/contentExceptions#media-stream into the Omnibar.
2. You'll see the Media Exceptions screen, where you can see which host names have permissions to your microphone and camera, and which of those two each site has access to.
3. Highlight any site you want to remove, and click the "x" on the right side of the line.
4. Save your changed by clicking Done.
PCWorld also notes that if you prefer, you can just go to: chrome://settings/content Scroll down to Media, and instead of "Ask me when a site wants to use a plug-in to access my camera and microphone" (which is the default setting), select "Do not allow any sites to access my camera and microphone," which is kind of the nuclear option.
Doing this will also disable features like Google's Conversational Search, which can be pretty useful, likely break any voice integration with Google Now (which will arrive in Chrome any day now), and disable any other voice-activated features in Chrome or elsewhere on the web. (more) (background)
800+ Detained in China for Illegal Surveillance
Chinese police have arrested over 800 people suspected of producing, selling and using illegal wiretapping and photography equipment to conduct surveillance.
Through joint efforts by police from 14 provincial regions, 13 production facilities have been destroyed and 67 groups associated with illegal wiretapping equipment have been uncovered in the action, the Ministry of Public Security said.
The police have uncovered over 1,550 criminal cases involving the use of wiretapping equipment in blackmail, kidnapping, illegal detention and other crimes. Over 15,000 sets of equipment for covert tracking, positioning, photographing and recording have been confiscated, state-run Xinhua news agency reported today. (more) (sing-a-long)
Through joint efforts by police from 14 provincial regions, 13 production facilities have been destroyed and 67 groups associated with illegal wiretapping equipment have been uncovered in the action, the Ministry of Public Security said.
The police have uncovered over 1,550 criminal cases involving the use of wiretapping equipment in blackmail, kidnapping, illegal detention and other crimes. Over 15,000 sets of equipment for covert tracking, positioning, photographing and recording have been confiscated, state-run Xinhua news agency reported today. (more) (sing-a-long)
Labels:
amateur,
blackmail,
business,
eavesdropping,
lawsuit,
mores,
product,
spycam,
wiretapping
Cell Phone Snitch Stories
Butt Dialing Law Suit Busted
KY - A federal judge has dismissed a lawsuit filed by Kenton County Airport Board Chairman Jim Huff and his wife after an airport secretary that Huff called accidentally overheard their private conversation... Huff accidentally dialed secretary Carol Spaw while on a business trip. Spaw overheard Huff discussing ways to demote the Cincinnati/Northern Kentucky International Airport's chief executive officer or get her to resign... Spaw took notes on the conversation and recorded a portion of it... (The judge) ruled that even though the cell phone call was accidental, Spaw was under no obligation to hang up. (more)
Butt Photos Proved It
A suspicious Kuwait man thought it was his chance to verify whether his wife is loyal to him when she went out and left her mobile phone at home. As he surfed through the phone’s files, he got the shock of his life when he saw obscene pictures of her with another man... “The man rushed to the police station and showed them what he found on his wife’s mobile. “He accused her of adultery and police decided to summon the wife to face her with the charges,” the Kuwaiti daily Al Shahid said. (more)
KY - A federal judge has dismissed a lawsuit filed by Kenton County Airport Board Chairman Jim Huff and his wife after an airport secretary that Huff called accidentally overheard their private conversation... Huff accidentally dialed secretary Carol Spaw while on a business trip. Spaw overheard Huff discussing ways to demote the Cincinnati/Northern Kentucky International Airport's chief executive officer or get her to resign... Spaw took notes on the conversation and recorded a portion of it... (The judge) ruled that even though the cell phone call was accidental, Spaw was under no obligation to hang up. (more)
Butt Photos Proved It
A suspicious Kuwait man thought it was his chance to verify whether his wife is loyal to him when she went out and left her mobile phone at home. As he surfed through the phone’s files, he got the shock of his life when he saw obscene pictures of her with another man... “The man rushed to the police station and showed them what he found on his wife’s mobile. “He accused her of adultery and police decided to summon the wife to face her with the charges,” the Kuwaiti daily Al Shahid said. (more)
Saturday, January 25, 2014
Tennessee Bill Would Shut Down NSA Spy Center
Legislators in Tennessee have introduced a bill that would ban the state from providing water and electricity to an NSA data center which is currently involved in building supercomputers designed to crack encrypted data.
The Fourth Amendment Protection Act, which mirrors legislation introduced in other states, would prohibit local and state agencies from “providing material support to…any federal agency claiming the power to authorize the collection of electronic data or metadata of any person pursuant to any action not based on a warrant.”
The bill also disincentivizes local companies from doing business with the NSA. (more)
Interestingly, Tennessee is the home of the most patriotic city in the U.S., Knoxville, and the largest manufacturer of counterspy gear in the U.S., REI. Tennessee's slogan, "America at its best."
The bill also disincentivizes local companies from doing business with the NSA. (more)
Interestingly, Tennessee is the home of the most patriotic city in the U.S., Knoxville, and the largest manufacturer of counterspy gear in the U.S., REI. Tennessee's slogan, "America at its best."
Two New Android Spyware Issues
Hop, Skip and a Bank Bug...
Malware capable of infecting Android handsets using Windows PCs and laptops has been uncovered targeting developers.
Security response manager at Symantec Alan Neville told V3 the malware is atypical as it uses a two-stage attack process to jump from Windows PCs to Android handsets.
"It starts with a Trojan that when executed creates a new service on a Windows machine," he said. "It then targets Android devices that connect on USB. It uses the Android debugging bridge to deliver the Fakebank Trojan." Fakebank is a notorious Trojan designed to take victims' financial data. (more)
Fake Security App Intercepts Calls and Texts...
Researchers have discovered a new Android malware family that disguises itself as a security app, and intercepts the incoming texts and calls of victims.
According to Hitesh Dharmdasani, a malware researcher... six variants of the Android malware, dubbed “HeHe,” have been detected by the firm.
On Wednesday, Dharmdasani told SCMagazine.com that the free app is most likely infecting users via third party app marketplaces or through SMS spam. (more)
Malware capable of infecting Android handsets using Windows PCs and laptops has been uncovered targeting developers.
Security response manager at Symantec Alan Neville told V3 the malware is atypical as it uses a two-stage attack process to jump from Windows PCs to Android handsets.
"It starts with a Trojan that when executed creates a new service on a Windows machine," he said. "It then targets Android devices that connect on USB. It uses the Android debugging bridge to deliver the Fakebank Trojan." Fakebank is a notorious Trojan designed to take victims' financial data. (more)
Fake Security App Intercepts Calls and Texts...
Researchers have discovered a new Android malware family that disguises itself as a security app, and intercepts the incoming texts and calls of victims.
According to Hitesh Dharmdasani, a malware researcher... six variants of the Android malware, dubbed “HeHe,” have been detected by the firm.
On Wednesday, Dharmdasani told SCMagazine.com that the free app is most likely infecting users via third party app marketplaces or through SMS spam. (more)
War On Drones Drones On War
NH - Rep. Neal M. Kurk (R) has introduced a bill that would limit the use of drones in the Granite State.
HB1620 is similar to a bill introduced earlier in the session by Rep. Joe Duarte, but takes things a step further by applying the prohibition to drone use by the federal government and including penalties for violating its provisions.
Kurk’s proposed legislation regulates the use of drones by governments, as well as individuals. It requires search warrants, levies fines, and does not allow for the lethal or nonlethal arming of drones in the state. (more)
Hope they include some reasonable exemptions, like flying model aircraft and FedEx hospital to hospital deliveries of transplant organs.
Friday, January 24, 2014
Conflicting Reports About the Turkish President's Bug
Turkey - The Supreme Court of Appeals denied a report saying that an apparatus used to reflect signals from a bugging device found in Prime Minister Recep Tayyip Erdoğan's office in Ankara in 2012 was found that same year on the roof of the top court's headquarters.
The Milliyet daily reported that the signal from a bugging device found in Erdoğan's office was found to be reflected by an apparatus installed on the roof of the Supreme Court of Appeals' headquarters, which is very close to the former Prime Ministry Office in Ankara, during technical inspections of the court's headquarters soon after the bugging devices were found. (more)
Coincidentally...
Turkish gov't to increase penalties for illegal wiretapping
The penalties for illegal wiretapping are to be strengthened in a government-led draft law which has stirred reactions from the opposition for increasing the justice minister’s power on the judiciary.
The draft law, on which the government is currently working, will increase the penalties for illegal wiretapping as well as limiting the wiretapping done by the permission of Turkey’s Directorate of Telecommunication (TİB), which is the sole authority over all of the wiretapping and surveillance activities of security units.
The penalties for those who leaked the wiretappings will be increased. The penalties for the officials, who used their authority to wiretap illegally, will also be regulated with the draft law. The use of wiretapping and audio surveillance as part of the investigations will be limited. (more)
The Milliyet daily reported that the signal from a bugging device found in Erdoğan's office was found to be reflected by an apparatus installed on the roof of the Supreme Court of Appeals' headquarters, which is very close to the former Prime Ministry Office in Ankara, during technical inspections of the court's headquarters soon after the bugging devices were found. (more)
Coincidentally...
Turkish gov't to increase penalties for illegal wiretapping
The penalties for illegal wiretapping are to be strengthened in a government-led draft law which has stirred reactions from the opposition for increasing the justice minister’s power on the judiciary.
The draft law, on which the government is currently working, will increase the penalties for illegal wiretapping as well as limiting the wiretapping done by the permission of Turkey’s Directorate of Telecommunication (TİB), which is the sole authority over all of the wiretapping and surveillance activities of security units.
The penalties for those who leaked the wiretappings will be increased. The penalties for the officials, who used their authority to wiretap illegally, will also be regulated with the draft law. The use of wiretapping and audio surveillance as part of the investigations will be limited. (more)
Spybusters Tip #873 - Eavesdropping on Foscam IP Video Cameras
The following Foscam MJPEG based video cameras (firmware version .54) can be accessed without a password: FI8904W, FI8905E, FI8905W, FI8906W, FI8907W, FI8909W, FI8910E, FI8910W, FI8916W, FI8918W, FI8919W
Foscam will be posting a firmware upgrade on their website to fix this issue. Unfortunately, most users will never know about it.

Test Your Camera - A quick way to verify and confirm if your camera has this issue:
1. Enter your camera's IP address in your web browser. Example: 192.168.1.101
2. When you see the password screen do not enter a User Id and Password. Simply click the OK button. If you see your camera, you have the problem.
Use this work-around for temporary protection (here), and be sure to upgrade the firmware when it becomes available (here).
Foscam will be posting a firmware upgrade on their website to fix this issue. Unfortunately, most users will never know about it.

Test Your Camera - A quick way to verify and confirm if your camera has this issue:
1. Enter your camera's IP address in your web browser. Example: 192.168.1.101
2. When you see the password screen do not enter a User Id and Password. Simply click the OK button. If you see your camera, you have the problem.
Use this work-around for temporary protection (here), and be sure to upgrade the firmware when it becomes available (here).
Plan to Ban Instant Messaging has Unintended Consequences
Goldman Sachs Group Inc. is planning to ban traders from using some computer-messaging services in a bid to protect proprietary information at the heart of its sales-and-trading operation.
Under a new policy, the Wall Street firm won't allow person-to-person communication over instant-messaging (IM) services created by Bloomberg LP, Yahoo Inc., AOL Inc. and other third-party providers including Pivot Inc., according to a draft of a memo reviewed by The Wall Street Journal.
Goldman is seeking to prevent information from internal conversations from being filtered and disseminated beyond the bank's walls. The planned ban reflects a mistrust of technology developed by messaging-service providers that can make its traders more efficient but also be used to mine private communications for closely guarded intelligence on securities pricing. (more)
FutureWatch: Expect other financial institutions to follow.
Unintended Consequence: Scraping (a Wall Street term for collecting useful tidbits of info) attempts will continue as always, but it won't be easy pickings anymore. Conventional spycraft (bugging and wiretapping) worked before IM came along. It continues to work, and will become the best option again. Technical Surveillance Countermeasures (TSCM) inspections are the most cost-effective defense.
Under a new policy, the Wall Street firm won't allow person-to-person communication over instant-messaging (IM) services created by Bloomberg LP, Yahoo Inc., AOL Inc. and other third-party providers including Pivot Inc., according to a draft of a memo reviewed by The Wall Street Journal.
Goldman is seeking to prevent information from internal conversations from being filtered and disseminated beyond the bank's walls. The planned ban reflects a mistrust of technology developed by messaging-service providers that can make its traders more efficient but also be used to mine private communications for closely guarded intelligence on securities pricing. (more)
FutureWatch: Expect other financial institutions to follow.
Unintended Consequence: Scraping (a Wall Street term for collecting useful tidbits of info) attempts will continue as always, but it won't be easy pickings anymore. Conventional spycraft (bugging and wiretapping) worked before IM came along. It continues to work, and will become the best option again. Technical Surveillance Countermeasures (TSCM) inspections are the most cost-effective defense.
Labels:
business,
computer,
eavesdropping,
employee,
espionage,
FutureWatch,
leaks,
mores,
TSCM,
wiretapping
Wednesday, January 22, 2014
UPDATED - Privacy Journal's Compilation of State and Federal Privacy Laws
This new book includes new privacy laws on: demands for social-media passwords by employers and universities, use of credit reports by employers, new tracking technologies, new state restrictions on use and disclosure of Social Security numbers, plus updated chapters on credit reporting, medical, financial, testing in employment, insurance, government information, and much more, grouped by categories and listed alphabetically by states. Descriptions of state, federal, and Canadian laws are included.
Privacy Journal's Compilation of State and Federal Privacy Laws replaces the 2002 book and all subsequent supplements in one consolidated hard copy edition, 80 pages, ISBN is 9780930072568
It is also available in an electronic edition so that you may store it in your computer and search later by key words and states.
 Contact:
Contact:
Lee Shoreham, Assistant to the Publisher
PRIVACY JOURNAL
PO Box 28577
Providence RI 02908
Phone: 401/274-7861
Fax: 401/274-4747
orders@privacyjournal.net
www.privacyjournal.net
Also available from amazon.com.
Privacy Journal's Compilation of State and Federal Privacy Laws replaces the 2002 book and all subsequent supplements in one consolidated hard copy edition, 80 pages, ISBN is 9780930072568
It is also available in an electronic edition so that you may store it in your computer and search later by key words and states.
 Contact:
Contact:Lee Shoreham, Assistant to the Publisher
PRIVACY JOURNAL
PO Box 28577
Providence RI 02908
Phone: 401/274-7861
Fax: 401/274-4747
orders@privacyjournal.net
www.privacyjournal.net
Also available from amazon.com.
JoJo's TSCM Adventure... as told to the court.
NJ - Former city recreation employee Charles Hall III testified Tuesday that Joseph “JoJo” Giorgianni gave him anti-surveillance device to try to detect an FBI bug hidden in the clubhouse next door to JoJo’s Steakhouse on Dec. 23, 2012.
Hall testified on the seventh day of testimony in Trenton Mayor Tony Mack’s trial on bribery and extortion charges in U.S. District Court.
Hall told the court that Giorgianni had him sweep for an FBI listening device to attempt to locate a government bug.
“Nothing really happened,” Hall said. “I don’t know if the device worked at the time.” (more)
Hall testified on the seventh day of testimony in Trenton Mayor Tony Mack’s trial on bribery and extortion charges in U.S. District Court.
Hall told the court that Giorgianni had him sweep for an FBI listening device to attempt to locate a government bug.
“Nothing really happened,” Hall said. “I don’t know if the device worked at the time.” (more)
Security Alert - Eavesdropping via the Chrome Browser
Users of Google's Chrome browser are vulnerable to attacks that allow malicious websites to use a computer microphone to surreptitiously eavesdrop on private conversations for extended periods of time...
The attack requires an end user to click on a button giving the website permission to access the microphone. Most of the time, Chrome will respond by placing a blinking red light in the corresponding browser tab and putting a camera icon in the address bar—both indicating that the website is receiving a live audio feed from the visitor.
The privacy risk stems from what happens once a user leaves the site. The red light and camera icon disappear even though the website has the ability to continue listening in. (more)
The attack requires an end user to click on a button giving the website permission to access the microphone. Most of the time, Chrome will respond by placing a blinking red light in the corresponding browser tab and putting a camera icon in the address bar—both indicating that the website is receiving a live audio feed from the visitor.
The privacy risk stems from what happens once a user leaves the site. The red light and camera icon disappear even though the website has the ability to continue listening in. (more)
Surreptitious Recording in the Future
via The Wall Street Journal...
I've been snapping photos of everything in front of me for the last week. If we've passed, even for a moment, I probably have a picture of your face.
I'm not a spy, but I've been using gear you might associate with 007. New matchbook-size cameras that clip to your tie or shirt let you capture a day's worth of encounters, then upload them to the Internet to be remembered forever.
Why on Earth would anybody want to do that? After trying out two devices that recently began shipping, the $279 Narrative Clip and $399 Autographer, I think the answer for many will be why wouldn't you? (more)
The reporter, Geoffrey A. Fowler, goes on to say why these are inadequate for spy use, and reflects on the etiquette issues.
Security Directors: FREE Security White Paper - "Surreptitious Workplace Recording ...and what you can do about it."
FutureWatch - We are still in the infancy of documenting our entire lives. The black box of the future could record your life 24/7, with personal data, e.g. health statistics, your five senses and emotional states. Imagine the problems. Would using one become mandatory for law enforcement purposes? In what ways will your black box be valuable to thieves and hackers? Ultimately, who owns your life?
I've been snapping photos of everything in front of me for the last week. If we've passed, even for a moment, I probably have a picture of your face.
I'm not a spy, but I've been using gear you might associate with 007. New matchbook-size cameras that clip to your tie or shirt let you capture a day's worth of encounters, then upload them to the Internet to be remembered forever.
Why on Earth would anybody want to do that? After trying out two devices that recently began shipping, the $279 Narrative Clip and $399 Autographer, I think the answer for many will be why wouldn't you? (more)
The reporter, Geoffrey A. Fowler, goes on to say why these are inadequate for spy use, and reflects on the etiquette issues.
Security Directors: FREE Security White Paper - "Surreptitious Workplace Recording ...and what you can do about it."
FutureWatch - We are still in the infancy of documenting our entire lives. The black box of the future could record your life 24/7, with personal data, e.g. health statistics, your five senses and emotional states. Imagine the problems. Would using one become mandatory for law enforcement purposes? In what ways will your black box be valuable to thieves and hackers? Ultimately, who owns your life?
Sunday, January 19, 2014
Business Espionage: Bratz Bitch Slaps Barbie Over Spying to the Tune of $1 Billion
MGA Entertainment Inc. (MGA) filed a major trade secret theft lawsuit against Mattel Inc. on over reportedly stealing information at industry trade shows, and is seeking damages of at least $1 billion. This is the latest in a long-running battle between the two competing doll makers.
 MGA claims that throughout a period of years, Mattel instructed its employees to engage in acts of "espionage and fraud" to steal MGA's trade secrets...
MGA claims that throughout a period of years, Mattel instructed its employees to engage in acts of "espionage and fraud" to steal MGA's trade secrets...
The Bratz doll makers claim that for a number of years, Mattel employees used a "Market Intelligence Department" to steal MGA's trade secrets under the aspices of an 11-page "How-to-Steal" manual. Mattel also reportedly set up "spies," who created false identities by printing fake business cards and used Mattel's accounting department to create mocked-up invoices to back up their fictional businesses in to better gain access to MGA's private showrooms.
MGA also claims that Mattel employees purchased small video recorders (paid for by Mattel) and cameras to photograph and videotape what they saw in private showrooms and industry trade shows. As a result, Mattel obtained highly confidential information about MGA's designs, price lists and marketing plans for unannounced future products in the highly popular Bratz line, according to MGA. (more)
 MGA claims that throughout a period of years, Mattel instructed its employees to engage in acts of "espionage and fraud" to steal MGA's trade secrets...
MGA claims that throughout a period of years, Mattel instructed its employees to engage in acts of "espionage and fraud" to steal MGA's trade secrets...The Bratz doll makers claim that for a number of years, Mattel employees used a "Market Intelligence Department" to steal MGA's trade secrets under the aspices of an 11-page "How-to-Steal" manual. Mattel also reportedly set up "spies," who created false identities by printing fake business cards and used Mattel's accounting department to create mocked-up invoices to back up their fictional businesses in to better gain access to MGA's private showrooms.
MGA also claims that Mattel employees purchased small video recorders (paid for by Mattel) and cameras to photograph and videotape what they saw in private showrooms and industry trade shows. As a result, Mattel obtained highly confidential information about MGA's designs, price lists and marketing plans for unannounced future products in the highly popular Bratz line, according to MGA. (more)
Husband's Intimate Tweets to Other Woman Posted on Net by Wife... and then...
One of India's most prominent politicians, Shashi Tharoor, has been caught in an excruciating cross-border Twitter scandal after his wife posted allegedly intimate text messages between the government minister and a Pakistani journalist on his social media account.
The latest Twitter tempest for Dr Tharoor, Minister for Human Resources, author and former senior UN official once mooted as a candidate for secretary-general, threatens not only to scuttle a promising political career and a three-year marriage but also expose the politician to further legal scrutiny over a 2010 Indian Premier League cricket bidding scandal that cost him his then job as a junior minister. (more) (background)
This just in...
Shashi Tharoor's wife was found dead in a luxury hotel room in Delhi after she went public on Twitter... (more)
The latest Twitter tempest for Dr Tharoor, Minister for Human Resources, author and former senior UN official once mooted as a candidate for secretary-general, threatens not only to scuttle a promising political career and a three-year marriage but also expose the politician to further legal scrutiny over a 2010 Indian Premier League cricket bidding scandal that cost him his then job as a junior minister. (more) (background)
This just in...
Shashi Tharoor's wife was found dead in a luxury hotel room in Delhi after she went public on Twitter... (more)
Wiretap Boast Makes Mr. Harden Criminal (Darwin Award)
The first of my 2014 Darwin Awards goes to...
OR- Daniel Devon Harden, 38, was arraigned Thursday afternoon on allegations of attempted murder, first-degree assault, second-degree assault and unlawful use of a weapon stemming from a stabbing at a Northeast Portland club on Sept. 23...
Portland police solved the case after Harden boasted about the stabbing, which was picked up during an unrelated federal wiretap investigation into a cocaine-trafficking ring, according to court records. (more)
OR- Daniel Devon Harden, 38, was arraigned Thursday afternoon on allegations of attempted murder, first-degree assault, second-degree assault and unlawful use of a weapon stemming from a stabbing at a Northeast Portland club on Sept. 23...
Portland police solved the case after Harden boasted about the stabbing, which was picked up during an unrelated federal wiretap investigation into a cocaine-trafficking ring, according to court records. (more)
Saturday, January 18, 2014
Drone Law News. A license to shoot 'um down! And, a brillant career move.
• Legislation has been introduced in the Missouri House of Representatives that would regulate the use of unmanned aerial vehicles (drones) and protect the privacy rights of citizens. (more)
• Deer Trail, Colorado - Wearing a black duster and a black cowboy hat, Phil Steel walked to the front of the meeting room armed with a Nerf gun and a smile. The U.S. Army veteran was there to pitch his big idea: an ordinance that would legalize and regulate drone hunting inside Deer Trail city limits. If approved, residents could pay $25 to get a drone-hunting license; the town would pay a bounty for every drone bagged.
 Steel had hammered out the 2,800-word ordinance in just four hours. Its key points:
Steel had hammered out the 2,800-word ordinance in just four hours. Its key points:
- When a drone flies into its airspace, Deer Trail will consider it an act of war.
- You can only shoot at drones flying lower than 1,000 feet.
- Unless your life is in danger, you can only fire up to three shots at a drone. (more)
He has already sold more than 60 of his own licenses online.
• ND - Rodney Brossart, a North Dakotan cattle rancher, was sentenced to three years in prison, with all but six months suspended, for terrorizing police officers who were trying to arrest him at his property in 2011. The strange case garnered national attention because it was the first time a law enforcement agency had used an unmanned aerial vehicle to assist in carrying out an arrest. (more)
• With a 34-2 vote, New Jersey’s State Senate approved a bill that provides some of the nation’s strongest protections against drone surveillance. The bill, which went through several incarnations since being introduced last spring, restricts how police, firefighters and other first responders can use drones... It also includes a ban on outfitting them with weapons. bada-bing-bada-no-boom (more)
FutureWatch - Career Alert - Employment Hope for Twitchy Fingered Youth
The Federal Aviation Administration estimates up to 7,500 commercial drones could be flying in national airspace within a few years... Several colleges now offering courses! (more) (more)
 |
| Click to enlarge. |
 Steel had hammered out the 2,800-word ordinance in just four hours. Its key points:
Steel had hammered out the 2,800-word ordinance in just four hours. Its key points: - When a drone flies into its airspace, Deer Trail will consider it an act of war.
- You can only shoot at drones flying lower than 1,000 feet.
- Unless your life is in danger, you can only fire up to three shots at a drone. (more)
He has already sold more than 60 of his own licenses online.
• ND - Rodney Brossart, a North Dakotan cattle rancher, was sentenced to three years in prison, with all but six months suspended, for terrorizing police officers who were trying to arrest him at his property in 2011. The strange case garnered national attention because it was the first time a law enforcement agency had used an unmanned aerial vehicle to assist in carrying out an arrest. (more)
• With a 34-2 vote, New Jersey’s State Senate approved a bill that provides some of the nation’s strongest protections against drone surveillance. The bill, which went through several incarnations since being introduced last spring, restricts how police, firefighters and other first responders can use drones... It also includes a ban on outfitting them with weapons. bada-bing-bada-no-boom (more)
FutureWatch - Career Alert - Employment Hope for Twitchy Fingered Youth
The Federal Aviation Administration estimates up to 7,500 commercial drones could be flying in national airspace within a few years... Several colleges now offering courses! (more) (more)
The
Federal Aviation Administration estimates up to 7,500 commercial drones
could be flying in national airspace within a few years
Read more at http://www.toledoblade.com/local/2013/12/25/Ohio-students-eye-drone-jobs-Copy.html#2lCZsJDGZVL0iU62.99
Read more at http://www.toledoblade.com/local/2013/12/25/Ohio-students-eye-drone-jobs-Copy.html#2lCZsJDGZVL0iU62.99
The
Federal Aviation Administration estimates up to 7,500 commercial drones
could be flying in national airspace within a few years
Read more at http://www.toledoblade.com/local/2013/12/25/Ohio-students-eye-drone-jobs-Copy.html#2lCZsJDGZVL0iU62.99
Read more at http://www.toledoblade.com/local/2013/12/25/Ohio-students-eye-drone-jobs-Copy.html#2lCZsJDGZVL0iU62.99
Supreme Court to Consider if Police Need Warrants to Search Cellphones
The Supreme Court on Friday agreed to hear a pair of cases about whether the police need a warrant to search the cellphones of people they arrest, presenting a major test of the meaning of the Fourth Amendment in the digital age.
The court has long allowed warrantless searches in connection with arrests, saying they are justified by the need to find weapons and to prevent the destruction of evidence.
The question for the justices in the new cases is whether the potentially vast amounts of data held on smartphones warrant a different approach under the Fourth Amendment, which bars unreasonable searches.
The lower courts are divided. (more) (more) (GEICO Pig don't care.)
The court has long allowed warrantless searches in connection with arrests, saying they are justified by the need to find weapons and to prevent the destruction of evidence.
The question for the justices in the new cases is whether the potentially vast amounts of data held on smartphones warrant a different approach under the Fourth Amendment, which bars unreasonable searches.
The lower courts are divided. (more) (more) (GEICO Pig don't care.)
Obama on Digital Spying: Hey, Companies Do It, Too
In a much-anticipated speech, President Barack Obama took to the podium to introduce changes he aims to make to the National Security Administration's surveillance operations... Those in the business community may have been surprised that the president took a moment to remind Americans that spying isn't just a government practice.
Here's what the President said about corporate data tracking:
"Corporations of all shapes and sizes track what you buy, store and analyze our data, and use it for commercial purposes; that's how those targeted ads pop up on your computer or smartphone." (more)
Why does this remind me of my mother saying, "So, if George jumped off the roof would you do it too?"
Here's what the President said about corporate data tracking:
"Corporations of all shapes and sizes track what you buy, store and analyze our data, and use it for commercial purposes; that's how those targeted ads pop up on your computer or smartphone." (more)
Why does this remind me of my mother saying, "So, if George jumped off the roof would you do it too?"
Friday, January 17, 2014
Eye Spy - Scraping Info From Corneas
Advances in photography are rapidly making indirect spying possible. Reflections off of corneas, or any reflective surface, can be gleaned with off-the-shelf cameras and lenses.
Have a look...
You may want to close the blinds in your office. (more)
Have a look...
You may want to close the blinds in your office. (more)
Thursday, January 16, 2014
Surreptitious Workplace Recording - Jailer v Jailer
NJ - Federal prosecutors say the deputy director of the Hudson County jail used a website to illegally wiretap some of his fellow employees.
Kirk Eady turned himself in today and made his initial court appearance, where bail was set at $100,000 unsecured bond and he was order to surrender any firearms. Eady has been suspended without pay, Hudson County spokesman James Kennelly said today. Eady earns $120,000 annually...
Prosecutors say that between March and July 2012, Eady used a publicly available website to place telephone calls to four Hudson County jail employees. The website allowed Eady to conceal the telephone numbers from where the calls originated and also call and record two people simultaneously.
The site also made it appear that those people, and not Eady, originated the call. (more)
Kirk Eady turned himself in today and made his initial court appearance, where bail was set at $100,000 unsecured bond and he was order to surrender any firearms. Eady has been suspended without pay, Hudson County spokesman James Kennelly said today. Eady earns $120,000 annually...
Prosecutors say that between March and July 2012, Eady used a publicly available website to place telephone calls to four Hudson County jail employees. The website allowed Eady to conceal the telephone numbers from where the calls originated and also call and record two people simultaneously.
The site also made it appear that those people, and not Eady, originated the call. (more)
Kevin's Security Tip of the Day
With all the data breaches in the news recently, you may wonder if your information was plundered. Find out at Have I Been Pawned? Mine has:(
If so, it's time to scurry around and change your on-line passwords.
Need help?
Password generators.
Password managers.
Password strength testers.
Make sure your new passwords are not on this list...
The Top 500 Worst Passwords of All Time
How to Create Easy to Remember Secure Passwords...
You can create a memorable, secure password starting with a simple phrase. We call these "passphrases". For example, let's use a quote from Ogden Nash:
"Happiness is having a scratch for every itch."
If we use the first letter of each word, and substitute 4 for "for", we get:
Hihas4ei
This is a reasonably strong password but we can improve it a bit by adding some special characters:
#Hihas4ei:
Associating Web Sites...
We can use our new password on several different websites by adding a suffix with a mnemonic link to a particular site. Let's use the first letter and the next two consonants in the site name.
Just to add a bit more randomness we'll alternate upper-case and lower case, and if the first character in the site name is a vowel we'll start with upper-case. To mix things up a bit more we'll use the same rule to decide whether to add the site mnemonic to the left side or the right side.
#Hihas4ei:AmZ for Amazon
fBk#Hihas4ei: for Facebook
#Hihas4ei:YtB for YouTube
(more)
If so, it's time to scurry around and change your on-line passwords.
Need help?
Password generators.
Password managers.
Password strength testers.
Make sure your new passwords are not on this list...
The Top 500 Worst Passwords of All Time
How to Create Easy to Remember Secure Passwords...
You can create a memorable, secure password starting with a simple phrase. We call these "passphrases". For example, let's use a quote from Ogden Nash:
"Happiness is having a scratch for every itch."
If we use the first letter of each word, and substitute 4 for "for", we get:
Hihas4ei
This is a reasonably strong password but we can improve it a bit by adding some special characters:
#Hihas4ei:
Associating Web Sites...
We can use our new password on several different websites by adding a suffix with a mnemonic link to a particular site. Let's use the first letter and the next two consonants in the site name.
Just to add a bit more randomness we'll alternate upper-case and lower case, and if the first character in the site name is a vowel we'll start with upper-case. To mix things up a bit more we'll use the same rule to decide whether to add the site mnemonic to the left side or the right side.
#Hihas4ei:AmZ for Amazon
fBk#Hihas4ei: for Facebook
#Hihas4ei:YtB for YouTube
(more)
Wednesday, January 15, 2014
Your Automobile is Very Likely Spying on You
...but Republicans and Democrats in the U.S. Senate are uniting to put a stop to unfettered snooping via the "black boxes," or "event data recorders," placed in your car by automakers.
Is your car spying on you? If the vehicle is a fairly new model it probably is, thanks to a "black box" that collects data about what’s going on in your car. And there’s no off switch or way to opt out. By September all new cars sold in the United States will be required to have black boxes, or as they’re more formally called, "event data recorders."
"The amount of data that they record is vast. And it's not capped," said Nate Cardozo, a staff attorney with the Electronic Frontier Foundation (EFF).
That’s just one way new technology installed in automobiles is invading our privacy. At the 2014 Consumer Electronics Show (CES) last week, Google and a handful of automobile manufacturers, including Audi, GM, Honda and Hyundai, announced a partnership designed to bring the Android mobile platform to vehicles. Those devices are capable of broadcasting your location, Web pages you may have looked at, stores you shopped in and much much more. Chevrolet, for example, showed off a camera mounted on the windshield that records the driver’s point of view and a microphone in the cabin records any noises made in the car.
...Consider what Ford’s top sales guy James Farley said at a CES event: "We know everyone who breaks the law. We know when you’re doing it. We have GPS in your car, so we know what you’re doing." Farley quickly retracted his impolitic remarks, but they give you insight into how seriously some automakers take your privacy. (more)
Is your car bugged?
See if you are on the list.
If so, read this.
~Kevin
Is your car spying on you? If the vehicle is a fairly new model it probably is, thanks to a "black box" that collects data about what’s going on in your car. And there’s no off switch or way to opt out. By September all new cars sold in the United States will be required to have black boxes, or as they’re more formally called, "event data recorders."
"The amount of data that they record is vast. And it's not capped," said Nate Cardozo, a staff attorney with the Electronic Frontier Foundation (EFF).
That’s just one way new technology installed in automobiles is invading our privacy. At the 2014 Consumer Electronics Show (CES) last week, Google and a handful of automobile manufacturers, including Audi, GM, Honda and Hyundai, announced a partnership designed to bring the Android mobile platform to vehicles. Those devices are capable of broadcasting your location, Web pages you may have looked at, stores you shopped in and much much more. Chevrolet, for example, showed off a camera mounted on the windshield that records the driver’s point of view and a microphone in the cabin records any noises made in the car.
...Consider what Ford’s top sales guy James Farley said at a CES event: "We know everyone who breaks the law. We know when you’re doing it. We have GPS in your car, so we know what you’re doing." Farley quickly retracted his impolitic remarks, but they give you insight into how seriously some automakers take your privacy. (more)
Is your car bugged?
See if you are on the list.
If so, read this.
~Kevin
Labels:
Android,
business,
data,
FutureWatch,
law,
recording,
surveillance
Infographic - The Relative Cost of Surveillance
Ashkan Soltani, a privacy and security researcher who has been working with the Washington Post on the Snowden files, has published a graphic that illustrates how technology has greatly reduced the barriers to performing surveillance. Soltani included the graph in a paper published in the Yale Law Journal...
The cost comparison involves the several location surveillance techniques of physical pursuit by foot and in vehicles, location tracking using a radio beeper, a GPS device, or a cell phone.
A few examples for understanding the chart:
• Tracking a suspect using a GPS device is 28 times cheaper than assigning officers to follow him.
• Tracking a suspect using cell phone data is 53 times cheaper than physical covert pursuit.
• Tracking a cell phone is twice as cheap as using a GPS device. (more)
 |
| Click to enlarge. |
The cost comparison involves the several location surveillance techniques of physical pursuit by foot and in vehicles, location tracking using a radio beeper, a GPS device, or a cell phone.
A few examples for understanding the chart:
• Tracking a suspect using a GPS device is 28 times cheaper than assigning officers to follow him.
• Tracking a suspect using cell phone data is 53 times cheaper than physical covert pursuit.
• Tracking a cell phone is twice as cheap as using a GPS device. (more)
...and now, your moment of spy palindrome and Zen...
Nurse, I spy gypsies, run!
...and a chaser story...
New Zealander Nancy Wake fought fearlessly for the Allies in World War II, first for the French resistance and later as a spy for Britain’s Special Operations Executive.
Parachuted into the Auvergne in April 1944, she was hanging from a tree when a resistance fighter told her, “I hope that all the trees in France bear such beautiful fruit this year.”
She said, “Don’t give me that French sh_t.”
..."More!" I hear you say...
In November 2006, 23-year-old David Fearn of Staffordshire changed his name to James Dr. No From Russia With Love Goldfinger Thunderball You Only Live Twice On Her Majesty’s Secret Service Diamonds Are Forever Live and Let Die The Man With the Golden Gun The Spy Who Loved Me Moonraker For Your Eyes Only Octopussy A View to a Kill The Living Daylights Licence to Kill GoldenEye Tomorrow Never Dies The World Is Not Enough Die Another Day Casino Royale Bond.
It’s the longest name in deed poll history. (more)
...and a chaser story...
New Zealander Nancy Wake fought fearlessly for the Allies in World War II, first for the French resistance and later as a spy for Britain’s Special Operations Executive.
Parachuted into the Auvergne in April 1944, she was hanging from a tree when a resistance fighter told her, “I hope that all the trees in France bear such beautiful fruit this year.”
She said, “Don’t give me that French sh_t.”
..."More!" I hear you say...
In November 2006, 23-year-old David Fearn of Staffordshire changed his name to James Dr. No From Russia With Love Goldfinger Thunderball You Only Live Twice On Her Majesty’s Secret Service Diamonds Are Forever Live and Let Die The Man With the Golden Gun The Spy Who Loved Me Moonraker For Your Eyes Only Octopussy A View to a Kill The Living Daylights Licence to Kill GoldenEye Tomorrow Never Dies The World Is Not Enough Die Another Day Casino Royale Bond.
It’s the longest name in deed poll history. (more)
Tuesday, January 14, 2014
Huawei Defends Against Whitehall Bugging Claims
UK - Huawei, the Chinese telecoms company that came under suspicion of spying for the Chinese government, has been forced to defend its security records after reports that Government departments believed its technology could be bugged.
Reports at the weekend alleged that three Whitehall departments ordered that video conferencing devices supplied by Huawei should be removed, due to concerns about possible security vulnerabilities in the equipment. (more)
Reports at the weekend alleged that three Whitehall departments ordered that video conferencing devices supplied by Huawei should be removed, due to concerns about possible security vulnerabilities in the equipment. (more)
Eavesdropping Software Products Sold in the Open
Viet Nam - (Smartphone) software products have become so smart that they not only allow eavesdropping on normal calls or SMS, but the calls and SMS applied OTT apps as well.
There are four eavesdropping software products mostly popular in Vietnam, namely Amaza Tracker, Spyphone, Copyphone, Mobile Spy. They are originated from other countries, compatible to most of the popular operation systems now, from Android, iOS to Windows Phone, BlackBerry. Especially, the products have been updated regularly to be suitable to the mobile phones of the latest generations...
More dangerously, with the advanced technologies, some spyware products can allow to watch the messages and free calls on Line, Viber, WhatsApp, Facebook, Yahoo. Meanwhile, the majority of the popular products can be compatible with Android and iOS based smart phones.
The information can be copied in files, and then sent to the emails of the eavesdroppers. (more)
There are four eavesdropping software products mostly popular in Vietnam, namely Amaza Tracker, Spyphone, Copyphone, Mobile Spy. They are originated from other countries, compatible to most of the popular operation systems now, from Android, iOS to Windows Phone, BlackBerry. Especially, the products have been updated regularly to be suitable to the mobile phones of the latest generations...
More dangerously, with the advanced technologies, some spyware products can allow to watch the messages and free calls on Line, Viber, WhatsApp, Facebook, Yahoo. Meanwhile, the majority of the popular products can be compatible with Android and iOS based smart phones.
The information can be copied in files, and then sent to the emails of the eavesdroppers. (more)
British Spies – Licensed to Speed
British spies are to be given a "license to speed", allowing the likes of James Bond to drive fast with impunity in the name of national security.
 Transport minister Robert Goodwill was to announce the motoring law changes on Monday, which will hand spooks the same exemption as the police, fire service and ambulance drivers.
Transport minister Robert Goodwill was to announce the motoring law changes on Monday, which will hand spooks the same exemption as the police, fire service and ambulance drivers.
Officers in the MI5 and MI6 domestic and foreign intelligence agencies will be able to break the speed limit on surveillance and covert operations once they have completed a training course in high-speed driving. (more)
 Transport minister Robert Goodwill was to announce the motoring law changes on Monday, which will hand spooks the same exemption as the police, fire service and ambulance drivers.
Transport minister Robert Goodwill was to announce the motoring law changes on Monday, which will hand spooks the same exemption as the police, fire service and ambulance drivers. Officers in the MI5 and MI6 domestic and foreign intelligence agencies will be able to break the speed limit on surveillance and covert operations once they have completed a training course in high-speed driving. (more)
Business Extortion via Electronic Eavesdropping Bugs and Spyware
China - Police have arrested a divorced man and his mistress for subjecting his ex-wife to months of illegal surveillance, intimidation and extortion to gain control of half of her company, local media reported Friday.
The suspects, surnamed Zhu and Liu, spent almost a year spying on their victim, surnamed Wei, by installing monitoring software on her computers and bugging her home, her car and her luggage in a plot to destroy her reputation, according to a report in the Xinmin Evening News. By the time they were caught, the pair had cost Wei's company more than 100 million yuan ($16.5 million) in lost business.
Police said more and more illegal surveillance cases have emerged as technology has advanced, according to the report. Last year, Shanghai police arrested about 190 suspects for the illegal trade or use of surveillance equipment, seizing 500 pieces of equipment and more than 100 million pieces of personal information. (more)
The suspects, surnamed Zhu and Liu, spent almost a year spying on their victim, surnamed Wei, by installing monitoring software on her computers and bugging her home, her car and her luggage in a plot to destroy her reputation, according to a report in the Xinmin Evening News. By the time they were caught, the pair had cost Wei's company more than 100 million yuan ($16.5 million) in lost business.
Police said more and more illegal surveillance cases have emerged as technology has advanced, according to the report. Last year, Shanghai police arrested about 190 suspects for the illegal trade or use of surveillance equipment, seizing 500 pieces of equipment and more than 100 million pieces of personal information. (more)
Labels:
amateur,
business,
eavesdropping,
GPS,
lawsuit,
spyware,
wiretapping
Sunday, January 12, 2014
Government Begins Responding to Spying Objections
Maryland legislators will consider a package of laws to curb electronic surveillance by police, requiring a search warrant to use drones, email, cellphone towers or license plate readers to track people.
Measures sponsored by a bipartisan pair of senators come amid a national debate over government surveillance after revelations about the extent to which the National Security Agency collects information on U.S. citizens. (more)
Obama to unveil spying reforms on 17th January
White House spokesman Jay Carney said that Obama's remarks would show the "outcomes of the work that has been done on the review process."
The White House said on Thursday that the president was nearing the end of his soul searching about US spying reforms as he met lawmakers who oversee the intelligence community. (more)
FBI Director James Comey recently told reporters that the federal government's spying on American citizens via the National Security Agency is the "way the founders intended." (more)
CA - Sen. Ted Lieu (D-Torrance) and Sen. Joel Anderson (R-San Diego) introduced the Fourth Amendment Protection Act to prohibit any state support of the NSA. “State-funded public resources should not be going toward aiding the NSA or any other federal agency from indiscriminate spying on its own citizens and gathering electronic or metadata that violates the Fourth Amendment,” Lieu said in a press release. (more)
Measures sponsored by a bipartisan pair of senators come amid a national debate over government surveillance after revelations about the extent to which the National Security Agency collects information on U.S. citizens. (more)
Obama to unveil spying reforms on 17th January
White House spokesman Jay Carney said that Obama's remarks would show the "outcomes of the work that has been done on the review process."
The White House said on Thursday that the president was nearing the end of his soul searching about US spying reforms as he met lawmakers who oversee the intelligence community. (more)
FBI Director James Comey recently told reporters that the federal government's spying on American citizens via the National Security Agency is the "way the founders intended." (more)
CA - Sen. Ted Lieu (D-Torrance) and Sen. Joel Anderson (R-San Diego) introduced the Fourth Amendment Protection Act to prohibit any state support of the NSA. “State-funded public resources should not be going toward aiding the NSA or any other federal agency from indiscriminate spying on its own citizens and gathering electronic or metadata that violates the Fourth Amendment,” Lieu said in a press release. (more)
Thursday, January 9, 2014
Interesting Spy Stories Today
Private Eye Sky Spies
 Click-bait, or cold reality? The headline for Robinson Meyer’s article in the Atlantic about three Silicon Valley start-ups and their plans to make money off satellite photography of the earth is “Silicon Valley’s New Spy Satellites.” Very soon, it’s likely that it will be substantially easier to buy recent, high-resolution imagery of the Earth’s surface... the message they send together is simple: We’re all spies now. (more)
Click-bait, or cold reality? The headline for Robinson Meyer’s article in the Atlantic about three Silicon Valley start-ups and their plans to make money off satellite photography of the earth is “Silicon Valley’s New Spy Satellites.” Very soon, it’s likely that it will be substantially easier to buy recent, high-resolution imagery of the Earth’s surface... the message they send together is simple: We’re all spies now. (more)
What Will Anna Chapman Do Next? Former spy Anna Chapman, who was sent back from the United States to Russia in a major spy swap in 2010, is going to present her own clothing line at a fashion show in the Turkish resort of Antalya. (more) (Anna's adventure timeline)
500 Years of History Shows that Mass Spying Is Always Aimed at Crushing Dissent (more)
Boycott Of RSA Security Conference Builds In Wake Of NSA Spy Scandal (more)
 Click-bait, or cold reality? The headline for Robinson Meyer’s article in the Atlantic about three Silicon Valley start-ups and their plans to make money off satellite photography of the earth is “Silicon Valley’s New Spy Satellites.” Very soon, it’s likely that it will be substantially easier to buy recent, high-resolution imagery of the Earth’s surface... the message they send together is simple: We’re all spies now. (more)
Click-bait, or cold reality? The headline for Robinson Meyer’s article in the Atlantic about three Silicon Valley start-ups and their plans to make money off satellite photography of the earth is “Silicon Valley’s New Spy Satellites.” Very soon, it’s likely that it will be substantially easier to buy recent, high-resolution imagery of the Earth’s surface... the message they send together is simple: We’re all spies now. (more)What Will Anna Chapman Do Next? Former spy Anna Chapman, who was sent back from the United States to Russia in a major spy swap in 2010, is going to present her own clothing line at a fashion show in the Turkish resort of Antalya. (more) (Anna's adventure timeline)
500 Years of History Shows that Mass Spying Is Always Aimed at Crushing Dissent (more)
Boycott Of RSA Security Conference Builds In Wake Of NSA Spy Scandal (more)
Wednesday, January 8, 2014
Amateur Spies - Surgeon Accused of Spying on Ex with Software
TX - A pioneer in cancer research is facing a second degree felony charge in an alleged plot to spy on his ex-wife while they were going through their divorce.
According to prosecutors, Dr. Steven Curley plotted with a computer expert to install a program called eBlaster. (more)
IA - ...the Iowa City landlord found guilty last year of spying on his tenants (six counts) through bathroom peepholes in 2012, has motioned for a new trial... (speed bump) ...The city’s Housing and Inspections Services office says the city’s housing code doesn’t address cases such as this, therefore Miller is able to continue to own and manage the properties. (more)
PA - Forty-three years after the mysterious theft of up to 1,000 documents from an FBI office outside Philadelphia, three former political activists are publicly confessing to the brazen burglary, calling it an act of “resistance” that exposed “massive illegal surveillance and intimidation.”... Members of the burglary team, armed with little more than a crowbar and wearing suits and ties, then walked off undetected with suitcases stuffed with sensitive bureau files that revealed a domestic FBI spying operation known as COINTELPRO. (more)
Canada - A St. Albert man who surreptitiously took pictures of young girls in change rooms at five Alberta recreational facilities... was sentenced to two years in prison Tuesday. (more)
FL - A St. Augustine man and former Putnam County deputy (and St. Johns County reserve deputy) accused of using his cellphone to record a tanning room at the U.S. 1 South World Gym was sentenced Tuesday to 300 days in jail... a woman reported that a gym employee put a cellphone in the closet of the tanning room to record people getting in and out of the booth... (more)
The Point
Anyone can be a spy. The technology is cheap, and easy to use. Just add motivation.
FutureWatch
This will become a real workplace issue in 2014.
And now, a very creepy moment of spy Zen...
According to prosecutors, Dr. Steven Curley plotted with a computer expert to install a program called eBlaster. (more)
IA - ...the Iowa City landlord found guilty last year of spying on his tenants (six counts) through bathroom peepholes in 2012, has motioned for a new trial... (speed bump) ...The city’s Housing and Inspections Services office says the city’s housing code doesn’t address cases such as this, therefore Miller is able to continue to own and manage the properties. (more)
PA - Forty-three years after the mysterious theft of up to 1,000 documents from an FBI office outside Philadelphia, three former political activists are publicly confessing to the brazen burglary, calling it an act of “resistance” that exposed “massive illegal surveillance and intimidation.”... Members of the burglary team, armed with little more than a crowbar and wearing suits and ties, then walked off undetected with suitcases stuffed with sensitive bureau files that revealed a domestic FBI spying operation known as COINTELPRO. (more)
Canada - A St. Albert man who surreptitiously took pictures of young girls in change rooms at five Alberta recreational facilities... was sentenced to two years in prison Tuesday. (more)
FL - A St. Augustine man and former Putnam County deputy (and St. Johns County reserve deputy) accused of using his cellphone to record a tanning room at the U.S. 1 South World Gym was sentenced Tuesday to 300 days in jail... a woman reported that a gym employee put a cellphone in the closet of the tanning room to record people getting in and out of the booth... (more)
The Point
Anyone can be a spy. The technology is cheap, and easy to use. Just add motivation.
FutureWatch
This will become a real workplace issue in 2014.
And now, a very creepy moment of spy Zen...
Sunday, January 5, 2014
NSA Can Now Bug iPhones (yawn)
Reports have surfaced that the US National Security Agency can now turn iPhones into eavesdropping tools.
That’s the word from security expert Jacob Appelbaum, who told a hacker conference in Germany that the NSA can plant iPhone malware called Dropout Jeep, which gives American intelligence agents the ability to turn the gadget into a listening post using the iPhone camera and microphone. Also, it has a spyware function that can retrieve contact information, read through text messages and emails, and listen to voicemails. (more)
(Yawn.) Spyware for smartphones has been around for years. You can purchase it with a few keystrokes.
Don't worry about the NSA. They could probably care less about you. Worry about your employer, disgruntled employee, or significant other.
Then, if the question, "Is my cell phone bugged?" pops into your mind, buy a good book, or app, and find out what to do about it.
That’s the word from security expert Jacob Appelbaum, who told a hacker conference in Germany that the NSA can plant iPhone malware called Dropout Jeep, which gives American intelligence agents the ability to turn the gadget into a listening post using the iPhone camera and microphone. Also, it has a spyware function that can retrieve contact information, read through text messages and emails, and listen to voicemails. (more)
(Yawn.) Spyware for smartphones has been around for years. You can purchase it with a few keystrokes.
Don't worry about the NSA. They could probably care less about you. Worry about your employer, disgruntled employee, or significant other.
Then, if the question, "Is my cell phone bugged?" pops into your mind, buy a good book, or app, and find out what to do about it.
The Annabel Melongo Eavesdropping Case - 8 Years and Counting
The Annabel Melongo saga continues in the Illinois Supreme Court Tuesday, Jan. 14, marking the eighth year the case has been tied up in litigation.
Melongo was (also) indicted for eavesdropping, as a grand jury accused her of illegally recording conversations with a Cook County court reporter.
The indictment accused Melongo of:
(1) Eavesdropping without consent:
“…in that she knowingly and intentionally used an eavesdropping device, to wit: an audio recording device, for the purpose of recording a conversation, to wit: recording a conversation conducted by telephone between Annabel K. Melongo and Pamela Taylor of the Cook County Court Reporter’s Office, and without the consent of all parties to such conversation and without authorization provided by Article 108A or Article 108B of the ‘Code of Criminal Procedure of 1963,’ approved August 13, 1963, as amended.” (more)
Note to Clients: I will send you a private report this month about covert recording in the workplace, and what to do about it. You really don't want to be tied up in 8-year-long court battles.
Melongo was (also) indicted for eavesdropping, as a grand jury accused her of illegally recording conversations with a Cook County court reporter.
The indictment accused Melongo of:
(1) Eavesdropping without consent:
“…in that she knowingly and intentionally used an eavesdropping device, to wit: an audio recording device, for the purpose of recording a conversation, to wit: recording a conversation conducted by telephone between Annabel K. Melongo and Pamela Taylor of the Cook County Court Reporter’s Office, and without the consent of all parties to such conversation and without authorization provided by Article 108A or Article 108B of the ‘Code of Criminal Procedure of 1963,’ approved August 13, 1963, as amended.” (more)
Note to Clients: I will send you a private report this month about covert recording in the workplace, and what to do about it. You really don't want to be tied up in 8-year-long court battles.
Facebook Sued Under Federal Wiretapping Law For Mining Private Messages
Facebook faces a potential class action lawsuit (“Matthew Campbell v. Facebook Inc.”) for allegedly violating the US Electronic Communications Privacy Act and California privacy and unfair competition laws. At issue is the company’s alleged practice of scanning private Facebook messages (first discovered in 2012) for URLs and then using that information as part of its ad targeting data. (more)
Trending TV: Spies are hot, again
Secret agents are lurking everywhere on TV in 2014.
From "The Avengers" to "Mission Impossible" to "24," spy thrillers always have been a TV staple, but with the National Security Agency under fire for spying on everyday Americans and others, espionage stories seem all the more resonant these days. Here's a look at several current or upcoming spy shows and several old favorites that can be seen online... (more)
From "The Avengers" to "Mission Impossible" to "24," spy thrillers always have been a TV staple, but with the National Security Agency under fire for spying on everyday Americans and others, espionage stories seem all the more resonant these days. Here's a look at several current or upcoming spy shows and several old favorites that can be seen online... (more)
Subscribe to:
Comments (Atom)




















